Challenge: How to deploy browser adblocking company-wide without possibly hitting our own global properties, internal sites, or getting noticed by marketing? Push a uBlock Origin policy with Hroup Policy including a RegEx that disables it on domains with our company name.
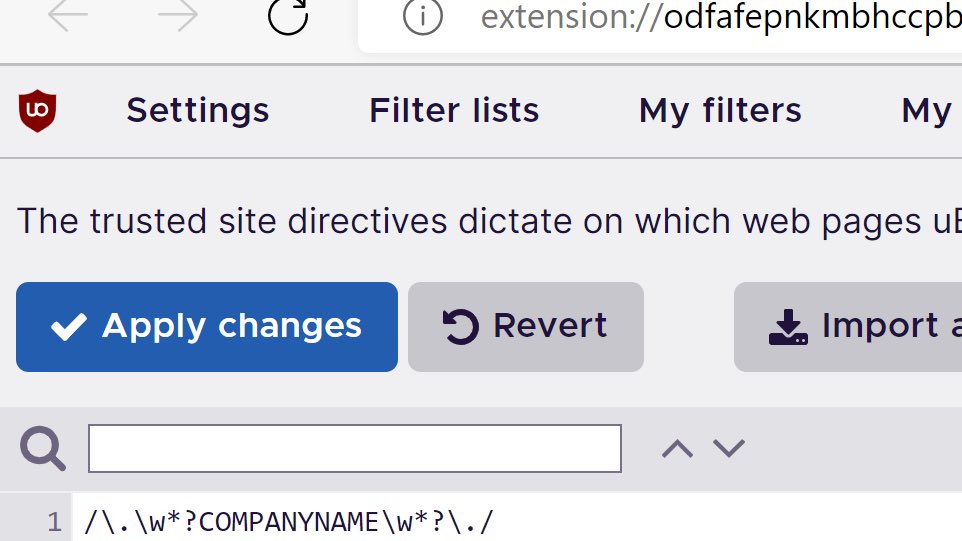
Adblocking is hyper-effective at quenching network threat alarms, massively reducing proxy log volume during threat investigations, and stopping users redirected to phishing and malware. Current corporate uBlock Origin configuration. I may move us to AdGuard instead of EasyList.

Yes I'm writing a blog on How We Do Browsers from top to bottom, but I use Twitter because I'm too impatient. I've been doing this for many many years and have even given feedback/bugs to the Chrome, Edge, and Firefox teams.
AS I WAS SAYING. If you have MDE/ATP and your SOC is getting deluged with alerts recently, it's because you don't have adblocking deployed to those machines yet. Adblocking STOPS THE BEGINNING OF THE ATTACK FROM EXISTING.
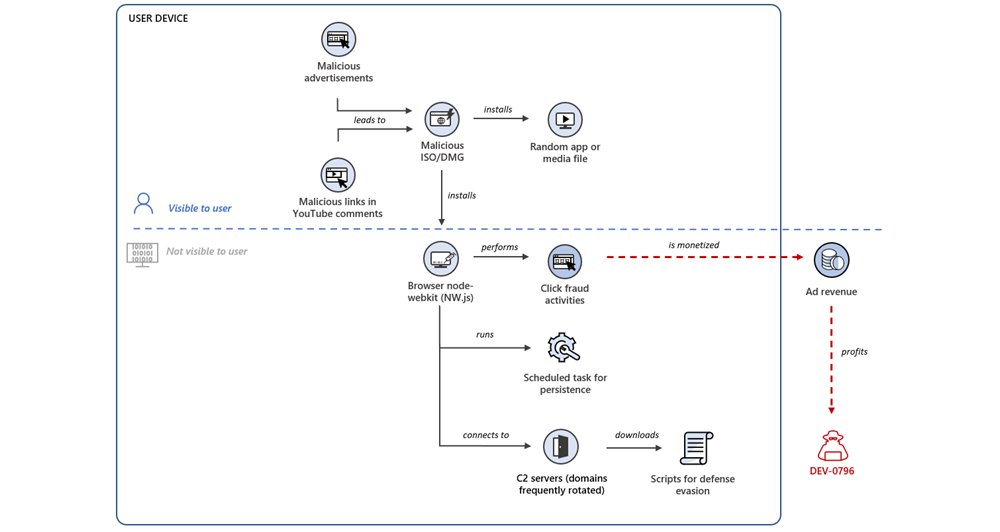
Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.
I don't just make this shit up you know like I'm a human person with experiences and feelings.
Your users are getting these malicious advertising redirects and workflow captures, browsing local news sites. All the time.
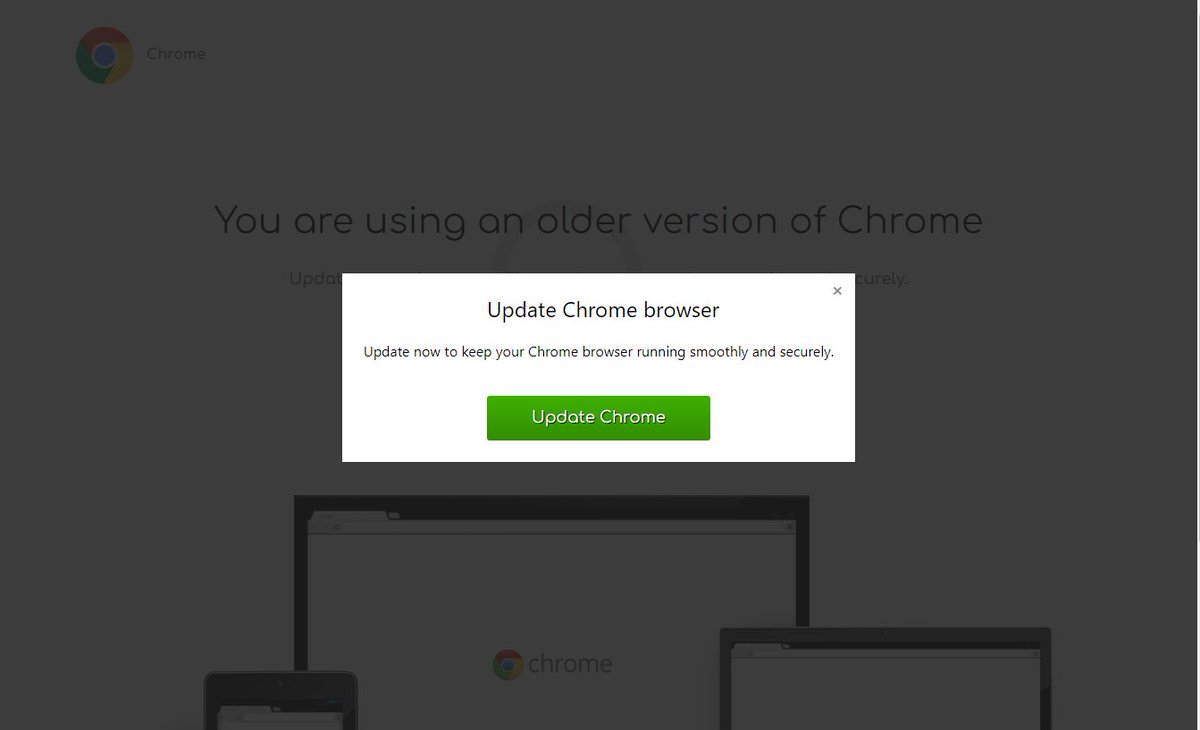
#SolarMarker pretending to be a chrome update. #Signed "Game Warriors Limited" tria.ge/220926-xqpq8sc… Back to PowerShell, file in the startup directory, PowerShell registry. C2: 146.70.53.146 Dropper: virustotal.com/gui/file/bb71d… Backdoor: virustotal.com/gui/file/db9dd… @JAMESWT_MHT

I like this idea. Are there a lot of cases in the industry that would require ads to be shown for an internal network?
+ use Protective DNS (if available) infoblox.com/dns-security-r… + (minimum for users) use Quad9 with Malware blocking+DNSSEC quad9.net/service/servic…
Nice share and a timely reminder on why ad blocking and extension handling should not be ignored at an enterprise level..
Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.

I'm not familiar with this... Hroup Policy you speak of. 🙃
Any safety concerns about using this extension in the work place? Have considered it but it doesn't seem to be in common usage in the enterprise
Really want to get this going but the impending Manifest v3 API changes, which seem targeted around breaking ad-blocking, make me wonder if a network based approach would have more longevity
Pi-hole? I guess it wouldn’t be browser tho, as it’s network level blocking
Just deployed uBlock Origin via GPO at one of my clients with all of their internal and line if business websites added to trusted sites. I wish adding things to trusted sites wasnt so unbelievably jank. Registry keys is jank enough, but a json oneliner?
Great thread but I'm slow to put time into implementing this with Manifest v3 coming down the tracks and the uncertainty as to whether or not uBlock will continue to work with that.
United States الاتجاهات
- 1. #StrangerThings5 251K posts
- 2. Thanksgiving 677K posts
- 3. BYERS 57.4K posts
- 4. robin 93.3K posts
- 5. Reed Sheppard 5,959 posts
- 6. Afghan 289K posts
- 7. holly 64.7K posts
- 8. Dustin 90K posts
- 9. Podz 4,538 posts
- 10. Vecna 59.3K posts
- 11. National Guard 664K posts
- 12. Jonathan 75.4K posts
- 13. hopper 16K posts
- 14. Erica 17.7K posts
- 15. Lucas 83.5K posts
- 16. Nancy 68.6K posts
- 17. Gonzaga 8,532 posts
- 18. noah schnapp 9,007 posts
- 19. Joyce 32.3K posts
- 20. Tini 9,647 posts
Something went wrong.
Something went wrong.