#malwareclassification search results
#MachineLearning learning aided #Androidmalware #Malwareclassification doi.org/10.1016/j.comp… #MobileMalware

#HighCitedPaper #HighViewedPaper👉Ensemble #MalwareClassification System Using #DeepNeuralNetworks👈by Barath Narayanan Narayanan (from @univofdayton) and Venkata Salini Priyamvada Davuluru (from @UDRI_1) 🖱️doi.org/10.3390/electr… #Electronics #ArtificialIntelligence
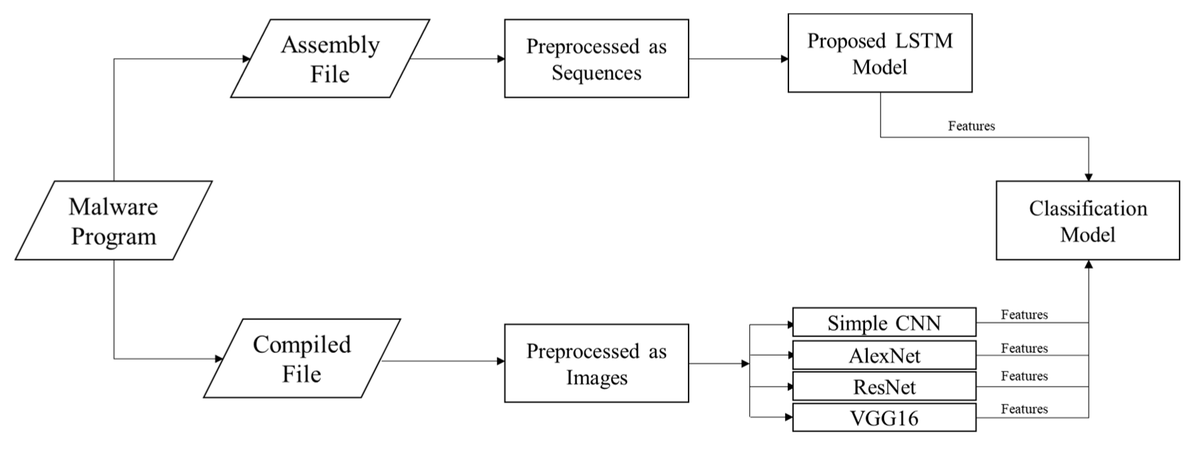
🔥 Read our Highly Cited Paper 📚Robust Malware Family Classification Using Effective Features and Classifiers 🔗mdpi.com/2076-3417/12/1… 👨🔬 by Dr. Baraa Tareq Hammad et al. #malwareclassification #deeplearning
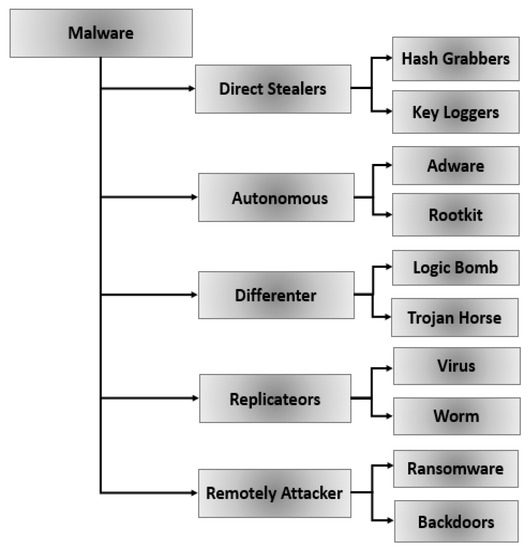
Genetic Malware Analysis helps organizations detect & classify advanced cyber threats, including evasive & fileless malware. Visit booth L45 during #infosec19 to demo our technology & pick up some fun SWAG @Infosecurity #codereuse #malwareclassification

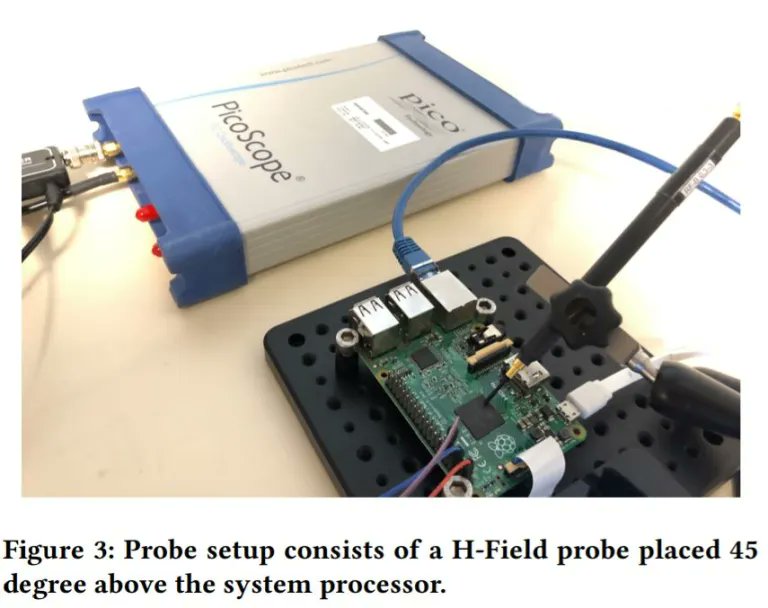
#Hacking #MalwareClassification #Malware #Vulnerability #CyberAttack #CyberCrime #CyberSecurity Cybersecurity researchers demonstrate how to use electromagnetic field emanations from IoT devices to detect malware. dl.acm.org/doi/10.1145/34…
#MalwareClassification encompasses the identification & attribution of code, has the power to unlock many clues that aid #security teams & helps to understand potential adversaries you are up against. Find out more in our @IntezerLabs report. bit.ly/2KaSIV2

Poster session at #EICC2023. Interesting posters being presented. #deviceadoption #malwareclassification #QuantumKeyDistribution
📚 Check out the Top 10 Papers from 🇺🇸 USA authors in MAKE (2022-2023): mdpi.com/journal/make/a… No. 10 "On Deceiving #MalwareClassification with Section Injection" By Adeilson Antonio da Silva and Maurício Pamplona Segundo 👉 mdpi.com/2504-4990/5/1/9
🥳Original Article: Graph neural network based function call graph embedding for malware classification 🔜Coming Soon! 🥰Stay tuned for our latest research 👉Follow us @JSSSJournal for updates and exciting insights! #malwareclassification #graphneuralnetworks #research

Something went wrong.
Something went wrong.
United States Trends
- 1. Mets 48.2K posts
- 2. Orioles 17.8K posts
- 3. Red Sox 8,127 posts
- 4. David Stearns 5,000 posts
- 5. Nimmo 2,795 posts
- 6. #TheMaskedSinger 1,034 posts
- 7. Bregman 3,507 posts
- 8. Cohen 11.5K posts
- 9. Bellinger 3,108 posts
- 10. Rule 5 4,927 posts
- 11. AL East 4,259 posts
- 12. John Henry 1,125 posts
- 13. #Supergirl 45.3K posts
- 14. Breslow 1,702 posts
- 15. Polar Bear 2,789 posts
- 16. #Birdland N/A
- 17. Yankees 11K posts
- 18. FOMC 49.2K posts
- 19. The Fed 89.8K posts
- 20. Chris Davis N/A









