Tal vez te guste
.@Volexity has released updates to its #opensource GoResolver project and more! This work was part of a project for one of our #summerinternship students. We are proud to contribute to the open source community + work alongside students in our annual #internship program!
.@Volexity #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets. volexity.com/blog/2025/04/2… #dfir
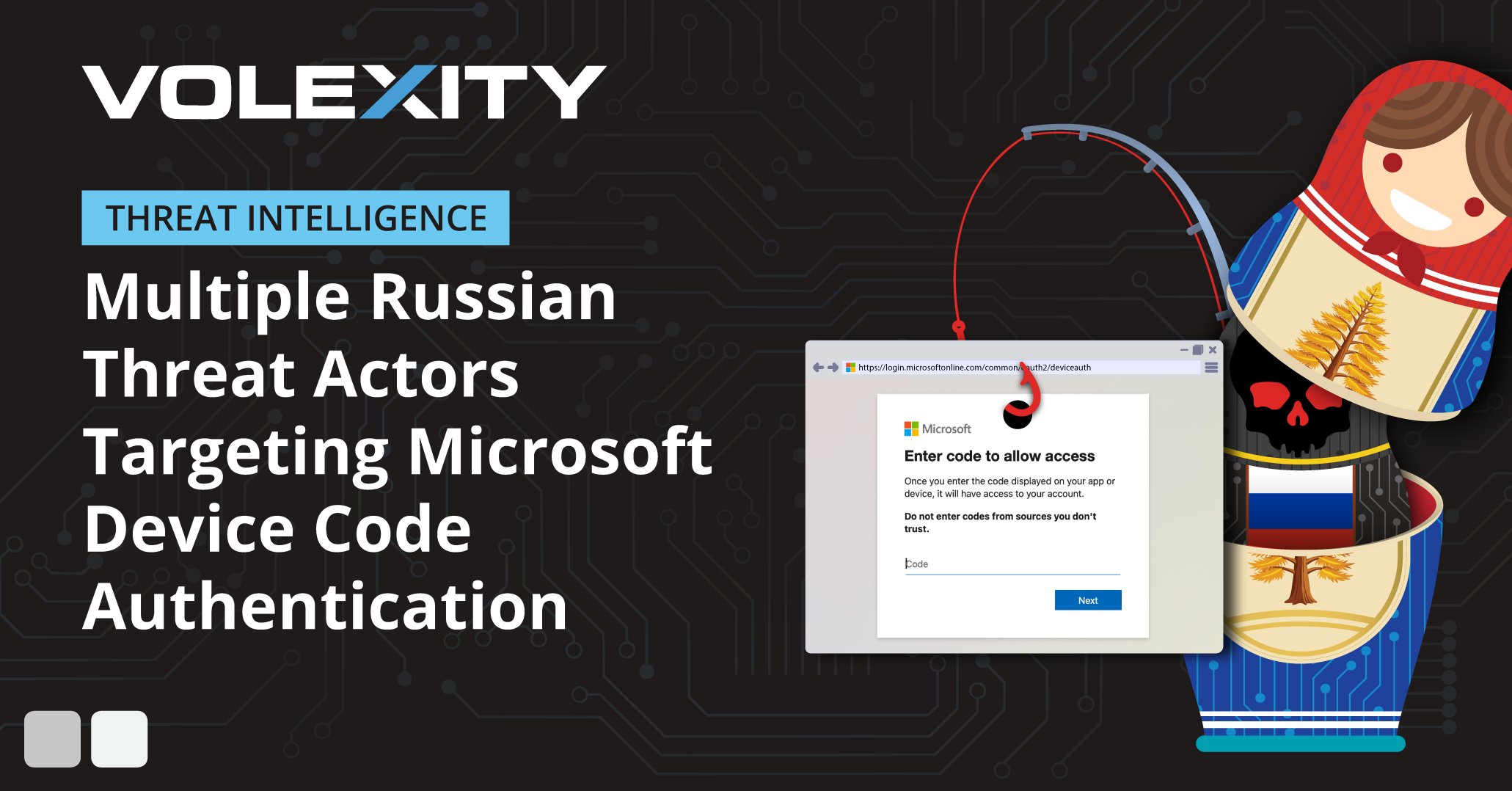
.@Volexity recently identified multiple Russian threat actors targeting users via #socialengineering + #spearphishing campaigns with Microsoft 365 Device Code authentication (a well-known technique) with alarming success: volexity.com/blog/2025/02/1… #dfir #threatintel #m365security
.@Volexity’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target, while the attacker was halfway around the world. volexity.com/blog/2024/11/2… #dfir
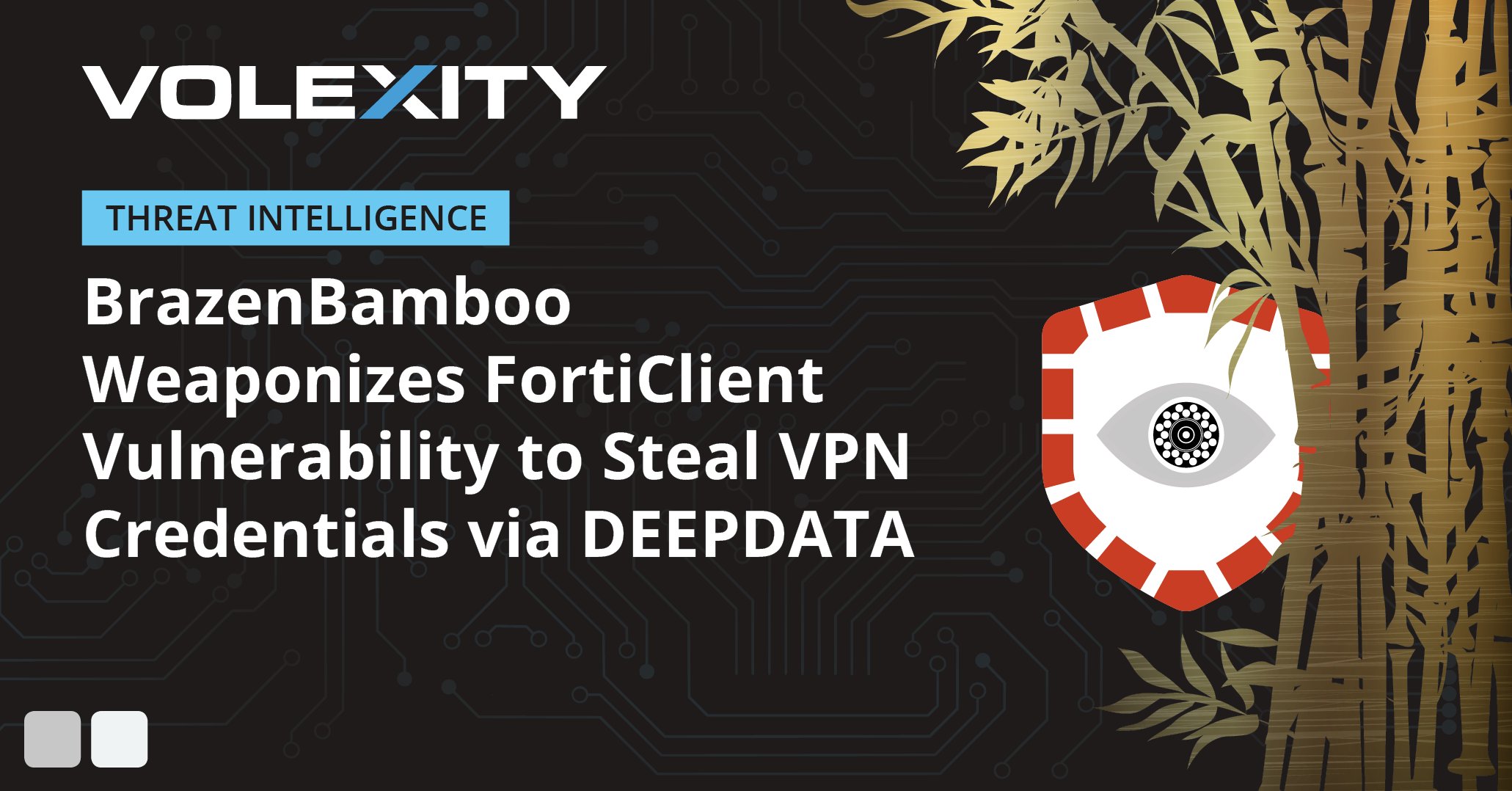
.@Volexity has published a blog post detailing variants of LIGHTSPY & DEEPDATA malware discovered in the summer of 2024, including exploitation of a vulnerability in FortiClient to extract credentials from memory. Read more here: volexity.com/blog/2024/11/1… #dfir #threatintel
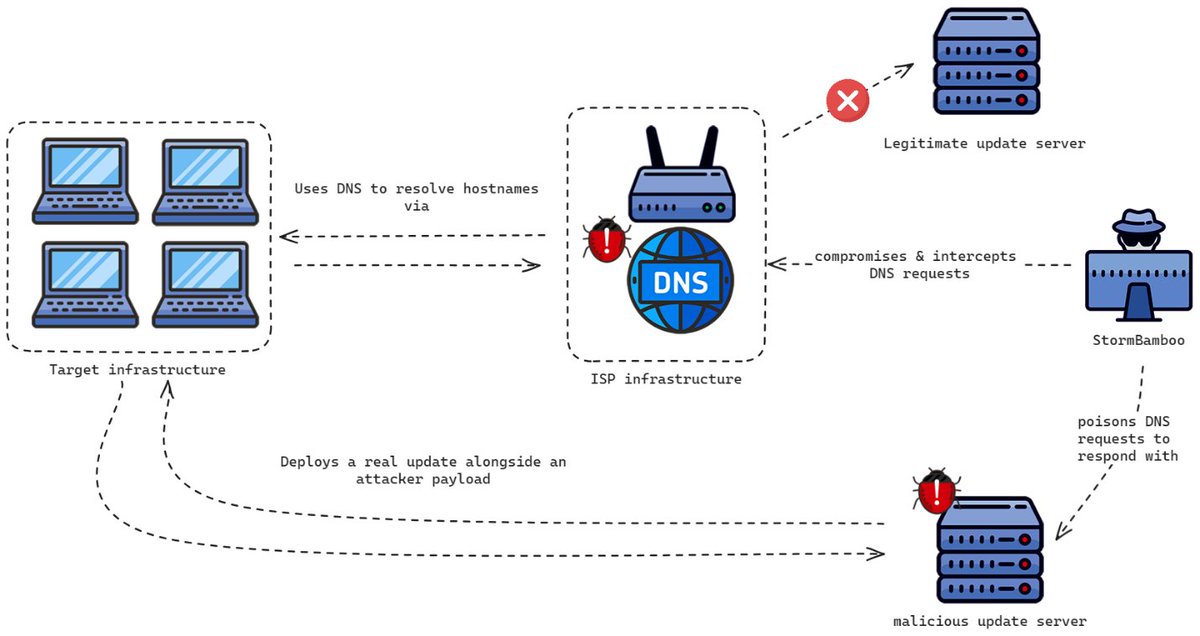
We released a blogpost concerning #StromBamboo (aka Evasive Panda). @volexity was involved in an incident where the attackers compromised an ISP to poison the customers' DNS requests to hijack software updates (using the HTTP protocol): volexity.com/blog/2024/08/0… 1/3
Volexity's Ankur Saini (@kernelm0de), Paul Rascagneres (@r00tbsd), Steven Adair (@stevenadair) & Thomas Lancaster (@tlansec) show how StormBamboo used DNS poisoning at the internet service provider level to deliver MACMA and POCOSTICK (aka MGBot). volexity.com/blog/2024/08/0…
Spicy Friday blog drop on an ISP compromise leading to DNS poisoning for downstream organisations and compromise via insecure application update methods. Great work as always @tlansec @r00tbsd @kernelm0de @stevenadair
.@Volexity shares #threatintel on how #StormBamboo compromised an ISP to conduct DNS poisoning attacks on targeted organizations & abuse insecure HTTP software updates, delivering custom malware on both macOS + Windows. Read the full analysis: volexity.com/blog/2024/08/0… #dfir
.@Volexity shares #threatintel on how #StormBamboo compromised an ISP to conduct DNS poisoning attacks on targeted organizations & abuse insecure HTTP software updates, delivering custom malware on both macOS + Windows. Read the full analysis: volexity.com/blog/2024/08/0… #dfir
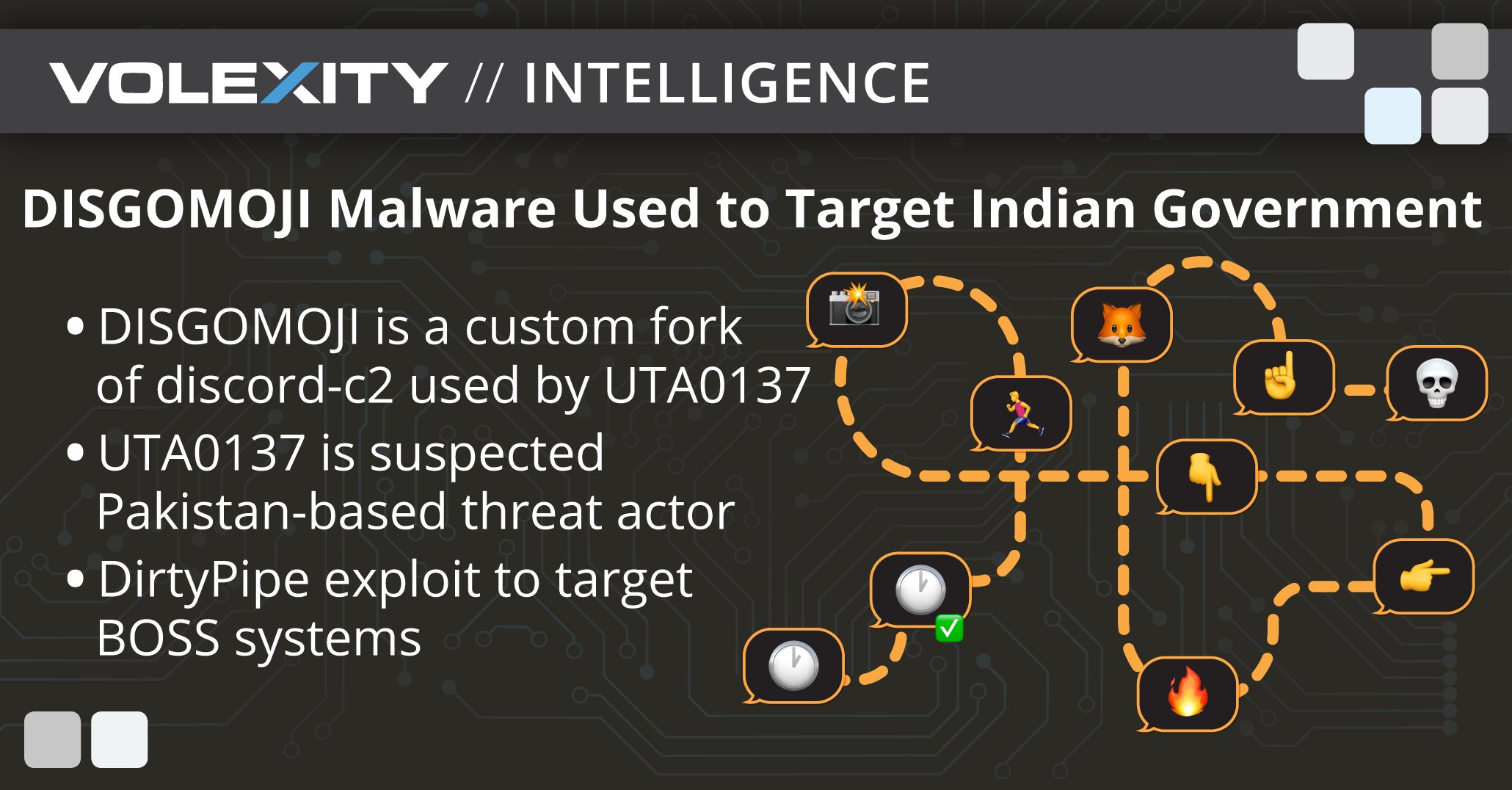
.@Volexity analyzes #DISGOMOJI 🔥, Discord-based malware 💀 using emojis for C2. #DISGOMOJI is used by #UTA0137, a suspected Pakistan-based threat actor. Read the full analysis here: volexity.com/blog/2024/06/1… #dfir #threatintel
Our latest blog post details @Volexity's identification & incident response associated with the Palo Alto Networks GlobalProtect #0day vuln, assigned CVE-2024-3400, that the team found being exploited in the wild. Read more here: volexity.com/blog/2024/04/1… #DFIR #ThreatIntel
Our team at @Volexity has identified a new 0day exploited in the wild. This time we caught a threat actor using an unauthenticated RCE in Palo Alto Networks GlobalProtect. It has been assigned CVE-2024-3400 and is covered in this @PaloAltoNtwks advisory security.paloaltonetworks.com/CVE-2024-3400
security.paloaltonetworks.com/CVE-2024-3400 Casual CVSS 10 exploited in the wild...
.@Volexity consistently observes Iranian #apt group CharmingCypress innovate ways to persistently pursue targets. This blog reviews the group's phishing tactics & malware + investigates an attack with Volexity Volcano: volexity.com/blog/2024/02/1… #dfir #threatintel #memoryforensics
Roses are red, violets are blue... install my VPN, so I can pwn you. volexity.com/blog/2024/02/1…
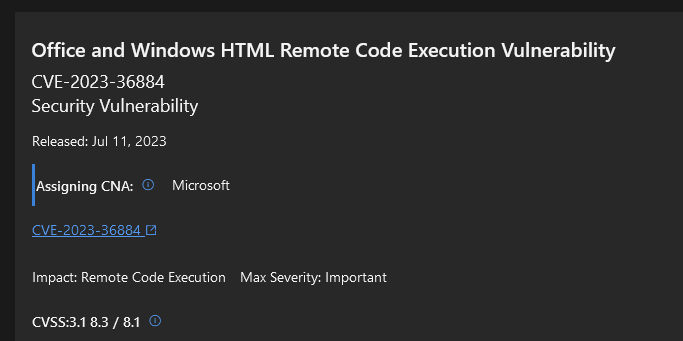
If you missed it yesterday, Microsoft released an advisory concerning the CVE-2023-36884: msrc.microsoft.com/update-guide/v…. This RCE is currently used by a TA and there is no patch. You should apply the mitigation described in the advisory. 1/4
Here at @Volexity we work with one of the organizations that was impacted by the use of forged authentication tokens to access a victim's @Microsoft365 email by a Chinese APT group as described (STORM-0558) by @Microsoft. blogs.microsoft.com/on-the-issues/… #STORM0558 1/7
blogs.microsoft.com
Mitigation for China-based threat actor activity - Microsoft On the Issues
Microsoft and others in the industry have called for transparency when it comes to cyber incidents so that we can learn and get better. As we’ve stated previously, we cannot ignore the exponential...
From the @Volexity #threatintel team: this blog post details #CharmingKitten's POWERSTAR malware, now with an InterPlanetary twist... Read more: volexity.com/blog/2023/06/2… #dfir
The @Volexity #threatintel team takes a look at the #3CX supply chain compromise: the malware delivered, the infrastructure used & the initial set up of the attack. Here's what we know so far: volexity.com/blog/2023/03/3… #dfir
United States Tendencias
- 1. #lip_bomb_RESCENE N/A
- 2. Ravens 58.5K posts
- 3. #River 3,530 posts
- 4. Lamar 46.6K posts
- 5. #heatedrivalry 15.4K posts
- 6. ilya 17.2K posts
- 7. Shane 20.6K posts
- 8. Joe Burrow 21.1K posts
- 9. Hudson 12.1K posts
- 10. Connor 15.4K posts
- 11. #WhoDey 4,179 posts
- 12. BNB Chain 8,208 posts
- 13. Zay Flowers 4,200 posts
- 14. #hrspoilers 3,247 posts
- 15. scott hunter N/A
- 16. Sarah Beckstrom 223K posts
- 17. Derrick Henry 4,481 posts
- 18. Third World Countries 27.7K posts
- 19. AFC North 2,374 posts
- 20. Harbaugh 3,186 posts
Something went wrong.
Something went wrong.