peterChain
@peterChain7
Cybersecurity, Digital forensics, CTF player, System development, Friend, Apache web server Configuration, CTFs Creator
你可能會喜歡
I just pwned Artificial on Hack The Box! hackthebox.com/achievement/ma… #HackTheBox #htb #CyberSecurity #EthicalHacking #InfoSec #PenTesting
🧠💣 381 FILES. 200+ GB. ELITE ONLY. I just unlocked a vault that would make even top bug bounty hunters drop everything: 🔥 OSCP 🔥 OSEP 🔥 OSWE 🔥 THM / HTB 🔥 EC-Council 🔥 Cisco CyberOps 🔥 Linux Priv Esc 🔥 PEN-300 Full Video Series 🔥 BloodHound, AD, SSH, API, SQL, 🔥…




We have just released our official writeup for the UrchinSec DTS Finals CTF challenge: 🔥 hackmd.io/@urchinsec/urc…
🔥 ADVANCED BUG BOUNTY RECON PLAYBOOK (2025) — FULL THREAD Most hackers only touch the surface. The real $$$ is in DEEP RECON. Here’s my ULTIMATE RECON PIPELINE for catching bugs everyone else misses (bookmark this): ⸻ 1️⃣ SCOPE REVIEW 🌍 Know your boundaries → authorized…

Finally our website is live! You’ll find all the bug hunting commands, tools, extensions & writeups here—many more things coming soon for all types of bugs. Huge thanks to @madhusudan91263 for contributing and making this toolkit even more amazing!
I just pwned TheFrizz on Hack The Box! hackthebox.com/achievement/ma… #HackTheBox #htb #CyberSecurity #EthicalHacking #InfoSec #PenTesting
As technology continues to evolve in business, a 25-year-old Kalebu Gwalugao has developed a system that enables businesses to operate via WhatsApp and issue electronic fiscal receipts (EFDs) to customers. READ: thecitizen.co.tz/tanzania/news/…

We are beyond proud to announce that two out of four of the top winners for the TCRA Cyberchampions, Amani Nsemwa ( 1st Winner) and Rebeca Kubanda (4th Winner) are products of the UDOM Cybersecurity Club.




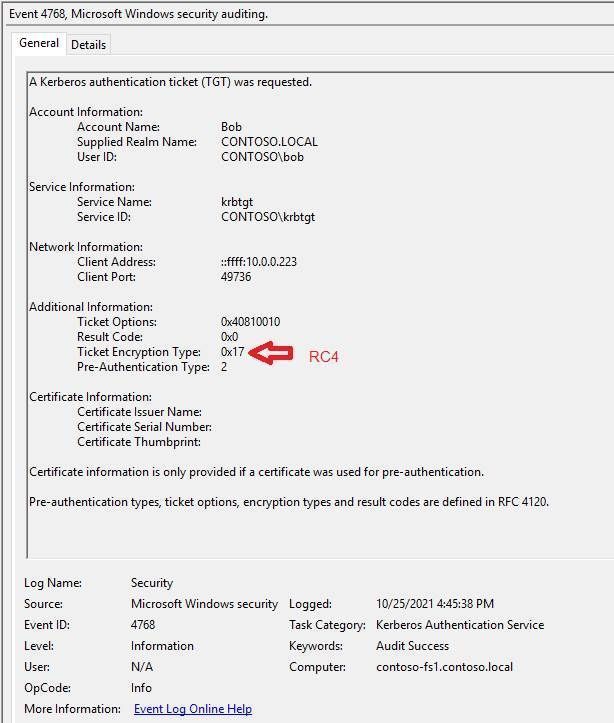
Active Directory Hardening Series - Part 1 – Disabling NTLMv1 : techcommunity.microsoft.com/blog/coreinfra… Part 2 – Removing SMBv1 : techcommunity.microsoft.com/blog/coreinfra… Part 3 – Enforcing LDAP Signing : techcommunity.microsoft.com/blog/coreinfra… Part 4 – Enforcing AES for Kerberos : techcommunity.microsoft.com/blog/coreinfra… Part 5 –…
Our Research and Innovation team led by Lawrence @muchilwa will be hosting a technical session on AI tomorrow starting at 12PM to 1:30PM for free. This is in collaboration with @CTF_Room who are pioneering training in the region through cyber range platform Register on time

But at least we showed up right? 🤷🏽♂️🤷🏽♂️🤷🏽♂️😂😂😂🚮🚮🚮, the meme’s i create at times even shock me 😂😂😂😂 @mukhtarsalim80 @mug3njutsu @joram_malley @trustie_rity
This study aims to identify the barriers that hinder the effective implementation of electronic health records (EHR) systems in developing countries while also uncovering the critical success factors (CSFs) that can facilitate their implementation. emerald.com/insight/conten…

Breaking down barriers to EHR implementation is key to transforming primary healthcare. Grateful for the chance to explore these challenges and contribute insights for meaningful change in Tanzania's health systems. #HealthInformatics journals.sagepub.com/doi/10.1177/14… @udom_public_hdp

Awesome @theXSSrat, your content are always 🔥🔥🔥
A special thanks to the organizers and the authors who made this all possible by authoring the enjoyable fruitful knowledgeful challenges for the UrchinSec Aware CTF 2024. Thanks to ; @tahaafarooq @nicl4ssic @AlienKeric @AlexiusSamson @V0ld3mrt @konfushon @trustie_rity 🔥

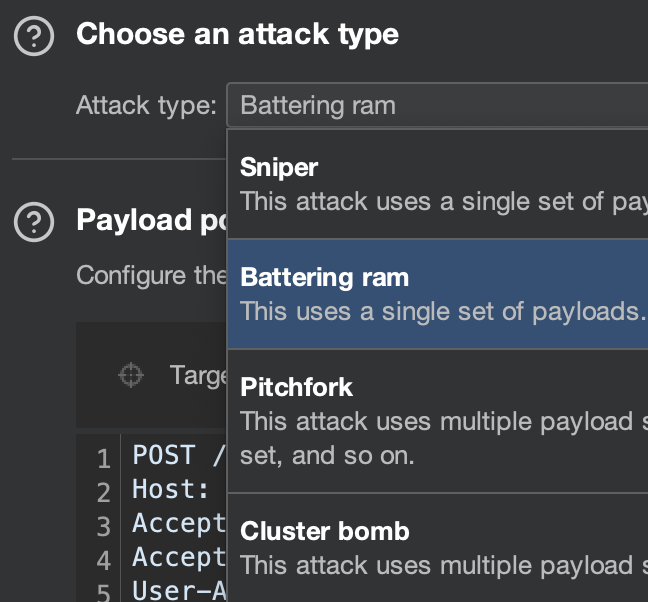
It's been over 10 years and I still cannot remember what each attack type means
Sehemu ambazo zinahitaji uvumbuzi na ushindani zaidi katika teknolojia kwa vijana wa Kitanzania ni: Fintech Innovations Edtech Initiatives Agri-tech Solutions Healthtech Solutions Smart City Solutions Environmental Tech Tourism and Cultural Tech Tech for Social Good
🧵 Complete Cybersecurity Professional Roadmap 🧵 1. Introduction to Ethical Hacking - Definition - Purpose - Types of Hackers - Legal and Ethical Considerations 2. Networking Basics - TCP/IP - OSI Model - Subnetting - DNS - DHCP 3. Operating Systems…
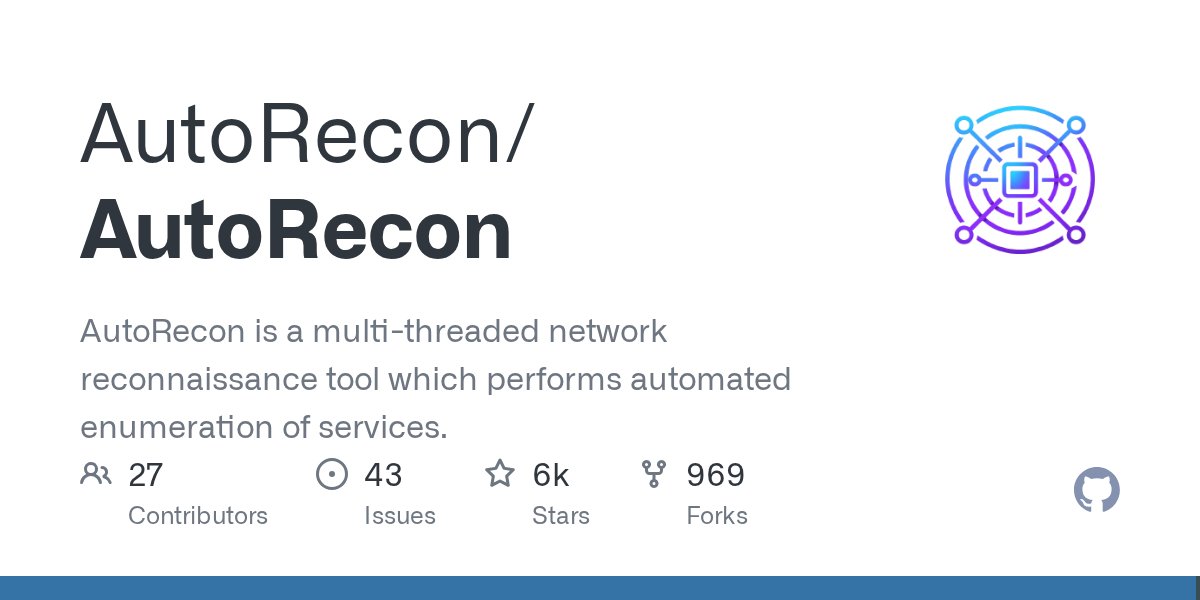
AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services by @0xTib3rius github.com/Tib3rius/AutoR…
List of bug hunting tools: 1. Burp Suite 🐛 2. OWASP ZAP (Zed Attack Proxy) 🛡️ 3. Nmap 🌐 4. Metasploit 🛠️ 5. Wireshark 🖥️ 6. Nikto 🕵️♂️ 7. SQLMap 🗺️ 8. Acunetix 🕷️ 9. Nessus 🚀 10. OpenVAS 🚪 11. BeEF (Browser Exploitation Framework) 🐄 12. Shodan 🔍 13. Wfuzz 🌀 14. DirBuster…
United States 趨勢
- 1. Bo Nix 5,351 posts
- 2. #BaddiesUSA 10.8K posts
- 3. Mariota 3,380 posts
- 4. #RHOP 7,408 posts
- 5. Tomlin 22.5K posts
- 6. Steelers 60.2K posts
- 7. #Married2Med 2,058 posts
- 8. Broncos 18.6K posts
- 9. Chicharito 4,619 posts
- 10. #RaiseHail 2,500 posts
- 11. Maxey 3,600 posts
- 12. Vikings 35.6K posts
- 13. Jalen Johnson 3,190 posts
- 14. #ITWelcomeToDerry 7,010 posts
- 15. Josh Allen 15K posts
- 16. Courtland Sutton 1,460 posts
- 17. Toya 5,704 posts
- 18. Chrisean 4,993 posts
- 19. Bills 90.3K posts
- 20. Rodgers 15.2K posts
你可能會喜歡
-
 Chalie
Chalie
@pwnipc -
 alienkeric
alienkeric
@alienker1c -
 pr0rat
pr0rat
@pr0rat -
 Kores
Kores
@joelkores_ -
 deathstalker
deathstalker
@c1ph3rbnuk -
 Fr334aks-mini
Fr334aks-mini
@fr334aksmini -
 Fraize
Fraize
@fraize__ -
 Ch4rl3s K00m3
Ch4rl3s K00m3
@CharlesKoome6 -
 Kimani Calvin
Kimani Calvin
@_kimanicalvin -
 Epitome
Epitome
@0xEpitome -
 P3rf3ct1onis7
P3rf3ct1onis7
@p3rf3ct1onis7 -
 Keith
Keith
@_0xKeith -
 _k4p3re
_k4p3re
@k4p3re_sam -
 D_C4ptain
D_C4ptain
@D_C4ptain -
 Ian Peter
Ian Peter
@IanPeterL
Something went wrong.
Something went wrong.