Adrien B
@Int2e_
Malware research and threat intel ex #DFIR responder at @Mandiant
You might like
🚨BREAKING: We uncovered LANDFALL — a commercial-grade Android spyware exploiting a now-patched Samsung zero-day (CVE-2025-21042) through weaponized DNG images sent via WhatsApp, enabling zero-click compromise of Samsung Galaxy devices. 1/ unit42.paloaltonetworks.com/landfall-is-ne…
Someone's really having a lot of fun with DNG. Another (!) DNG vuln patched in 2025-10 Samsung update. Google TAG assesses surveillance vendors may have been aware of this vuln (though not presently clear if deployed ITW or not) project-zero.issues.chromium.org/issues/4424237…
We really should be talking about this more....KASLR is just not working properly on Android right now, and it hasn't for a long time. googleprojectzero.blogspot.com/2025/11/defeat…
A recent analysis revealed MystRodX, a sophisticated C++ backdoor, employing dual-mode activation and advanced encryption, has been lurking undetected since 2024, posing a significant threat to network security. #MystRodX #CyberSecurity ift.tt/8vtwxFQ
Meta and Russian Yandex engaged in unprecedented internet tracking practices, likely illegal with EU data protection law. Companies designed tracking systems that exploited Android's localhost socket permissions to create covert communication channels between websites and native…




The Microsoft Threat Intelligence Center (MSTIC) is looking for malware reverse engineers and security researchers to join our team! Come join our brilliant, world-class team of malware REs and intelligence researchers: Principal Security Researcher (United States):…
Based on our findings and those reported by governments and other security vendors, Microsoft Threat Intelligence assesses the Russian nation-state actor we track as Secret Blizzard has used the tools and infrastructure of at least 6 other threat actors during the past 7 years.
Microsoft identified multiple vulnerabilities in the open-source platform OpenVPN, integrated into millions of devices worldwide, which could be exploited to create an attack chain allowing remote code execution (RCE) and local privilege escalation (LPE). msft.it/6014llDIQ
We are looking for a strategic threat intel analyst to join @ESETresearch. Interested in cyber-espionage and geopolitics? Apply! ca.linkedin.com/jobs/view/anal…
linkedin.com
1,000+ Intelligence Officer jobs in United States (30 new)
Today’s top 1,000+ Intelligence Officer jobs in United States. Leverage your professional network, and get hired. New Intelligence Officer jobs added daily.
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack. The issue has been identified, isolated and a fix has been deployed. We…
Welcome to the future of YARA: virustotal.github.io/yara-x/blog/ya…
virustotal.github.io
YARA is dead, long live YARA-X
For over 15 years, YARA has been growing and evolving until it became an indispensable tool in every malware researcher’s toolbox.
Trend Micro's Christopher So looks into two techniques used by Earth Freybug (a subset of APT41) in the UNAPIMON malware: dynamic-link library hijacking & application programming interface (API) unhooking to prevent child processes from being monitored. trendmicro.com/en_us/research…
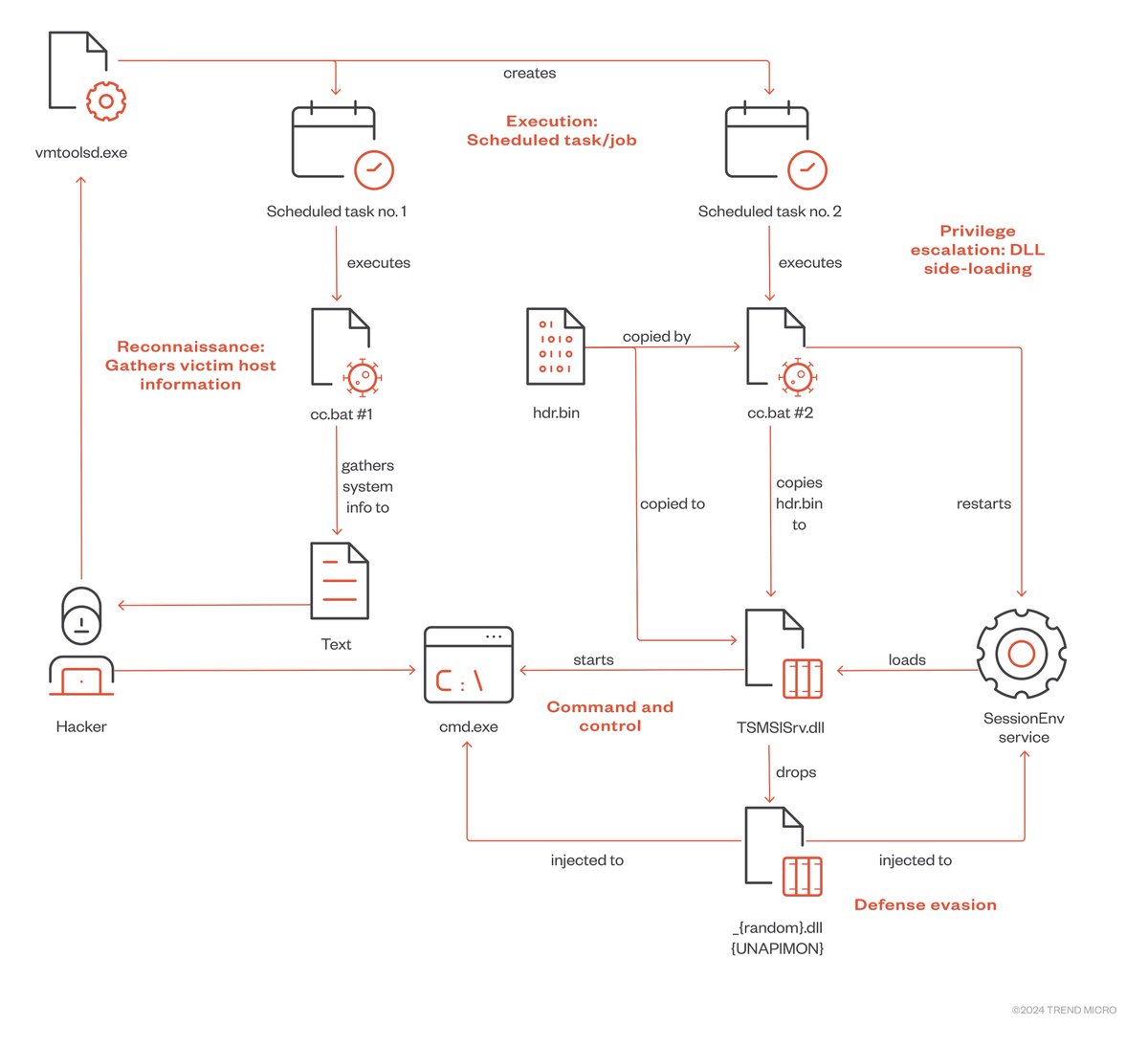
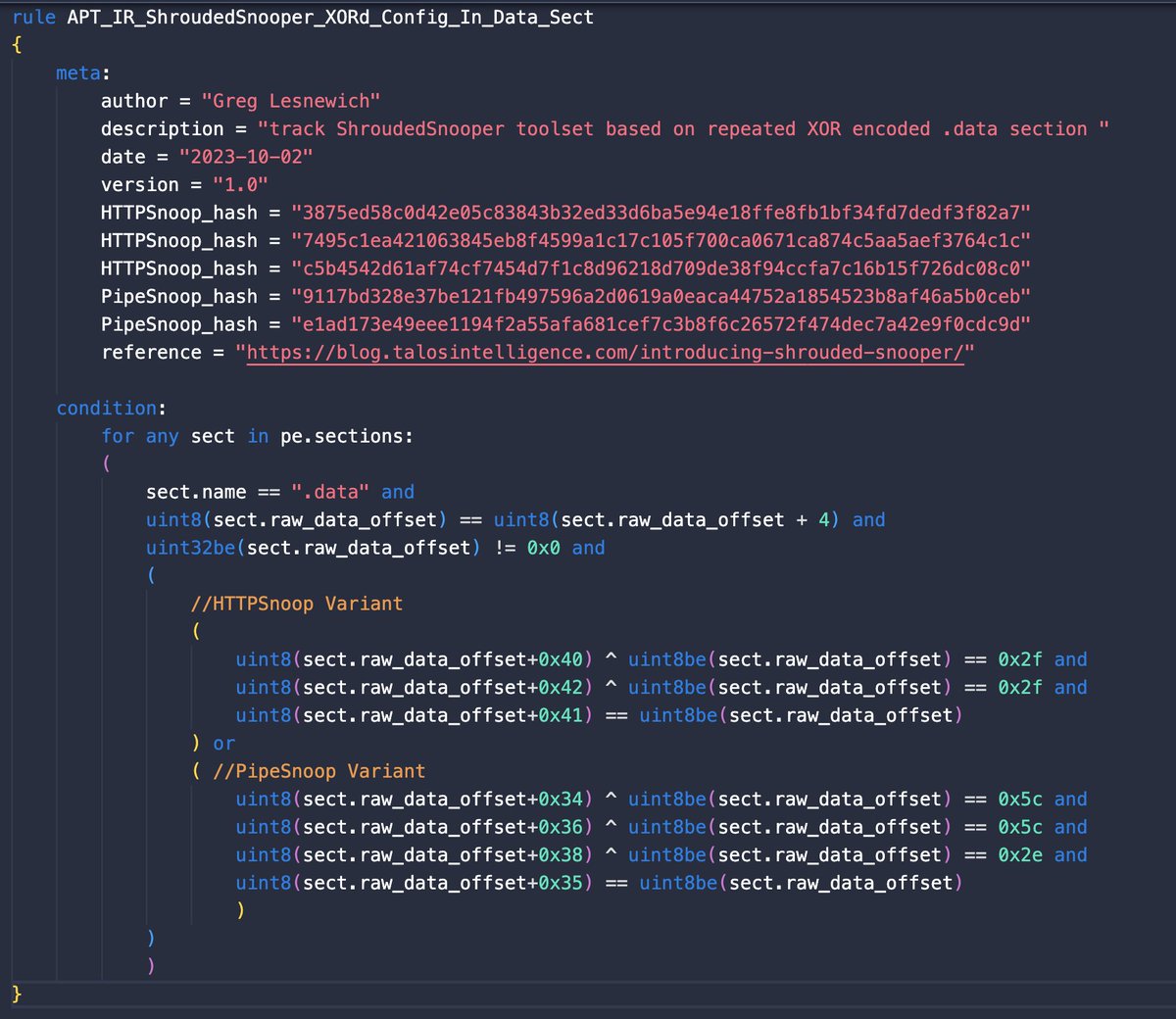
#100DaysofYARA Day 07 - another condition only rule this time looking for the HTTPSnoop and PipeSnoop families found by Talos a little avant garde, but both store config info in the .data section, XOR'd with a 1 byte key following the same structure github.com/100DaysofYARA/…

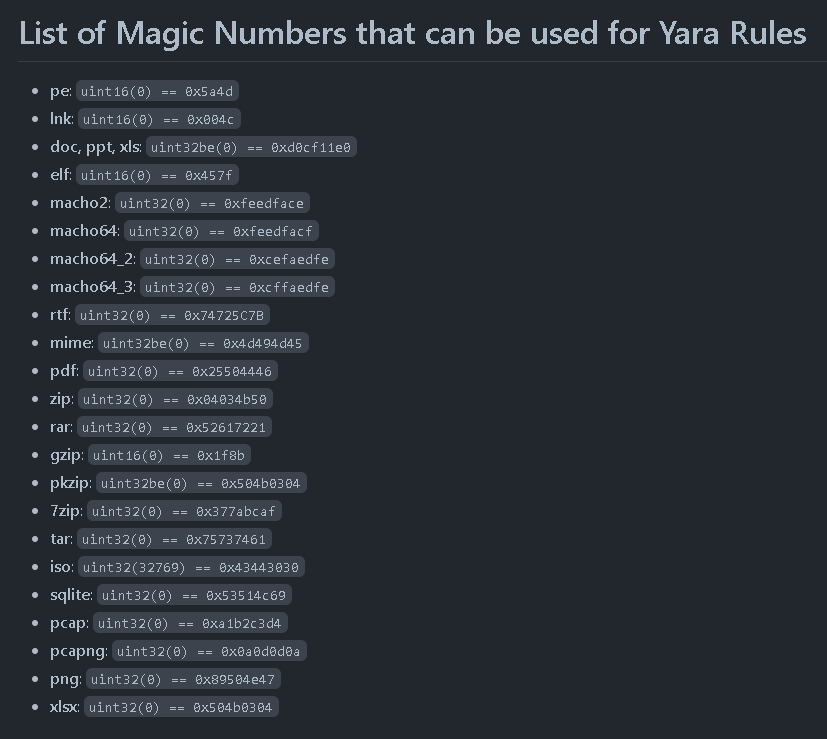
#100DaysOfYara Day 6: Yara can be used to access specific data at a given position. 👇 This feature is often used to identify Magic Numbers (used to determine the file format) to match your rule against a specific file type, such as a PE (0x4D5A), for example. Today, no…
#100DaysofYARA Day 6 sometimes our pals in TA404/Zinc/Temp.HERMIT/Diamond Sleet reuse export names and add a dubya ("W") to the end of the second name. lets create a loose rule looking for duplicates like that! Examples in the second pic thanks to Ronnie Coleman
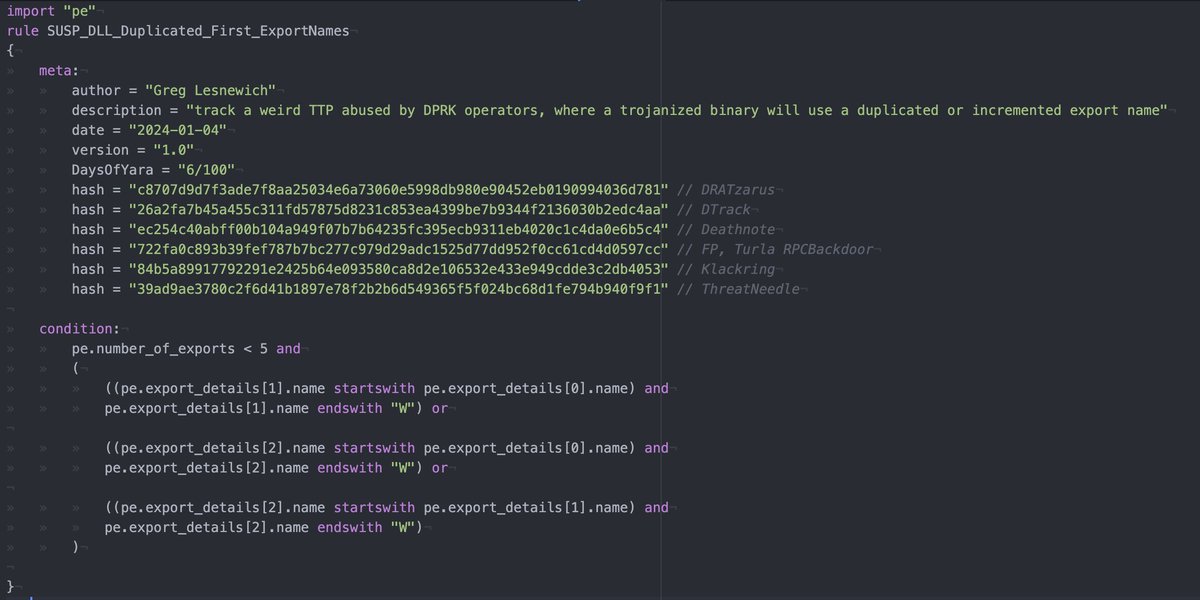
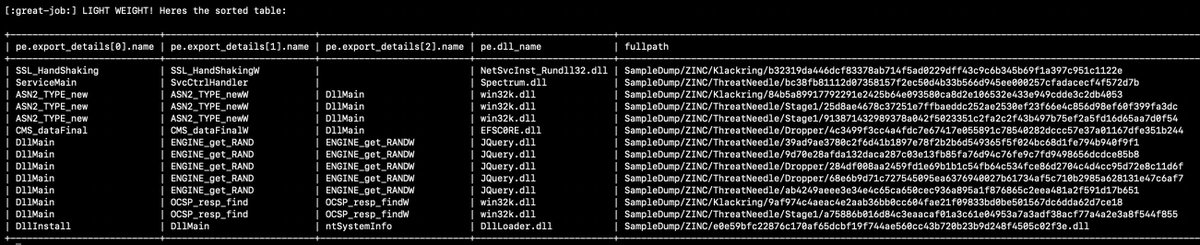
[1/4] Joined by @vmptrst (@PwC) and @MsftSecIntel, we release attribution information on the Sandman #APT, first revealed at @labscon_io '23. Link 👇 s1.ai/LuaDream
Microsoft has uncovered a supply chain attack by North Korean threat actor Diamond Sleet (ZINC) involving the modification of an installer file from software maker CyberLink. The payload calls back to attacker infrastructure for instructions. Learn more: msft.it/6013iHoQF
Teaser: we're working on a new #YARA module to enhance in-memory matching, allowing detection engineers to craft more precise rules. Stay tuned

A few weeks ago I was honored to speak at @labscon_io . Great people, great talks, great venue. I honestly could not suggest any improvements except something closer to CET timezone!
United States Trends
- 1. Texans 27K posts
- 2. Ray Davis 1,503 posts
- 3. #MissUniverse 89.9K posts
- 4. Davis Mills 2,414 posts
- 5. Josh Allen 11.7K posts
- 6. James Cook 4,521 posts
- 7. #TNFonPrime 1,626 posts
- 8. Nico Collins 1,451 posts
- 9. Christian Kirk 2,881 posts
- 10. Cole Bishop N/A
- 11. Taron Johnson N/A
- 12. Sedition 240K posts
- 13. Will Anderson 2,951 posts
- 14. Shakir 3,469 posts
- 15. Woody Marks 2,332 posts
- 16. #htownmade 1,525 posts
- 17. #BUFvsHOU 1,805 posts
- 18. Prater N/A
- 19. Treason 128K posts
- 20. Al Michaels N/A
You might like
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Dan Perez
Dan Perez
@MrDanPerez -
 nick
nick
@3dRailForensics -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Ramin Nafisi
Ramin Nafisi
@MalwareRE -
 Tyler McLellan
Tyler McLellan
@tylabs -
 Rufus
Rufus
@rufusmbrown -
 avallach (@[email protected])
avallach (@[email protected])
@xorhex -
 Matthew Dunwoody
Matthew Dunwoody
@matthewdunwoody -
 Daniel Lunghi
Daniel Lunghi
@thehellu -
 __mat__
__mat__
@matthieu_faou -
 Aaron Stephens
Aaron Stephens
@x04steve -
 French
French
@notareverser -
 ⚛️ Marcin Siedlarz
⚛️ Marcin Siedlarz
@siedlmar -
 Johnk3r
Johnk3r
@johnk3r
Something went wrong.
Something went wrong.