#detectiontechnique résultats de recherche
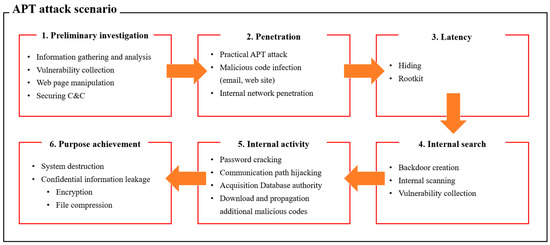
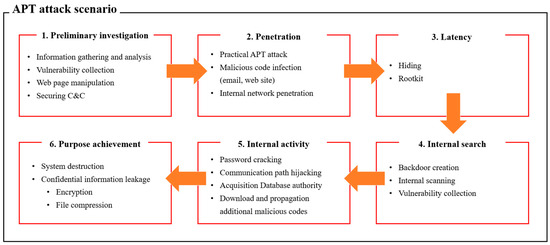
🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique
The Single-Packet Shovel: Digging for Desync-Powered Request Tunnelling #RequestTunnelling #DetectionTechnique #WebSecurityResearch #HTTPDesyncAttacks #SinglePacketAttack assured.se/posts/the-sing…
An intuitive explanation of the SSD MultiBox object detection technique towardsdatascience.com/understanding-… #IntuitiveExplanation #SsdMultibox #DetectionTechnique
techcmd.com/detection-of-h… Procedure of honeypot detection can be performed on a newly infected computer before allowing to join the network. Botmasters uses authorization mechanism to finalize a host .#botnet #detectiontechnique #honeypot
🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique

The Single-Packet Shovel: Digging for Desync-Powered Request Tunnelling #RequestTunnelling #DetectionTechnique #WebSecurityResearch #HTTPDesyncAttacks #SinglePacketAttack assured.se/posts/the-sing…
📢 Read our Review paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Dr. Kyungroul Lee et al. #maliciouscode #detectiontechnique
techcmd.com/detection-of-h… Procedure of honeypot detection can be performed on a newly infected computer before allowing to join the network. Botmasters uses authorization mechanism to finalize a host .#botnet #detectiontechnique #honeypot
An intuitive explanation of the SSD MultiBox object detection technique towardsdatascience.com/understanding-… #IntuitiveExplanation #SsdMultibox #DetectionTechnique
🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique

Something went wrong.
Something went wrong.
United States Trends
- 1. Rashford 43K posts
- 2. White House 456K posts
- 3. Fermin 66.3K posts
- 4. ChatGPT Atlas 7,343 posts
- 5. Crosby 5,751 posts
- 6. Woody Johnson 1,728 posts
- 7. #pilotstwtselfieday 1,397 posts
- 8. Lakers 33.4K posts
- 9. Barca 72.2K posts
- 10. Olympiacos 44.7K posts
- 11. Kurt Suzuki 2,406 posts
- 12. Lamine 30K posts
- 13. Ben Shelton N/A
- 14. John Brennan 16.2K posts
- 15. NASA 64.2K posts
- 16. #ScarierThanHalloween N/A
- 17. Warriors 51.6K posts
- 18. Chrome 14.2K posts
- 19. #TrumpHatesOurHealthCare 5,487 posts
- 20. Barcelona 156K posts




