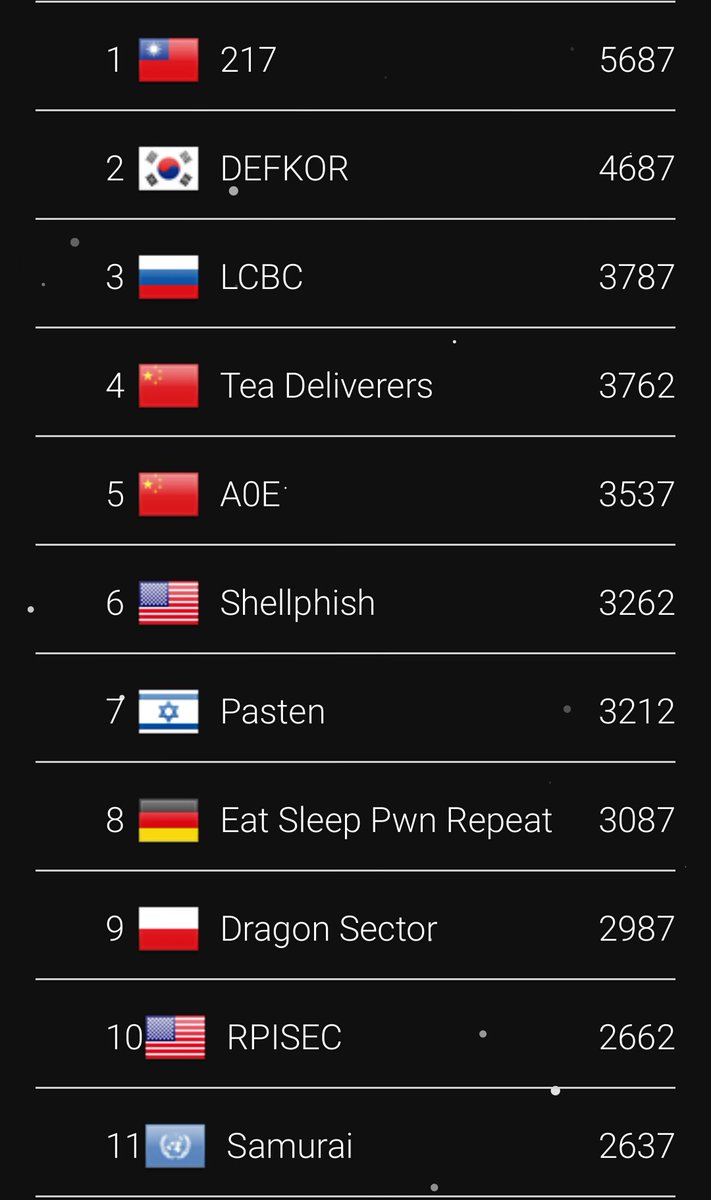
#plaidctf search results
New article: Exploiting a Single Null-Byte Overflow on the Heap. #Villoc #PlaidCTF #PlaidDB wapiflapi.github.io/2015/04/22/sin…

Demo: my new heap visualisation tool working on my exploit for #PlaidCTF 's PlaidDB: ctl.ovh/wapiflapi/plai… Try it.

Commented exploit for "roll a d8" from #plaidctf (N-day exploit for a v8 vuln): gist.github.com/saelo/52985fe4… Really fun bug and a great challenge to get started with JS engine exploitation. Thanks @PlaidCTF :)
Tenho que admitir, nunca imaginei que jogar o #PlaidCTF seria tão divertido. Recomendo a todos ! play.plaidctf.com

#PlaidCTF 2016 Pwnable 600 - Awkward Writeup dougallj.wordpress.com/2016/04/18/pla… #PCTF2016
dougallj.wordpress.com
PlaidCTF 2016 – Awkward [Pwnable 600]
Awkward was an exploitation challenge, providing a pretty serious “awk” like interpreter, with a variety of different bugs. I used IDA and Hex-Rays extensively to reverse it. After a bi…
(Quite) all CTF files from #plaidctf: ctf.plaidctf.com/media/pctf_fil…
せっかくなので、忘れないうちに…… #PlaidCTF Plaid CTF 2016 tonnerre writeup: gist.github.com/Bono-iPad/124e…
#PlaidCTF – giga (Crypto 250): r3dey3.com/2013/04/plaid-…
#PlaidCTF Just started :) Welcome to 48 hours of #Funtimes and frowns. "I like to MV it, MV it" @PlaidCTF #CTF

Quick'n'dirty #plaidctf Arduino reversing write-up: http://www.limited-entropy.com/docs/pctf/writeup/rev350/reversing350.txt
#PlaidCTF 2013 Writeups Collection: devpsc.blogspot.fr/2013/04/plaid-…
#NFLabs のエンジニアが、NTT グループの有志とともに Team Enu として、#PlaidCTF 2024 に出場しました。 Team Enu は 6 つのフラグを獲得し、27 位でした。 plaidctf.com

Upsolved single crypto chall: choreography. Appeared at #PlaidCTF 2022. Writeup: github.com/pcw109550/writ…
CTF Challenges of the Week PlaidCTF: github.com/sajjadium/ctf-… HackPack: github.com/sajjadium/ctf-… UMDCTF: github.com/sajjadium/ctf-… GLSC: github.com/sajjadium/ctf-… @PlaidCTF @HackPackCTF @kapravel @umdcsec #PlaidCTF #hackpack #UMDCTF #CTFtime #CaptureTheFlag #CTF #Pwn
I only managed to solve Leaky Block Cipher during #PlaidCTF. I am so weak... mystiz.hk/posts/2021-04-…
Miserably failing at "Secure OCAML sandbox" challenge from #plaidCtf. Btw, I never touched Ocaml so it's a good crash course 😂
Our (@pastenctf ) last #plaidctf write-up is up: Mooz Chat. kernel (which doesn't have a Twitter handle) is responsible for almost everything, I'm responsible for the tiny Diffie-Hellman part at the end. Have fun! github.com/koolkdev/ctf-w…
I got bored so I solved #plaidctf #mojo after-the-fact. Thanks @yoavalon for the tip: RenderFrameHost being used with an unowned pointer :-) It's pretty unreliable, but you do get the flag after a few runs: github.com/oranav/ctf-wri…
I publish a post about the web challange Catalog in #PlaidCTF in Chinese. If you can't read it, the author of Catalog says it will be a writeup in this weekend and you can wait for it. blog.zeddyu.info/2020/04/24/Pla…
Just got my writeup for #PlaidCTF 's mojo chromium pwn challenge up. First time to Chromium. Didn't solve it in time through. Tried my best to make the writeup helpful for anyone new to Chromium like myself. Enjoy. trungnguyen1909.github.io/blog/post/Plai…
Pwn challenges for PlaidCTF 2020 (ctftime.org/event/936): gitlab.com/sajjadium/CTFi… bitbucket.org/sajjadium/ctfi… github.com/sajjadium/CTFi… @PlaidCTF @CTFtime #PlaidCTF #PlaidCTF2020 #CTFtime #CTF #Pwn
Without further ado, here's my #PlaidCTF #sandybox write-up: github.com/oranav/ctf-wri…
About #MoozChat #plaidctf #pctf2020 #pctf I got RCE using XFF under nsjail. I think that to get a first flag, leak $JWT_KEY and construct JWT with username=“tomnook”, is it right?
How about using #:~:text=flag{this_is_a_flag} and onscroll to leak data?
Cracked two Crypto challs: MPKC, dyrpto #PlaidCTF Writeup: github.com/pcw109550/writ…
Os dejo por aquí el #writeup del reto golf.so del #PlaidCTF 2020: devploit.dev/2020/04/19/pla…
MSAgentDataSpecification_v1_3.htm Fuck my life... #plaidctf
New article: Exploiting a Single Null-Byte Overflow on the Heap. #Villoc #PlaidCTF #PlaidDB wapiflapi.github.io/2015/04/22/sin…

#NFLabs のエンジニアが、NTT グループの有志とともに Team Enu として、#PlaidCTF 2024 に出場しました。 Team Enu は 6 つのフラグを獲得し、27 位でした。 plaidctf.com

Demo: my new heap visualisation tool working on my exploit for #PlaidCTF 's PlaidDB: ctl.ovh/wapiflapi/plai… Try it.

New article: Exploiting a Single Null-Byte Overflow on the Heap. #Villoc #PlaidCTF #PlaidDB wapiflapi.github.io/2015/04/22/sin…

Tenho que admitir, nunca imaginei que jogar o #PlaidCTF seria tão divertido. Recomendo a todos ! play.plaidctf.com


Something went wrong.
Something went wrong.
United States Trends
- 1. Wirtz 43.6K posts
- 2. Elander 3,077 posts
- 3. Tosin 8,154 posts
- 4. $TSLA 43.6K posts
- 5. Ajax 68.9K posts
- 6. Danny White 2,628 posts
- 7. Estevao 26.4K posts
- 8. Tony Vitello 12K posts
- 9. Caicedo 18K posts
- 10. East Wing 141K posts
- 11. #YesOnProp50 6,196 posts
- 12. SNAP 662K posts
- 13. Atalanta 12K posts
- 14. Ekitike 23.4K posts
- 15. Frankfurt 46.2K posts
- 16. Juve 17.5K posts
- 17. Frank Anderson N/A
- 18. Hamburger Helper N/A
- 19. Vini 19.3K posts
- 20. Enzo 28.5K posts