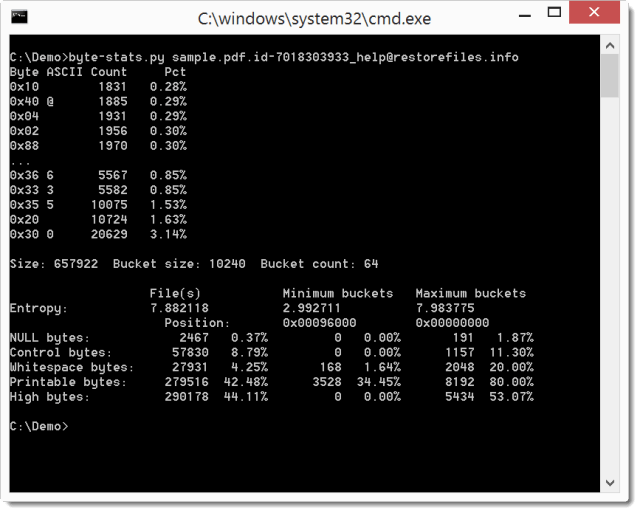
peepdf
@peepdf
peepdf is a Python tool to perform PDF analysis in order to find out if the explored files can be harmful or not.
You might like
Fresh PDF (81fa2eb97128b6d711158f37698e044f) being used to drop docm file which downloads #Dridex Easy extraction with #peepdf ;) #malware

It seems there are still PDF vulns to be exploited... @ESET discovered a #PDF uploaded to @virustotal containing two 0days, one for Adobe Reader (CVE-2018-4990) and a sandbox bypass (CVE-2018-8120) welivesecurity.com/2018/05/15/tal… #vulnerabilities #infosec #apt #cybercrime
Happy to see the @sekoia_fr guys using @peepdf in their new dropper analysis service (malware.sekoia.fr) presented at #Botconf 😊

New tool added: peepdf (PDF analysis) by @peepdf #pdf #tools linuxsecurity.expert/tools/peepdf/
More details about the #Dridex campaign (botnet 7200) using PDF documents as infection vector eternal-todo.com/blog/dridex-sp… #malware #spam #peepdf
Another #malware campaign spreading PDFs (85066792c8952100ac057055a2f49a8c) to ask the user to execute docm files. The docm was detected ;)
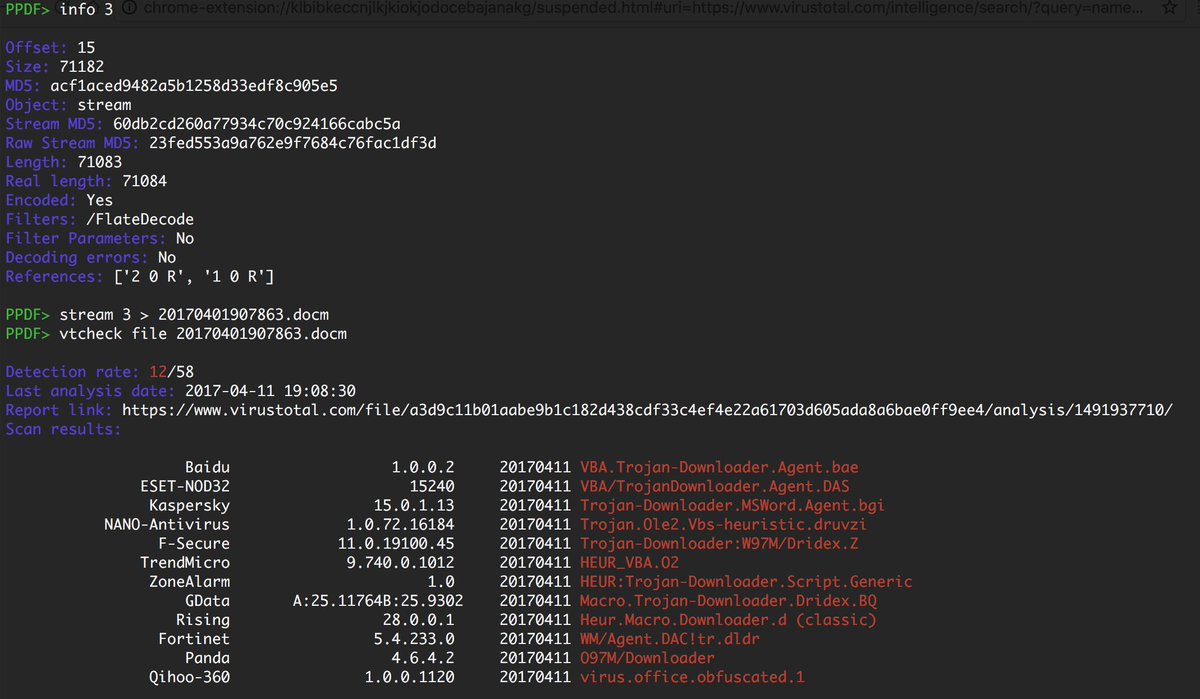
Big thanks to Jose Miguel Esparza @peepdf @EternalTodo for interview, questions on his Kali Linux tools (Peepdf) buff.ly/2m6iame

Detailed analysis of a heap buffer overflow in Adobe Acrobat and Reader (CVE-2016-4203) by @Fortinet blog.fortinet.com/2016/07/20/ana… #infosec #PDF
Interesting post by @DidierStevens about reconstructing a PDF file parcially encrypted by ransomware blog.didierstevens.com/2016/06/07/rec… #DFIR #infosec
Comprehensive vulnerability analysis of a Use-After-Free in Adobe Acrobat and Reader (CVE-2016-4119) by @Fortinet blog.fortinet.com/2016/06/06/ana…
@michael_yip @ProjectHoneynet @bartblaze @decalage2 Give it a try! ;) It is listed here, btw :) decalage.info/en/file_format…
Jose Esparza showing how to analyze a malicious PDF, extract shellcodes and automate analysis with Peepdf #HNW2016

Just added a new parameter (-C) to execute commands via command line, update! ;) #security #infosec #DFIR #tools


Just one week for the PDF Analysis workshop with @peepdf at #HNW2016 in San Antonio sanantonio2016.honeynet.org/schedule/train… sanantonio2016.honeynet.org/registration/ #infosec
It is not in the master branch yet, but take a look at the @peepdf scoring system! ;) eternal-todo.com/blog/adding-sc… #gsoc
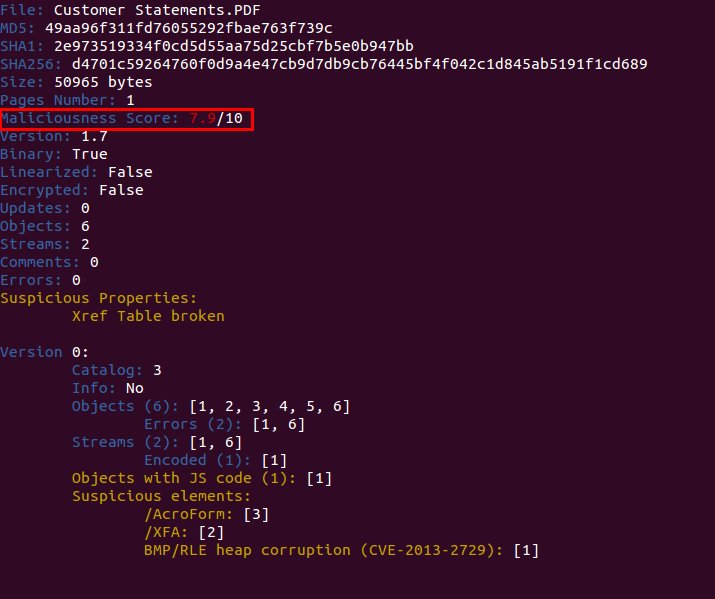
Still in beta but if you update #peepdf you can use "extract" to extract all URIs and Javascript code in a PDF file


@peepdf : A Python tool to explore PDFs to find out if they can be harmful or not. + github.com/jesparza/peepdf + eternal-todo.com/tools/peepdf-p…
The Honeynet Project is applying for Google Summer of Code 2016, more information on honeynet.org/gsoc #GSoC2016
Adding a scoring system to #peepdf honeynet.org/node/1304 #gsoc @EternalTodo

United States Trends
- 1. Klay 20.9K posts
- 2. McLaren 65.4K posts
- 3. #AEWFullGear 70.7K posts
- 4. Lando 113K posts
- 5. #LasVegasGP 202K posts
- 6. Ja Morant 9,305 posts
- 7. Oscar 104K posts
- 8. Hangman 10.1K posts
- 9. Samoa Joe 4,935 posts
- 10. Max Verstappen 56.5K posts
- 11. Gambino 2,590 posts
- 12. LAFC 15.7K posts
- 13. Piastri 42.9K posts
- 14. Swerve 6,438 posts
- 15. #Toonami 2,841 posts
- 16. Bryson Barnes N/A
- 17. Kimi 42K posts
- 18. Utah 23.9K posts
- 19. Fresno State 1,013 posts
- 20. LJ Martin 1,304 posts
You might like
-
 Bart
Bart
@bartblaze -
Xavier Mertens @[email protected] 🇧🇪
@xme -
 Danny Quist
Danny Quist
@OpenMalware -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Philippe Lagadec
Philippe Lagadec
@decalage2 -
 Kse Proso
Kse Proso
@KseProso -
 Jose Miguel Esparza
Jose Miguel Esparza
@EternalToDo -
 Antelox
Antelox
@Antelox -
 Daniel Plohmann
Daniel Plohmann
@push_pnx -
 Giuseppe `N3mes1s`
Giuseppe `N3mes1s`
@N3mes1s -
 Malware Utkonos
Malware Utkonos
@MalwareUtkonos -
 Glenn
Glenn
@hiddenillusion -
 Gadix
Gadix
@GadixCRK -
 R136a1
R136a1
@TheEnergyStory -
 Shusei Tomonaga
Shusei Tomonaga
@shu_tom
Something went wrong.
Something went wrong.