CTF Security
@ctf_sec
Information Security | Cyber Security | Web App Pentesting |
你可能會喜歡
⚠️ New video alert! ⚠️ Just uploaded a detailed walkthrough of @hack_sparo Death Note challenge on THM! 🚀 File upload exploits, SSH Misconfig, File immutability & Append Only attributes and Simple Docker breakouts. Check it out with the link below! 👇 youtu.be/emBZdoqjsCc
Hijacking Eureka User Management Microservices and Heapdump Memory Leak Analysis youtu.be/cZUE7QYiktc?si…

youtube.com
YouTube
Eureka Microservices Exploit & Heapdump Memory leak | Eureka Hackth...
Exploiting Path Traversal on Ruby on Rails 7.1.4 to Access config/database.yml – Leaking Database Credentials
Upload alert on @ctf_sec youtu.be/H8qImbdex_o?si…

youtube.com
YouTube
From F’s to A’s | Hacking Natasha’s Way into Hacker Camp - OSUSEC CTF...
What if you could log in as anyone, make yourself an admin, and change grades? Login bypass, tweaking session, decrypting user IDs, and rewriting student grades in the DB. youtube.com/@ctf-sec Drops at 12 AM! Stay tuned. #ctfsec #websec #cybersecurity #session #sqli

If the target system is running Google Chrome Debugger with specific port, we can port forward and may be able to retrieve sensitive data in browser debugging mode. exploit-notes.hdks.org/exploit/linux/…

Sometimes it's just right in front of you. EFCC Hacked Phantom
Happy New Year from @ctf_sec Here’s to a BIG 2025 filled with growth, learning, and responsible hacking. Let’s crush new challenges and level up together. Stay sharp! 💻 #BIG2025 #HappyNewYear2025 #CyberSecurity

Breaking down the Pizza Paradise challenge from Intigriti CTF 2024. Client-side validation flaws, hashing scripting credential leakage, and path traversal exploits. youtu.be/5TMSZWVRpvU?si…
youtube.com
YouTube
Hacking Pizza Paradise: Exploiting Client-Side Validation & Path...
why this SQL get paid 15K and my SQL get paid 2K on the same scope.... we should understand that its all the time depends on the impact not the bug it self Ex: impact of SQL injection in a **store app** not like impact in a **docs app** Ex: /.git/ bug ==> in general its a P3…
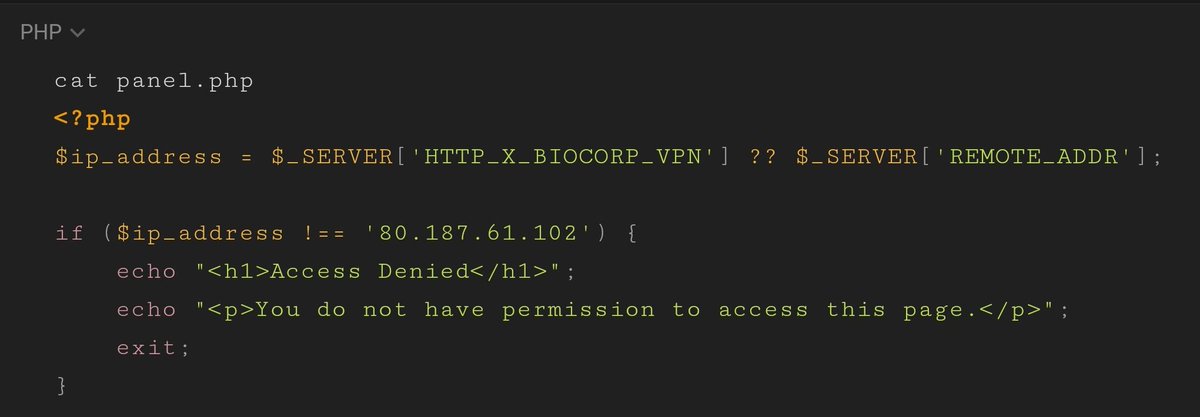
How would you bypass this XSS filter? #XSS #Websecurity #ctfseurity #ctfsec

Last Thursday's Twitch live stream on hacking Ticketastick hacker101 CTF is now available on both Twitch and YouTube! Watch it anytime and catch all the action. Don't forget to follow and subscribe! Twitch: twitch.tv/ctfsec YouTube: youtu.be/s1Fab1UbiMU?si…

File Inclusion to PHP Remote Code Execution (RCE): Gaining Control and Executing Arbitrary Commands. youtu.be/7e1XA7eIyhU #Webappsec #php #webhacking
Hey amazing hackers ! 👋What have you hacked recently or what are you struggling with?? let me know in the comments below 🧨🔥
Check out @r007User's insightful explanation on the security risks of using string interpolation and setting subprocess call(shell=True) in Python. Essential for anyone invested in secure coding practices youtu.be/SaZDeUMEXJY
Exciting update! 🚨 Our latest tutorial on Exploiting Blind SQL Injection to Execute OS Commands is now live. Learn how to turn a vulnerability into full system control youtu.be/SaZDeUMEXJY

I don't usually use Ghauri for SQL, but I'm giving it a try to see how it fits into my toolkit.

United States 趨勢
- 1. $CHA 1,131 posts
- 2. #TORQSports N/A
- 3. Nancy 82.5K posts
- 4. Supreme Court 122K posts
- 5. Argentina 475K posts
- 6. Banish 1,504 posts
- 7. Waddle 4,794 posts
- 8. Malcolm Brogdon 4,375 posts
- 9. #PokemonGO 3,795 posts
- 10. SCOTUS 38.5K posts
- 11. #TWICExVictoriasSecret 21.4K posts
- 12. #VSFashionShow 37.1K posts
- 13. Olave 3,930 posts
- 14. Big Balls 30K posts
- 15. TWICE LIGHTS UP VSFS 20.4K posts
- 16. #ClockTower1Year N/A
- 17. Martha 22.8K posts
- 18. Voting Rights Act 39.3K posts
- 19. Biker Boyz N/A
- 20. Russ 20.7K posts
Something went wrong.
Something went wrong.