#ethicalhacking نتائج البحث
Day 1 of my #30DayMobileHackingChallenge! 🛠️📱 Set up Android Studio, adb & apktool to dive into mobile app hacking. #EthicalHacking #Cybersecurity

.@DubaiPoliceHQ has announced a major #cybersecurity initiative for October, featuring a “Capture the Flag” (CTF) competition with a total prize pool of Dh223,000. The competition, aimed at discovering and attracting talent in #EthicalHacking, is a cornerstone of a broader…

Enough SQLI's for today ( part 2 ) Thanks @intigriti <3 #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

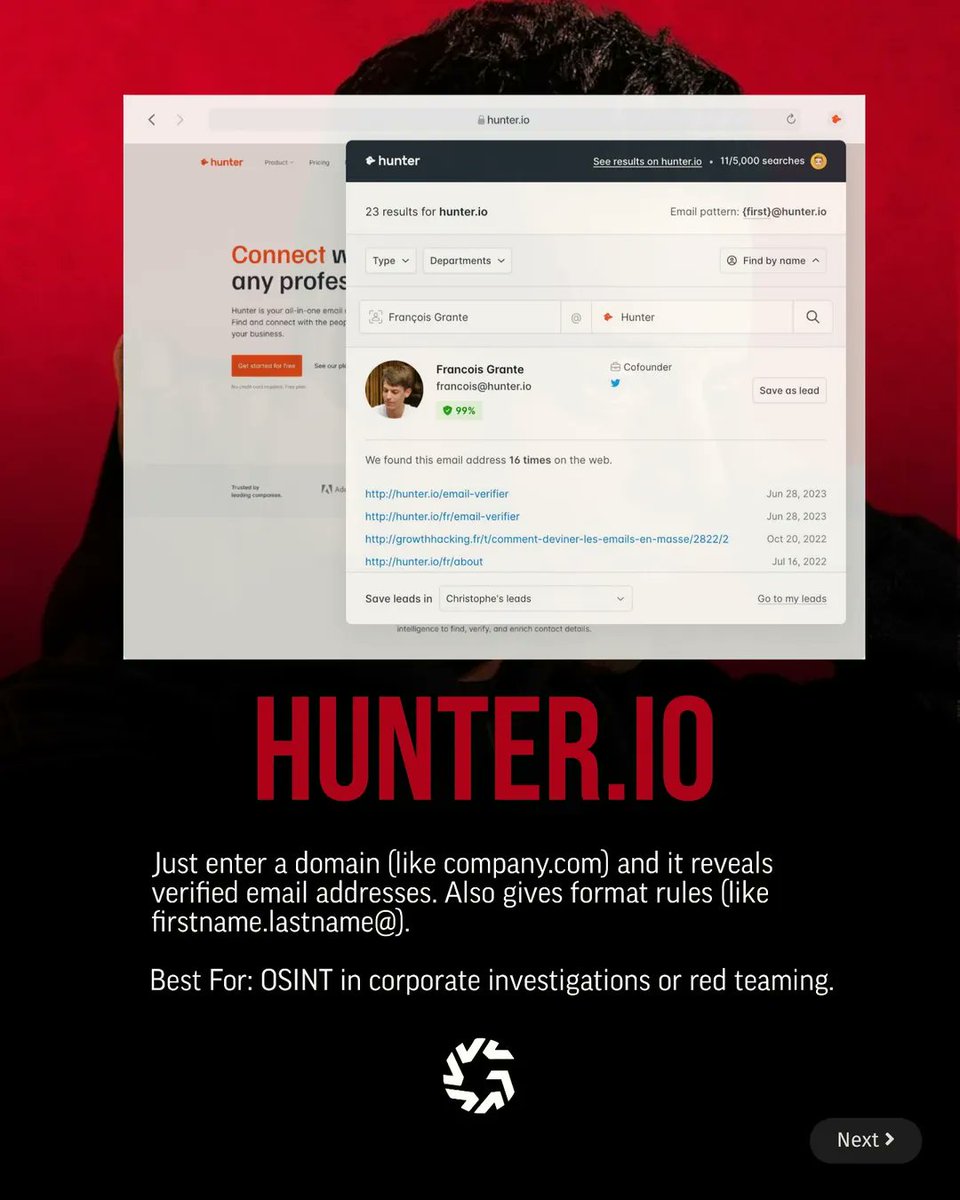
🔎 Want to Find Someone Online? Ethical OSINT Tools You Should Know 💻 Use open-source intelligence (OSINT) to uncover public digital footprints from social media and emails to photos, metadata, and exposed devices. #OSINT #CyberSecurity #EthicalHacking #DigitalInvestigation



Alhamdulillah! Not bad at all I received three bounties at the start of October, and more are on the way, insha’Allah. #BugBounty #EthicalHacking #BEGINNERS #October



Free Ethical Hacking Courses 👇👇👇👇 icttube.com/category/secur… free4arab.net/courses/?c_sea… #Free4arab #ethicalhacking

For #Cybersecurity, #EthicalHacking àti bẹ́ẹ̀ bẹ́ẹ̀ lọ 😂 You can always reach us anytime at @o_cyberservices 23 Taiwo #Hackingsanya St., Oshodi-Isolo, Lagos, Nigeria 🇳🇬 WhatsApp / Call: +2347067864301 and +2349034847995 @CoyEmerald1 Cybersecurity Specialist
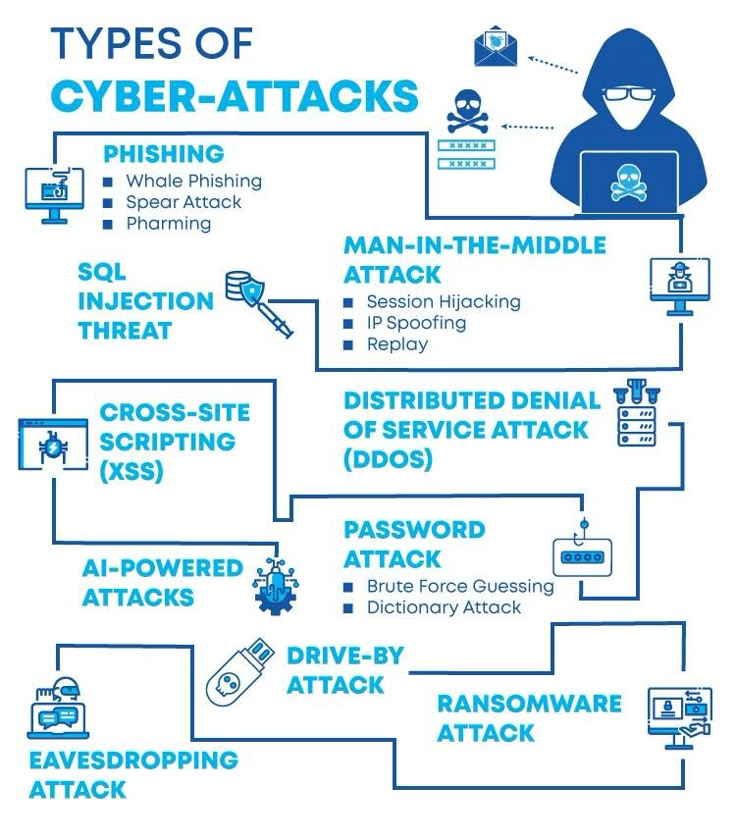
Protect Your Digital Life! 🛡️ This map of cyber-attacks shows the challenges businesses and individuals face every day. Connect with us:wa.link/gpelah #CyberSecurity #EthicalHacking #hacker #cyberatack #phishing #passwordattack
I reported sensitive information such as email, full name, date of birth, city, image of each user, everything had more than 10 files and the company just asked thank you for the information and closed withThe triage team knew the problem #BugBounty #EthicalHacking

Enough SQLI’s for today #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

Again on the Top 3 in intigriti leaderboard for this month 🙌🏻 Thanks @intigriti #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking #WebApp

⚔️ Penetration Testing Tools — Essential Toolkit Curated list of must-have tools for recon, scanning, exploitation, post-exploit, and reporting — use only in labs or with explicit permission. 🔍🛠️ #PenTesting #Infosec #EthicalHacking #RedTeam




Thanks @CocaCola Coca-Cola bug bounty via @intigriti My jacket arrived very quickly, now I'm going to wear it.👾🔥💻 #BugBounty #ethicalhacking #cocacola

I’ve developed **Aurora_Tool**, a tool to help speed up testing Salesforce pages and generate ready-to-use reports. Interested in learning more or getting access? Join me on TG for details: t.me/kassems94 #BugBounty #Cybersecurity #EthicalHacking #Salesforce


Yay getting 1000 euros 🥵👾💻🔥 #hacking #bugbounty #EthicalHacking #Bugbountytipes Hunting Tips --> Whenever you find an exposed token, try to validate it

Follow this journey here 👾💻This bounty is a good amount of money. Thank you to the best triage team in the world and the best platform in the world. @intigriti #BugBounty #bugbountytips #EthicalHacking Hunting tips --> always check the JSON and JS can lead

New hunters be like 👀💸 Bug Bounty Programs all day… meanwhile VDPs and Responsible Disclosure programs are out here gasping for attention. 🫠🔍 #BugBounty #EthicalHacking

Day 3 of #100DaysOfCybersecurity Built my ethical-hacking lab today, I installed VirtualBox + Kali Linux. Learnt about the relevance of using Obsidian for note taking #EthicalHacking @ireteeh @AQskill @cybergirl_io @elormkdaniel @cyber_razz

Hello huntings, this was my 16 duplicate on hackerone A classic open-redirect 👾💻 #bughunting #BugBounty #EthicalHacking #bugbountytips
Free Ethical Hacking Courses 👇👇👇👇 icttube.com/category/secur… free4arab.net/courses/?c_sea… #Free4arab #ethicalhacking

Ready to ace your CompTIA PenTest+ exam? 🎯 Our ultimate guide has you covered, from exam prep to career boost in #Cybersecurity! 🔗 Get certified: flashgenius.net/blog-article/u… #PenTestPlus #EthicalHacking #ITCertifications
Digital threats never sleep and neither do we. Our Ethical Hacker Solutions protect your data, privacy, and future with integrity and precision. 📩 [email protected] 🌐RecoveryPro.Online #EthicalHacking #lestraîtres #CyberAnalyst #Pakistan

Today is the day to try to capture this flag. I don't understand much about CTF, I don't think I'll even be able to capture it lol. more doing what just for fun and understanding how it works 👾👾 #EthicalHacking #ctf #Hacking

Enough SQLI's for today ( part 2 ) Thanks @intigriti <3 #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

.@DubaiPoliceHQ has announced a major #cybersecurity initiative for October, featuring a “Capture the Flag” (CTF) competition with a total prize pool of Dh223,000. The competition, aimed at discovering and attracting talent in #EthicalHacking, is a cornerstone of a broader…

Day 1 of my #30DayMobileHackingChallenge! 🛠️📱 Set up Android Studio, adb & apktool to dive into mobile app hacking. #EthicalHacking #Cybersecurity

Mau belajar Cyber Security tapi bingung mulai dari mana? Dari news channel, website, YouTube, hingga aplikasi & sertifikasi — semua ada di sini! 🚀 Mulai tingkatkan skill, biar jadi lebih aman di dunia digital. #CyberSecurity #EthicalHacking

Ethical Hacker, Fate i bravi! 😆😆 #redhotcyber #informationsecurity #ethicalhacking #dataprotection #hacking #cybersecurity

Is it the time to come back ? YES #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

Today was a tough one 🥵. I started Module 3 of Ethical Hacking — Information Gathering & Vulnerability Scanning. Learned about passive vs active recon and tried out some other OSINT tools for enumeration. Not done yet, still pushing through 💻🔍 #EthicalHacking #OSINT




Alhamdulillah! Not bad at all I received three bounties at the start of October, and more are on the way, insha’Allah. #BugBounty #EthicalHacking #BEGINNERS #October



Again on the Top 3 in intigriti leaderboard for this month 🙌🏻 Thanks @intigriti #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking #WebApp

Day in the lab @Cisco Ethical Hacking 🔐 — leveled up on Active Reconnaissance. From Nmap scans to enumeration & packet crafting with Scapy, every packet told a story. 🚀 #CyberSecurity #EthicalHacking @ireteeh


Free Ethical Hacking Courses 👇👇👇👇 icttube.com/category/secur… free4arab.net/courses/?c_sea… #Free4arab #ethicalhacking

Yay getting 1000 euros 🥵👾💻🔥 #hacking #bugbounty #EthicalHacking #Bugbountytipes Hunting Tips --> Whenever you find an exposed token, try to validate it

Enough SQLI's for today ( part 2 ) Thanks @intigriti <3 #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

I reported sensitive information such as email, full name, date of birth, city, image of each user, everything had more than 10 files and the company just asked thank you for the information and closed withThe triage team knew the problem #BugBounty #EthicalHacking

Enough SQLI’s for today #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

Follow this journey here 👾💻This bounty is a good amount of money. Thank you to the best triage team in the world and the best platform in the world. @intigriti #BugBounty #bugbountytips #EthicalHacking Hunting tips --> always check the JSON and JS can lead

OSINT fundamental logic ! Hacker-must-know #cybersecurity #ethicalhacking #hacking #hackerlife #hacker #mind #psychology

🔎 Want to Find Someone Online? Ethical OSINT Tools You Should Know 💻 Use open-source intelligence (OSINT) to uncover public digital footprints from social media and emails to photos, metadata, and exposed devices. #OSINT #CyberSecurity #EthicalHacking #DigitalInvestigation




Protect Your Digital Life! 🛡️ This map of cyber-attacks shows the challenges businesses and individuals face every day. Connect with us:wa.link/gpelah #CyberSecurity #EthicalHacking #hacker #cyberatack #phishing #passwordattack

Something went wrong.
Something went wrong.
United States Trends
- 1. Auburn 42.4K posts
- 2. Brewers 59.9K posts
- 3. Georgia 66.3K posts
- 4. Cubs 54K posts
- 5. Kirby 22.6K posts
- 6. Michigan 61.9K posts
- 7. Hugh Freeze 2,987 posts
- 8. #GoDawgs 5,348 posts
- 9. Kyle Tucker 3,028 posts
- 10. #ThisIsMyCrew 3,136 posts
- 11. Boots 49.9K posts
- 12. Amy Poehler 3,027 posts
- 13. Gilligan 5,232 posts
- 14. Jackson Arnold 2,110 posts
- 15. Tina Fey 2,093 posts
- 16. #MalimCendari3D 3,009 posts
- 17. Nuss 5,630 posts
- 18. Arizona 40.9K posts
- 19. Sherrone Moore 2,021 posts
- 20. #MagicBrew 11.9K posts