Sergey Voynov
@make_oneself
CEO & Founder of @G71Inc. (@LeaksID), IT /Security expert, inventor, enthusiast, husband, dad, yachtsman, biker, a sound-color synesthete in love with cooking.
You might like
External breaches at 65%, but internal threats have surged to 35% (from 20%). Key risk areas: web apps and email. At G-71 Security, we’re advancing our tech to tackle these challenges. Stay tuned for updates on our new integration! Request a demo at g-71.com

2024 Code42 Report reveals a 28% surge in insider-driven #databreaches since 2021. Traditional DLP systems can't keep up. Time for a holistic security approach. One option in this direction is to install the G-71 Security invisible marking. Learn more: g-71.com

On March 6 and 7, the G-71 Security team, Sergey Voynov @make_oneself and Julia Doronina @juliet__de, took part in the Cloud & Cyber Security Expo at Tech Show London 2024. We're excited to share our impressions, outcomes, and photos from the event: g-71.com/2024/03/14/g-7…
In this #RSAC blog, (@make_oneself), CEO & Founder of @G71Inc, explores new data-supported trends and approaches to defend against #insiderthreats. spr.ly/6013u16HF
Dive into the Top 5 Trending Approaches to Protect Against Insider Threats in 2024: rsaconference.com/library/blog/h…
In an era of digital vulnerability, safeguarding your documents is crucial. Explore these valuable insights on how to secure your Word documents effectively! Read more: leaksid.com/how-to-protect… #leaksid #dataprotection #insiderthreat #insiderrisk #cybersecuritytips
82% of companies implement #BYOD policies, allowing employees to bring their own devices. However, №1 security concern surrounding BYOD is #databreaches. We have examined this issue and presented 8 solutions that can help reduce the risk of #dataleaks. leaksid.com/what-is-byod-i…
I am sure that we will soon stop hearing scandalous news that someone unknown has published someone's email. helpnetsecurity.com/2023/07/21/g-7…
Discover the power of steganography as a game-changing solution for preventing document leaks and securing confidential email attachments. Read more about it at @Hackernoon: hackernoon.com/exploring-subs… #Steganography #DataSecurity #LeaksID
Protecting confidential data requires more than just basic security measures. In our latest article, we with our CEO, @make_oneself, explore a three-part approach to ensure document confidentiality. Read the article leaksid.com/protecting-con… #cybersecurity #dataprotection
leaksid.com
Protecting Confidential Documents: The Power of Hidden Anti-Leak Marks | LeaksID
This article examines three vital aspects of document confidentiality: Access Control, Monitoring, and Detection, with a focus on steganography.
Did you know? 55% of organizations see privileged users as the top insider threat. LeaksID solves this by labeling confidential documents for owner identification if they are leaked. Explore more at leaksid.com. #LeaksID #DataProtection #InsiderThreat #CyberSecurity

LeaksID is constantly evolving with new features and integrations. Now you can now add an invisible forensic watermark to email attachments on-the-fly by integrating with MS Exchange, as well as connect external storage to LeaksID, such as Google Drive.
We are happy to announce that LeaksID has expanded its integration capabilities to include email servers and external storage such as One Drive or Google Drive. More details: leaksid.com/g-71-inc-stren… #leaksid #dataprotection #insiderthreat #cybersecurity

On April 17th, we had the opportunity to attend the Content Protection Summit in Las Vegas, hosted by @CDSAonline and @MESAlliance. It was a great chance for us to connect with professionals from different fields, including content creators, distributors, and security experts.

Happy birthday, dear G-71! On this day, I wish you great success and prosperity! Your potential for growth is boundless, and we, your team, are thrilled to help you every step of the way. Happy Birthday! 🎂 🎉
Let's break out the confetti and balloons because it's party time! G-71 is thrilled to be celebrating its birthday today! It's been an incredible year full of growth, and we're so grateful to have gained more supporters, followers, users, and insights.
Just a few days ago, we received an update on our patent. We couldn’t be prouder that our unique approach has no direct competitors in the market, and it was confirmed by our legal team’s market analysis, which makes us even more excited to keep pushing our technology further.

PowerPoint presentations can contain sensitive information that should be protected. Leaks can happen through unauthorized sharing, or even screenshots. Use LeaksID to keep your PPTX presentations secure - leaksid.com #insiderthreat #dataprotection #dataleakage

We have decided to launch a new content section - integration opportunities. We will be sharing information about other information security solutions that LeaksID can work together with, in order to create a comprehensive approach to protecting confidential documents. #leaksid
LeaksID is a versatile solution that can be integrated with a variety of other tools, offering a comprehensive approach to #documentprotection. One of these solutions is #dataclassification, that involves organizing data into different categories based on its level of sensitivity

Insider threats are a real risk for any organization. Don’t let your business fall victim - read “Insider Threat Indicators” on leaksid.com to learn how to identify warning signs and prevent attacks. Stay informed. #insiderthreats #cybersecurity
Don't let insider threats damage your organization. Learn how to identify warning signs and prevent insider attacks by reading "Insider Threat Indicators". Gain insights, and take steps to minimize the risks. #insiderthreats #cybersecurity #dataprotection leaksid.com/insider-threat…
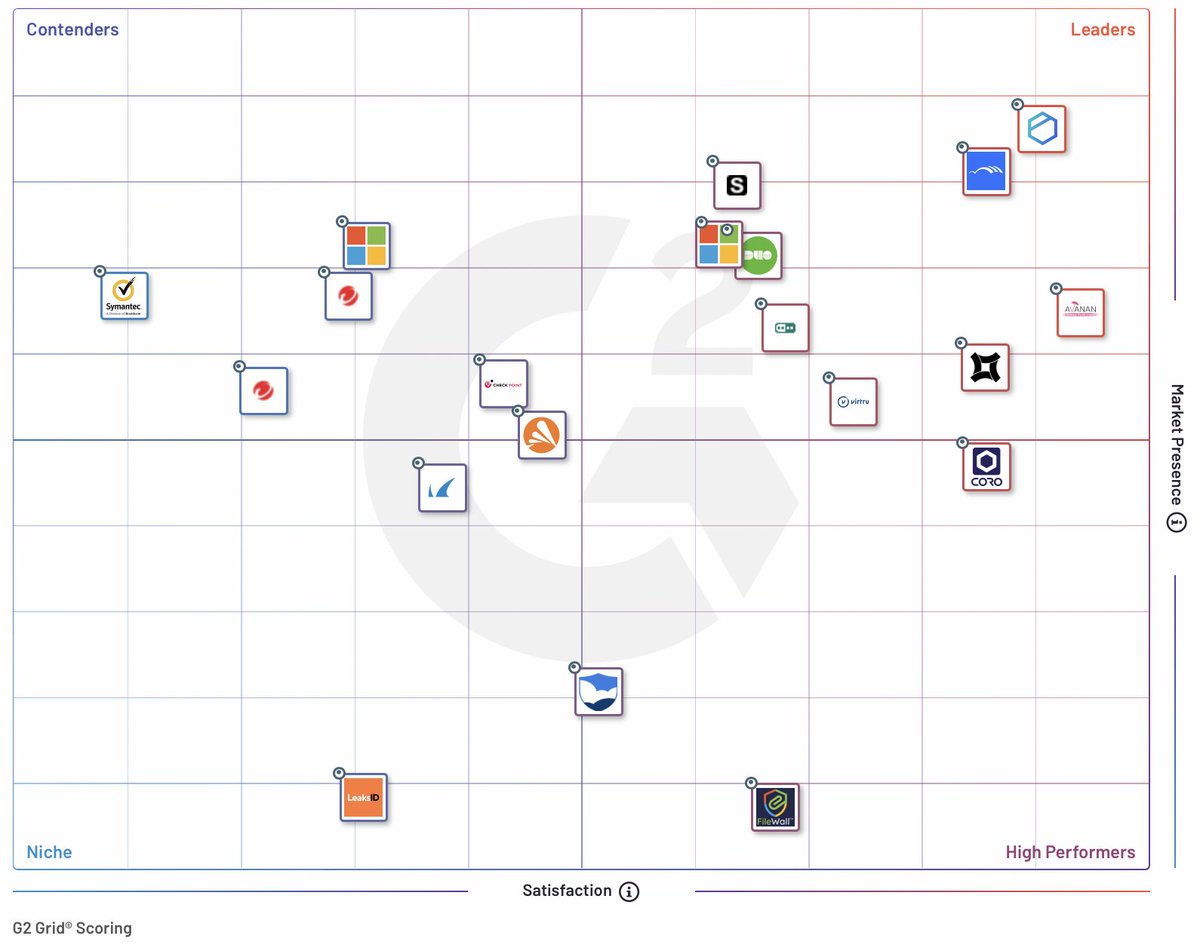
I'm excited to announce that LeaksID has been recognized as one of the “Best Cloud File Security Software” options on G2, where we ranked among the top players in the industry. This is a significant achievement for us. #leaksid #filesecurity #cybersecurity #dataprotection
Exciting news! LeaksID was selected as a top player for "Best Cloud File Security Software" on @G2dotcom and recognized as a niche product on G2 Grid® for Cloud File Security. Try our 2-week trial to securely store confidential docs: leaksid.com/pricing #cybersecurity
Totally agree. Eliminating the possibility of anonymous leaks is the key to combating insider risks. identityweek.net/how-to-stop-do…
United States Trends
- 1. Epstein N/A
- 2. Jay Z N/A
- 3. Pusha N/A
- 4. Iron Lung N/A
- 5. #OPLive N/A
- 6. Marina N/A
- 7. Izzo N/A
- 8. Podz N/A
- 9. Pistons N/A
- 10. Bill Gates N/A
- 11. Mariah N/A
- 12. #questpit N/A
- 13. #VERZUZ N/A
- 14. Michael Watts N/A
- 15. #DragRace N/A
- 16. $Accelerando N/A
- 17. Hanoi Jane N/A
- 18. Hield N/A
- 19. SANTA FROST WARM SIGN N/A
- 20. Jokic N/A
You might like
Something went wrong.
Something went wrong.