bruh
@cppbruh
OSCP, OSCE, OSEE
Bạn có thể thích
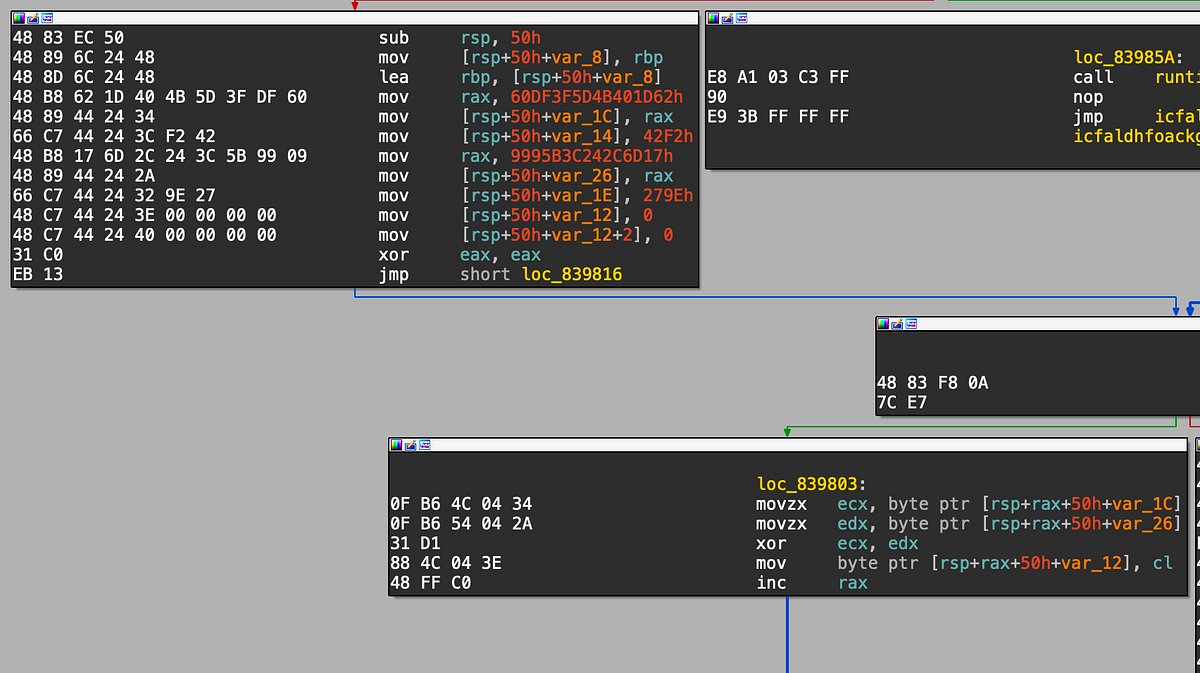
ok, installing Magisk and rooting the Android Emulator by applying custom crappy scripts is totally obsolete now. it is simple and clean: just "./build[.]py avd_patch" from the official repo now. thanks @topjohnwu.
![an0n_r0's tweet image. ok, installing Magisk and rooting the Android Emulator by applying custom crappy scripts is totally obsolete now.
it is simple and clean: just "./build[.]py avd_patch" from the official repo now. thanks @topjohnwu.](https://pbs.twimg.com/media/G7hmJzmWkAMUEDK.jpg)
just updated my Magisk installer script (ramdisk patcher) for Android Emulator to support recent Android API and Magisk versions: gist.github.com/tothi/1a206791…

We updated the agents and added them to the channel as well. #cfs #edr ▪️#SentinelOne Windows Agent 25.1.3.334 ▪️#CarbonBlack EDR 7.9.0 x Linux Sensor 7.4.0 x macOS Sensor 7.4.0 ▪️#CrowdStrike Falcon Sensor 7.29 x Linux 7.29 x macOS 7.29


Slide: powerofcommunity.net/2025/slide/x-8… Thanks for the fantastic conference @POC_Crew :)
Slides from @n0psledbyte, @st424204 & @Peterpan980927 at @codeblue_jp talk are also up: “Dancing with Exynos Coprocessor: Pwning Samsung for fun and ‘profit’” github.com/star-sg/Presen… Shout-out to @rainbowpigeon_ for contributing a lot in this research during his internship.
Inspired by this talk youtube.com/watch?v=9pyR_C…, I wrote some (janky) heuristics that might aid in shellcode detection. github.com/winterknife/SN… In this example below though, it works as intended.

How Windows DLL works #dfir #infosec #malware winitor.com/pdf/DynamicLin…

In an attempt to hide the spyware operator's identity, all data is relayed through a chain of anonymization servers called the “CNC Anonymization Network.” Since the spyware relies on browser exploits, the operator must trick the victim into opening the malicious link; if the…

Ongoing research and technical investigations by Amnesty International indicate that advertisement-based infection methods are being actively developed and used by multiple mercenary spyware companies and by certain governments that have built similar ADINT infection systems.…

Our team discovered CVE-2025-13032, an LPE in the Avast sandbox driver! Read the story of a SYSTEM token heist involving a break-in and escape from the antivirus sandbox. Full details: safateam.com/intelligence-h… #CVE #LPE #Antivirus #KernelExploit #WindowsSecurity
The AdaptixC2 model allows you to develop your own agents and listeners. There are already several similar extenders from the community, and two blogs describing the creation process. For example p0142.github.io/posts/lamperlv…
p0142.github.io
Lessons from Perlyite(Building a custom Adaptix agent)
Process of developing a custom agent for the Adaptix C2. Creating a listener, getting a callback, and basic command execution.
Vercel is questioning whether or not a WAF bypass is possible... Pushed an update that uses a payload from @SLCyberSec research team (specifically @hash_kitten). Payload has been running for @assetnote customers for last 18h. github.com/assetnote/reac… use --vercel-waf-bypass flag
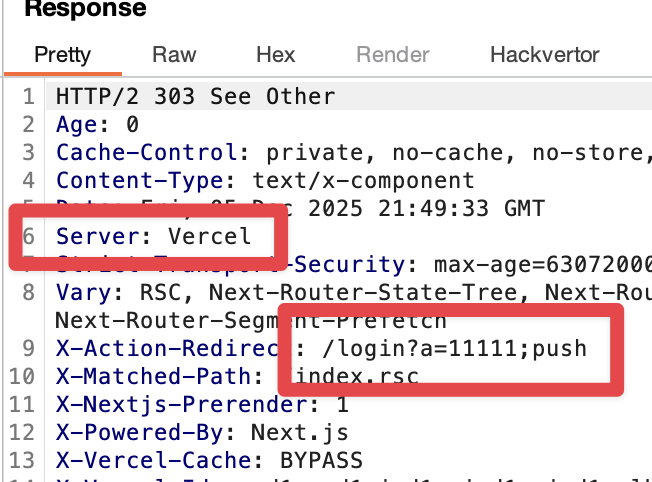
DM’d you. You have a working repro for bypassing Cloudflare but not Vercel. Would love to correct the record or see the evidence.
Can't Stop the ROP: Weaponizing ROP on Windows to Bypass System DLLs x.com/i/broadcasts/1…
Pixel 8 kernel debugging with GDB over serial connection xairy.io/articles/pixel… Credits @andreyknvl #cybersecurity


try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

Bypassing AMSI with Guard Pages. Combining Vectored Exception Handler to handle exceptions generated by PAGE_GUARD set on AmsiScanBuffer() memory leads to flow control over the said function. A post by Leon Weinmann (ShigShag). Source: shigshag.com/blog/amsi_page… #redteam…

Windows secrets extraction: a summary After compromising a Windows host and having obtained local admin privileges, secrets extraction is usually the first step performed to elevate privileges in the context of an ad domain or to perform lateral movements inside an internal…

An unauthenticated RCE PoC for the React vuln (CVE-2025-55182) is now public. Confirmed to work on my test setup (Next.js 16.0.6 with React 19.2.0).
pre-auth RCE (CVE-2025-9242) stack buffer overflow vulnerability in WatchGuard Fireware OS labs.watchtowr.com/yikes-watchgua… Credits @watchtowrcyber #infosec

United States Xu hướng
- 1. Jalen 19.3K posts
- 2. #WWERaw 19.6K posts
- 3. Chargers 28.7K posts
- 4. #FlyEaglesFly 6,840 posts
- 5. Philip Rivers 10.8K posts
- 6. Bradley Bozeman N/A
- 7. AJ Brown 2,319 posts
- 8. Dragon Lee 2,590 posts
- 9. #PHIvsLAC 1,092 posts
- 10. Saquon 3,298 posts
- 11. The Usos 1,055 posts
- 12. Herbert 10.6K posts
- 13. #BoltUp 2,327 posts
- 14. Cooper DeJean N/A
- 15. Nakobe Dean N/A
- 16. Rudy Gobert N/A
- 17. #MondayNightFootball N/A
- 18. Piers 54.7K posts
- 19. Fumble 8,817 posts
- 20. Mark Williams N/A
Something went wrong.
Something went wrong.