#maliciouscode search results
Pharming ≠ farming. It’s a cyber trick using #MaliciousCode to redirect to fake sites. Criminals use #AI to clone legit pages, exploit weak spots & dodge #MalwareDetection. Add #SocialEngineering, #Spoofing & #Typosquatting Cyber zoo ahead, stay sharp with #Cybersecurity!

🧩 Browser Injection Layer Page-load overlays were observed as part of the payload. 💬 JavaScript injection 🎯 Persistent bottom-right prompt 🔍 Matches known credential-targeting techniques tied to PlugX ecosystems #JavaScript #MaliciousCode #Phishing #WebSecurity #CyberCrime…
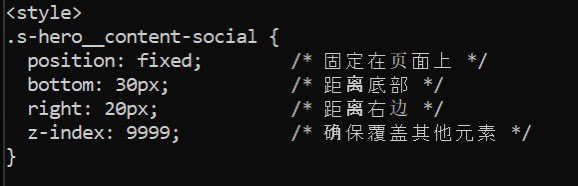
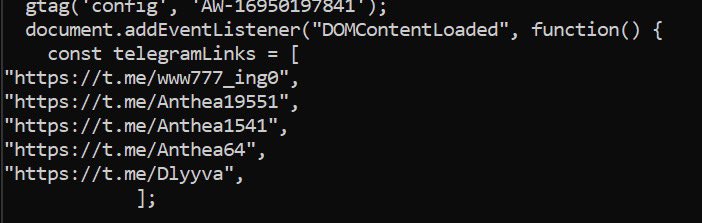
🦟Threat Actors Start Hiding Malware within Website Images🖼️ Cybercriminals are increasingly embedding malware in website images to evade detection and compromise IT systems. Read more👇 buff.ly/224mfhG #generativeAI #maliciouscode #Phishing #websiteimages
"Types of Malicious Codes" Youtube Channel :- lnkd.in/dwD9BzX @www.fornsec.in #MaliciousCode #CyberThreats #MalwareAttack #ComputerVirus #TrojanHorse #WormAttack #Spyware #Ransomware #Adware #Rootkit #Keylogger #Botnet #PhishingAttack #CyberSecurity #CyberAwareness

Malicious contracts are often masked as legitimate SPL tokens. SPL Shield detects and flags these malicious contracts instantly upon launch. #MaliciousCode #SPLToken

Why you should delete your browser extensions right now - or do this to stay safe #BrowserExtensions #MaliciousCode #TrustedSources #CreditCardInformation #Linux #MacOS #Cyberthreat zdnet.com/article/why-yo…
Could your CI/CD pipeline be harboring malicious code silently? Red flags include obfuscated scripts, rogue CI jobs, unusual network calls, and secrets misuse. Dive in➡️ xygeni.io/blog/which-of-… #DevSecOps #MaliciousCode #AppSec #CI_CD #SupplyChainSecurity #Xygeni
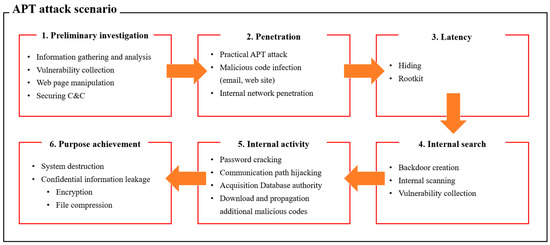
🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique
@FogoChain’s security continuously monitors smart contract bytecode for signs of obfuscated malicious code. #BytecodeMonitoring #MaliciousCode?
Socket researchers found Go modules rigged with code to wipe Linux disks, exposing new risks in open source supply-chain security. #LinuxSecurity #SupplyChainAttack #MaliciousCode

The discovery of security vulnerabilities in Apple AirPlay has raised concerns about the potential for hackers to access networks and disseminate malicious code among different devices. bit.ly/3ERYUUE #MaliciousCode #Cybersecurity #IncreasedRisk

It's not exactly something that is going to affect users but still wild to see such a blatant use of malicious code in the wild. #javascript #cookies #maliciouscode
We're just gonna leave this here.. Knowledge is power. The more you know... #MaliciousCode #HackThePlanet #Anonymous thehackernews.com/2025/03/coffee…
Something went wrong.
Something went wrong.
United States Trends
- 1. Kansas 23.8K posts
- 2. Missouri 9,243 posts
- 3. Arrowhead 6,728 posts
- 4. Vince Zampella 25.1K posts
- 5. McNeil 5,931 posts
- 6. Clark Hunt 1,602 posts
- 7. Call of Duty 27K posts
- 8. Olathe N/A
- 9. Jackson County 1,507 posts
- 10. Titanfall 5,084 posts
- 11. Token "F" N/A
- 12. Rob Refsnyder N/A
- 13. KCMO N/A
- 14. Royals 5,226 posts
- 15. Trump Class 4,231 posts
- 16. Golden Fleet 1,808 posts
- 17. Zimbabwe 29.5K posts
- 18. Fartcoin v2 N/A
- 19. #Fliffmas 2,200 posts
- 20. Utah State 2,092 posts




















