You might like
Had fun with some network protocol 🔍RE and BugSleep 🐞👇 raw-data.gitlab.io/post/bugsleep_… #MuddyWater #ida
I had some time to work on the RE Rust Tickler challenges from @HuntressLabs recent CTF. Specifically, I wanted to focus on @vector35 Binary Ninja's TTD implementation Over weekend I made some quick write-ups on how I approached these easier challenges. github.com/Rurik/CTF/tree…
2 new videos: Using the Anti-Malware Scan Interface (AMSI) to scan a file. C++: youtu.be/EQYoFiWjRhM C#: youtu.be/OGhky7He_yA

youtube.com
YouTube
AMSI Scanning - C# Edition
Binary Ninja plugins I developed during my XProtect Remediator research are now available in the Binary Ninja Plugin Manager! - Swift Analyzer - XProtect Remediator Analyzer - Missing Link Many thanks to @vector35 for suggesting it!



My recent writeup on updates in #Rhadamanthys stealer, along with some scripts that may be helpful in analysis. Check it out!
🚨 Rhadamanthys v0.9.2 is here! What’s new in this multi-layered stealer’s latest evolution? We break down the updates, tactics, and what defenders need to know. Dive into our blog for the full analysis. research.checkpoint.com/2025/rhadamant…
This talk looks interesting. > We also show how rare entitlement combinations (e.g., com.apple.private.tcc.allow) appear 25x more often in malware, enabling stealth access to sensitive hardware like the microphone and camera. AFAIK, private entitlements aren’t…

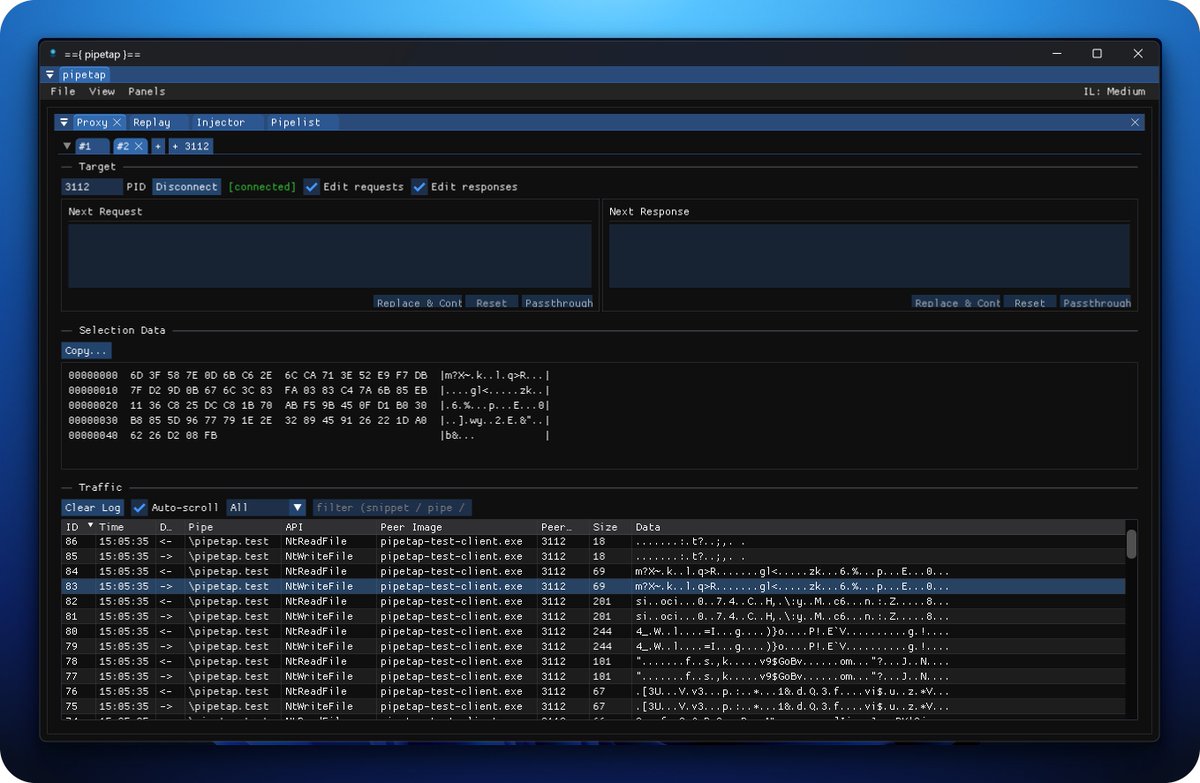
I've been hacking on a new Windows Named Pipe tool called PipeTap which helps analyse named pipe communications. Born out of necessity while doing some vulnerability research on a target, its been super useful in reversing it's fairly complex protocol. :)
I just released a new video: How WSL 1 Works. In this video, I explain how Windows Subsystem for Linux version 1 runs ELF binaries. trainsec.net/library/window…
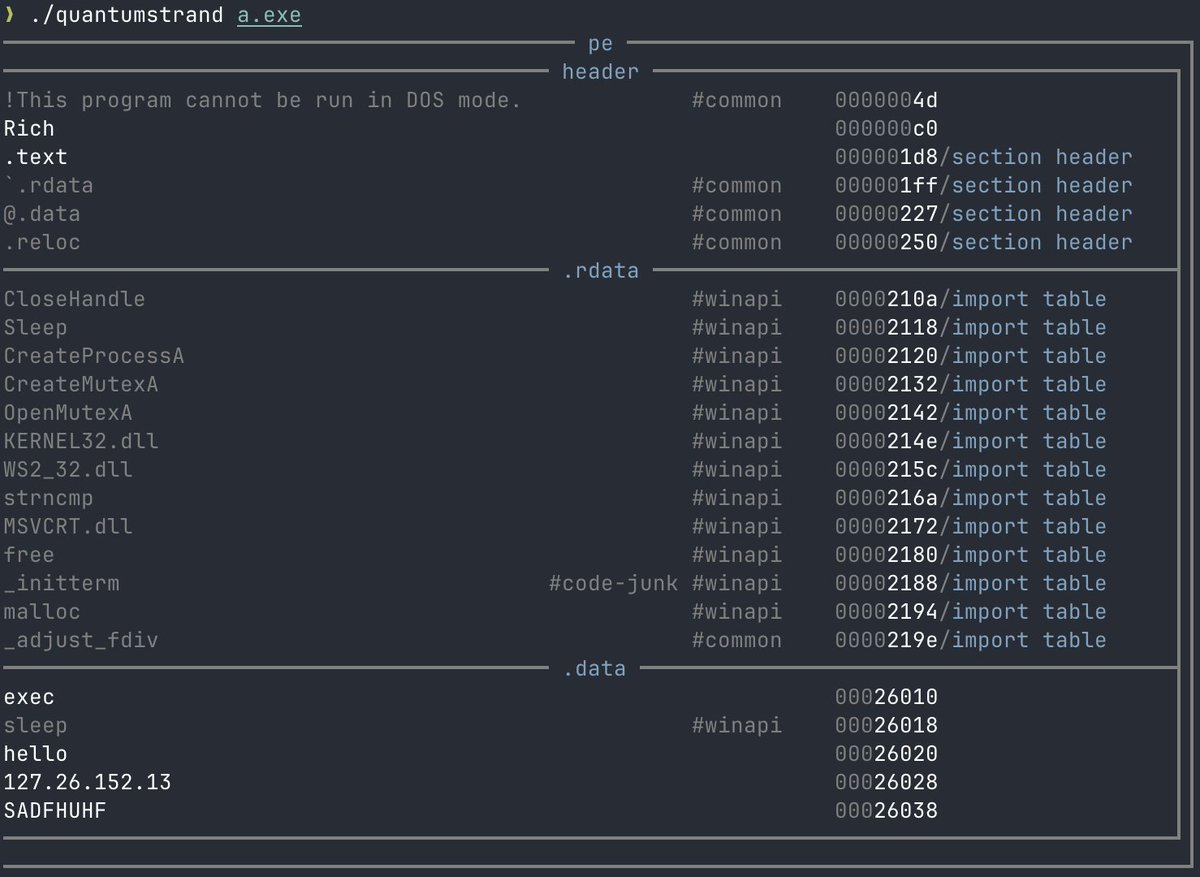
QUANTUMSTRAND beta 1 released: built for analysts to quickly understand *where* strings are, *what* they might be, and *how* important they are, without getting lost in a sea of undifferentiated text. Thanks @m_r_tz and the crew at @Mandiant FLARE github.com/mandiant/flare…
1/ Nice catch by @g0njxa: ads drop #macOS #stealer as well. First stage: signed DMG "Alli-Ai.dmg". Inside: Mach-O file named sudoku?🤷♀️ Seems to be a Swift app, in real a wrapper (loader/launcher) that spawns a child process and hands it AppleScript that does the actual data theft

In the past days I've been observing a malware campaign using X verified accounts affiliated to account @KindleBookVerse (I see +140 accounts, consider each one malicious) running malicious X ads redirecting users to a fake AI website delivering malware. While the ads redirect…



New blog post just dropped! West Shepherd breaks down extending the Mythic Poseidon agent for ARM64 Dylib injection on Apple Silicon. Details include: ✅ Shellcode construction ✅ Memory allocation ✅ Runtime patching ✅ Thread creation Read more ⤵️ ghst.ly/41Nu4ED
My presentation “XUnprotect: Reverse Engineering macOS XProtect Remediator” at #BHUSA wrapped up yesterday. Thank you so much to everyone who attended. For those who couldn’t make it to #BHUSA, I’ll be sharing the key points from my research in this thread. (1/22)

YARA-X 1.5.0 has been released! It comes with new features and multiple bug fixes. github.com/VirusTotal/yar…
Today we released a new stable version of DRAKVUF Sandbox v0.19.0 🎉– a project that leverages the DRAKVUF system for agentless malware analysis. Detailed release notes can be found on our Github: github.com/CERT-Polska/dr…
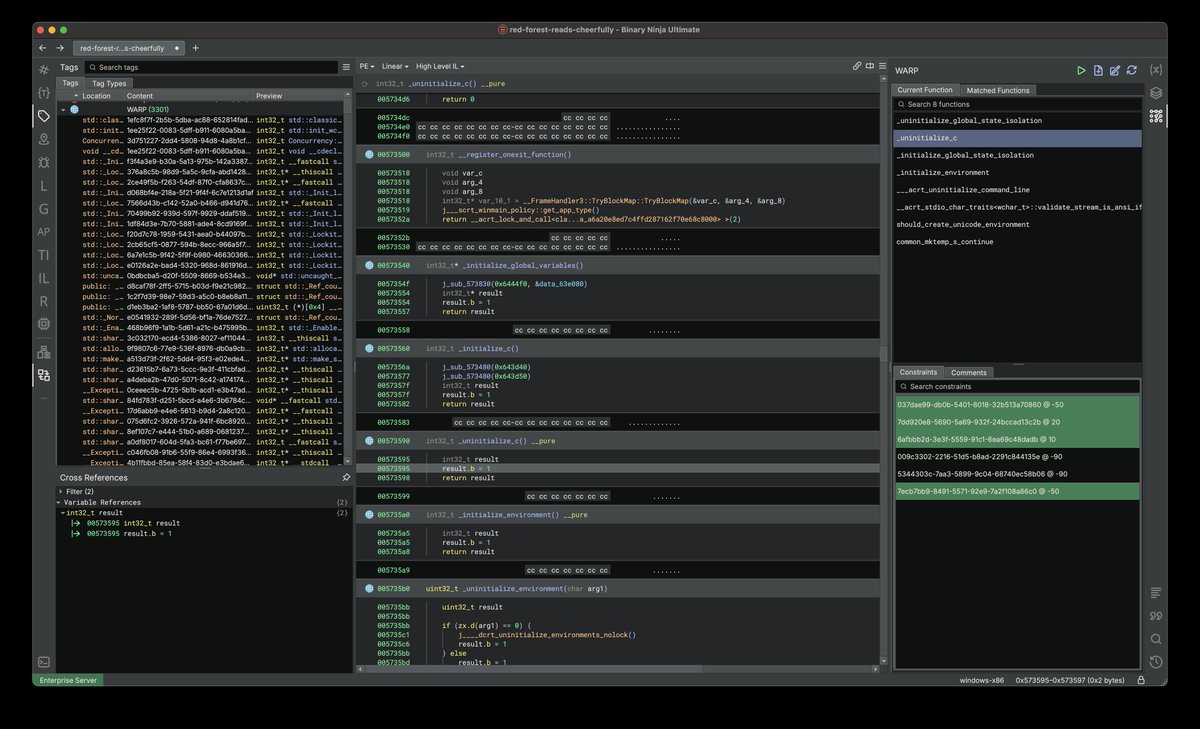
WARP is here in Binary Ninja 5.1! It’s our new signature‑matching system that’s not just faster and smarter, but actually easier to use too. Build and share libraries easily, pull in type info, even prep for cross‑tool compatibility. WARP is the future. Go try it.…
I updated the #Rhadamanthys custom format converter (for XS modules), to support the latest version (0.9.x): github.com/hasherezade/hi…
Binary Ninja 5.1 is now released: binary.ninja/2025/07/24/5.1… - New WARP function matching - Pseudo Objective-C - Binexport plugin built-in - IL Rewriting Examples, APIs, and Docs - Arch: PPC VLE, mips-r5900, x32 + Much more!
First time in Ibiza for #OBTS 🌴☀️ and couldn’t be more stoked! Honored to be speaking alongside some brilliant researchers. In my new talk I'll explore Apple Security Updates and how to tear them open for intel. Bring your sunscreen and your curiosity😎🧠
📢 Just dropped: the full #OBTS v8 talk lineup! objectivebythesea.org/v8/talks.html And for the first time we'll have 3 full days of presentations! 🤩 Congrats to the selected speakers and mahalo to all who submitted. With ~100 submissions, selecting the final talks was a daunting task! 😫
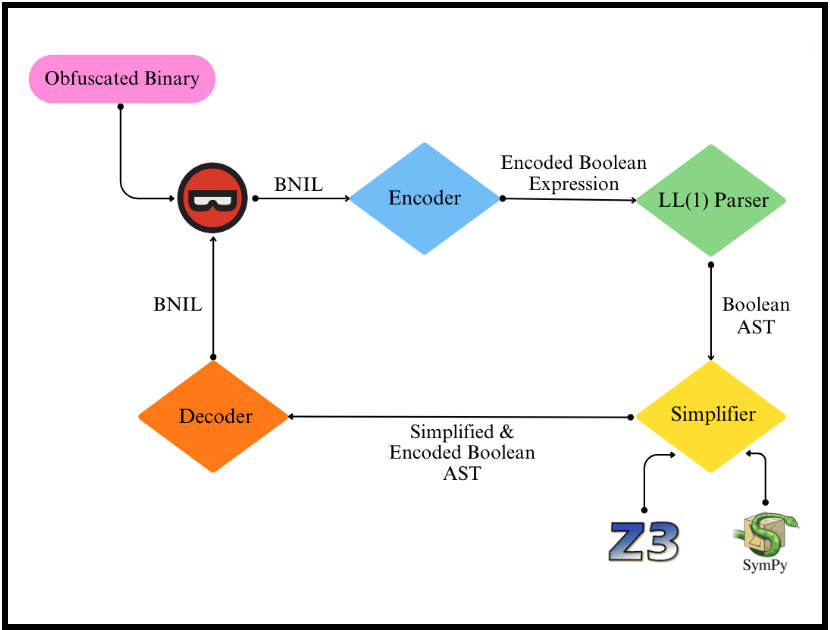
This has been getting some activity on my GitHub recently so thought I would cross post here. 👀✨Last year I worked on a cool project with some students tackling mixed-boolean arithmetic (MBA) deobfuscation and built a plugin for Binary Ninja (@vector35)! 🐛🥷 🧵(1/n)
Have you wanted to report signed Mac binaries like this one? Now you can with certReport 3.3* (pip install certreport). You can also add them to the Cert Central DB with -p, and tag a malware family with -t. Easy. See thread for more detail. *VT API key required



I've been poking at #Golang malware a bit lately and wrote up some tips/tricks that I use when analyzing Golang. @jstrosch and I just talked about this on his live stream too. Check it out here -> (The livestream replay is linked in the blog post) 🤓 securityliterate.com/go-big-or-go-h…
United States Trends
- 1. #GRAMMYs 42.4K posts
- 2. #FanCashDropPromotion 2,551 posts
- 3. ADDISON RAE 6,168 posts
- 4. Dizzy 7,350 posts
- 5. #FridayVibes 5,529 posts
- 6. Good Friday 62.8K posts
- 7. olivia dean 3,257 posts
- 8. #FursuitFriday 9,982 posts
- 9. #PETITCOUSSIN 23.1K posts
- 10. Happy Friyay 1,651 posts
- 11. Munetaka Murakami 2,133 posts
- 12. chappell 4,435 posts
- 13. Kehlani 21.6K posts
- 14. Clipse 1,684 posts
- 15. Publix 2,109 posts
- 16. Elise Stefanik 10.7K posts
- 17. Best New Artist 6,200 posts
- 18. Happy N7 2,837 posts
- 19. Laporta 9,276 posts
- 20. Katseye 50.9K posts
You might like
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 UNPACME
UNPACME
@unpacme -
 Abdallah Elshinbary
Abdallah Elshinbary
@_n1ghtw0lf -
 Bryce
Bryce
@bryceabdo -
 m4n0w4r
m4n0w4r
@kienbigmummy -
 Yogesh Londhe
Yogesh Londhe
@suyog41 -
 Bart
Bart
@bartblaze -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 J.A.R.V.I.S
J.A.R.V.I.S
@peppermalware -
 4rchib4ld
4rchib4ld
@4rchib4ld -
 dao ming si
dao ming si
@dms1899 -
 sean
sean
@seanmw -
 Jesko Hüttenhain
Jesko Hüttenhain
@huettenhain -
 ⚛️ Marcin Siedlarz
⚛️ Marcin Siedlarz
@siedlmar -
 immortalp0ny
immortalp0ny
@immortalp0ny
Something went wrong.
Something went wrong.