
Ashif_(Ai)
@XploitAsh
eJPT || eWAPTXv2 || eCPTXv2 || C|EH || Security Researcher || BugBounty Hunter || Penetration taster
Hackers 🔥 An easy — but very realistic example you’ll actually find in the wild 🎯 Did you catch the vulnerability here? 🪲 How would you exploit it? 💥

CVE-2025-55752 Apache Tomcat possible RCE if PUT is enabled 🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡 This is like saying i can extract your data from db if sql query is enabled

Tip:Google dork is still alive!!🔥 payload used:<svg><animate onbegin=alert(1) attributeName=x dur=1s> Source:portswigger.net/web-security/c… #BugBounty #bugbountytips #cybersecurity #googledorks #xss

#bugbountytips ❌ Stop Doing These 10 Bug Hunting Mistakes ... And revise your methodology if : 1. You spend 2 days or less per program 2. You run automated tools on each URL and wait for unique results 3. You don't scan servers' open ports 4. You don't register an account in…

Autoswagger: A command-line tool designed to discover, parse, and test for unauthenticated endpoints using Swagger/OpenAPI documentation. GitHub: github.com/intruder-io/au…

HACKER’S most basic — yet powerful — trick: 💥 AUTHENTICATION BYPASS 💥 via SQL injection Still works in 2025. Still crazy effective. What’s your go-to payload? 👇 Here are a few of mine: ' OR 'chux'='chux ' OR IF(1=1, SLEEP(5), 0)-- ⏱️ This weird looking payload got me A LOT…

🚨 Hackers & Bug Hunters! By combining Katana, LinkFinder, Arjun, and Burp Suite, I uncovered hidden API endpoints — including ones under /dev/ — and exploited: ✅ Mass Assignment ✅ API Excessive Data Exposure ✅ IDOR (Insecure Direct Object Reference) These tools are gold when…


Alhamdolilah Released BackupFinder ❤️ Big thanks to all contributors for making BackupFinder awesome! @infosec_au @coffinxp7 @intigriti @GodfatherOrwa For Wordlists @assetnote and for chaining with tools @pdiscoveryio Github : github.com/MuhammadWaseem… #OpenSource #BugBounty

Enter email to check if it is connected to some PGP key (it can then be used to gather information in document archives, leak databases, forums, etc). keys.openpgp.org Tip by @DoingFedTime

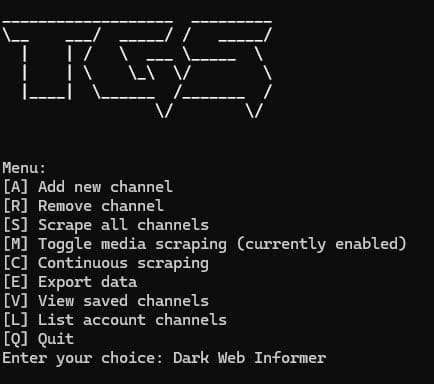
Telegram Scrapper 2.0: A powerful Python script that allows you to scrape messages and media from Telegram channels using the Telethon library. Features include real-time continuous scraping, media downloading, and data export capabilities. GitHub: github.com/robertaitch/te… Major…
Web Check: All-in-one OSINT tool for analysing any website GitHub: github.com/lissy93/web-ch… Link: web-check.xyz


Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

Bug bounty is not just about finding bugs You need to understand what’s not meant to be seen. Here’s a usefull JS ENUMERATION to break into buried endpoints, logic, and secrets. 👇 A thread for the bug-bounty hunters #BugBounty #JavaScript #Recon #BurpSuite #websecurity

💾 SQLi Tips for Modern Apps • Always check JSON body params • Test GraphQL queries for injections • Try time-based payloads (SLEEP()) • Bypass WAFs with encodings or comments • Don’t ignore errors in logs or responses 🧩 SQLi still lives—in new places. #BugBounty #SQLi…
Lookout later this week for some giveaways!
Broken Access Control via Hardcoded Bearer Token in Public JS File medium.com/@nnouh4967/bro…
The best writeup i read related to Chaining Vulnerabilities medium.com/@ahmdhalabi/th… medium.com/@Hx0_0h4nf1/ho…
SQL Injection Payload i was able to locate a SQL injection very hard to exploit , with digging I successfully got it with the sleep payload ''||(select 1 from (select pg_sleep(6))x)||' ==> i added as well to my SQL wordlist happy hunting ♥ #bugbountytips #bugbountytip…

United States Trends
- 1. Veterans Day 81.7K posts
- 2. Good Tuesday 30.3K posts
- 3. Mainz Biomed N/A
- 4. SoftBank 8,249 posts
- 5. United States Armed Forces N/A
- 6. #tuesdayvibe 1,789 posts
- 7. Vets 13.6K posts
- 8. #Talus_Labs N/A
- 9. Armistice Day 11.9K posts
- 10. #Gratitude 1,434 posts
- 11. Bond 61.5K posts
- 12. #ARMY 1,584 posts
- 13. #RemembranceDay 11.8K posts
- 14. World War 39.7K posts
- 15. 600k Chinese 6,027 posts
- 16. $NBIS 6,744 posts
- 17. 600,000 Chinese 10.9K posts
- 18. Window 54K posts
- 19. Islamabad 42.1K posts
- 20. Berkeley 101K posts
Something went wrong.
Something went wrong.






















































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)













