#websecurity search results
Website maintenance is essential. Security updates protect the site, content updates keep it relevant, and structural reviews maintain its value for the business. #WebsiteTips #WebSecurity
Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
Your website needs regular maintenance to stay fast, secure, and reliable. It’s the small things that prevent big issues. Keep your site healthy, and it’ll keep your business running smoothly. #WebsiteMaintenance #WebSecurity #SiteHealth #SquidDigital #WebTips

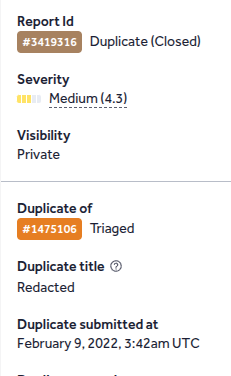
Original report submitted on Feb 9, 2022, when I didn’t even know what bug bounty was 😁😁 The bug was fixed, but now I found a bypass. As the original report is in triaged state, @HackerOne marked this as duplicate. #BugBounty #HackerOne #WebSecurity #Infosec #Bypass
Enjoy your shopping on Black Friday🛒🛍️ Just make sure every script running on your site is actually yours 😉 #blackfriday #websecurity #cybersecurity

Play The Shai-Hulud 2 Game: shai-hulud-data-crawl.lovable.app #shaihulud #CyberSecurity #websecurity
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

Regular website updates are critical. They ensure the site remains relevant, secure, and accurately reflects the business's current focus and activities. #WebsiteTips #WebSecurity
Gov websites need more than flashy CMS features. ✅ Drupal: strong on roles, workflows, security by design. ✅ WordPress: quick, but needs strict upkeep. 🔐 Both can be secure—if managed well. 🔗 bit.ly/4ogXgwt #Drupal #GovTech #WebSecurity

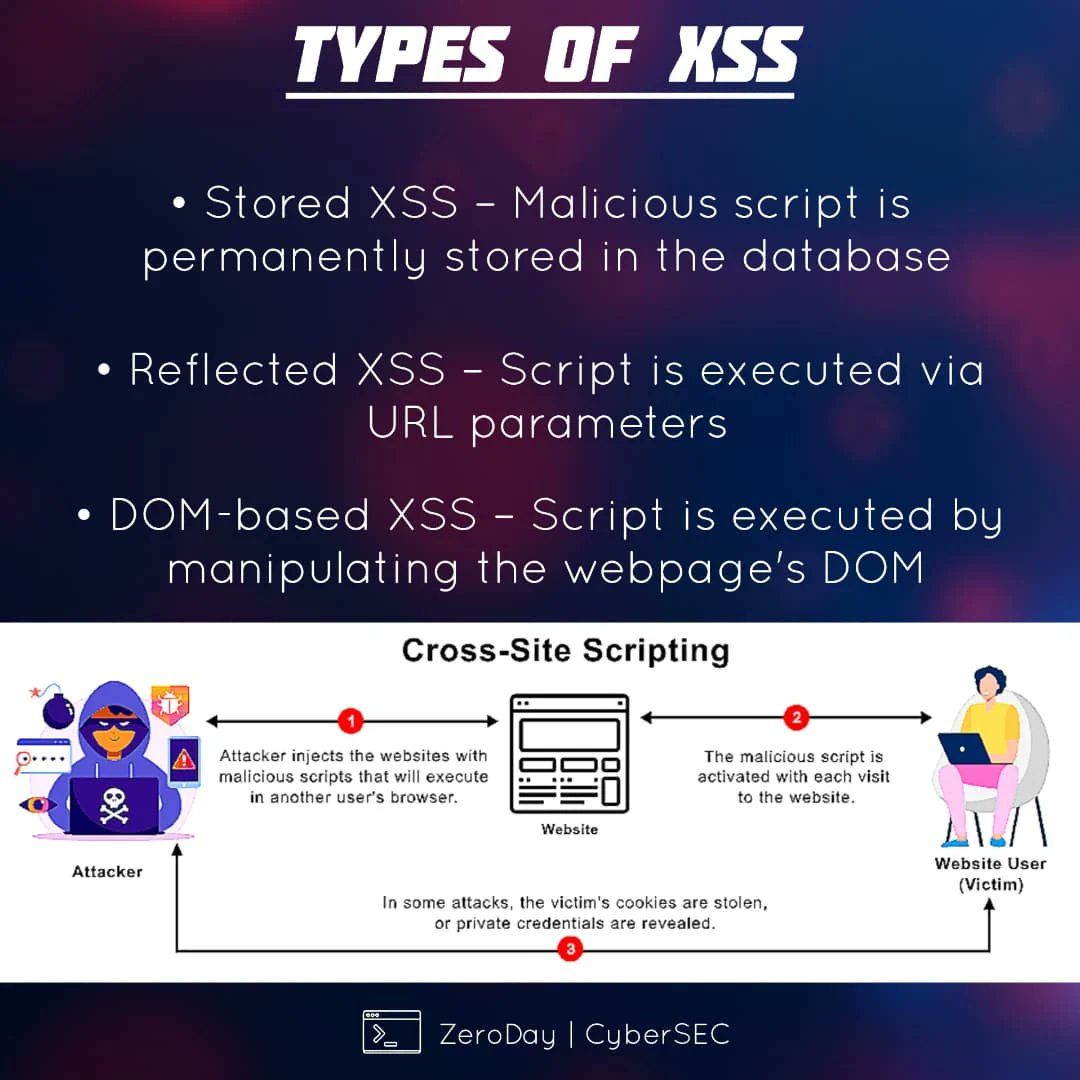
⚠️ Understanding XSS — Cross-Site Scripting Explained Cross-Site Scripting (XSS) is one of the most persistent and impactful web application vulnerabilities, appearing consistently in the OWASP Top 10. 🔖 #infosec #cybersecurity #websecurity #XSS #OWASP #pentesting #appsec



How does File Upload Bypass work? See the full workflow: 1. Setup Netcat listener. 2. Exploit restricted file extension (e.g., .php.jpg). 3. Trigger Remote Code Execution (RCE) to get a www-data shell. #Cybersecurity #WebSecurity
Our web development & IT support services keep your site running smoothly, so you can focus on growing your business, not fixing it. Learn more at htc.ca #IT #webinfrastructure #websecurity #webservices

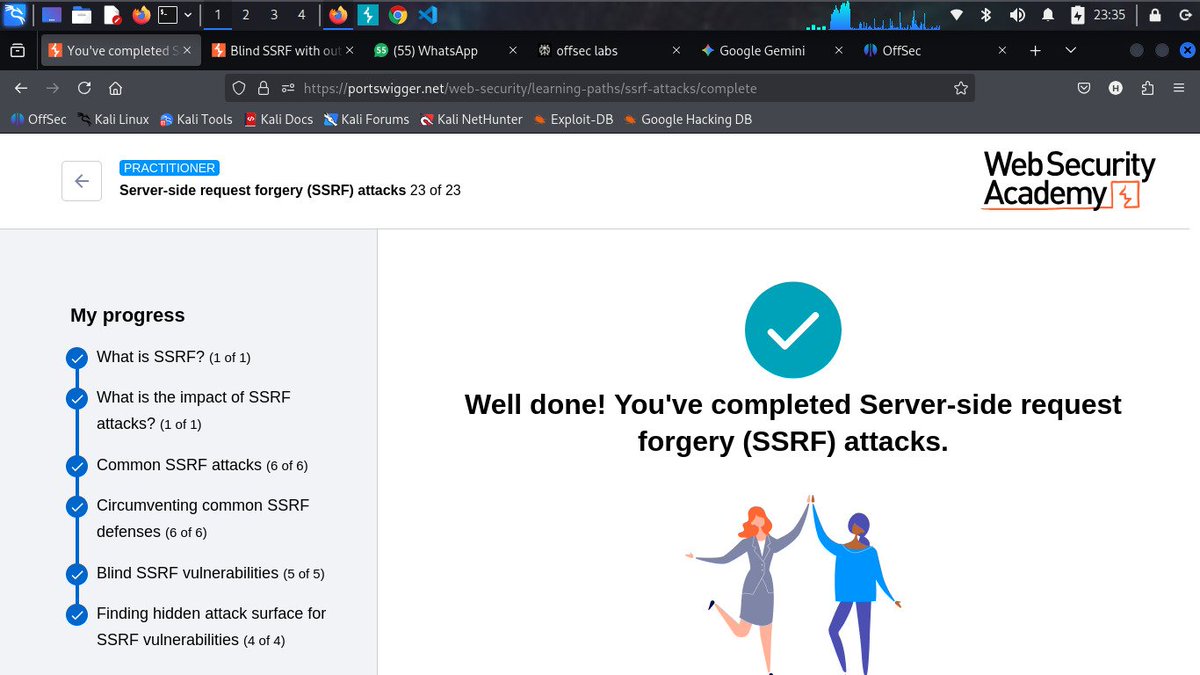
#Day4ofLearningCyberSecurity Today I completed the SSRF module and began the authentication module Web security has been a joy with @PortSwigger making it easy @commando_skiipz @h4ruk7 @_0b1d1 @cybergirl_io #CyberSecurity #WebSecurity #BugBounty #InfoSec #Hacking
🔎 100 Days of Cybersecurity | Day 11: Learned how cookies & sessions keep users logged in since HTTP is stateless. This is key in understanding web security risks like session hijacking. #100DaysOfCybersecurity #EthicalHacking #WebSecurity

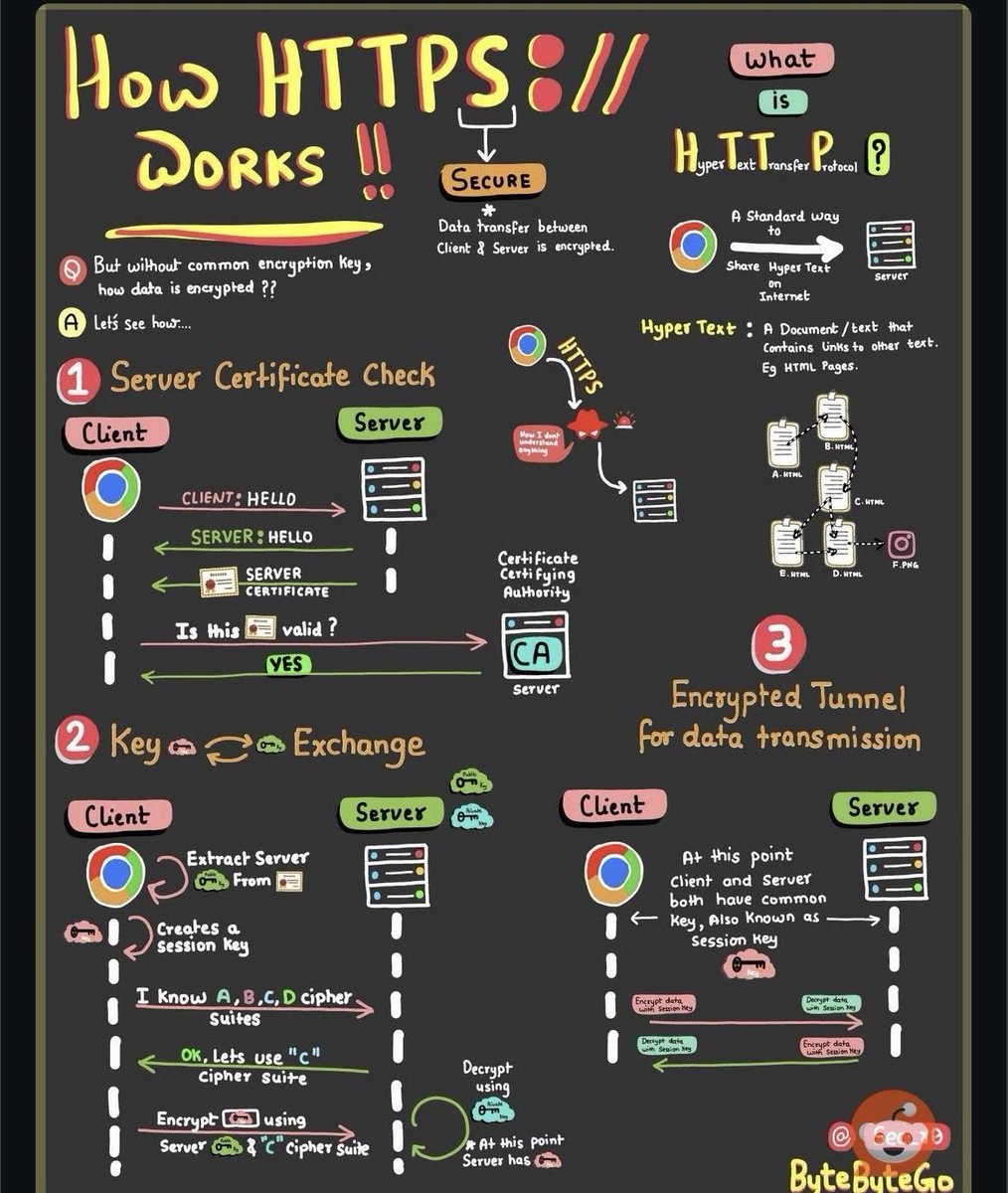
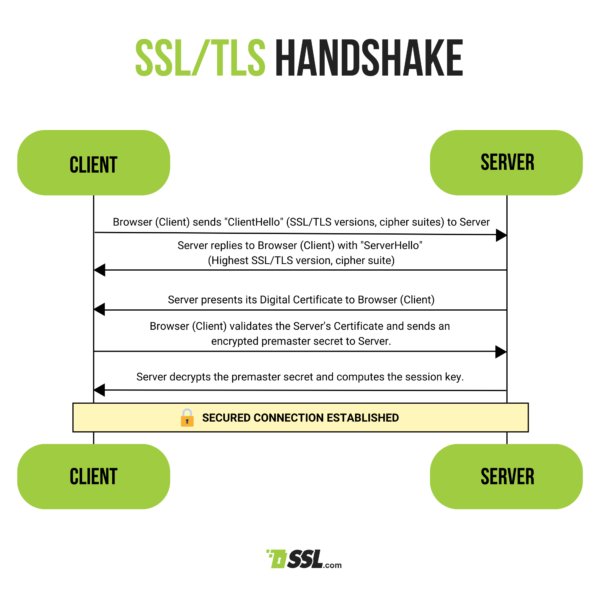
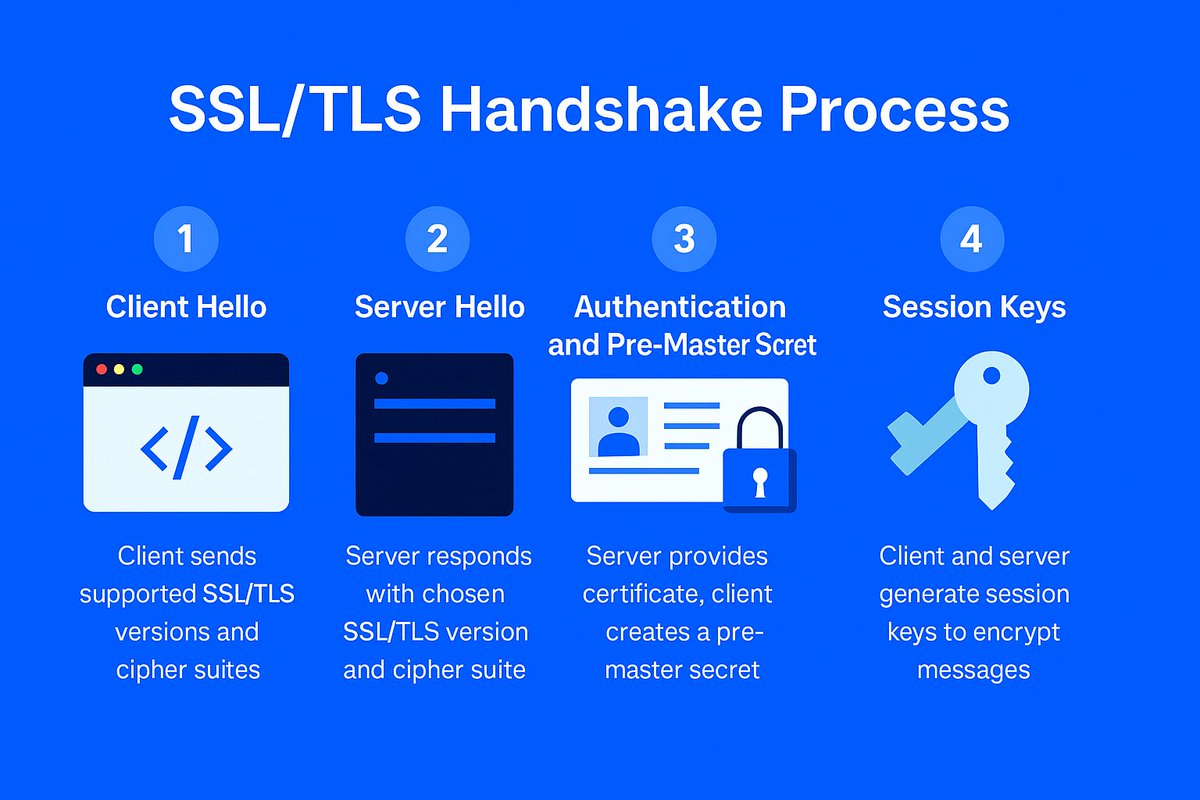
🔎 100 Days of Cybersecurity & Ethical Hacking | Day 12: Learned how the SSL/TLS handshake secures HTTPS connections. Client & server verify identity ➝ agree on encryption ➝ create secure session 🔐 #100DaysOfCybersecurity #EthicalHacking #WebSecurity
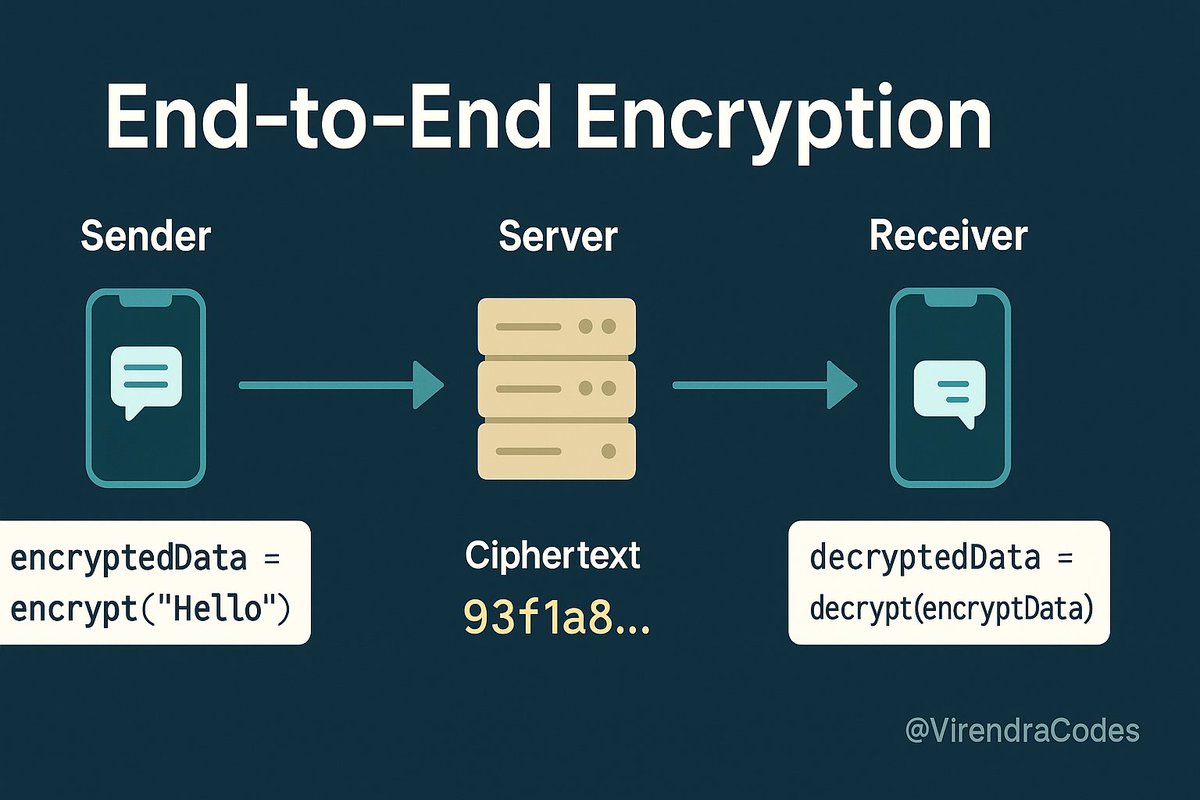
End-to-end encryption is one of the strongest ways to protect user data. It ensures that only the sender and receiver can read the message, not even the server in the middle. Every developer should understand how it works and when to use it. #E2EE #WebSecurity
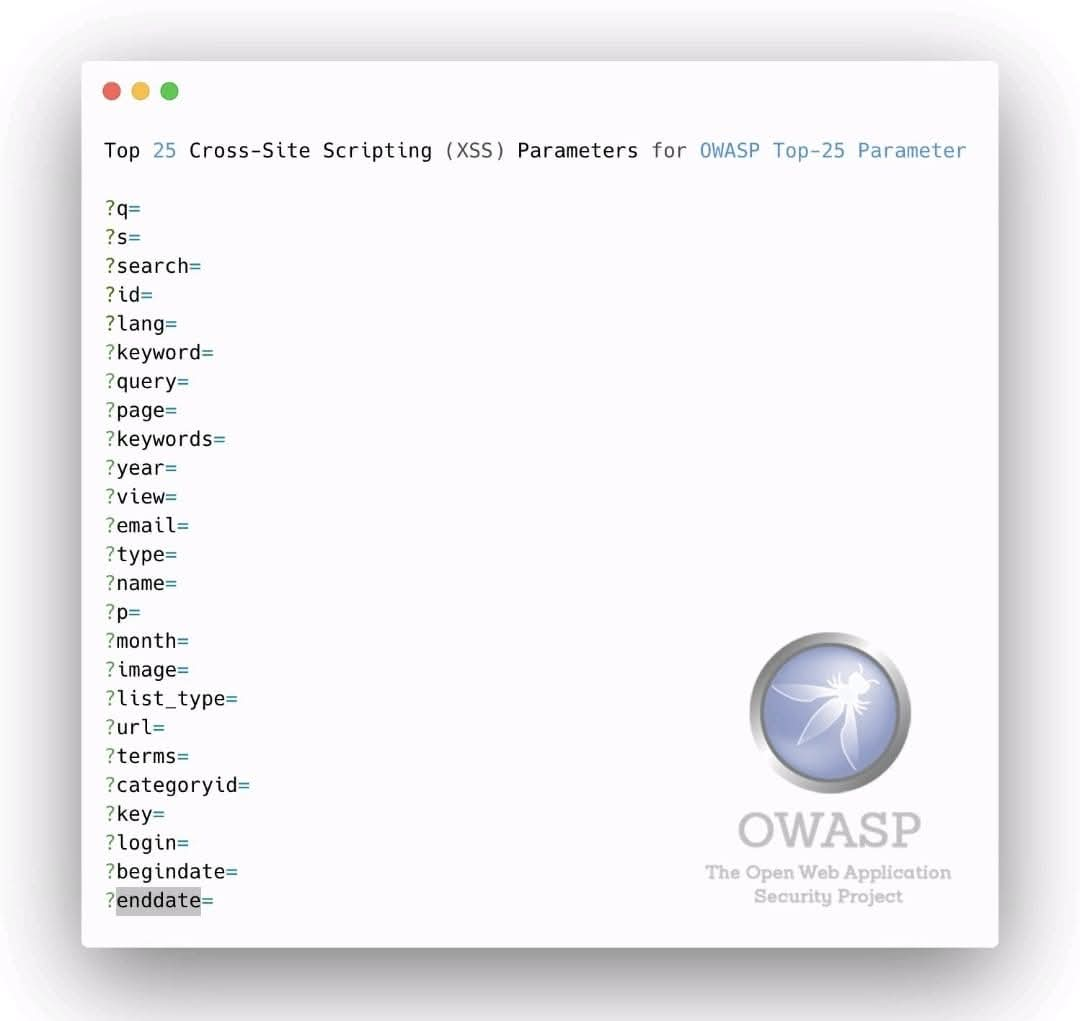
🪰 OWASP Top 25 Parameters A concise overview of the most commonly targeted web parameters identified in security testing and analysis. 🔖 #OWASP #WebSecurity #AppSec #CyberSecurity #InfoSec #SecureDevelopment

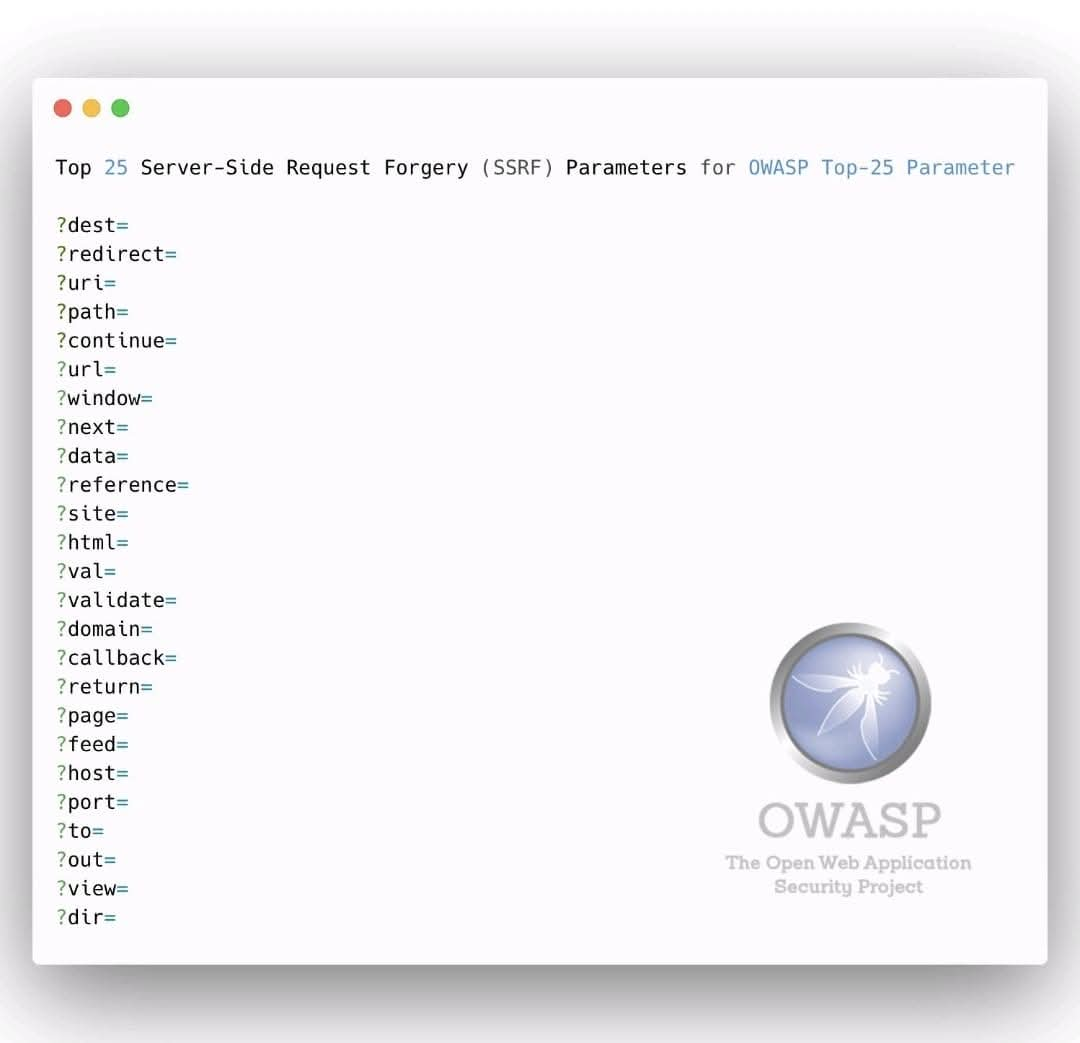
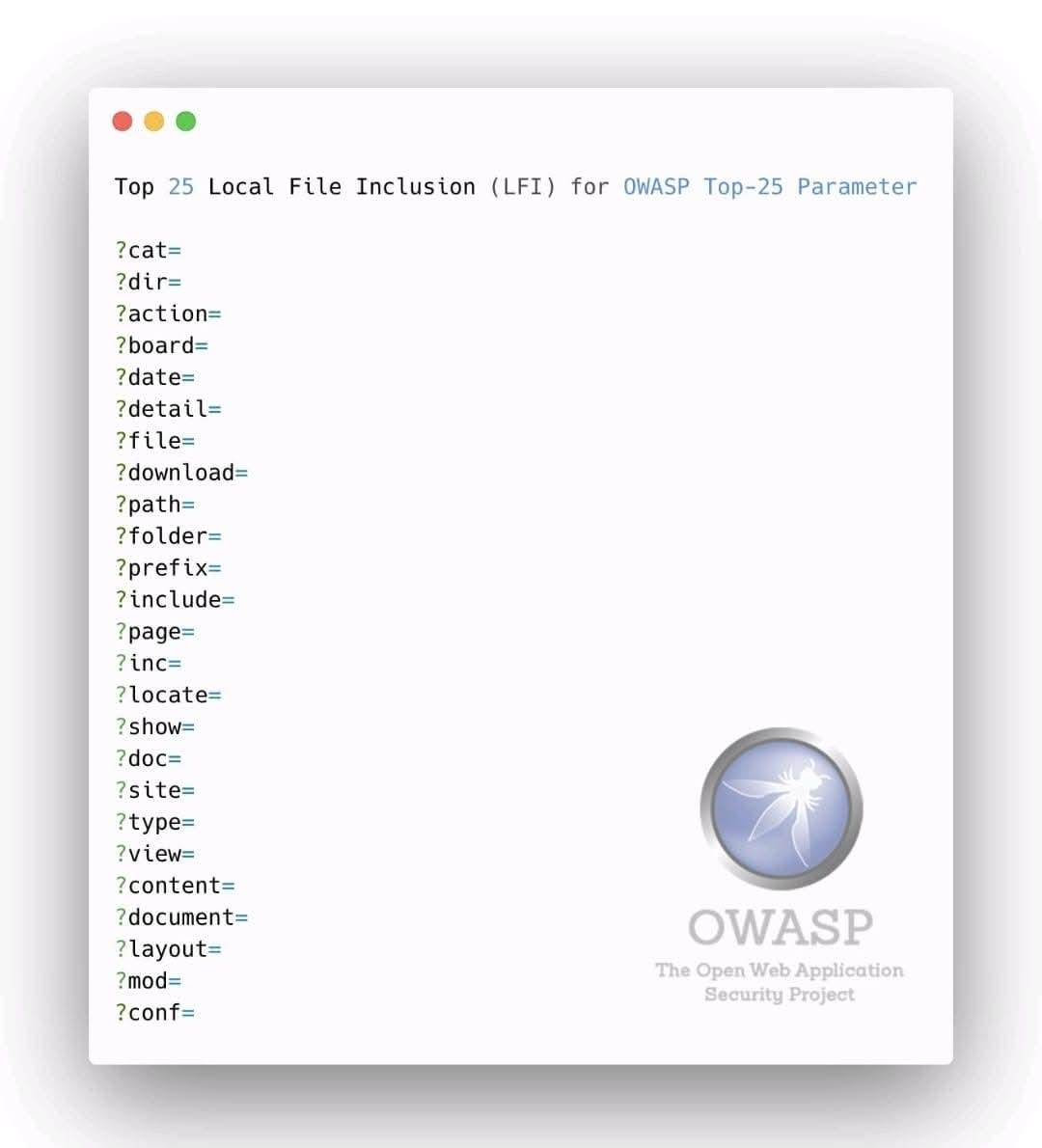
Never push .env. Never store secrets in frontend. Never trust user input. #CyberSecurity #WebSecurity #BestPractices
Enjoy your shopping on Black Friday🛒🛍️ Just make sure every script running on your site is actually yours 😉 #blackfriday #websecurity #cybersecurity

💡 Authentication in 2025: 🚫 Don't: Roll your own ✅ Do: NextAuth.js, Clerk, Auth0 🚫 Don't: Plain text passwords ✅ Do: bcrypt with salting 🚫 Don't: JWT in client ✅ Do: httpOnly cookies #WebSecurity #Auth
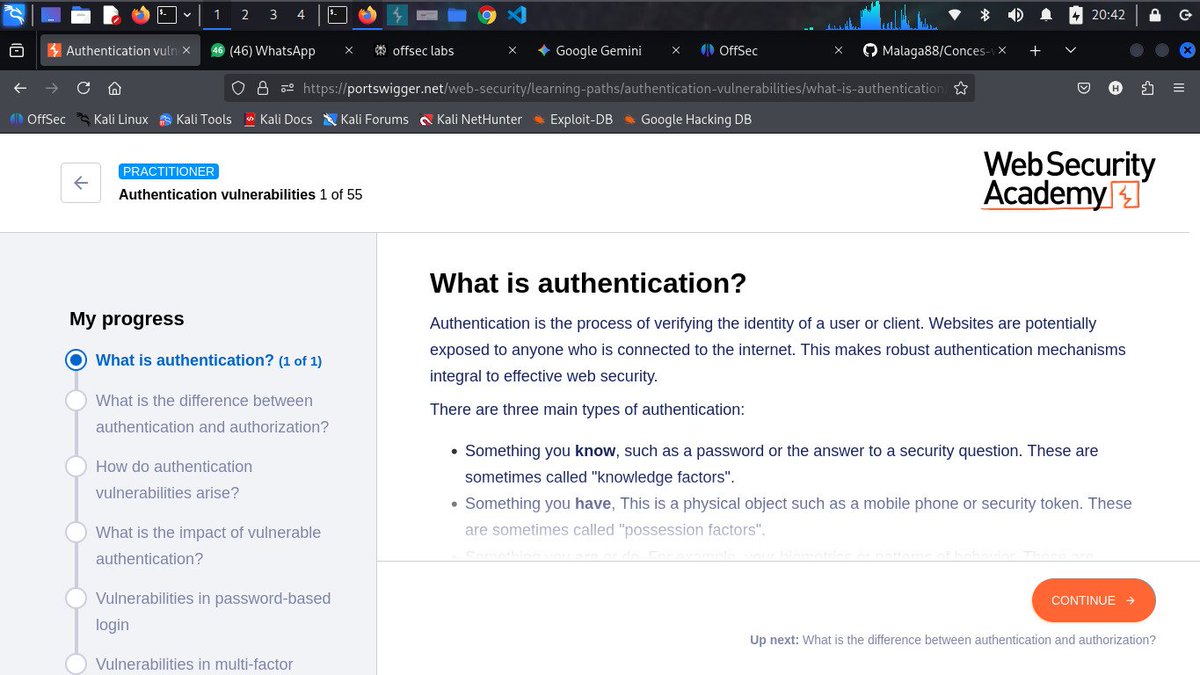
#Day5ofLearningCyberSecurity Today was a rather disappointing day I continued the authentication module but couldn't solve the labs since I use the community version @commando_skiipz @h4ruk7 @_0b1d1 @cybergirl_io #CyberSecurity #WebSecurity #BugBounty #InfoSec #Hacking
Gov websites need more than flashy CMS features. ✅ Drupal: strong on roles, workflows, security by design. ✅ WordPress: quick, but needs strict upkeep. 🔐 Both can be secure—if managed well. 🔗 bit.ly/4ogXgwt #Drupal #GovTech #WebSecurity

Our web development & IT support services keep your site running smoothly, so you can focus on growing your business, not fixing it. Learn more at htc.ca #IT #webinfrastructure #websecurity #webservices

Play The Shai-Hulud 2 Game: shai-hulud-data-crawl.lovable.app #shaihulud #CyberSecurity #websecurity
Worried about XSS? Sanitize input, use templating engines that auto-escape, and add a solid Content-Security-Policy. #websecurity #XSS
30,000 websites get hacked every day. At Developyn, we keep your business safe with secure code, robust systems & ongoing monitoring. Focus on growth, leave security to us. Learn more: developyn.com #CyberSecurity #WebSecurity #DataProtection

100 Web App Exploits Every Pentester Should Be Able to Sniff Out thexssrat.podia.com/bf?coupon=BF If your target has even one of these… dinner is served. #websecurity #bugbounty #infosec #cybersecurity #pentesting #ethicalhacking
Day 82 —XSS Deep Dive ⚡ Reflected, Stored, Blind, each XSS type shows how powerful one script can be. “XSS: where one line of code can shift the whole story.” #EthicalHacking #WebSecurity

#Day4ofLearningCyberSecurity Today I completed the SSRF module and began the authentication module Web security has been a joy with @PortSwigger making it easy @commando_skiipz @h4ruk7 @_0b1d1 @cybergirl_io #CyberSecurity #WebSecurity #BugBounty #InfoSec #Hacking


Just wrapped up Intigriti Challenge 1125 — unsigned JWT + Jinja2 SSTI chained into full RCE. Forged admin access, escaped the sandbox, ran system commands, and automated the exploit with a tiny Go PoC. Thanks @intigriti Writeup; hackmd.io/@KutaySec/rJZt… #bugbounty #websecurity
Your website needs regular maintenance to stay fast, secure, and reliable. It’s the small things that prevent big issues. Keep your site healthy, and it’ll keep your business running smoothly. #WebsiteMaintenance #WebSecurity #SiteHealth #SquidDigital #WebTips

Original report submitted on Feb 9, 2022, when I didn’t even know what bug bounty was 😁😁 The bug was fixed, but now I found a bypass. As the original report is in triaged state, @HackerOne marked this as duplicate. #BugBounty #HackerOne #WebSecurity #Infosec #Bypass

Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

When IDOR isn’t just IDOR… it’s Mass Wipe + Feature Hijack 🚨 Reward: $200 🪙 Big thanks to @hackenproof 🙏 More drops coming soon… stay tuned ⚡ #BugBounty #WebSecurity #Hacker #InfoSec #Vulnerability #EthicalHacking #CyberSecurity #Pentesting #IDOR #Exploits #TechNews



Just 4 of your most-visited websites can identify you online - no name needed. Is online anonymity just an illusion? 👀🔍 news-medical.net/news/20251017/… #Privacy #WebSecurity

HTTP vs HTTPS—are you still running your site without encryption? It’s not just about the padlock—it affects SEO, trust, and user safety. What’s your site using? ⬇️ #WebSecurity #TechTips #HTTPS

🔎 100 Days of Cybersecurity | Day 11: Learned how cookies & sessions keep users logged in since HTTP is stateless. This is key in understanding web security risks like session hijacking. #100DaysOfCybersecurity #EthicalHacking #WebSecurity

Enjoy your shopping on Black Friday🛒🛍️ Just make sure every script running on your site is actually yours 😉 #blackfriday #websecurity #cybersecurity

#Day4ofLearningCyberSecurity Today I completed the SSRF module and began the authentication module Web security has been a joy with @PortSwigger making it easy @commando_skiipz @h4ruk7 @_0b1d1 @cybergirl_io #CyberSecurity #WebSecurity #BugBounty #InfoSec #Hacking


🧵 Everyone’s building the future of Web3. But only one project is protecting it before it’s even attacked. Let’s talk about @Abatis_ABTU the silent firewall of the blockchain. 🔥 $ABTU #CyberSecurity #websecurity

WordPress spam isn’t just noise — it’s lost time, lost users, and lost trust CleanTalk stops spam quietly — in the cloud, not on your forms. -Fast setup - Real protection - 200K+ WordPress sites trust CleanTalk cleantalk.org #wordpressapi #WebSecurity #AntiSpam…

Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity
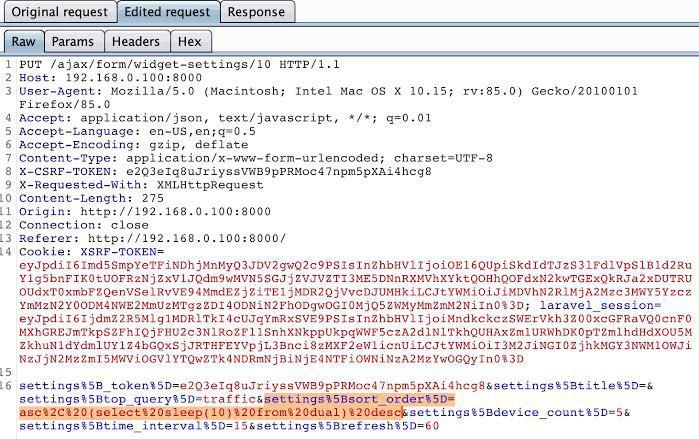
🔎 100 Days of Cybersecurity & Ethical Hacking | Day 12: Learned how the SSL/TLS handshake secures HTTPS connections. Client & server verify identity ➝ agree on encryption ➝ create secure session 🔐 #100DaysOfCybersecurity #EthicalHacking #WebSecurity


If a proxy is cheap, can it still keep up with your viral cat thread on Twitter? 🐱💨 Source: topdealsnet.com/blog/best-chea… #TechSavvy #WebSecurity #BudgetTech #CheapProxies #proxy #proxies

Something went wrong.
Something went wrong.
United States Trends
- 1. Ravens 56.5K posts
- 2. Lamar 45.1K posts
- 3. #heatedrivalry 9,256 posts
- 4. Joe Burrow 20K posts
- 5. ilya 11.9K posts
- 6. shane 14.4K posts
- 7. Zay Flowers 4,043 posts
- 8. #WhoDey 3,554 posts
- 9. Cowboys 91.7K posts
- 10. Derrick Henry 4,389 posts
- 11. Perine 1,570 posts
- 12. Hudson 10.5K posts
- 13. Zac Taylor 2,599 posts
- 14. AFC North 2,279 posts
- 15. Harbaugh 3,051 posts
- 16. Sarah Beckstrom 206K posts
- 17. Mahomes 33.6K posts
- 18. #CINvsBAL 2,672 posts
- 19. Boozer 5,403 posts
- 20. Tinsley 1,607 posts