BinaryChunk
@BinaryChunk
Security Reseacher
Exciting update on Project Zero’s LLM research: googleprojectzero.blogspot.com/2024/10/from-n…
How do you explain to normal people that modern exploits are actual pieces of art?
An Introduction to Chrome Exploitation - Maglev Edition :: — uf0 matteomalvica.com/blog/2024/06/0…
My new Project Zero blog post, Driving Forward in Android Drivers is live! 🥳 googleprojectzero.blogspot.com/2024/06/drivin…
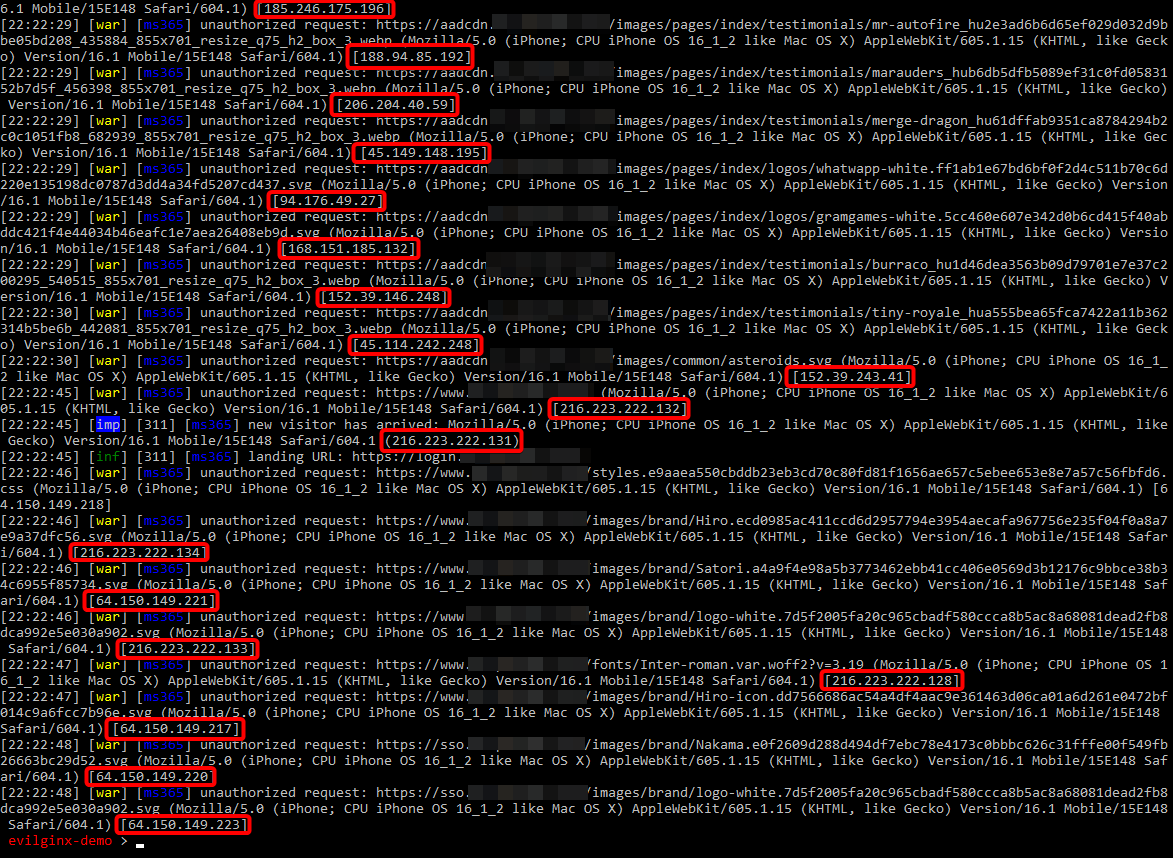
This screenshot shows how external bots try to scan a phishing page, hosted by Evilginx Pro. Every request is made from a different IP address, which ultimately proves that IP blacklisting is dead as a method to block scanners. JA4 & browser telemetry analysis is the way to go.
Exciting news! 🚀 Just dropped my blogpost unveiling the universal Linux kernel LPE PoC for CVE-2024-1086 (working on v5.14 - v6.7) used for pwning Debian, Ubuntu, and KernelCTF Mitigation instances, including novel techniques like Dirty Pagedirectory 🧵 pwning.tech/nftables
We've started a blog series on N-day full chain exploits. The first part is about chrome renderer exploit, CVE-2023-3079. Check it now!👇👇 blog.theori.io/chaining-n-day… #Theori #티오리 #Blog #Research #Fermium252 #Chrome #VirtualMachine #CVE #Vulnerability
Do you use a virtual machine to browse dangerous links safely? If you use the Chrome browser inside that virtual machine, is it secure enough? As you might have guessed, the answer is not so much. We chained six unique CVEs from 2023 listed below. • Chrome Renderer RCE :…
In this post I'll use CVE-2023-6241, a vulnerability in the Arm Mali GPU that I reported last November to gain arbitrary kernel code execution from an untrusted app on a Pixel 8 with MTE enabled. github.blog/2024-03-18-gai…
Chrome sandbox escape abusing Liftoff assembly by @r3tr074 retr0.zip/blog/abusing-L… #chrome #infosec

ptrace, mmap and the clone system calls for process injection in Linux Credits @BinaryChunk mutur4.github.io/posts/linux-ma… #Linux #infosec


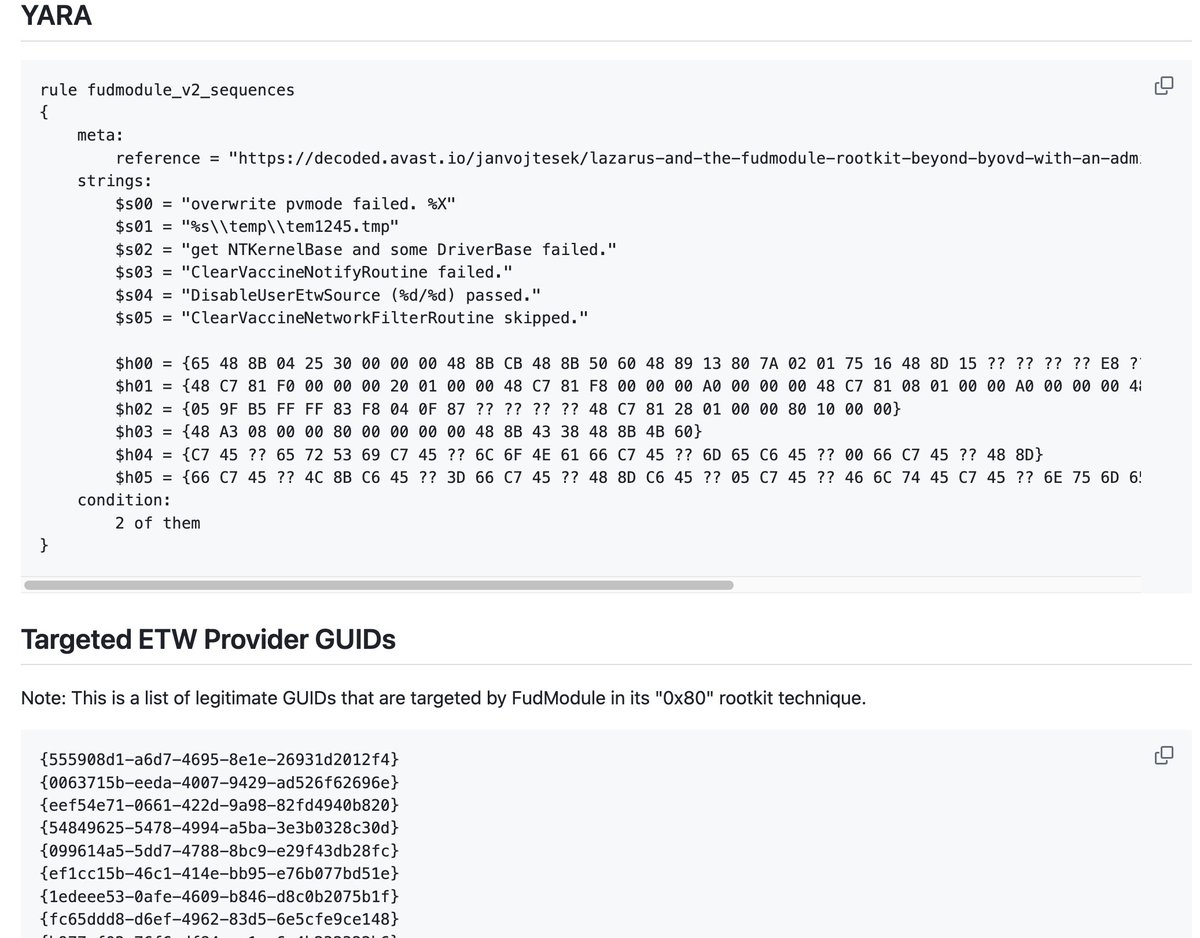
#Lazarus exploited a flaw in the Windows AppLocker driver (appid.sys) as a zero-day to gain kernel-level access and turn off security tools.CVE-2024-21338 Beyond BYOVD with an Admin-to-Kernel Zero-Day decoded.avast.io/janvojtesek/la…
(CVE-2023-6702)[1501326][$16000][promises, async stack traces]Type Confusion in V8 is now open with a PoC: issues.chromium.org/issues/40941600 This vulnerability has existed since the `Promise.any` function was introduced. chromium-review.googlesource.com/c/v8/v8/+/2198… PoC: ./d8 poc.js issues.chromium.org/action/issues/…
![xvonfers's tweet image. (CVE-2023-6702)[1501326][$16000][promises, async stack traces]Type Confusion in V8 is now open with a PoC:
issues.chromium.org/issues/40941600
This vulnerability has existed since the `Promise.any` function was introduced.
chromium-review.googlesource.com/c/v8/v8/+/2198…
PoC:
./d8 poc.js
issues.chromium.org/action/issues/…](https://pbs.twimg.com/media/GG9iaGsWEAAZTfX.jpg)
CVE-2023-6702: Type Confusion in V8(CaptureAsyncStackTrace). [1501326]Fix the case when the closure has run We were using the closure pointing to NativeContext as a marker that the closure has run, but async stack trace code was confused about it. chromium.googlesource.com/v8/v8.git/+/bd…
Short blog post introducing how to add psuedo-syscalls and struct definitions to Syzkaller for Linux kernel vulnerability research Credits @notselwyn pwning.tech/ksmbd-syzkalle… #Linux #cybersecurity



💫 Here are my slides from my @BSidesNairobi : "From Likes To Leaks" 💫. Solving the ‘hack my boyfriend’s WhatsApp’ question canva.com/design/DAFzbnj…
canva.com
From Likes to Leaks
Check out this Presentation designed by Charles.
Linux Process Injection: Emulating the Windows VirtualAllocEx and CreateRemoteThread to inject into a Linux Firefox process. mutur4.github.io/posts/linux-ma…
Reverse Engineering a tcpip.sys DOS Vulnerability
Releasing my new project to the public. "Mshikaki" is a shellcode injector that utilizes APC injection, XOR encryption, remote/on-disk shellcode loading, arbitrary process injection, and can bypass AMSI. github.com/trevorsaudi/Ms…
Linux Kernel Exploit (CVE-2022–32250) with mqueue An article about exploit a slab use-after-free bug in the netfilter subsystem. blog.theori.io/linux-kernel-e…
theori.io
Linux Kernel Exploit (CVE-2022–32250) with mqueue - Theori BLOG
We exploited CVE-2022-32250, a use-after-free vulnerability in Linux Netfilter, to achieve root on Ubuntu 22.04. Learn how we bypassed KASLR and modified modprobe_path. | Vulnerability Research
United States Trends
- 1. Jonathan Taylor 20.1K posts
- 2. Bills 112K posts
- 3. Falcons 31K posts
- 4. Colts 51.7K posts
- 5. Diggs 6,275 posts
- 6. Browns 22.6K posts
- 7. Kyle Williams 5,097 posts
- 8. Daniel Jones 9,958 posts
- 9. Joe Brady 1,716 posts
- 10. Jaxson Dart 3,390 posts
- 11. Penix 10.8K posts
- 12. Parker Washington 2,712 posts
- 13. Dillon Gabriel 1,414 posts
- 14. #Bears 3,199 posts
- 15. Drake Maye 6,412 posts
- 16. Liverpool 221K posts
- 17. Starks 1,996 posts
- 18. Max B 25.3K posts
- 19. #NYGiants 1,938 posts
- 20. #DawgPound 1,632 posts
Something went wrong.
Something went wrong.