dreadl0ck
@dreadcode
Tortures computers for fun and profit. Interested in network security monitoring, machine learning, Golang and Rust. Shellscript ninja. Will debug for food.
قد يعجبك
Published my Bachelor Thesis: "Implementation and evaluation of secure and scalable anomaly-based network intrusion detection" along with my network traffic analysis framework: github.com/dreadl0ck/netc… #golang #IDS #NSM #DeepLearning #ML
Attacking UNIX Systems via CUPS, Part I evilsocket.net/2024/09/26/Att…
evilsocket.net
Attacking UNIX Systems via CUPS, Part I
Attacking UNIX Systems via CUPS, Part I
I'm glad everyone has discovered memory safe languages after several decades. Now can we start looking at secure package management or are we just going to import memory safe rando libs from ninja876 on Github forever?
My dystopian vision of an AI-powered future is that LLMs drives down the cost of generating long text even further, and the only way for readers to keep up is to use LLMs to summarize.
Okay here's a ridiculous (but true) take: word processing is bad. Before it, document length was bounded by the human capacity to copy long-form text. After word processing, the tax & legal codes grew without check. And became incomprehensible to anyone but career experts.

Guest: “Is that a RAM stick glued to your door?” Me: “Yes. Old memories.”

Best security quote I heard this week: "Do you want to mitigate against an auditor, or against an attacker?"
Bellingcat and investigative partners @derspiegel and @the_ins_ru have discovered a hitherto secretive group of engineers involved in Russian missile strikes on Ukraine. These strikes have killed hundreds and left millions without heating or power bellingcat.com/news/uk-and-eu…
You can force any v8/Electron process to execute arbitrary js code (child_process, http, etc) by forcefully enabling and abusing the builtin debug mechanism ... here's VS Code executing Calc, but I suspect any Electron app is susceptible 🔥 it works with SIP enabled on macOS

@BadgeteamNL thanks for the great #MCH2022 badge - here's my Music Computing Handheld app, to be found in the Hatchery in ESP32 - Games. Happy soloing
Do you know you can set up a custom Transform server in #Maltego? The #DittoTRX Transform developed by @dreadcode can be used to investigate #IDNHomographAttack and imposter domain on various websites. Learn how to set it up here: maltego.com/blog/dittotrx-…
The Trojan Source vulnerability allows supply-chain attacks on software written in C, C++, Go, Java, Javascript, Python and Rust. We're releasing details after a 99-day coordinated disclosure period, and some of these compilers will be patched quickly. See lightbluetouchpaper.org/2021/11/01/tro…
Wow, just realized C is turning 50 next year. Not sure how to tell students that we're learning about security problems caused by a language that's half a century old.
Memory safety in a huge codebase is hard. We've published some work and an update on our work in the Chromium codebase - security.googleblog.com/2021/09/an-upd….
We're releasing CapLoader 1.9 today! 🔁 Better detection of periodic beacons 🔍 More L7 protocols identified 🚀 Faster 🛠️ Improved filtering of flows 🔭 OSINT lookups w/ CIRCL, ThreatFox, RIPEstat etc. netresec.com/?b=2159bda
Ever dreamed about analysing a PCAP file properly in Maltego? Next netcap release will have a full blown Maltego integration, currently have ~200 entities, ~120 local transforms and 4 machines :) #madewithmaltego #golang #netcap



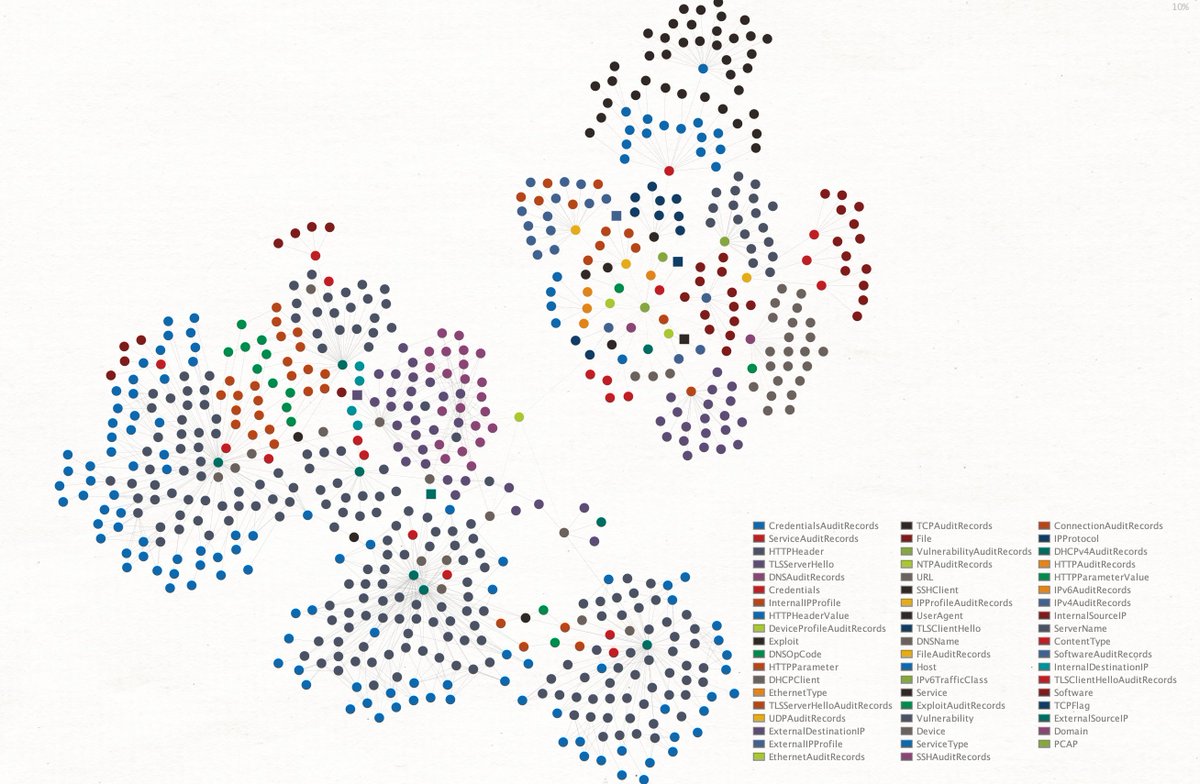
Open sourced my Maltego (@MaltegoHQ) integration for @evilsocket's ditto tool and wrote a blogpost about it: dreadl0ck.net/posts/ditto-trx Happy graphical link analysis! #madewithmaltego #golang #ditto
United States الاتجاهات
- 1. Australia 467K posts
- 2. Hanukkah 148K posts
- 3. Good Sunday 69.2K posts
- 4. Brown University 264K posts
- 5. Naveed Akram 64.2K posts
- 6. #HealingServiceDay 9,382 posts
- 7. Ahmed al Ahmed 13.1K posts
- 8. Muhammad Qasim 21.2K posts
- 9. #sundayvibes 4,146 posts
- 10. Gunther 101K posts
- 11. Globalize the Intifada 10.7K posts
- 12. Blessed Sunday 19K posts
- 13. #SundayThoughts 1,084 posts
- 14. Chrisean 9,190 posts
- 15. Guns 98.5K posts
- 16. Chabad 14.9K posts
- 17. Spurs 79K posts
- 18. Rhode Island 63.8K posts
- 19. #SundayMotivation 1,774 posts
- 20. #DrAllyxJossGawin 111K posts
Something went wrong.
Something went wrong.