
codechacker
@codechacker
👁️🗨️ Cuts so sharp they leave traces. 💻 Code so clean it’s encrypted. 🧠 Here to disrupt your scroll. #cybersecurity
🛠️ 7 Top Hacking Gadgets You Should Know (Thread) 🧵 Whether you're into ethical hacking, pentesting, or just curious about cyber tools, these devices are powerful, versatile, and a bit scary 👀 Let’s break them down one by one 👇 #CyberSecurity #HackingTools #Infosec

Your network in tech is just as important as your skills. if you’re into dev, AI, or building projects. we can connect.
GPT-5 Just Dropped… And It’s NOT What You Think Watch the video on YouTube: youtu.be/Pq1PtOiXAwQ #blackhat #gpt5 #ai

AI will never replace shitposters
A hacker doesn’t need your password if they can trick a support agent. SIM swapping proves it — call your carrier, pretend to be you, and transfer your number. Suddenly, all your OTPs belong to them. That’s why phone numbers make terrible 2FA.

A hacker doesn’t need your password if they can trick a support agent. SIM swapping proves it — call your carrier, pretend to be you, and transfer your number. Suddenly, all your OTPs belong to them. That’s why phone numbers make terrible 2FA.
Hackers don’t need zero-days to succeed. They live off human shortcuts: weak WiFi passwords, outdated software, or “temporary” logins that never get deleted. The biggest threat to security isn’t advanced malware — it’s neglect.
Data leaks aren’t about “hackers finding your password.” They’re about entire identity blueprints — names, addresses, security questions, phone numbers. Once that’s exposed, attackers don’t hack… they impersonate. Identity theft is harder to fix than a hacked account.
On public WiFi, attacks like Man-in-the-Middle (MITM) are still alive and well. A hacker can silently intercept traffic, inject scripts, or steal cookies that keep you “logged in.” VPNs aren’t hype — they’re the only shield against this
Phishing isn’t always obvious. Hackers now use pixel-perfect clones of login pages with HTTPS + padlock icons. The only giveaway is the URL. If you don’t train yourself to check domains carefully, no tool in the world will save you.
Most “hacks” aren’t about brute force or coding genius — they’re about automation. Hackers use scripts that test thousands of stolen logins in seconds. That’s why even a strong password is useless if it’s reused across sites. Unique passwords kill automation.
Dark Cybersecurity Fact: Most breaches don’t happen because of elite hackers. They happen because Bob from accounting clicked a fake invoice. #CyberSecurity #Infosec #HumanError #PhishingKills
If your threat model stops at antivirus and firewalls, you’re not thinking like an attacker. Real security starts when you assume the breach already happened. #CyberSecurity #RedTeam #Infosec #ZeroTrust #ThreatHunting
Web development Courses for 𝐟𝐫𝐞𝐞 CSS SQL HTML Node.js MongoDB Database Javascript Git & GitHub Back-End Web Development Front-End Web Development Just 𝐟𝐫𝐞𝐞 Of Cost! Grab, Simply: 1. Like & Repost 2. Comment "Web" 3. Follow me for sure DM
When Microsoft turns its back, Linux extends a hand 🤝 Old PCs deserve a second life — give them Linux. #Linux #TechHumor #OpenSource #Windows11 #OldPCNewLife

Who's up ?? 😏
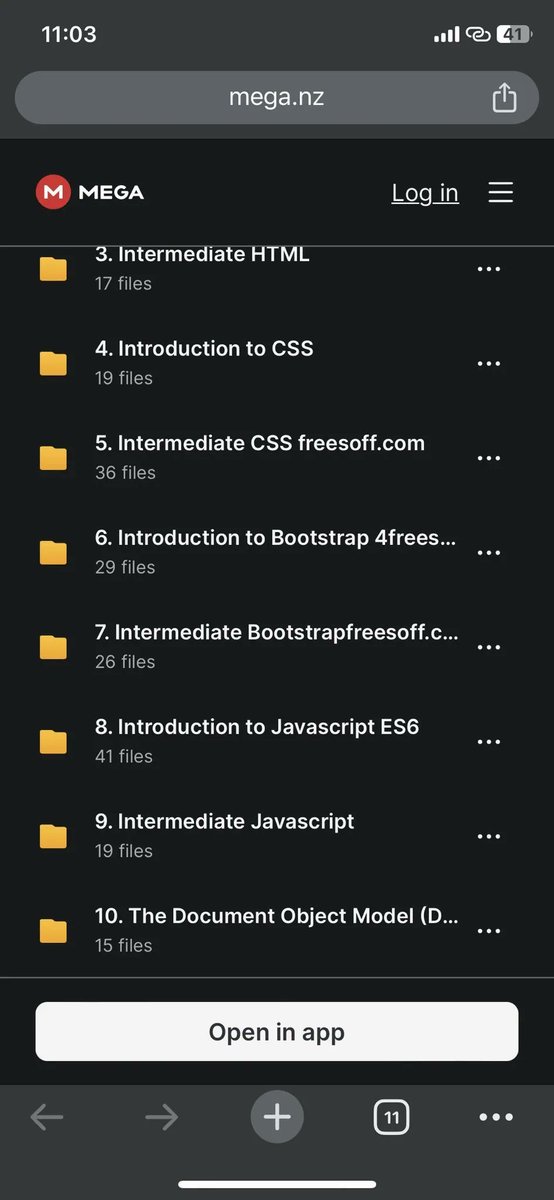
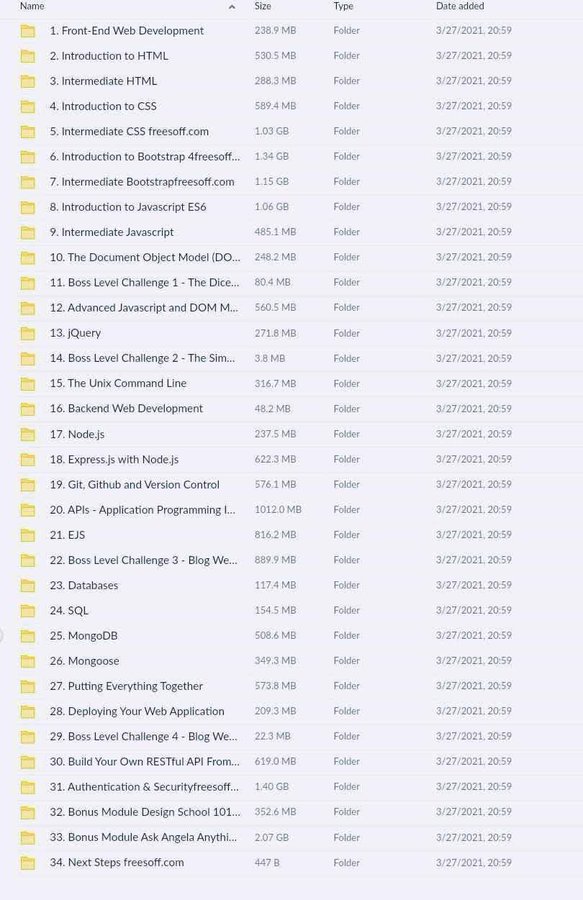
Full stack web development courses for free: 💻 HTML 💅 CSS 🚀 JavaScript ⚛️ React 💡 jQuery 🐙 Git & GitHub 🌐 APIs ⚙️ Node.js 📊 SQL ➕..and more! To get it, just 48 Hours ⏰ - 1. Like & repost 2. Reply " send " 3. Follow me (so that I can DM)
STOP WATCHING P0RN STOP WATCHING P0RN STOP WATCHING P0RN STOP WATCHING P0RN STOP WATCHING P0RN STOP WATCHING P0RN STOP WATCHING P0RN
Real cybersecurity isn’t flashy. It’s late nights, failed scans, broken scripts, and silent wins. Nobody claps when the breach doesn’t happen. But that’s the point. #CyberGrind #RedTeam #CodeChacker

United States Trendler
- 1. Chauncey Billups 72.3K posts
- 2. #FalloutDay 4,103 posts
- 3. Damon Jones 19.6K posts
- 4. Mafia 107K posts
- 5. #7_years_with_ATEEZ 64.6K posts
- 6. Tiago Splitter 2,201 posts
- 7. #에이티즈_7주년_항해는_계속된다 50.8K posts
- 8. #A_TO_Z 50.2K posts
- 9. Changpeng Zhao 14.7K posts
- 10. Kash Patel 43.6K posts
- 11. The FBI 159K posts
- 12. 5sos 33.6K posts
- 13. Gilbert Arenas 7,227 posts
- 14. La Cosa Nostra 7,708 posts
- 15. Gambling 144K posts
- 16. Ti West 1,215 posts
- 17. The NBA 207K posts
- 18. Toronto Rangers 3,042 posts
- 19. Kirby Air Riders 9,369 posts
- 20. Adam Silver 5,091 posts
Something went wrong.
Something went wrong.














