You might like
I published an article how BlackByte evades EDR by removing kernel callbacks via abuse of vulnerable driver Rtcore64.sys news.sophos.com/en-us/2022/10/… #reverseengineering #malware #infosec #windows #cybersecurity #blackbyte #ALPHV #sophos #ida #ransomware #endpoint
Lots of frustration in the malware analysis and reverse engineering community. It's been discovered a DEFCON talk, presentation, and the code which coincided with it, was AI slop. The talk itself had hallucinated terminology which (apparently) no one at DEFCON noticed. Bad.

#PipeMagic is a highly modular backdoor used by the financially motivated threat actor Storm-2460. It masquerades as a legitimate open-source ChatGPT Desktop Application. Microsoft Threat Intelligence encountered PipeMagic as part of research on an attack chain involving the…

🚨 Ever tangled with virtual machine-based code protection? 🚨 In 2020, I wrote a virtual machine deobfuscator for a crack me challenge. Check it out! malwareandstuff.com/taming-virtual… malwareandstuff.com/taming-virtual… 🔍 #ReverseEngineering #MalwareAnalysis #windows #idapro #deobfuscation
🚨 Microsoft reports Russian APT Secret Blizzard is targeting embassies in Moscow with AiTM attacks using ApolloShadow malware. It installs a trusted root cert to spoof legit sites & maintain persistence—ongoing since 2024. 🧵 Details: microsoft.com/en-us/security… #CyberSecurity…
🚨 RIFT update! Now supports FLIRT signature generation on Linux 🐧 🔗 github.com/microsoft/RIFT #RustLang #MalwareAnalysis #ReverseEngineering #DFIR #FLIRT
🚨 RIFT Update: We’ve boosted our compiler detection! 🛠️ Now with sharper insights into binaries built using GNU, MinGW, and MSVC toolchains. More enhancements are on the way—stay tuned! 🔍✨ #ReverseEngineering #MalwareAnalysis #RIFT #malware #msft github.com/microsoft/RIFT
Do you find analyzing Rust binaries/malware tedious and unpleasant? You’re not alone! If you’re attending #REcon this year, our own @hackingump1 will be unveiling #RIFT today at 2PM EST (not at REcon? We got you covered, stay tuned). We have been using RIFT internally for some…
Unpacking VMProtect 3 (x64) 🤷♂️
Presenting "Unveiling RIFT: Advanced Pattern Matching for Rust Libraries" at RECON Montreal 2025! Sharing research on discovering Rust dependencies in compiled binaries. See you there! 🚀 #RECON2025 #RustLang #ReverseEngineering
The deep dive below into PebbleDash’s FakeTLS C2 protocol shows how North Korean APTs fake TLS handshakes and use hardcoded RC4 encryption to blend in with legit HTTPS traffic. malwareandstuff.com/reversing-pebb… #malware #infosec #reverseengineering #pebbledash #cybersecurity #windows
Recon CFP ends in less than 2 weeks on April 28. Prices for the training and conference increase on May 1st. Register now to save with early bird price. We have already announced a few talks and workshops, and more videos from last year have been released. recon.cx…

🔍 Exploring Domain Generation Algorithms (DGAs) in Malware 🔍 Below is an article I wrote years ago, which explains the difference between seed based and dictionary based algorithms. malwareandstuff.com/dgas-generatin… #malware #infosec #cybersecurity #dga #dns
@hackingump1 will be presenting about "Unveiling RIFT: Advanced Pattern Matching for Rust Libraries" at Recon Montreal recon.cx more details to come soon #reverseengineering #cybersecurity
Symbolic Execution is powerful technique that explores all possible execution paths without actual inputs. An interesting display of this technique is below: doar-e.github.io/blog/2014/10/1… #malware #reverseengineering #cybersecurity #infosec #symbolicexecution
Russia-Linked “BadPilot” Cyber Campaign Exposed 🚨 Microsoft has uncovered a multiyear global access operation executed by a sub group of Seashell Blizzard, a Russian nation state actor. microsoft.com/en-us/security… #threatintel #cybersecurity #infosec #microsoft #mstic
🚨 Secret Blizzard, a Russian nation-state actor exploits other hackers' infrastructure to evade detection & conduct espionage. 🔍 Learn more: 🔗 Part I: microsoft.com/en-us/security… 🔗 Part II: microsoft.com/en-us/security… #CyberSecurity #ThreatIntelligence #malware #infosec
microsoft.com
Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack...
Since January 2024, Microsoft has observed Secret Blizzard using the tools or infrastructure of other threat groups to attack targets in Ukraine and download its custom backdoors Tavdig and KazuarV2.
🚀 MSTIC Uncovers STAR Blizzard Spear-Phishing Campaign Targeting WhatsApp Users Microsoft has identified STAR Blizzard, a phishing campaign targeting WhatsApp accounts through social engineering. microsoft.com/en-us/security… #threatintel #infosec #starblizzard #mstic
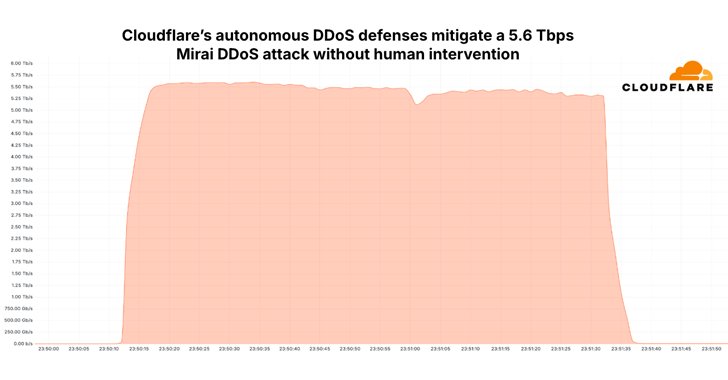
🚨 Then vs. Now: The Evolution of DDoS Attacks 🚨 In 2016, Mirai's botnet caused chaos with a 1.2 Tbps DDoS attack(theguardian.com/technology/201…). Fast forward to 2025, and we’re now witnessing 5.6 Tbps attacks—nearly 5x the scale! thehackernews.com/2025/01/mirai-… Mirai botnet was first…
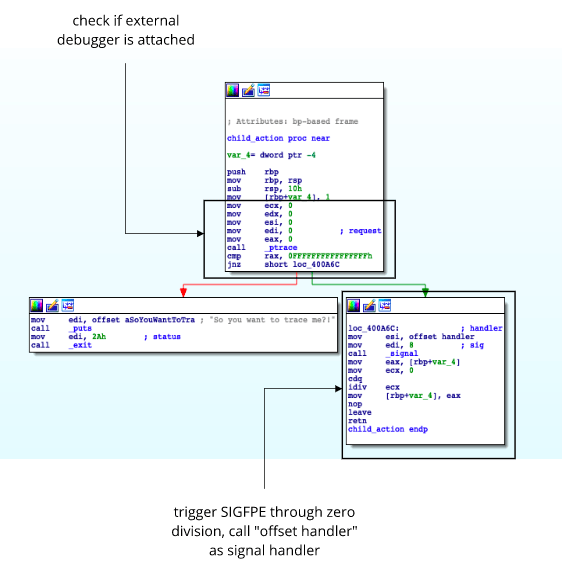
Ever heard about "nanomites"? 🐞🖥️ By allowing a parent process to control its child, the technique can hinder reverse engineers from debugging a binary. malwareandstuff.com/nanomites-on-l… #malware #cybersecurity #infosec #reverseengineering #nanomites
United States Trends
- 1. phil 115K posts
- 2. Bills 98K posts
- 3. Bills 98K posts
- 4. Bijan 13.6K posts
- 5. Drake London 3,123 posts
- 6. Josh Allen 9,092 posts
- 7. McDermott 2,274 posts
- 8. phan 88.7K posts
- 9. Columbus 252K posts
- 10. #RiseUp 1,026 posts
- 11. #BUFvsATL 2,147 posts
- 12. #DaBears 1,795 posts
- 13. #RaiseHail 3,636 posts
- 14. Beane 1,086 posts
- 15. Palmer 10.3K posts
- 16. Penix 2,796 posts
- 17. Starship 63.4K posts
- 18. Jake Moody 1,383 posts
- 19. Brisker N/A
- 20. Jorge Polanco 7,659 posts
You might like
-
 UNPACME
UNPACME
@unpacme -
 Ori Damari
Ori Damari
@0xrepnz -
 Josh Stroschein | The Cyber Yeti
Josh Stroschein | The Cyber Yeti
@jstrosch -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 CAPE Sandbox
CAPE Sandbox
@CapeSandbox -
 m4n0w4r
m4n0w4r
@kienbigmummy -
 Bryce
Bryce
@bryceabdo -
 Moritz
Moritz
@m_r_tz -
 💥 𝕭𝖑4𝖈𝖐𝖍0𝖑3𝖟 👾
💥 𝕭𝖑4𝖈𝖐𝖍0𝖑3𝖟 👾
@bl4ckh0l3z -
 d00rt
d00rt
@D00RT_RM -
 Dmitry Melikov
Dmitry Melikov
@DmitriyMelikov -
 immortalp0ny
immortalp0ny
@immortalp0ny -
 avallach (@[email protected])
avallach (@[email protected])
@xorhex -
 Lloyd Davies
Lloyd Davies
@LloydLabs -
 ᴘᴀʀᴛʜɪ
ᴘᴀʀᴛʜɪ
@cyber__sloth
Something went wrong.
Something went wrong.























![hackingump1's tweet card. So I was looking through the CISA’s recent publications regarding three tools named PebbleDash[1], Copperhedge[2] and Taintedscribe[3] which are believed to be used by the state-sponsored Nor…](https://pbs.twimg.com/card_img/1975836375196049411/sxl4NU3n?format=png&name=orig)