SK Rana
@FuzzyLogic404
Dream, Plan, Execute, Dream | VAPT | Red Teaming | 😎
Was dir gefallen könnte
UEFI Bootkits and Kernel-Mode Rootkits Development with Alejandro Vazquez x.com/i/broadcasts/1…
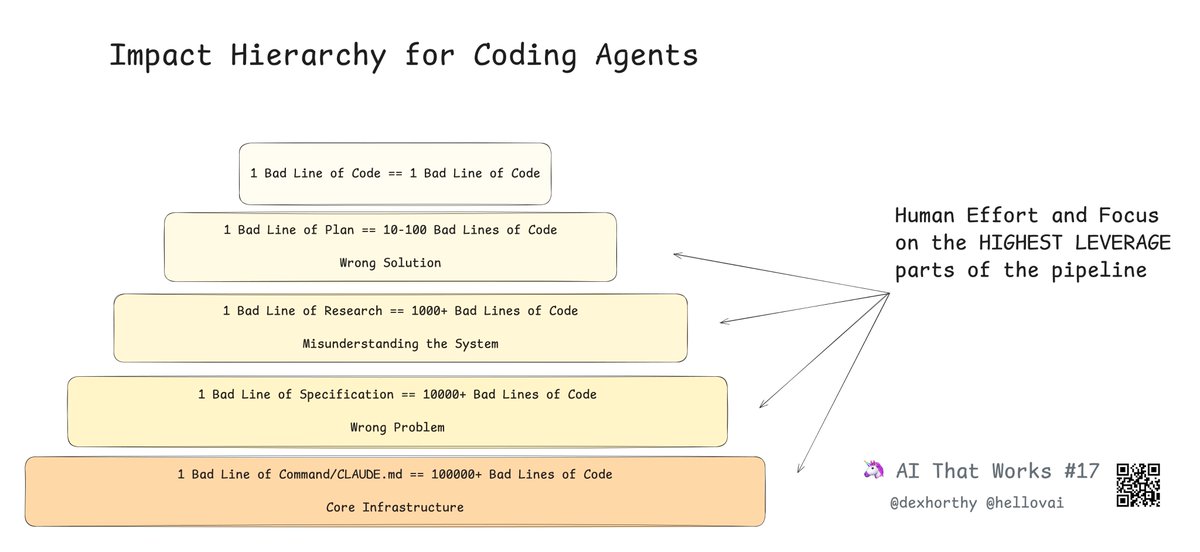
These guys dropped an absolute masterclass on AI agents. No hype. No n8n spaghetti. Just practical agent building, explained in away that anyone can understand. Thanks @dexhorthy and @hellovai. AI That Works is quickly becoming the best AI content on the Internet.
You got access to vsphere and want to compromise the Windows hosts running on that ESX? 💡 1) Create a clone into a new template of the target VM 2) Download the VMDK file of the template from the storage 3) Parse it with Volumiser, extract SAM/SYSTEM/SECURITY (1/3)

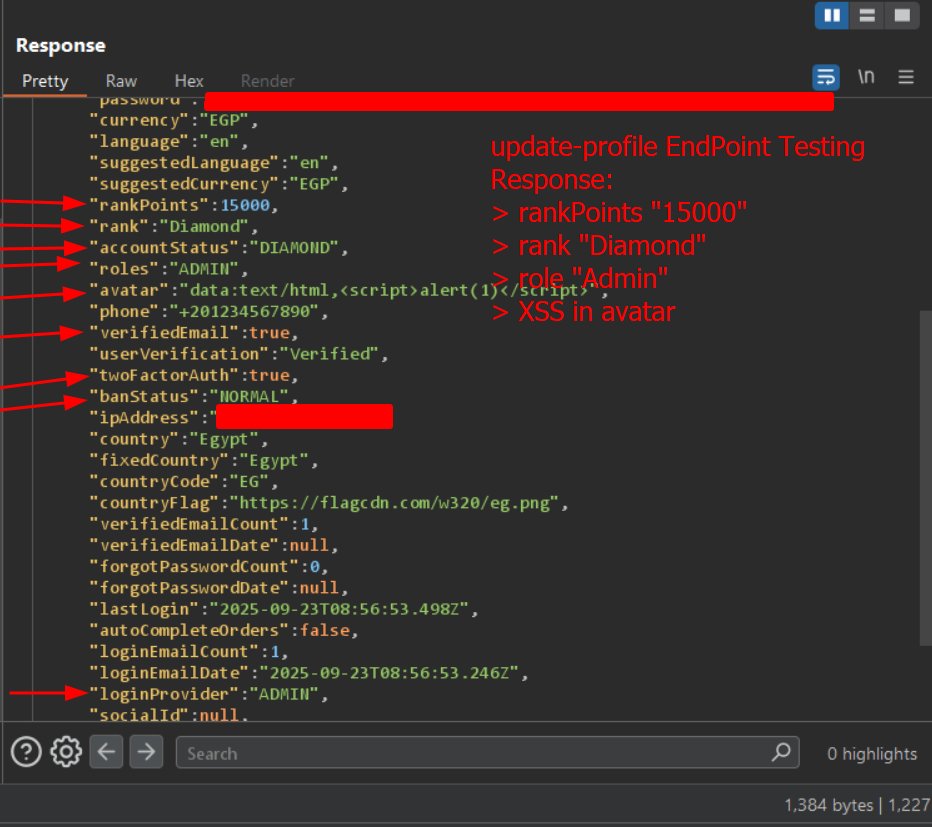
🔥 Wow. Amazing blog post on Agentic Coding. Views agentic coding as a deeply technical engineering craft. Teaches you how to: ✅ Work in brownfield codebases ✅ Solve complex problems ✅ Not generate slop ✅ Maintain mental alignment across the team From @dexhorthy
Had to cut down this video by a lot so I can make it more digestible for YT. Thinking about making a full one if this one does well. 👉🏼 youtu.be/evyxNUzl-HA

Interested in attack vectors in Azure. I have documented another example to have read permission on all the applications exposed in the tenant and more. Blocking default applications is crucial to prevent such vectors. linkedin.com/posts/charles-… #Azure #RedTeam
Introducing BountyBuddy — A Complete Bug Bounty Checklist & Pentesting Checklist infosecwriteups.com/introducing-bo… #bugbounty #bugbountytips #bugbountytip
🚨 Chinese hackers are hijacking legit websites to poison Google results. Experts uncovered Operation Rewrite: a BadIIS malware campaign targeting East & Southeast Asia—redirecting search traffic to scam sites and even planting web shells for deeper breaches. Read →…

A Critical Bug Let Me Become an Admin on an External Bug Bounty Program ln0rag.medium.com/a-critical-bug… #bugbounty #bugbountytips #bugbountytip
Top 25 MCP Vulnerabilities Reveal How AI Agents Can Be Exploited - securityweek.com/top-25-mcp-vul…
🚨 New DDoS-for-hire threat: ShadowV2 Hackers are renting out a botnet that hijacks misconfigured AWS Docker servers—using a Go-based RAT and Python C2 on GitHub Codespaces—to launch massive HTTP/2 “Rapid Reset” attacks and even bypass Cloudflare protections. Read →…

5 Tools No Bug Bounty Hunter Should Be Without =============== 1. Burp Suite – The Swiss Army knife of web hacking; intercept, modify, and fuzz requests like a pro. 2. Nmap – Scan for open ports and services fast; knowing what’s exposed is half the hack. 3. FFUF – Fast web…
Added some pre-set rulesets to hackxpert brute on requests <3 github.com/The-XSS-Rat/ha…

The "Subtle Snail"(UNC1549) group's C2 architecture catalyst.prodaft.com/public/report/…
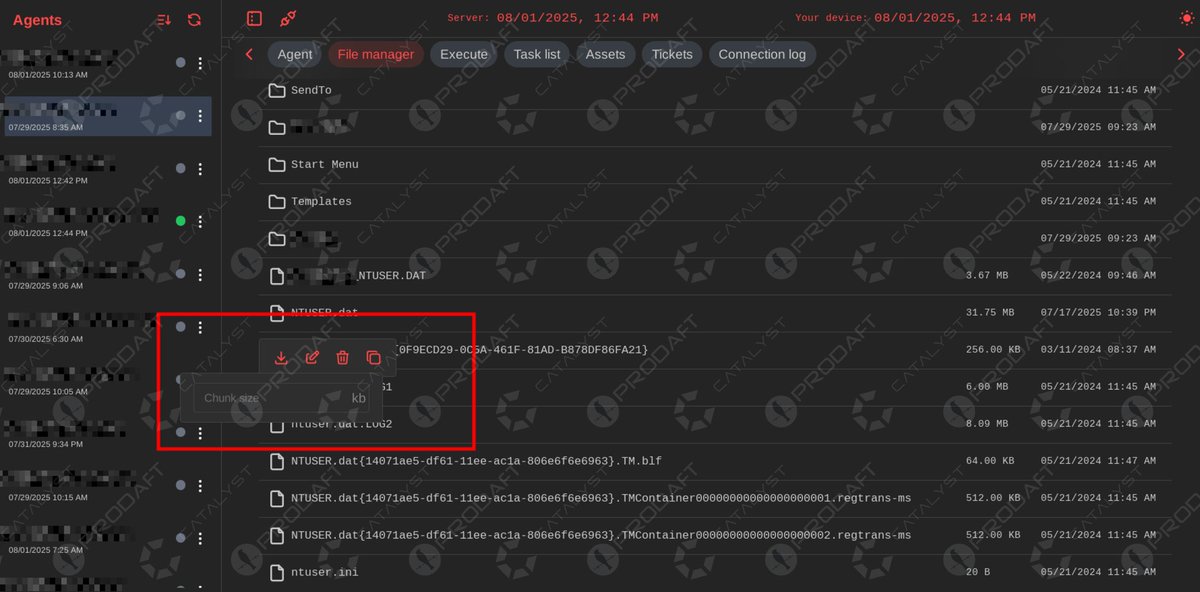
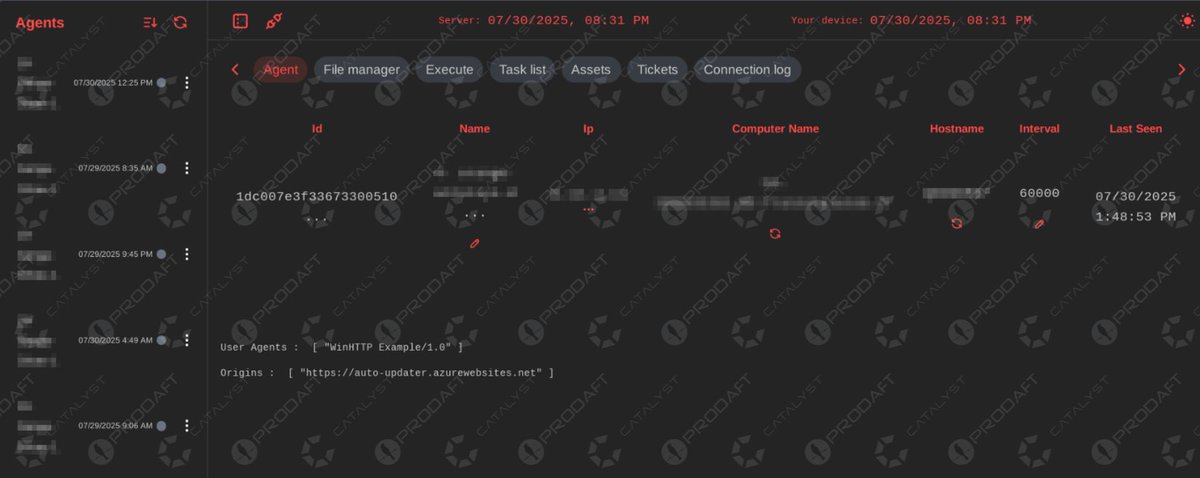
EDR-Freeze This is a tool that exploits the software vulnerability of WerFaultSecure to suspend the processes of EDRs and antimalware without needing to use the BYOVD (Bring Your Own Vulnerable Driver) attack method. github.com/TwoSevenOneT/E…
🥳 Congratulations to the lucky winners of our @OWASP Global AppSec USA conference ticket raffle! 🎟️ Learn more 👇🏽 linkedin.com/posts/infosecm… Thanks everyone for participating. Next giveaway coming soon! 👀 #Giveaway #Raffle #AppSec #CyberSecurity #InfoSec #WashingtonDC
🚨 GIVEAWAY ALERT 🚨 Score a FREE ticket to @OWASP Global AppSec in #WashingtonDC – worth $1,320! 🎟️ To enter: ✅ Follow us ✅ ❤️ + RT this post ✅ Optional: Tag 2 friends = extra entry ⏳ Ends in 7 days – winners announced next week! #Giveaway #AppSec #CyberSecurity #OWASP

I Found A Security Flaw Just By Reading JavaScript Files medium.com/@ibtissamhamma… #bugbounty #bugbountytips #bugbountytip
⚠️ First-ever GPT-4 powered malware uncovered. Researchers found “MalTerminal,” a prototype that can write its own ransomware or reverse shell—code dated before Nov 2023. Hackers are also slipping hidden prompts into phishing emails to trick AI scanners and unleash Follina…

You can watch the recorded stream on "CTAP Impersonation & API Confusion Attacks on FIDO2" here: youtube.com/watch?v=07B0et… Check out our upcoming streams by @offby1security

kinda unhinged that none of the agent frameworks that were hot a year ago are used in any of the top coding agents and now @opencode @CodebuffAI @claude_code are all adding agent-framework-y things... at sprout we used to call this "refactor AFTER patterns emerge". its a good…
United States Trends
- 1. Butker 4,515 posts
- 2. Baker 43.6K posts
- 3. Lions 49.8K posts
- 4. Lions 49.8K posts
- 5. Goff 7,060 posts
- 6. 49ers 40.2K posts
- 7. #OnePride 2,740 posts
- 8. #TNABoundForGlory 14.8K posts
- 9. Ty Dillon N/A
- 10. Bucs 13.6K posts
- 11. #BNBdip N/A
- 12. Packers 36.1K posts
- 13. Dan Campbell 1,405 posts
- 14. #DETvsKC 1,182 posts
- 15. #RHOP 8,557 posts
- 16. Fred Warner 15.5K posts
- 17. Flacco 13.2K posts
- 18. Denny Hamlin 1,599 posts
- 19. George Springer 2,941 posts
- 20. Byron 6,400 posts
Something went wrong.
Something went wrong.