
Winmill Software
@WinmillSoftware
Winmill is a technology services company. We provide consulting services in Application Development, App Sec, PPM, Data Center & Cyber Security, and more.
You might like
Winmill PPM has announced it is expanding its product portfolio by adding Clarizen solutions to its best-of-breed Project and Portfolio Management (#PPM) lineup. Learn more about this exciting news! ppm.winmill.com/blog/winmill-e…
ppm.winmill.com
Winmill Expands Planview Partnership for Enhanced PPM
Clarizen Project and Portfolio Management supports empowered project management and help for organizations in their digital journeys.
Join Winmill's Ben DiMolfetta (Principal Solutions Director / Client Solutions Architect) for SecureWorld Houston on May 18 as he will be presenting on Web Application API's: Building a Modern Approach to Vulnerability Testing. bit.ly/42noabl #SWHOU23
In this new blog post from our Cloud Computing expert - he discusses when it is appropriate to implement a Serverless Architecture. #cloud #architecture #CloudComputing bit.ly/3AqE6xn

Discover how the MITRE ATT&CK framework can significantly improve the effectiveness of your Security Operations Center (SOC) assessments. bit.ly/3N5Ht4J

What is the role of automation in pen testing? It frees up the pen tester’s time so that they can target and exploit vulnerabilities. bit.ly/3rT7DMa #Manualpenetrationtesting #Automatedpentesting #Vulnerabilityassessment #Pentesting #Penetrationtesting

Our security expert discusses the Social Engineer’s Toolkit (SET), which provides attackers with a wide range of pre-built attack vectors that can be used to launch social engineering attacks and also an essential tool for security professionals. More: bit.ly/3GjlT8u
winmill.com
Social Engineers' Toolkit: Kali Linux for Penetration Testing
The Social Engineers' Toolkit (SET) and Kali Linux for Penetration Testing, optimized for Blue and Purple Teams.
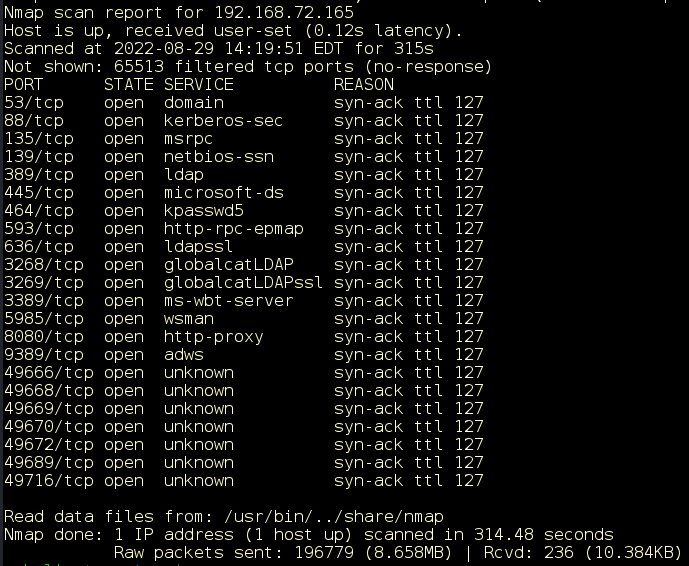
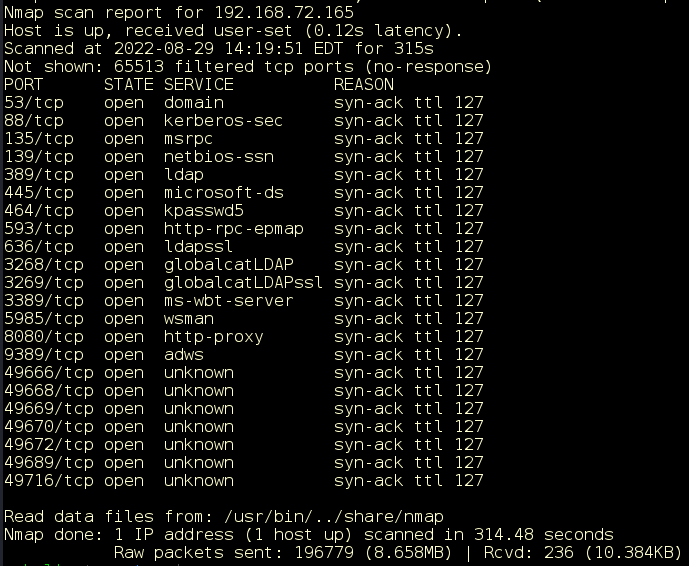
You ran a #vulnerability scan and it found an #SSRF vulnerability. Unfortunately, this may give you a false sense of security. A #penetrationtest will exploit that vulnerability and help you remediate it. bit.ly/3B1Qy6N #penetrationtester #vulnerabilityscan
Winmill is pleased to be a partner of Micro Focus and the winner of their 2022 Apex Program contest. bit.ly/3E04yk0 #MicroFocusApexProgram #Applicationsecurity #Solvingclientpainpoints #Salesenablementcompetition

What if there were a repository of known threat actor activity that could help identify your #applicationsecurity risks? MITRE ATT&CK® is that repository and it can be used to model possible application #vulnerabilities and threats. bit.ly/3gJ9hOr #MITREATTACKDefender

Winmill pen testers follow the Penetration Testing Execution Standard, which includes seven steps to strengthen your network and system security. bit.ly/3TMyjKi #Penetrationtestingphases #pentesting #conductingpenetrationtesting #CIAtriad #cybersecurity

Cyber security is an overriding concern for companies today. Winmill’s #penetrationtesters know how to find #vulnerabilities, determine if they can be exploited, and offer guidance on how to remediate them. bit.ly/3hPQpgF #understandingpenetrationtesting #pentesting

The sales enablement competition sponsored by Micro Focus was challenging, but our Winmill team completed milestone after milestone to secure victory. bit.ly/3EATgmN #Apexsalesenablementcompetition #Apexcompetition #MicroFocusSalesEnablementCompetition #business

Automated penetration testing is simply a vulnerability assessment. Manual pen testing targets and exploits those vulnerabilities. bit.ly/3rT7DMa #Manualpenetrationtesting #Automatedpentesting #Vulnerabilityassessment #Pentesting #Penetrationtesting

A #paddedoracle attack can only happen if your AES encryption is implemented properly. Penetration testing will discover if it’s not and will help remedy the cyber security vulnerability. bit.ly/3vXCg5n #penetrationtest #cybersecurity #cryptographicattack
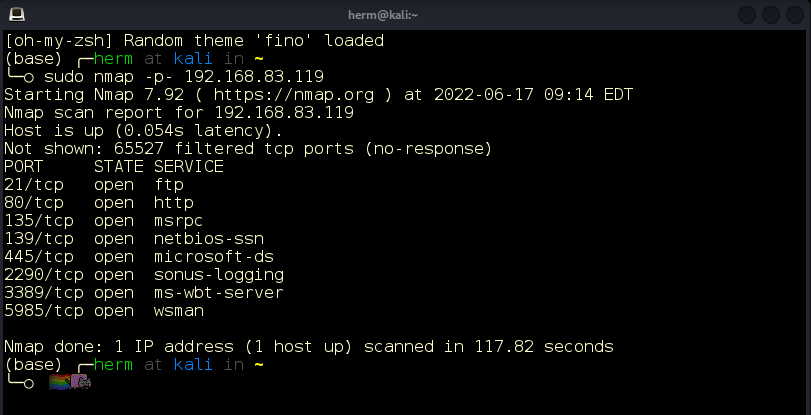
If you have an #SSRF vulnerability that your vulnerability scan found, you need penetration testing to discover the ways that vulnerability could be exploited. bit.ly/3B1Qy6N #pentestingserversiderequestforgery #penetrationtester #penetrationtest #vulnerabilityscan
Winmill claimed victory in the 2022 Micro Focus sales enablement competition. As part of the Apex Program, Winmill partnered with #MicroFocus to solve some of their most limiting issues and help them secure new deals. bit.ly/3E04yk0 #Applicationsecurity

The MITRE ATT&CK Framework provides an intelligence-based method of identifying application #securitythreats and #vulnerabilities that have been exploited by seasoned threat actors. bit.ly/3gJ9hOr #MITREATTACKDefender #threatmodeling #threatintelligence #MADskills

Threat actors will find and exploit your system and network #vulnerabilities if a #penetrationtester doesn’t find them, safely exploit them, and offer expert remediation to remove them. Winmill can do this, and more. bit.ly/3TMyjKi #Penetrationtesting #cybersecurity

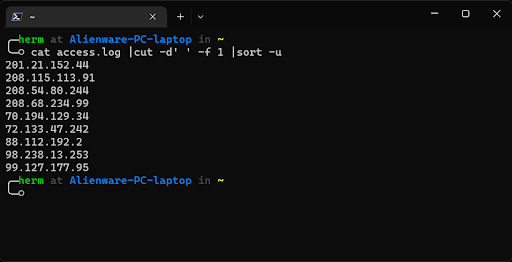
Penetration testers have many tools they can use to detect #cybersecuritybreaches. One tool, #Bash, is low-tech, but it uncovered a brute force attack on an #Apacheserver in just four steps. bit.ly/3OjLGyw #cybersecuritythreathunting #cybersecurity #penetrationtesting
Today’s threat actors are subtle, smart, and dangerous. Winmill #penetrationtesting services help you identify your cyber weaknesses and help you eliminate them before threat actors find them. bit.ly/3hPQpgF #vulnerabilityassessment #penetrationtesting #pentesting

It took six months and much hard work, but Winmill was able to earn the top spot in the Micro Focus Sales Enablement Competition of 2022. Discover what we learned and accomplished. bit.ly/3EATgmN #Apexsalesenablementcompetition #MicroFocusSalesEnablementCompetition

United States Trends
- 1. TOP CALL 3,662 posts
- 2. #BaddiesUSA 64.9K posts
- 3. #centralwOrldXmasXFreenBecky 493K posts
- 4. SAROCHA REBECCA DISNEY AT CTW 513K posts
- 5. AI Alert 1,312 posts
- 6. Good Monday 25K posts
- 7. #LingOrmDiorAmbassador 263K posts
- 8. Rams 30K posts
- 9. Market Focus 2,479 posts
- 10. #LAShortnSweet 23.8K posts
- 11. Check Analyze N/A
- 12. Token Signal 1,741 posts
- 13. #MondayMotivation 6,881 posts
- 14. Vin Diesel 1,549 posts
- 15. Scotty 10.4K posts
- 16. Chip Kelly 9,107 posts
- 17. DOGE 178K posts
- 18. Ahna 7,834 posts
- 19. Raiders 68.2K posts
- 20. Stacey 23.3K posts
You might like
-
 🌩️ NVIDIA GeForce NOW
🌩️ NVIDIA GeForce NOW
@NVIDIAGFN -
 Devpost
Devpost
@devpost -
 Dev Ittycheria
Dev Ittycheria
@dittycheria -
 Clarifai
Clarifai
@clarifai -
 GraalVM
GraalVM
@graalvm -
 Objective-See Foundation
Objective-See Foundation
@objective_see -
 Jamf
Jamf
@JamfSoftware -
 Jonathan Ellis
Jonathan Ellis
@spyced -
 Jesse Hall
Jesse Hall
@codeSTACKr -
 Exclaimer
Exclaimer
@Exclaimer -
 Lukasz Olejnik
Lukasz Olejnik
@lukOlejnik -
 PACSystems Industrial Automation & Controls
PACSystems Industrial Automation & Controls
@EMR_PACSystems -
 MotionVFX | Video Effects
MotionVFX | Video Effects
@motionVFX -
 Antonio Nieto-Rodriguez
Antonio Nieto-Rodriguez
@ANietoRodriguez -
 CIO WaterCooler
CIO WaterCooler
@CIOWaterCooler
Something went wrong.
Something went wrong.











































































































