#pentesting search results
Okay, we'll spill it 🍵 There are TWO new Professional Labs scenarios on #HTB Enterprise Platform! Jump into these #ActiveDirectory scenarios and perform red teaming engagements on the internal networks of two different companies. Sharpen your team's #pentesting skills now:…

I am not that into bug bounty hunting anymore, but if I need a larger amount of money for a side project, I usually simply start... and its always the same... there is always stuff to find.😂 #pentesting #bugbounty #bbp #hackerone

Estos son los comandos más básicos de Linux que debes dominar para empezar en ciberseguridad, hacking ético o informática. #ciberseguridad #kalilinux #Pentesting #informatica #linux
Our LLM Agent successfully exploits a critical Cross-Stie Scripting Vulnerability and provides a complete POC. The Deep QN RL Algorithm is properly working. :) Visit: novaize.com #AI #pentesting #SaaS

Kali Linux 😍 . . . #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #cyberattacks #bugbounty #bugbountytips #hacking #codelivly #ethicalhacking
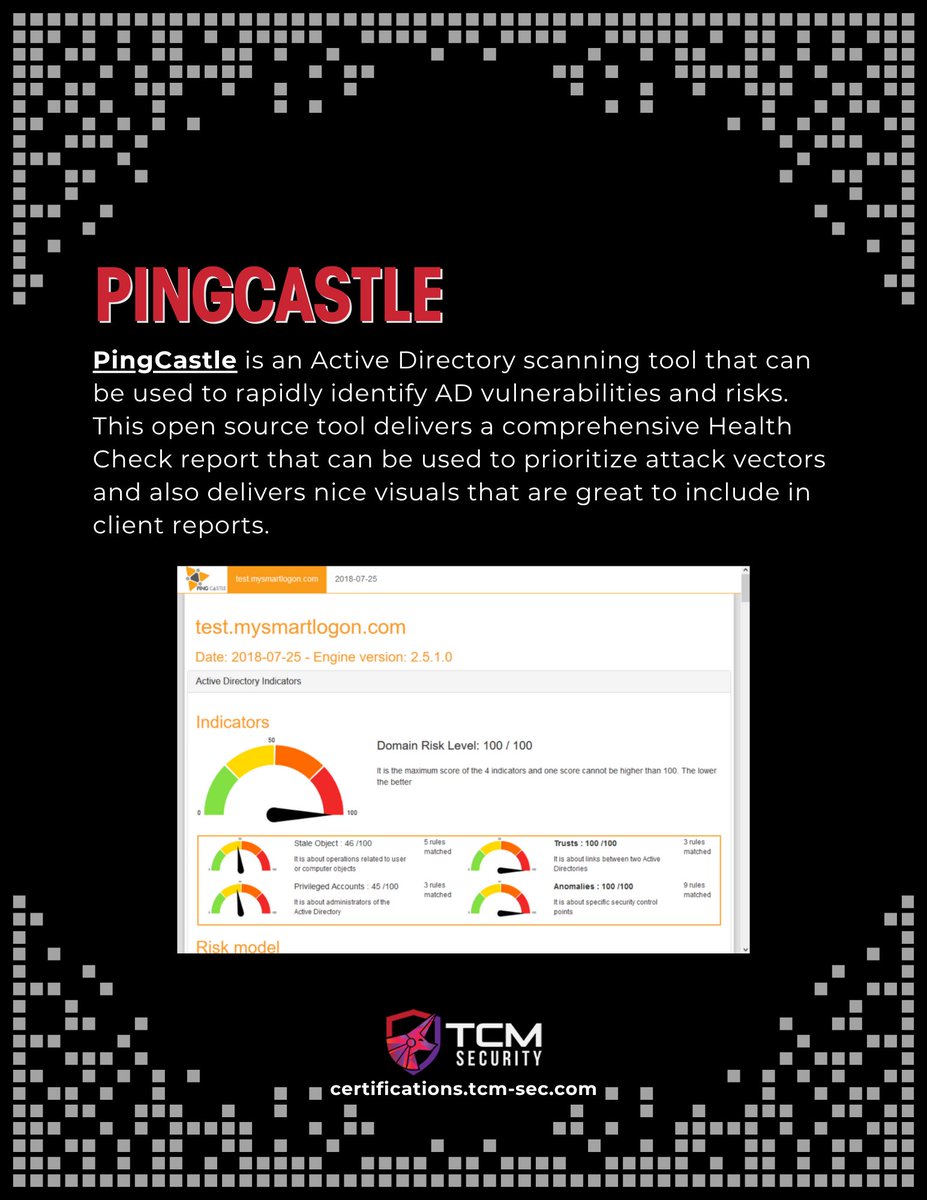
🔐 Top 5 Active Directory Pentesting Tools Five essential AD tools for mapping, auditing, and validating Windows/AD defenses — use only in authorized engagements or lab environments. #ActiveDirectory #ADSecurity #Pentesting #InfoSec #EthicalHacking




At Hackrowd, we’ve seen one truth: companies wait until AFTER a breach to take security seriously. But security should be by design, not by disaster. #Hackrowd #CyberSecurity #Pentesting
Linux Networking Tools . . . #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #bugbounty #bugbountytips #hacking #ethicalhacking

🔐 Top 5 Active Directory Pentesting Tools Five essential AD tools for mapping, auditing, and validating Windows/AD defenses use only in authorized engagements or lab environments. #ActiveDirectory #ADSecurity #Pentesting #EthicalHacking
Most Fortune 500 organizations rely on Active Directory, and that means AD security knowledge is a must for any serious security professional. Whether you’re offensive or defensive, understanding AD improves your ability to find and fix real-world risks. To help, here are 5…



Mobile pentesting is one of the most overlooked areas in a pentester’s journey, and mastering it can instantly set you apart from the crowd 🥷 Today, we’re sharing some tried-and-true resources to help you as you start down the mobile #pentesting path - an assortment of static…




USBKill V4 Tactical Kit: Your all-in-one solution for device testing 🎮. From phones to industrial equipment, we've got you covered. 🌐 l.usbkill.com/kORaK #usbkill #usbkillV4 #pentesting #infosec #hacking #pentester

Subverting the Windows Kernel with exploits and rootkits. Juan Sacco from exploitpack.com will run a hands-on workshop at @BITM_HACKLAB 2025. Check the website of the No Hat conference: nohat.it #cybersecurity #infosec #Pentesting #kernel #exploits
Top Nmap Commands 🚀 Here is your essential cheat sheet for the most common Nmap commands, from stealth scans to OS detection. ⭐️ Save this post for your next security audit or pentest! 👇 What's your most-used command? Share it below! #cybersecurity #pentesting #bugbountytips

AI's potential to enhance scalability and create new avenues in pen testing is becoming increasingly apparent. Adopting AI in some capacity is essential for faster results. #AI #pentesting
USBKill V4 Tactical Kit: Your all-in-one solution for device testing 🎮. From phones to industrial equipment, we've got you covered. 🌐 l.usbkill.com/kORaK #usbkill #usbkillV4 #pentesting #infosec #hacking #pentester

Subverting the Windows Kernel with exploits and rootkits. Juan Sacco from exploitpack.com will run a hands-on workshop at @BITM_HACKLAB 2025. Check the website of the No Hat conference: nohat.it #cybersecurity #infosec #Pentesting #kernel #exploits

Get the full downloadable pdf of Linux Privilege Escalation (Red - Blue team ) here at : resources.codelivly.com/product/rootcr… . . . #infosec #cybersecurity #pentesting #redteam #CyberSec #networking #security #linux #bugbounty #dns #hacker #hacking #codelivly #ethicalhacking

🔐 Top 5 Active Directory Pentesting Tools Five essential AD tools for mapping, auditing, and validating Windows/AD defenses use only in authorized engagements or lab environments. #ActiveDirectory #ADSecurity #Pentesting #EthicalHacking
Most Fortune 500 organizations rely on Active Directory, and that means AD security knowledge is a must for any serious security professional. Whether you’re offensive or defensive, understanding AD improves your ability to find and fix real-world risks. To help, here are 5…




Finished the Hydra room on @TryHackMe — practised brute-forcing SSH and POST web forms with THC-Hydra. Great reminder: use long, unique passwords + MFA. Ethical testing only. 🔐🛡️ tryhackme.com/room/hydra?utm… #Infosec #Pentesting #tryhackme via @realtryhackme
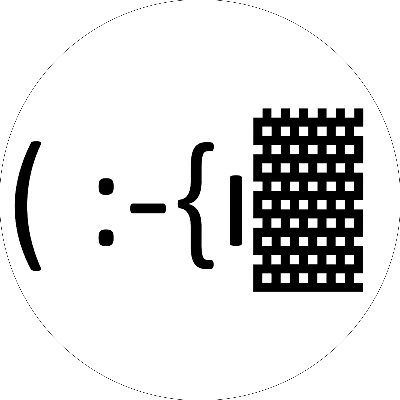
Originally from: BHIS: EyeWitness Cheatsheet blackhillsinfosec.com/eyewitness-che… ( :-{ı▓ #BlackHillsInfoSec #Pentesting #cyberresearch

I am not that into bug bounty hunting anymore, but if I need a larger amount of money for a side project, I usually simply start... and its always the same... there is always stuff to find.😂 #pentesting #bugbounty #bbp #hackerone

Linux Networking Tools . . . #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #bugbounty #bugbountytips #hacking #ethicalhacking

Okay, we'll spill it 🍵 There are TWO new Professional Labs scenarios on #HTB Enterprise Platform! Jump into these #ActiveDirectory scenarios and perform red teaming engagements on the internal networks of two different companies. Sharpen your team's #pentesting skills now:…

#Pentester #Cybersecurity #Pentesting #EthicalHacking #InfoSec #HackerTools #PenetrationTesting #BugBounty #CyberSec #KaliLinux #NetworkSecurity

Mobile pentesting is one of the most overlooked areas in a pentester’s journey, and mastering it can instantly set you apart from the crowd 🥷 Today, we’re sharing some tried-and-true resources to help you as you start down the mobile #pentesting path - an assortment of static…




🔐 Top 5 Active Directory Pentesting Tools Five essential AD tools for mapping, auditing, and validating Windows/AD defenses — use only in authorized engagements or lab environments. #ActiveDirectory #ADSecurity #Pentesting #InfoSec #EthicalHacking




Top Nmap Commands 🚀 Here is your essential cheat sheet for the most common Nmap commands, from stealth scans to OS detection. ⭐️ Save this post for your next security audit or pentest! 👇 What's your most-used command? Share it below! #cybersecurity #pentesting #bugbountytips

Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 62.9K posts
- 2. #TNABoundForGlory 25.7K posts
- 3. Butker 7,060 posts
- 4. Goff 10.1K posts
- 5. Kelce 10.2K posts
- 6. Baker 47K posts
- 7. #OnePride 4,408 posts
- 8. Bryce Miller 2,132 posts
- 9. #DETvsKC 2,688 posts
- 10. #SNFonNBC N/A
- 11. Dan Campbell 1,898 posts
- 12. Cal Raleigh 3,996 posts
- 13. Leon Slater 2,047 posts
- 14. #ALCS 7,005 posts
- 15. 49ers 42.1K posts
- 16. Pacheco 4,082 posts
- 17. Gibbs 4,558 posts
- 18. Ty Dillon 1,134 posts
- 19. Gausman 2,812 posts
- 20. Denny 5,606 posts