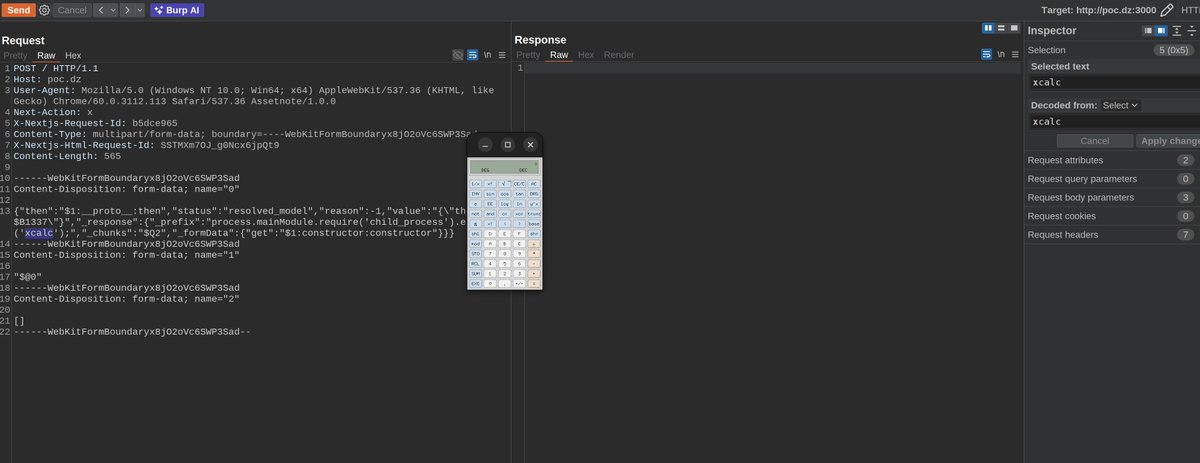
#react2shell نتائج البحث
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

🚨 Censys on #React2Shell (CVE-2025-55182): We observe ~2.15M exposed web services running Next.js or other RSC-based frameworks—mostly in the U.S. and China. Not all are vulnerable, but active exploitation is underway. Patch now. 👉 Full advisory: hubs.ly/Q03X5QFV0

just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
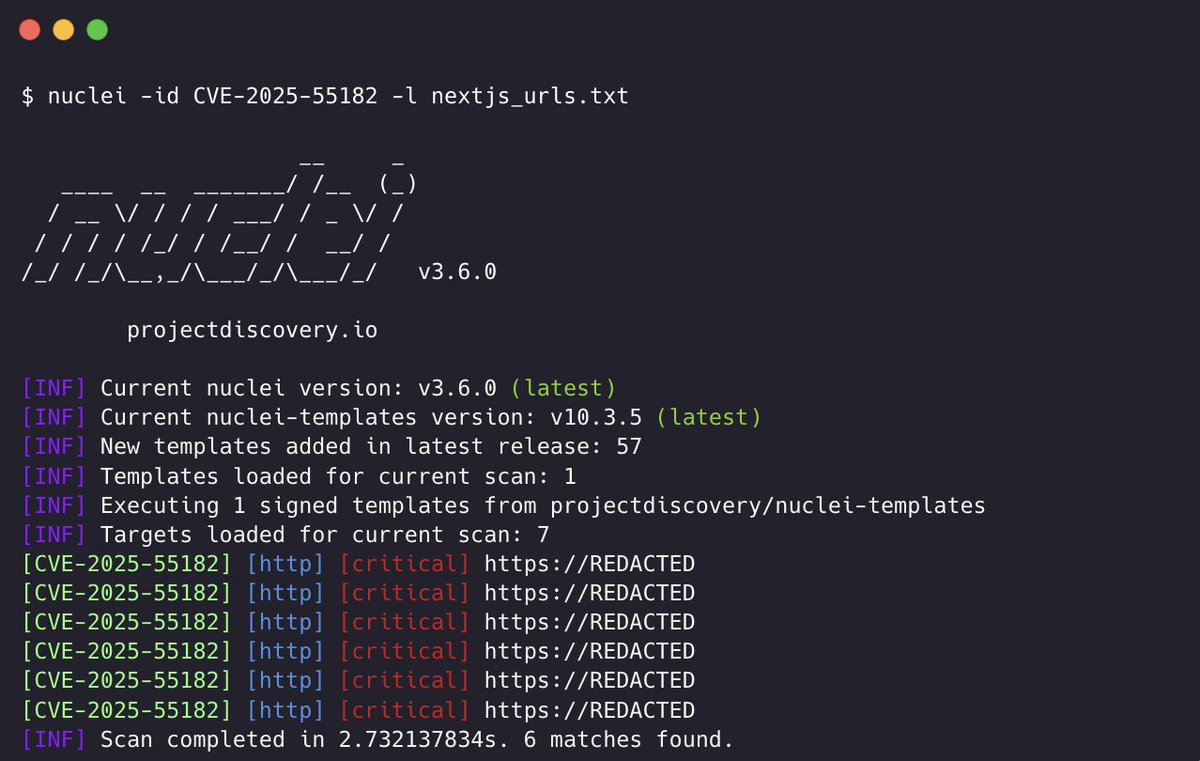
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

#React2Shell via FOFA. Chile: 4,503 results ( 1,649 unique IP )



🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


We’ve got confirmation of a working #react2shell POC being shared. We’ve verified Vercel’s Web Application Firewall is successfully blocking this known variant. We are also seeing bad actors attempt exploitation. Upgrading React & frameworks remains a top priority.
Built a vulnerable React/Next.js lab for testing the #React2Shell bugs (CVE-2025-55182 & CVE-2025-66478). Everything ships in Docker containers.. use it 4fun github.com/jctommasi/reac…

React2Shell Exploited Within Hours as Firms Rush to Patch cysecurity.news/2025/12/react2… #cyberattack #React2Shell #VulnerabilitiesandExploits

Wow #React2Shell Critical Security Vulnerability in React Server Components CVE-2025-55182 and rated CVSS 10.0 The vulnerability is present in versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of: react-server-dom-webpack react-server-dom-parcel react-server-dom-turbopack
中国黑客利用React2Shell漏洞 Amazon报告称,中共国家关联黑客利用React Server Components漏洞(CVE-2025-55182)攻击数千万网站,漏洞已紧急修复。 #React2Shell #CVE202555182 #中国黑客 #网站安全 #Amazon

中国黑客利用React2Shell漏洞 Amazon报告称,中共国家关联黑客利用React Server Components漏洞(CVE-2025-55182)攻击数千万网站,漏洞已紧急修复。 #React2Shell #CVE202555182 #中国黑客 #网站安全 #Amazon

Yo @CrowdStrike , do you have a blog explainig how falcon can defend against #react2shell ?
The speedrun is real on the BB platform 😂 Do you guys ever take a break? #React2Shell
🚨 Critical Alert: Over 77,000 IP addresses at risk! Hackers breach 30 orgs! 😱 #SecurityThreat #CVE2025 #React2Shell 👾 Read more: bleepingcomputer.com/news/security/…
🚨🧨 React2Shell fallout widens 77k systems exposed Over 77,000 Internet-facing systems remain vulnerable as attackers already breached 30+ orgs across sectors. Patch now. #react2shell #cyberattack #patchnow

#React2Shell #Vulnerabilities #flaw #exploited to #breach 30 orgs, 77k #IP_addresses #vulnerable ift.tt/3v8qfob

#vuln #React2Shell DK - 528 x React Framework + Next.js CVE-2025-55182 CVEE 10.00 (OSINT) 329 x Gensyn testnet


I made a tool to scan for targets that use Next.js from a list of domains. #BugBounty #bugbountytips #React2Shell github.com/hackerxploit7/…
For all my FrontEnd buddies, #React2Shell is a vulnerability found this week, make sure to update your #React / #Nextjs packages.
Ещё прикол про #cloudflare Правды ради - они большие молодцы, ибо рили сделали стопперы против #React2Shell Однако! Выбранный Action = Managed Challenge (читай каптча) Так что идите в настройки Cloudflare Managed RuleSet, ищите React и меняйте Action на Block
WordPress people worrying about React UIs in plugins/themes etc the React vuln hits React Server Components & Next.js, not typical client side React. Most WP plugins only use React in wp-admin, so they aren’t exposed to that attack vector. #react2shell
Active exploitation of React2Shell flaw lands it on CISA KEV list, linked to Cloudflare outage. Apache Tika RCE, Oracle zero-day breach at Barts Health NHS, rising LockBit activity, and Agentic Wiper hitting Google Drive. #React2Shell #UK #DataBreach ift.tt/R8l73Q5
"Vercel paid 50k to one researcher so far" to my opinion its a trap to reward one and fix the rest of varitants of all the bypasses as Duplicate don't be foolish enough This reward is for someone for some reasons You know what I mean!!! #React2Shell
Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 92.4K posts
- 2. Kelce 21.2K posts
- 3. Kelce 21.2K posts
- 4. Texans 39.3K posts
- 5. Andy Reid 5,484 posts
- 6. #ITWelcomeToDerry 41.5K posts
- 7. Collinsworth 5,735 posts
- 8. Rashee Rice 4,944 posts
- 9. CJ Stroud 3,216 posts
- 10. #BaddiesUSA 21.5K posts
- 11. #HOUvsKC 1,964 posts
- 12. Chris Jones 2,563 posts
- 13. #SNFonNBC 1,116 posts
- 14. #HTownMade 2,160 posts
- 15. Pitre 5,173 posts
- 16. Jeff Kent 8,209 posts
- 17. Nick Caley N/A
- 18. Packers 79K posts
- 19. Bears 88.9K posts
- 20. AFC West 2,171 posts