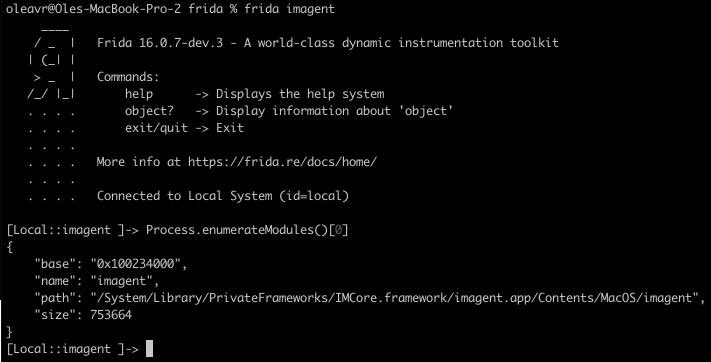
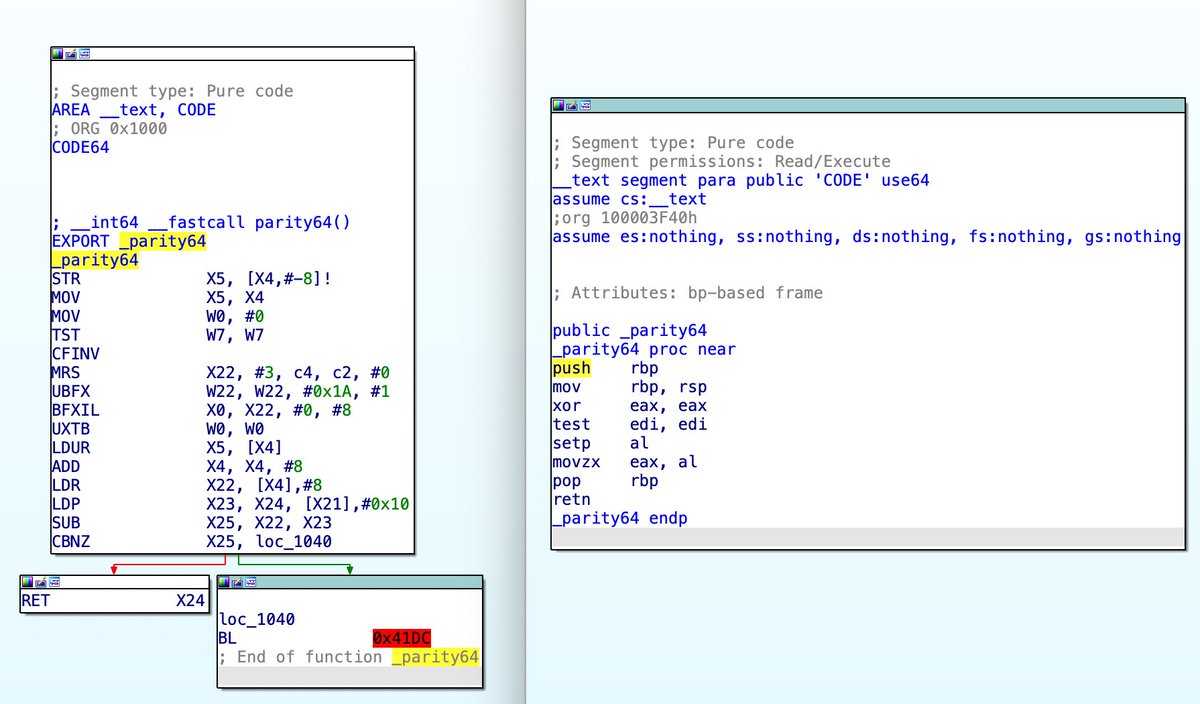
📣 Announcing the tmp.0ut Volume 3 Call For Papers! For information on submission guidelines and ways to contact us, visit the CFP page: tmpout.sh/blog/vol3-cfp.…

The Christmas open-obfuscator challenge is live at this address: obfuscator.re/challenges/ Thank you to @vector35 @build38dotcom and @eshard for sponsoring the prizes of this challenge.

Le SSTIC aura lieu du 7 au 9 juin 2023. L'appel à contributions est en ligne: sstic.org/2023/cfp/. Date limite de soumission : 30 janvier. Vous hésitez ? Relisez nos conseils: blog.sstic.org/2017/01/06/com…
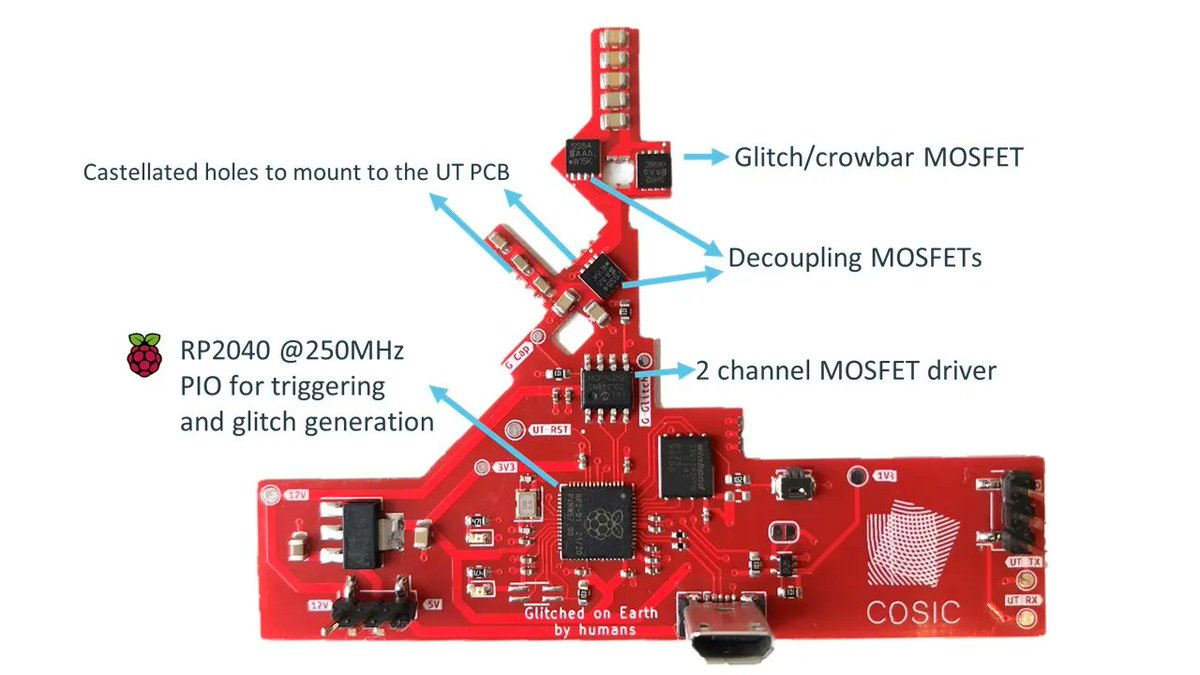
Boot ROM authentication bypass and arbitrary code execution on the Starlink User Terminal using voltage fault injection Great work by @LennertWo GitHub: buff.ly/3gpX5ly Slides: buff.ly/3tOWCMQ #embedded #hardware #faultinjection #starlink #hacking #infosec


Today we remember our friend the late Jerry Lawson, one of the most influential names of the early video game industry. Jerry created game cartridges as we know them, changing the way games were created and sold, and helped to grow our industry immeasurably. Thank you, Jerry.

Here are some slides and hands-on about Linux x86-64 reverse engineering: github.com/romainthomas/r…

We now support executing GPU code compiled with nvc++ - godbolt.org/z/36rEac6zY - we're not yet quite sure why it's so very slow but it's a start! -mg
For whom I've ever wondered how Rosetta 2 can be so efficient! Very interesting insights in this blog post! I naïvely thought it was decompiling code to a higher level IR (LLVM or something else) and then opt+retargetting. How wrong I was.
Reverse engineering via GDB.
United States トレンド
- 1. $NVDA 85.1K posts
- 2. Peggy 39.1K posts
- 3. FEMA 17.7K posts
- 4. Jensen 28.4K posts
- 5. Sheila Cherfilus-McCormick 15.2K posts
- 6. WE HURT PEOPLE 1,302 posts
- 7. Dean Wade N/A
- 8. Jabari N/A
- 9. #Jupiter 4,444 posts
- 10. Raisel Iglesias N/A
- 11. Baba Oladotun 1,063 posts
- 12. Koa Peat N/A
- 13. Nae'Qwan Tomlin N/A
- 14. #YIAYalpha N/A
- 15. Sam Harris 1,189 posts
- 16. NASA 58.1K posts
- 17. GeForce Season 6,647 posts
- 18. #CMAawards N/A
- 19. #SomosPatriaDePaz 1,053 posts
- 20. Arabic Numerals 7,798 posts
Something went wrong.
Something went wrong.