hadOkeN
@kerne1_p4n1c
Against the bugz 🧐 Pentesting , RedTeaming , Infosec lover.
You might like
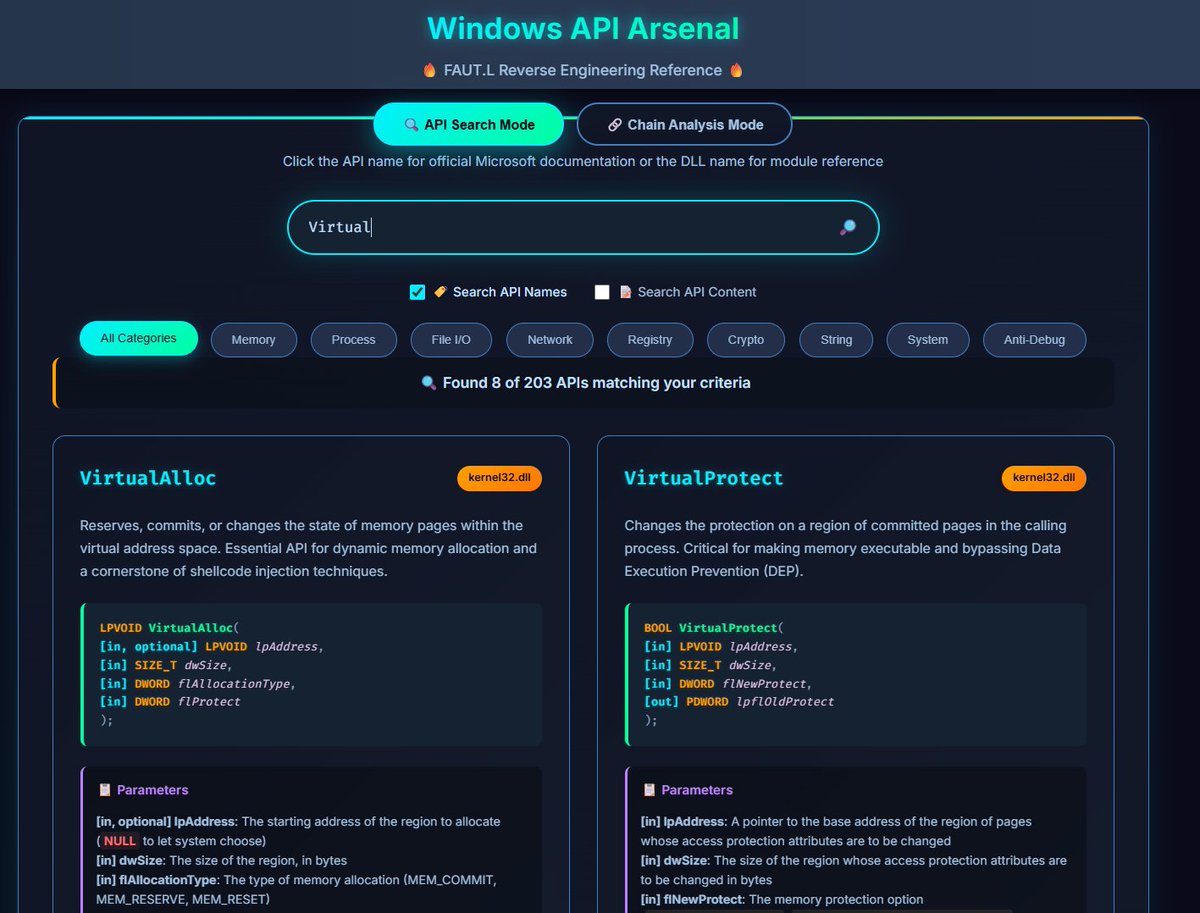
Windows API arsenal by @0x6970 for reversers blog.fautl.com/api-list.html
Reverse engineering the obfuscated TikTok VM : github.com/LukasOgunfeiti…
NEW TOOL: ITOA (Image to ASCII) Convert your images to an ASCII canvas, monochrome or colored, and save them into a separate image. Works on mobile (but large size is more limited than on desktop).
A #vulnerability in VMware ESXi hypervisors has been exploited by #ransomware groups to gain administrative access and deploy #malware. It allows attackers to escalate privileges easily, posing a severe risk to organizations using ESXi. thehackernews.com/2024/07/vmware… #CyberSecurity
Find and execute WinAPI functions with Assembly (Shellcode x64) : print3m.github.io/blog/x64-winap… credits @Print3M_ shellcodes : github.com/Print3M/shellc…


DarkGate loader has the most sophisticated loader we've ever seen. It's over for the anti-virus industry. How would anyone defeat or detect this?!

My new favourite technical drawing tool is Excalidraw.. Just the right amount of unprofessionalism to keep the inner anarchist alive.

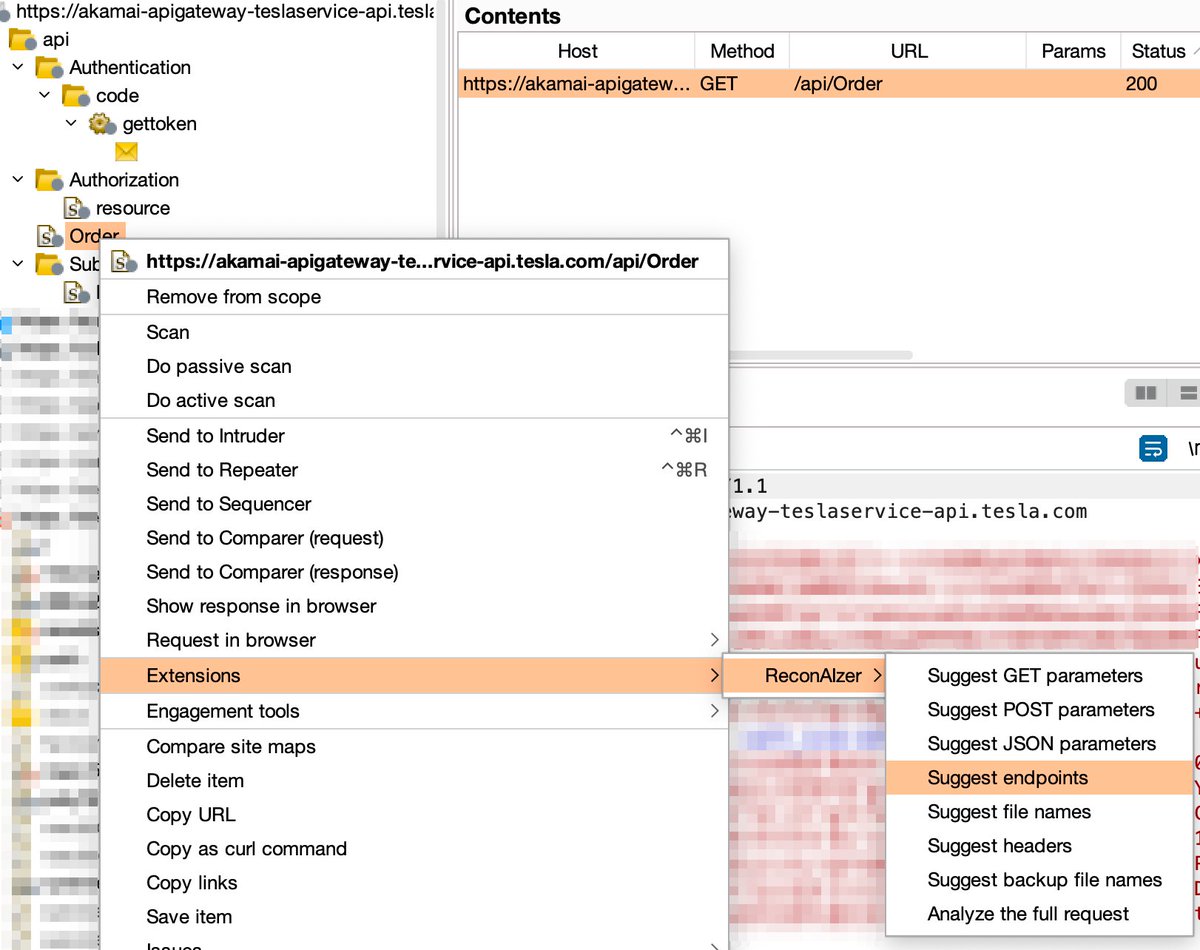
🤯 OpenAI + Burp Suite = welcome to "ReconAIzer" A powerful extension for Burp Suite that leverages OpenAI to help bug bounty hunters optimize their recon process. 🔗Link: github.com/hisxo/ReconAIz… (It's not a serious project, it's just for fun 😂)
Speed up your subdomain port scanning by querying A records from a list subdomains and removing duplicate IP addresses 🏃♀️💨 You can do this easily by chaining subfinder, dnsx, sort and naabu together: subfinder -d <domain> 🔗 dnsx -a -ro 🔗 sort -u 🔗 naabu

CveEventWrite() seems to be the easiest way of putting your own events into the Application Event Log. Nothing to prepare in advance, no special privileges, just two PCWSTRs as params, one call, obvious result. Why cannot the rest of Event Logging API work the same way...?🙄

We’ve launched Maldev Academy Code Search! search.maldevacademy.com We’ve built two projects with the help of this service and posted the code and videos to the GitHub repository below: github.com/Maldev-Academy…


ssh has secrets. Too many to share in one tweet. One of which is how it acts as a serial-line processor for secret keyboard functionality you probably never knew about. For example, why, when you press ENTER and then ~ immediately after, does the ~ not appear right away? Thread…
Believe or not but used to do this a lot as a kid. Shells were hard to buy so my Dad made them on his own. Totally normal back then … now probably someone would call some agency to save my kids from me if I would do this at home 🤷
Reloading brass shotgun shells.
Lets bypass Cortex XDR again! Mortar v3 is out and comes with following features: -Fileless execution -Early Bird APC injection. -Process masquerading. -Supports Named Pipes. -Strings and function calls obfuscation. - covert reload subroutine. -Delay execution techniques.
Our friend @nikhil_mitt hooked us up with MORE stuff to giveaway for the holiday season. We've got 3 vouchers for the CARTP (Azure Red Teaming course). He's the real MVP. Thank you so much 🙏 Comment below for a chance to win Course details: alteredsecurity.com/azureadlab
I updated the EDR telemetry project with corrected telemetry and new additions! See below the changes and upcoming EDRs: ✅ Corrected Trend Micro Telemetry ✅ Corrected ESET Telemetry 🌟 Added Qualys EDR 🎯New Additions Coming Up: 🔜 Sophos EDR 🔜 Cortex EDR Vendors are…
United States Trends
- 1. Sonny Gray 6,677 posts
- 2. Dick Fitts N/A
- 3. Red Sox 6,756 posts
- 4. Godzilla 19.7K posts
- 5. #yummymeets N/A
- 6. National Treasure 5,019 posts
- 7. Clarke 6,230 posts
- 8. Rush Hour 4 4,747 posts
- 9. Raising Arizona N/A
- 10. Gone in 60 1,780 posts
- 11. Giolito N/A
- 12. #GMMTV2026 4.25M posts
- 13. Happy Thanksgiving 20.8K posts
- 14. NextNRG Inc N/A
- 15. Lord of War 1,279 posts
- 16. Thankful 50.4K posts
- 17. Academic All-District N/A
- 18. Breslow N/A
- 19. Chuck and Nancy 4,585 posts
- 20. Ghost Rider 2,147 posts
You might like
-
 DeepBlue Security & Intelligence
DeepBlue Security & Intelligence
@DeepBlueInfoSec -
 Haris Khan
Haris Khan
@harissaeedkhann -
 G0ld1e
G0ld1e
@G0ld1e1 -
 faryad rahmani
faryad rahmani
@faryadR -
 Lindsey
Lindsey
@linslulich -
 satty
satty
@satty305 -
 Nectux ~$ Hacking since 1337
Nectux ~$ Hacking since 1337
@Nectux -
 BALOGUN ADEOLU
BALOGUN ADEOLU
@balocyberpro -
 Brittany Kathleen
Brittany Kathleen
@Thebrittany4u -
 Euey 으아이
Euey 으아이
@YoonEuey -
 Marcel Gerardino
Marcel Gerardino
@_goetia_ -
 THOMAS
THOMAS
@0xSH4RKS
Something went wrong.
Something went wrong.