你可能會喜歡
Start Your Career with Cyber Security #Join_Shellbytes_Cyber_Security #Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensic_Investigation #In_Depth_Advance_Networking #Web_Application_Security #Malware_Analysis Phone:+91 8707307583 web-www.shellbytes.in
New Critical Exim #Vulnerability Exposes Email Servers to Remote Attacks, Potentially Leading to Remote Code Execution (RCE). Details ➤ thehackernews.com/2019/09/exim-e… Exim Version 4.92.3 Released With Patches. Update Now! #Shellbytes_Cyber_Secuirity shellbytes.in
DumpsterFire - "Security Incidents In A Box!" A Modular, Menu-Driven, Cross-Platform Tool For Building Customized, Time-Delayed, Distributed Security Events ift.tt/2m3ejJc
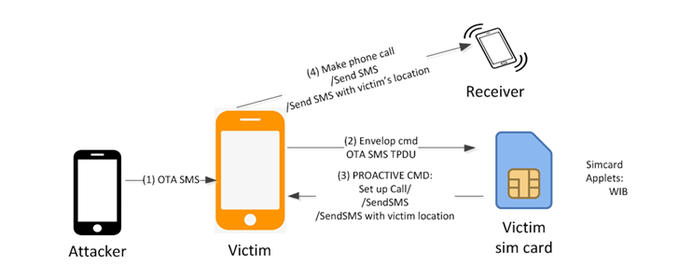
🔥 Important — More SIM cards are vulnerable to #Simjacker attacks than previously disclosed Details ➤ thehackernews.com/2019/09/dynami… Turns out the S@T Browser is not the only dynamic SIM toolkit that could allow remote attackers to compromise phones just by sending SMS. #Shellbytes
#Shellbytes_Cyber_Security #Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensic_Investigation #In_Depth_Advance_Networking #Web_Application_Security #Certified_Network_Defender #Malware_Analysis web-www.shellbytes.in Email:[email protected]

#What_is_ethical_hacking? Ethical hacking involves the use of hacking tools, tricks and techniques to identify vulnerabilities so as to ensure system security. #Learn_Ethical_Hacking_With_Shellbytes #Shaping_Your_carrer_With_Us Phone:+91 8707307583 shellbytes.in

#Malware_analysis:- Malware analysis is the study or process of determining the functionality, origin and potential impact of a given malware sample such as a virus, worm, trojan horse, rootkit, or backdoor. #Learn_Malware_analysis_with_shellbytes_cyber_Security #Ethical_Hacking

#Grab_The_Knowledge_With_Shellbytes #Certified_Ethical_Hacker #Certified_Threat_Intelligent #Penetration_Testing #Malware_Analysis #Siem_Tool #Oracle_Oca #Web_Application_Security #Mobile_Application_Security Phone:+91 8707307583 Email:[email protected]

#Shellbytes #Certified_Ethical_Hacker #Certified_Network_Defender #Certified_Information_Security_Auditor #Certified_Information_Security_Manager #Certified_Security_Analyst #Certified_Secure_Programmer Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

#Malware_Analysis #Penetration_Testing #Certified_Information_Security_Manager #Network_Associate_Security #Network_Associate_Routing_And_Switching #Hacking_Forensic_Investigator #System_Security_Professional Phone:+91 8707307583 Email:[email protected]

#System_Auditor #Security_Manager #System_Security_Professional #Network_Associate_Security #Malware_Analysis #Certified_Threat_Intelligent #CHIFF_Information_Security_Officer #Certified_Network_Defender Phone:+91 8707307583 Email:[email protected] web-www.shellbytes.in

Mozilla launches a new privacy-focused VPN service, called—Firefox Private Network—that aims to encrypt your online activity and limit what websites and advertisers know about you Details Here ➤ thehackernews.com/2019/09/firefo… #privacy #infosec #software #cybersecurity #VPN

#Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensics_Investigation #In-Depth_Advance_Networking #Web_Application_Security #Malware_Analysis #Certified_Information_Security_Manager Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

#Grab_The_Knowledge_With_Shellbytes #Shaping_Your_Carier_With_Us #Web_Designing #Android_Development #Digital_Marketing #Machine_Learning #Python #Advance/Core_Java #Big_Data #Graphics_Designing #Live_Project_Based_Training Phone:+91 8707307583 Email:[email protected]

#Certified_Ethical_Hacker #Penetration_Testing #Network_Associate_Security #Malware_Analysis #Certified_Information_System_Security_Professional #Certified_Threat_Intelligent #Certified_Secure_Computer_User Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

#Ethical_Hacking_Course_Training_In_Lucknow #Certified_Ethical_Hacker #Penetration_Testing #System_Auditor #Security_Manager #System_Security_Professional #Network_Associate_Security #Malware_Analysis #in_depth_advance_networking Phone:+91 8707307583 Email:[email protected]

#Certified_Network_Defender #Certified_Information_Security_Auditor #Certified_Information_Security_Manager #CCNA_Security #CCNP_Router&Switching #Malware_Analysis #cybersecurity #informationsecurity Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

#Learn_Ethical_Hacking_With_Shellbytes #Certified_Network_Defender #Certified_Information_Security_Manager #Malware_Analysis #Security_Analyst #SIEM_Tool #Web_Designing #Internship_Opportunity Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

#Ethical_Hacking_Course_Training_In_Lucknow #Ethical_Hacking_Certification #Advanced_Penetration_Testing #Cyber_Forensics_Investigation #In-Depth_Advance_Networking #Web_Application_Security #Live_Project Phone:+91 8707307583 Email:[email protected] Web-www.shellbytes.in

United States 趨勢
- 1. #AskFFT N/A
- 2. Good Sunday 63.7K posts
- 3. #sundayvibes 5,507 posts
- 4. #HardRockBet 1,049 posts
- 5. Go Bills 3,675 posts
- 6. #Talus_Labs N/A
- 7. Full PPR N/A
- 8. Sunday Funday 3,760 posts
- 9. Ireland 109K posts
- 10. #AskBetr N/A
- 11. Gronk 2,209 posts
- 12. Blessed Sunday 20.7K posts
- 13. Kelly Green 1,720 posts
- 14. Real Madrid 144K posts
- 15. Cambodia 38.2K posts
- 16. McLaurin 1,301 posts
- 17. Schultz 12K posts
- 18. Barcelona 147K posts
- 19. Mooney 1,948 posts
- 20. Noel 22.1K posts
你可能會喜歡
Something went wrong.
Something went wrong.
































