JaeRyoung Oh
@h4z3dic
Just a coder and a trader
Tal vez te guste
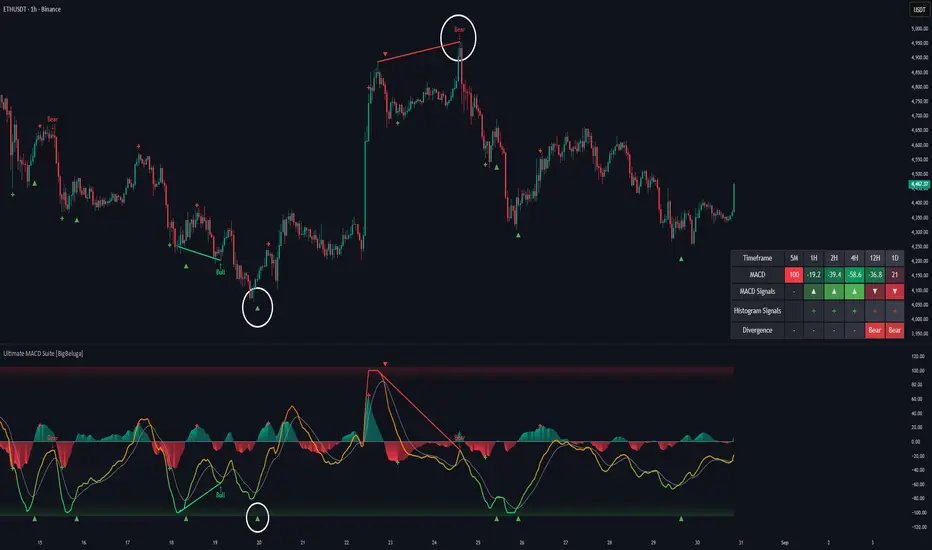
Ultimate MACD Suite 🐳 🐳 🐳 This toolkit goes far beyond standard MACD, helping traders identify trend momentum shifts, exhaustion zones, high-probability reversal areas, and breakout confirmation signals across multiple timeframes simultaneously. tradingview.com/script/ZGKfhFO…
이 글은 개인적으로 현재의 단기자금시장을 이해하는데 매우 중요한 포인트라 생각되어 공유합니다. 꼭 읽어 보셨으면 합니다. 이 글을 읽으시면 현재 왜 로건 총재가 SOFR > TGCR로 변경을 하려고 하는지 왜 이번 SRF의 사용 증가가 은행권이 아닌 “딜러”의 시세 차익 때문이었는지를 보다 쉽게…
일반 레포를 하면 딜러의 대차대조표는 첫 그림처럼 확대됩니다. Sponsored Repo 기능을 활용하면 딜러가 마주하는 대상은 레포차입, 레포대출 모두 중앙청산소(FICC-DPV)가 되면서 대차대조표의 Reverse Repo(레포 대출)과 Repo(레포 차입)을 상계해줘 딜러의 대차대조표는 확대되지 않습니다.…

I'm open-sourcing all my published TradingView indicators. Take the code. Tweak it. Fork it. Feed it to an AI and build something new or modify according to your trading needs. The barrier to entry for creating powerful tools just crashed. github.com/TradeINski/Tra…
Wow, this is exactly what I needed!!!! github.com/caido-communit…
Visual Studio 2026 is now generally available. 🎉 devblogs.microsoft.com/visualstudio/v… Keys: Professional: NVTDK-QB8J9-M28GR-92BPC-BTHXK Enterprise: VYGRN-WPR22-HG4X3-692BF-QGT2V
HOMEWORK: Learn to fish Reversals: bit.ly/MarketReversals Volume shelves: bit.ly/VolumeShelves Anchored VWAP: bit.ly/AnchVWAP Hollow Candles: bit.ly/HllwCndles S/R Flips: bit.ly/SR_flips MACD: bit.ly/MACD_JW Trend Zones: bit.ly/TrendZones

GitHub - OmerYa/Invisi-Shell: Hide your Powershell script in plain sight. Bypass all Powershell security features github.com/OmerYa/Invisi-…
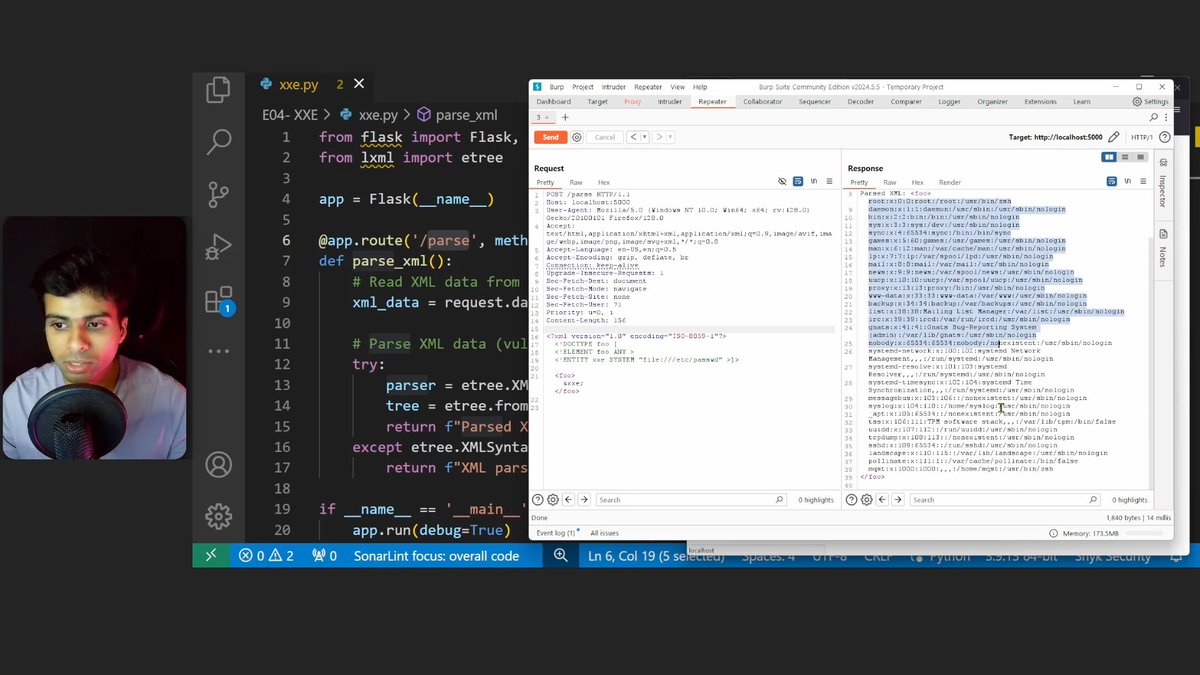
👨💻 If you're a Beginner in Secure Code Review, watch this video. It gives you a basic idea of how to find XXE vulnerabilities during Secure Code Reviews. Video: youtube.com/watch?v=HKDe1z…
NEW FREE INDICATOR ALERT 🐳 🐳 🐳 Volume HeatMap Divergence A smart volume visualization tool that overlays normalized volume data directly on the chart. tradingview.com/script/3DTOFol…
WOW64!Hooks: WOW64 Subsystem Internals and Hooking Techniques cloud.google.com/blog/topics/th…

GitHub - boku7/venom: Venom C2 is a dependency‑free Python3 Command & Control framework for redteam persistence github.com/boku7/venom
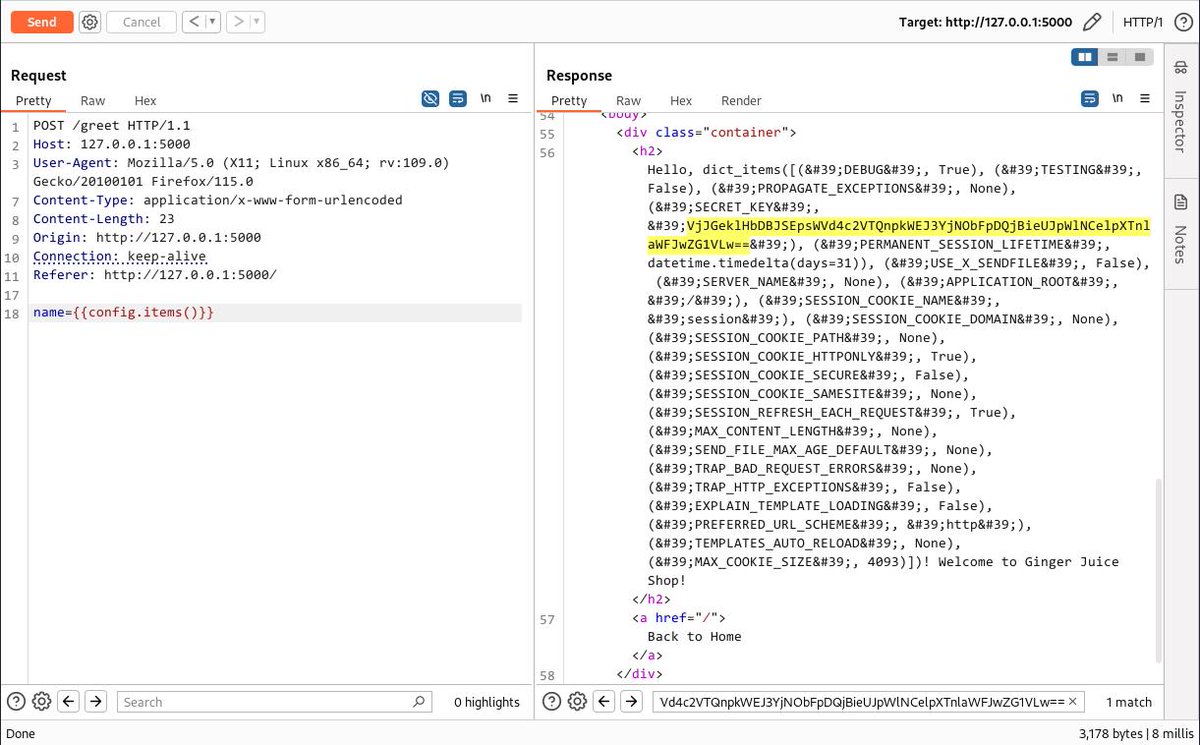
📓 A Complete Guide to Cracking Server-Side Template Injection (SSTI) for Fun & Profit! Blog 1: dr34mhacks.github.io/posts/how-to-e… Blog 2: pmnh.site/post/writeup_s… Practice: ssti.pythonanywhere.com
If you want to get better at finding and bypassing SSRF, take a look at this repo: github.com/cujanovic/SSRF…
''GitHub - DarkCoderSc/OptixGate: Open-source multi-purpose remote access tool for Microsoft Windows'' #infosec #pentest #redteam #blueteam github.com/DarkCoderSc/Op…
Want to learn a way to find those hard-hitting critical vulnerabilities? 🐛 CVE-2025-29927 is a vulnerability in Next.JS that can lead to a complete authorization bypass. Watch the video below to get a quick peek and then try the lab yourself 👇 app.hackinghub.io/hubs/cve-2025-…
한국 최고 엘리트 그룹이 일반인도 이해하기 쉽도록 배려한 ✍️스테이블코인 보고서를 공개했습니다. '코인-스테이블코인-실물경제'로 이어지는 구조와 여기에 따르는 리스크, 해결책, 대안 등 다양한 이야기가 약 157쪽 정도로 정리되어 있으니 꼭 읽어보시기 바랍니다. 최근 미국쪽 금융구조는…


D4m0n/CVE-2025-50168-pwn2own-berlin-2025: CVE-2025-50168 Exploit PoC — Pwn2Own Berlin 2025 - LPE(Windows 11) winning bug. - github.com/D4m0n/CVE-2025…
Dynamic Instrumentation with QBDI - YuriVerse - awsl.rip/reverse-engine…
awsl.rip
Dynamic Instrumentation with QBDI - YuriVerse
Dynamic Instrumentation with QBDI - YuriVerse
United States Tendencias
- 1. Clay Higgins 11.5K posts
- 2. Saudi 212K posts
- 3. #UNBarbie 9,663 posts
- 4. Gemini 3 44K posts
- 5. Jamal Khashoggi 24.6K posts
- 6. #UnitedNationsBarbie 9,827 posts
- 7. Peggy 5,331 posts
- 8. Nicki 87.3K posts
- 9. Mary Bruce 1,800 posts
- 10. Salman 66.2K posts
- 11. Robinhood 5,129 posts
- 12. #NXXT2Run 1,271 posts
- 13. Cloudflare 257K posts
- 14. Shanice N/A
- 15. Merch 66.4K posts
- 16. McTominay 10.2K posts
- 17. Pat Bev 2,034 posts
- 18. Frankie Montas N/A
- 19. Pirates 17.8K posts
- 20. #EpsteinFiles 9,293 posts
Tal vez te guste
-
 Piotr Bania
Piotr Bania
@PiotrBania -
 Jacob Soo
Jacob Soo
@_jsoo_ -
 REhints
REhints
@REhints -
 Ethical Hacker
Ethical Hacker
@offethhacker -
 Alex Matrosov
Alex Matrosov
@matrosov -
 Stephen A. Ridley
Stephen A. Ridley
@s7ephen -
 Vay3t
Vay3t
@vay3t -
 beist
beist
@beist -
 Securityblog
Securityblog
@Securityblog -
 gartzen
gartzen
@Gartzen72 -
 보안프로젝트
보안프로젝트
@ngnicky -
 Alessio
Alessio
@alessio_dp -
 Constantin Milos ♏@Tinolle infosec.exchange
Constantin Milos ♏@Tinolle infosec.exchange
@Tinolle1955 -
 Sanoop Thomas ⠵
Sanoop Thomas ⠵
@s4n7h0 -
 Chanam Park
Chanam Park
@hkpco
Something went wrong.
Something went wrong.