Dark@Joker:~$
@ExploitNest
CRTA | CAP | OSCP (Aspirant) - Pentration Tester & Bug Hunter - Red Teamer 🤡
قد يعجبك
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

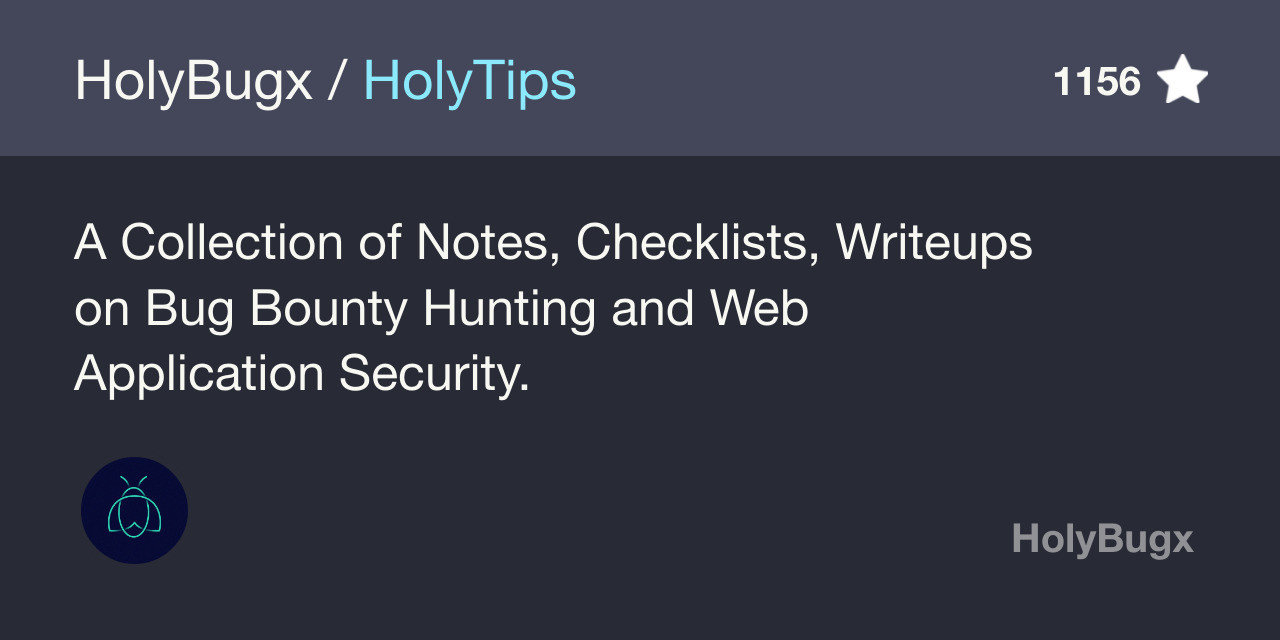
This is a nice resource on Bug Bounty notes and checklists: github.com/HolyBugx/HolyT…
Full Web App Checklist : 📓 - blog.hackxpert.com/2024/02/web-ap… #infosec #cybersec #bugbountytips

30 low-high level honeypots in a single PyPI package github.com/qeeqbox/honeyp…

DAY 28/365 Tip : Modify account email to "[email protected]", application says "Email already registered"... Bypass using dot-notation ( this is where the vuln showed itself to me, haha ) Instead of using "[email protected]", try "[email protected]" ( with this…

Deep dive into Android Pentesting Covered everything from static & dynamic analysis, Frida, Drozer, SSL pinning bypass,and more If you're into mobile security, this one's packed with real-world scenarios & tools #mobilesecurity #androidapptesting coal-memory-97b.notion.site/Android-Pentes…
Cloudflare has started blocking proxy tools like Burp Suite. If you encounter this error, download the “Bypass Bot Detection” extension from the BApp Store in Burp Suite. It should resolve the issue for Burp Suite.

Nobody can memorize all XXE payloads/vectors. Use this payload list when testing for XXE vulnerabilities: github.com/payloadbox/xxe…
location-based WAF bypass techniques Tag Blending: <Svg OnLoad= location=textContent>JavaS<a>cript:al<a>ert(<a>1)// Template Literals: <Svg OnLoad= location=`Java${/S/.source}cript:alert${"\50"}1)`> Credit - @BRuteLogic
📂 Target: robots.txt + sitemap.xml 👀 What to look for: /admin_old/ /staging/ /backup/ Hidden API routes .env, .git, .bak files 🎯 Use found paths in: Fuzzing Bruteforce Hidden login discovery
Ultimate Reconnaissance + Port Mapping Methodology (Advanced) 1. Enumerate all the domains+subdomains `$ amass enum -ip -d <domain>` 2. Extract the hosts from the Amass file, to create a file named hosts-amass.txt. `$ cat amass_output/amass.txt | cut -d']' -f 2 | awk…
![TheMsterDoctor1's tweet image. Ultimate Reconnaissance + Port Mapping Methodology (Advanced)
1. Enumerate all the domains+subdomains
`$ amass enum -ip -d &lt;domain&gt;`
2. Extract the hosts from the Amass file, to create a file named hosts-amass.txt.
`$ cat amass_output/amass.txt | cut -d']' -f 2 | awk…](https://pbs.twimg.com/media/GoUWKW3XgAAtFWw.jpg)
United States الاتجاهات
- 1. Merry Christmas 432K posts
- 2. Pro Bowl 31.7K posts
- 3. Ryan O'Hearn 1,644 posts
- 4. Kam Williams N/A
- 5. Ben Sasse 3,574 posts
- 6. Happy Holidays 116K posts
- 7. Bellarmine N/A
- 8. Semenyo 75.3K posts
- 9. Pirates 24.3K posts
- 10. Steve Rogers 22.8K posts
- 11. Louisville 5,062 posts
- 12. Because Chicago 1,056 posts
- 13. Lookman 12.3K posts
- 14. #Fliffmas 2,701 posts
- 15. Neymar 21.6K posts
- 16. Russell Brand 13.2K posts
- 17. Happy Festivus 4,811 posts
- 18. Toledo 7,053 posts
- 19. Captain America 7,392 posts
- 20. Iwobi 9,267 posts
قد يعجبك
Something went wrong.
Something went wrong.