0x1CE
@BugAbuse
*** NOTHING TO SEE HERE - CARRY ON *** 👾
You might like
🚨BREAKING: We uncovered LANDFALL — a commercial-grade Android spyware exploiting a now-patched Samsung zero-day (CVE-2025-21042) through weaponized DNG images sent via WhatsApp, enabling zero-click compromise of Samsung Galaxy devices. 1/ unit42.paloaltonetworks.com/landfall-is-ne…
CNCERT confirms Operation Triangulation attacks on Chinese orgs and connects it to NewDSZ - the implant we discovered and analyzed in 2023 mp.weixin.qq.com/s/XPjT0BVOJPJx…
Great work @_CPResearch_!
Zero-Day used by Stealth Falcon APT group in a spear-phishing campaign: 💥 .URL file exploitation (assigned CVE-2025-33053) 🧰 Custom Mythic implants, LOLBins, and custom payloads 🌍 High-profile targets across the Middle East and Africa research.checkpoint.com/2025/stealth-f…
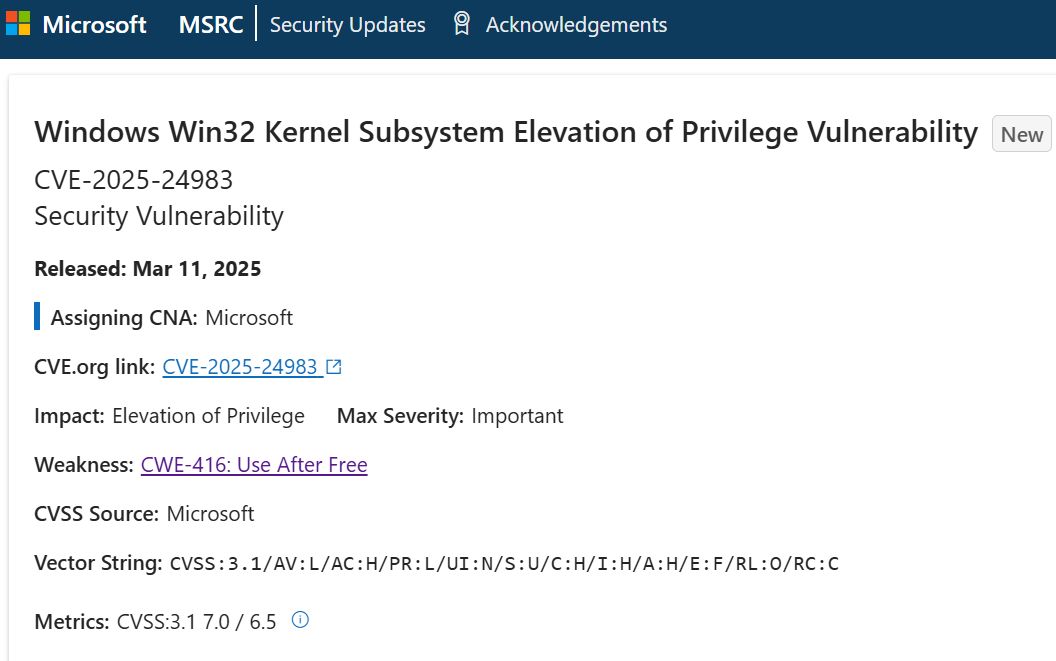
#ESETresearch has discovered a zero day exploit abusing #CVE-2025-24983 vulnerability in Windows Kernel to elevate privileges (#LPE). First seen in the wild in March 2023, the exploit was deployed through #PipeMagic backdoor on the compromised machines. 1/4
#PIVOTcon25 #CfP is open and you can submit your proposals till 7 FEB 2025 Remember - one track,30m - no recording/streaming/tweeting. U should feel comfy to share more - No TLP:WHITE - Original content only Let us guide u through with a little meme-thread #CTI #ThreatIntel 1/10

#ESETresearch reveals the first Linux UEFI bootkit, Bootkitty. It disables kernel signature verification and preloads two ELFs unknown during our analysis. Also discovered, a possibly related unsigned LKM – both were uploaded to VT early this month. welivesecurity.com/en/eset-resear… 1/5
.@Volexity’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target, while the attacker was halfway around the world. volexity.com/blog/2024/11/2… #dfir
Issue #4 is out – enjoy! pagedout.institute/?page=issues.p… Please RT and tell your friends :)

#ESETresearch has discovered the Lunar toolset, two previously unknown backdoors (which we named #LunarWeb and #LunarMail) possibly linked to Turla, compromising a European MFA and its diplomatic missions abroad. welivesecurity.com/en/eset-resear… 1/6
❤️🔥!! CALL FOR PAPERS !! ❤️🔥 Submission Deadline: June 21, 2024 - Talks are 20 minutes long + 5 minutes for Q&A - Workshops are 90 minutes long. LABScon is primarily a threat intelligence and vulnerability research conference but we keep an open-mind. CFP is live:…
Thanks to marcan (social.treehouse.systems/@marcan/111655…) and @zhuowei (x.com/zhuowei/status…) now we know the original purpose for this unknown hardware feature. Its MMIO debug registers for GPU L2 cache. I am really excited that we are very close to solving this mystery!
We're revealing details of an obscure debugging feature in the Apple A12-A16 SoC’s that bypasses all of the hard-to-hack hardware-based memory protections on new iPhones. Its not used by the firmware and we don't know how the attackers found out about it. securelist.com/operation-tria…
The recording of our (me, @bzvr_, @kucher1n) #37c3 talk “Operation Triangulation: What You Get When Attack iPhones of Researchers” was published! media.ccc.de/v/37c3-11859-o…

media.ccc.de
Operation Triangulation
Worst rebranding of the year Microsoft APT rebranding

What’s the worst rebranding this year? I’ll go first… Azure AD > Entra ID🤦🏻♂️
During routine monitoring of suspicious activities on the systems of high-profile customers, #ESETresearch discovered a sophisticated and previously undocumented #StealthFalcon backdoor that we named #Deadglyph. welivesecurity.com/en/eset-resear…
Our research on Tick APT group is out! 👇
#ESETResearch discovered an attack by APT group Tick against a data-loss prevention (DLP) company in East Asia and found a previously unreported tool used by the group. welivesecurity.com/2023/03/14/slo… @0xfmz 1/6
More 0day in the wild, this time from North Korea targeting Internet Explorer from @_clem1 and @benoitsevens in TAG. Yes IE exploits still work in 2022! blog.google/threat-analysi… Targets seem to be N. Korean defectors and human rights activists and South Korean journalists.
#ESETesearch discovered Dolphin, a sophisticated backdoor extending the arsenal of the #ScarCruft APT group. Dolphin has a wide range of spying capabilities and is deployed on selected targets only. welivesecurity.com/2022/11/30/who… 1/6
#BREAKING #ESETresearch helped analyze a #Sandworm campaign against an energy company in #Ukraine 🇺🇦 using #CaddyWiper and a new version of the infamous #Industroyer malware. #WarInUkraine welivesecurity.com/2022/04/12/ind… 1/5
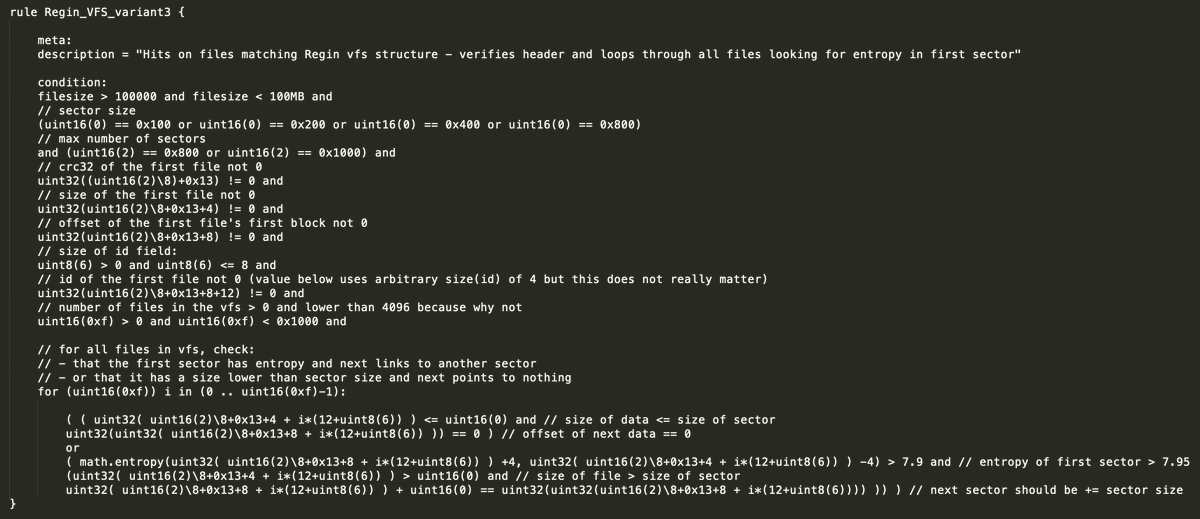
Time to chip in for #100DaysofYARA, this rule is a (fun) example that looks for a structure (#Regin VFS) instead of data. Structures (often config) are useful to validate your understanding of malware functionality and for more resilient rules. But be careful with boundaries :)
Today we're publishing a detailed technical writeup of FORCEDENTRY, the zero-click iMessage exploit linked by Citizen Lab to the exploitation of journalists, activists and dissidents around the world. googleprojectzero.blogspot.com/2021/12/a-deep…
United States Trends
- 1. Duke N/A
- 2. #JustinStrong N/A
- 3. #SmackDown N/A
- 4. Mensah N/A
- 5. Tony Blair N/A
- 6. #LightningStrikes N/A
- 7. Roger Waters N/A
- 8. Andor N/A
- 9. Panarin N/A
- 10. Providence N/A
- 11. Bichette N/A
- 12. SMITH HOCKEY N/A
- 13. Ryan Air N/A
- 14. Jamier Jones N/A
- 15. Phillies N/A
- 16. #drwfirstgoal N/A
- 17. Vincent Price N/A
- 18. Real ID N/A
- 19. Kit Wilson N/A
- 20. Baty N/A
Something went wrong.
Something went wrong.