Sharo K h
@Sharo_k_h
Junior Hunter🙂 My Github: https://github.com/SharokhAtaie
You might like
I submitted my first critical vulnerability and awarded $3500 on @Hacker0x01 Bug: Default WordPress Installation lead to RCE Tip: cat subdomains.txt | httpx -title -fr Result: [WordPress > Installation] Watch on your Targets🙂 Thanks to @voorivex and @dollarisho_com
![Sharo_k_h's tweet image. I submitted my first critical vulnerability and awarded $3500 on @Hacker0x01
Bug: Default WordPress Installation lead to RCE
Tip:
cat subdomains.txt | httpx -title -fr
Result: [WordPress > Installation]
Watch on your Targets🙂
Thanks to @voorivex and @dollarisho_com](https://pbs.twimg.com/media/F0vsycfWwAATqY3.jpg)
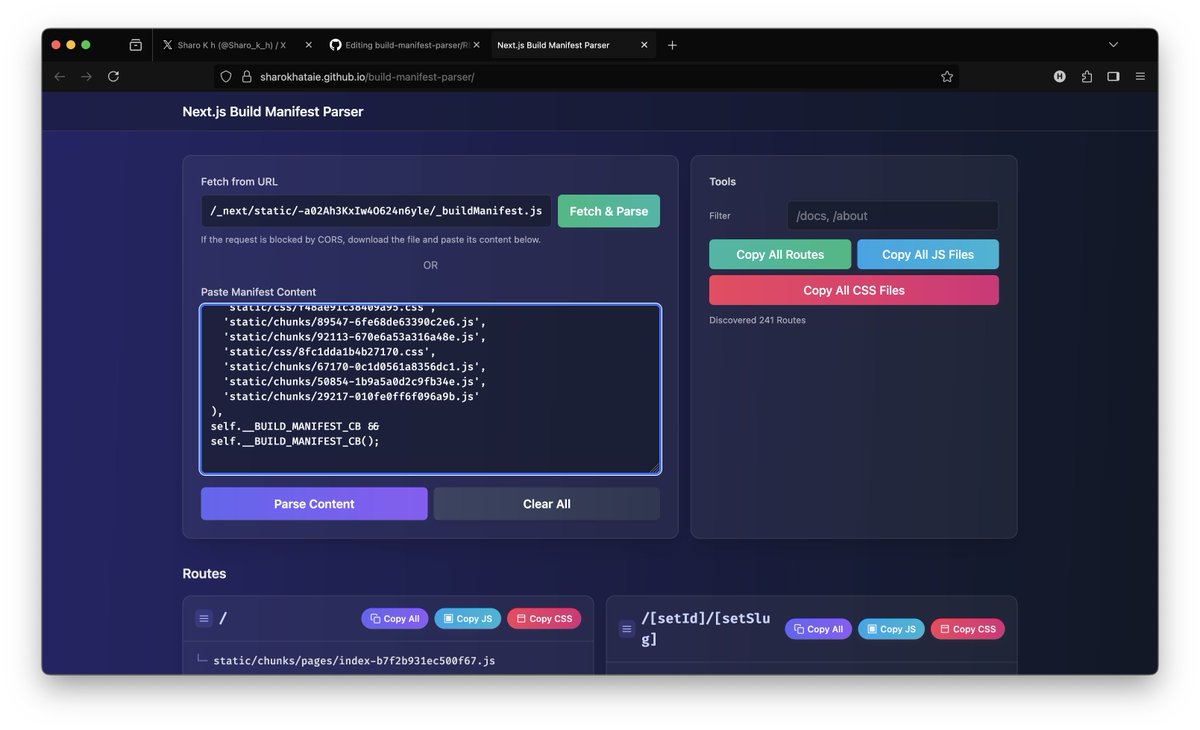
🚀 New Tool Alert! Easily parse _buildManifest.js files from Next.js web apps 🔍 🛠 Try it online: sharokhataie.github.io/build-manifest… 💻 Source code: github.com/SharokhAtaie/b… #BugBounty #JS #NextJS #WebSecurity
۳ تا cve ساده که قبلا زده بودم اگه دوست داشتید حتما بخونید t.me/gotocvechat/27… مرسی از علی جان بابت وقتی که برا ما میذاره🙏❤️ @soltanali0
🧵 Bug Bounty Methodology 🧵 After reading countless write-ups and checklists, I created my own methodology that has helped me find vulnerabilities effectively. #BugBounty #Infosec #Cybersecurity #ethicalhacking #bugbountytip #bugbountytips #methodology
I have created a chrome extension for extract endpoints and urls from js files. You can use it for modern web app which this tool watch for new js files that loaded (lazyload). github.com/SharokhAtaie/e… #BugBounty #tools #PenTest
JsFuck ❌ FuckJS ✅ We also bypassed a very strict Cloudflare WAF with @ehsan_nkd @0xb0hl00l . Hint: When you face a WAF that allows you to use `javascript:` scheme but blocks every payload that you know, DEFINE variables! #HiveCommunity #BugBounty #hackerone #XSS

Discovered an XSS vulnerability but Imperva WAF blocked it? Try this XSS payload to bypass Imperva's protection. <details x=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx:2 open ontoggle=alert(origin)> #bugbounty #bypass_imperva #xss #hacking


XSS Tip: If you have two parameter reflections in a JavaScript context and can't close the script tag or break the string with ( " ), you can use a backslash ( \ ) to escape the ( " ) of the first reflection and inject your JavaScript payload in the second reflection.



My new tool: A tool for extract money😆 github.com/SharokhAtaie/e…
github.com
GitHub - SharokhAtaie/extractify: A tool for extract Endpoints, URLs and Secrets from contents
A tool for extract Endpoints, URLs and Secrets from contents - SharokhAtaie/extractify
A very simple tool to compare 2 file and return unique diff. Alternative to comm command in linux. github.com/SharokhAtaie/c…
United States Trends
- 1. Bama 17.6K posts
- 2. Oklahoma 26.6K posts
- 3. #UFC322 31.2K posts
- 4. Ty Simpson 3,649 posts
- 5. Jeremiah Smith 1,439 posts
- 6. BOOMER SOONER 1,810 posts
- 7. Iowa 19.2K posts
- 8. Mateer 3,072 posts
- 9. Sabatini 1,296 posts
- 10. Brent Venables 1,113 posts
- 11. #RollTide 3,205 posts
- 12. Benn 39K posts
- 13. Jungkook 250K posts
- 14. South Carolina 33.7K posts
- 15. Heisman 10.7K posts
- 16. Kline 1,561 posts
- 17. DeBoer 1,379 posts
- 18. Arbuckle 1,048 posts
- 19. Talty 1,625 posts
- 20. Ryan Williams 1,717 posts
You might like
-
 Meydi
Meydi
@mehdiparandin -
 sepix
sepix
@0xSepix -
 Zero
Zero
@ZeroXUF -
 ferferof
ferferof
@ferferof_ -
 Mohammad
Mohammad
@MehrazarDev -
 Ali Firoozi
Ali Firoozi
@afssec000 -
 Sadra
Sadra
@MrMSA16 -
 Milad Safdari (Ξulex)
Milad Safdari (Ξulex)
@eulex0x -
 Ali Soltani
Ali Soltani
@soltanali0 -
 ꜱʜᴀʏᴀɴ ᯤ
ꜱʜᴀʏᴀɴ ᯤ
@The0xGeek -
 You can call me charlie
You can call me charlie
@khode4liam -
 Call me matitanium
Call me matitanium
@MatinNouryan -
 Mahan Xp
Mahan Xp
@_0xaurora -
 AmirMohammad Safari
AmirMohammad Safari
@AmirMSafari -
 ELmin
ELmin
@real_Elmin
Something went wrong.
Something went wrong.