Pyvonix
@Pyv0nix
Security Research • If all persons who can do something are in the bad side, the game could not be balanced.
Może Ci się spodobać
#opendir: http://hokoog[.]com/yo/ I think I like these little guys that make your life easier by letting access to to their webshell. @JAMESWT_MHT @James_inthe_box @ViriBack
![Pyv0nix's tweet image. #opendir: http://hokoog[.]com/yo/
I think I like these little guys that make your life easier by letting access to to their webshell.
@JAMESWT_MHT @James_inthe_box @ViriBack](https://pbs.twimg.com/media/Dhz8G8tXkAAT-ks.jpg)
![Pyv0nix's tweet image. #opendir: http://hokoog[.]com/yo/
I think I like these little guys that make your life easier by letting access to to their webshell.
@JAMESWT_MHT @James_inthe_box @ViriBack](https://pbs.twimg.com/media/Dhz8PwaX4AAsBa7.jpg)
![Pyv0nix's tweet image. #opendir: http://hokoog[.]com/yo/
I think I like these little guys that make your life easier by letting access to to their webshell.
@JAMESWT_MHT @James_inthe_box @ViriBack](https://pbs.twimg.com/media/Dhz8RKDWsAA0BJg.jpg)
#opendir: aitelong[.]top/amadi/ contents: .exe and .hta malware: #lokibot #pony For this episode of "chose your malware", I offer a wide range of files. @James_inthe_box
![Pyv0nix's tweet image. #opendir: aitelong[.]top/amadi/
contents: .exe and .hta
malware: #lokibot #pony
For this episode of "chose your malware", I offer a wide range of files.
@James_inthe_box](https://pbs.twimg.com/media/DgDQbWdWkAEa-Wi.jpg)
Besides developing malware, they make poetry... Oh wait. It's lyrics of Nerd Ambition by YTCracker. Malware: #tinynuke Payload: coriolis[.]site/facture/ Panel: 4s65xlo930ubyjz8dlcm[.]com/admin/login.php
![Pyv0nix's tweet image. Besides developing malware, they make poetry...
Oh wait. It's lyrics of Nerd Ambition by YTCracker.
Malware: #tinynuke
Payload: coriolis[.]site/facture/
Panel: 4s65xlo930ubyjz8dlcm[.]com/admin/login.php](https://pbs.twimg.com/media/DfpGLg3WkAAft0i.jpg)
![Pyv0nix's tweet image. Besides developing malware, they make poetry...
Oh wait. It's lyrics of Nerd Ambition by YTCracker.
Malware: #tinynuke
Payload: coriolis[.]site/facture/
Panel: 4s65xlo930ubyjz8dlcm[.]com/admin/login.php](https://pbs.twimg.com/media/DfpGMmuWAAEzYEn.jpg)
Second stage dropper hosted on: pomf.pyonpyon[.]moe/befqki.doc Find different payload on #opendir: irishlebanese[.]com/wp-admin/images/eight/ It's seen like files aren't on Virus Total, yet. @malwrhunterteam @ViriBack
![Pyv0nix's tweet image. Second stage dropper hosted on: pomf.pyonpyon[.]moe/befqki.doc
Find different payload on #opendir: irishlebanese[.]com/wp-admin/images/eight/
It's seen like files aren't on Virus Total, yet.
@malwrhunterteam @ViriBack](https://pbs.twimg.com/media/Dff0ozCWkAEvrQE.jpg)
![Pyv0nix's tweet image. Second stage dropper hosted on: pomf.pyonpyon[.]moe/befqki.doc
Find different payload on #opendir: irishlebanese[.]com/wp-admin/images/eight/
It's seen like files aren't on Virus Total, yet.
@malwrhunterteam @ViriBack](https://pbs.twimg.com/media/Dff0qA1X4AAsTtT.jpg)
Our Security Research Team has identified a zero-day #vulnerability in Adobe Flash that enables an attacker to execute code on a victims computer. #0day #networksecurity ow.ly/6plP50hBDMp
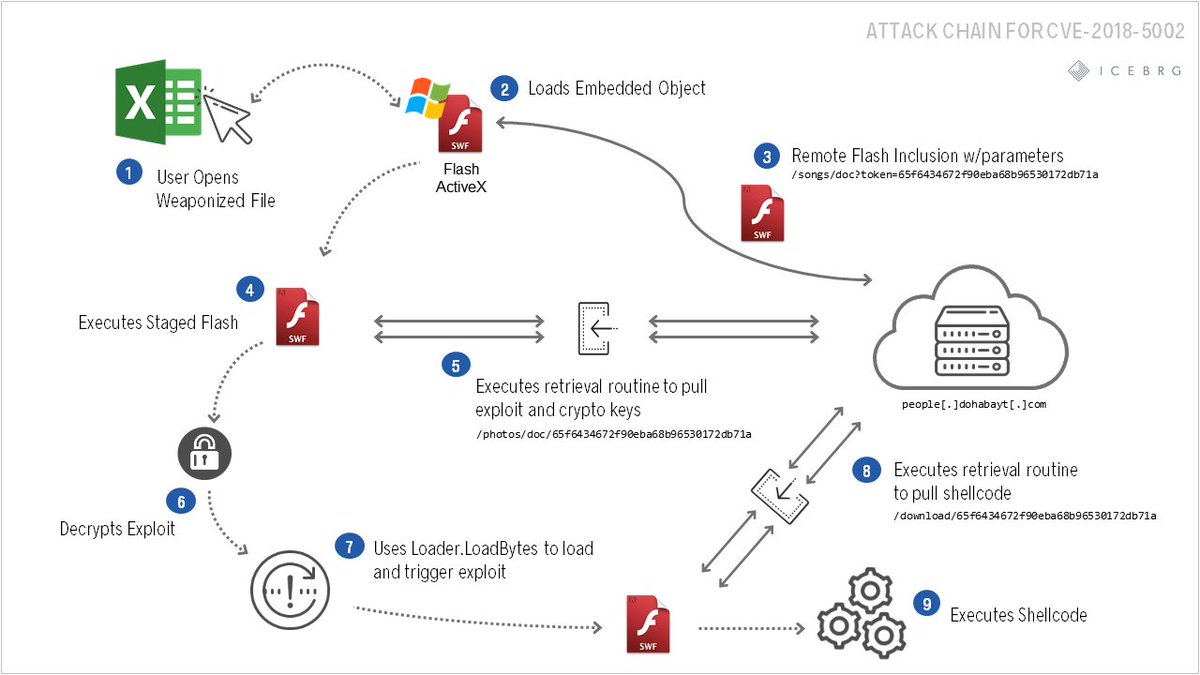
Current wave of #dropper but i'm not sur about the payload... Do you have more info? @malwrhunterteam @James_inthe_box @ViriBack All info: pastebin.com/iQXsPvXR

Today the presentation of my POC: a solution who collect and identify threats ✓ scalable solution ✓ automatically collect links ✓ identify the threat ✓ design a "user friendly" interface Thank to @benkow_ and @ViriBack for them great job who help me for identification


Amazing PO_.doc: RTF HASH: d6122adcf1bc34f293fed334d928f25dda5a76e53226c89a7bdb4c869c734ec8 It's NOT a dropper but an "all inclusive package" with all what he needs Behavior: #Ransomware + #Persistance Request: test1[.]ru/newbuild/t.php (may be a test ?) @malwrhunterteam
![Pyv0nix's tweet image. Amazing PO_.doc: RTF
HASH: d6122adcf1bc34f293fed334d928f25dda5a76e53226c89a7bdb4c869c734ec8
It's NOT a dropper but an "all inclusive package" with all what he needs
Behavior: #Ransomware + #Persistance
Request: test1[.]ru/newbuild/t.php (may be a test ?)
@malwrhunterteam](https://pbs.twimg.com/media/DcQ6MYWWsAABOe6.jpg)
![Pyv0nix's tweet image. Amazing PO_.doc: RTF
HASH: d6122adcf1bc34f293fed334d928f25dda5a76e53226c89a7bdb4c869c734ec8
It's NOT a dropper but an "all inclusive package" with all what he needs
Behavior: #Ransomware + #Persistance
Request: test1[.]ru/newbuild/t.php (may be a test ?)
@malwrhunterteam](https://pbs.twimg.com/media/DcQ6NWBX0AAsyPS.jpg)
![Pyv0nix's tweet image. Amazing PO_.doc: RTF
HASH: d6122adcf1bc34f293fed334d928f25dda5a76e53226c89a7bdb4c869c734ec8
It's NOT a dropper but an "all inclusive package" with all what he needs
Behavior: #Ransomware + #Persistance
Request: test1[.]ru/newbuild/t.php (may be a test ?)
@malwrhunterteam](https://pbs.twimg.com/media/DcQ6N9hW0AUW4SA.jpg)
![Pyv0nix's tweet image. Amazing PO_.doc: RTF
HASH: d6122adcf1bc34f293fed334d928f25dda5a76e53226c89a7bdb4c869c734ec8
It's NOT a dropper but an "all inclusive package" with all what he needs
Behavior: #Ransomware + #Persistance
Request: test1[.]ru/newbuild/t.php (may be a test ?)
@malwrhunterteam](https://pbs.twimg.com/media/DcQ6Op-W4AA8fU7.jpg)
Website compromised: mcts-qatar[.]com Url used for delivering payload: mcts-qatar[.]com/wp-content/plugins/de6.exe Well, it's not your first time: urlhaus.abuse.ch/host/mcts-qata… … May be it's time to upgrade your Wordpress extensions or you deliberately host malware?
Wave of office document. mimetype: RTF Dropper use CVE-2017-11882 with eqnedt32.exe Domain with payload: b.reich[.]io (/jsdrjs.exe or /kdhqfz.png) Paypload: Password Stealer #lokibot Panel: detini.nut[.]cc cc @ViriBack @malwrhunterteam
Malware from: sendspace[.]com/file/6fjyyf He embed and use the @ImminentMethods solution (Cf. official website : imminentmethods.net ). Sample behavior: Keylogging C&C: DUJANADEC.djaoke[.]ga (no reponse) C&C infos :urlquery.net/report/924a8f3…
![Pyv0nix's tweet image. Malware from: sendspace[.]com/file/6fjyyf
He embed and use the @ImminentMethods solution (Cf. official website : imminentmethods.net ).
Sample behavior: Keylogging
C&C: DUJANADEC.djaoke[.]ga (no reponse)
C&C infos :urlquery.net/report/924a8f3…](https://pbs.twimg.com/media/DboBsJTWkAAFI3D.jpg)
Dropper dowload payload from @github : github[.]com/yeahtheboys19892/beets/raw/master/beets/bin.exe Payload: AutoIT Keylogger Hash: 49475fa8074b25cd6aeb06551fa1f8544cdbc90e8d479858802a6510bb205d67 Behavior: drop 'nthwytulqctogyqrypoegivdc1696780.png'
United States Trendy
- 1. Vandy 10.4K posts
- 2. Brian Kelly 4,970 posts
- 3. No Kings 933K posts
- 4. Diego Pavia 3,242 posts
- 5. Vanderbilt 8,152 posts
- 6. Clark Lea N/A
- 7. Dork Cult Protest Day 40.8K posts
- 8. Nuss 3,314 posts
- 9. Beamer 2,457 posts
- 10. #GoBlue 2,520 posts
- 11. Tony Vitello 2,171 posts
- 12. South Carolina 11K posts
- 13. Joe Sloan 1,002 posts
- 14. Shula 2,122 posts
- 15. Duke 69K posts
- 16. Tulane 1,874 posts
- 17. Arsenal 158K posts
- 18. Georgia Tech 4,734 posts
- 19. Sellers 10K posts
- 20. Demond 1,316 posts
Może Ci się spodobać
Something went wrong.
Something went wrong.