
SecureBinary
@thesecurebinary
Information Security Company | App Sec • Red Teaming • Digital Forensics
قد يعجبك
Bounties that are split with the hackforgood user on H1 will now go to help people in Türkiye and Syria. hackerone.com/hackforgood
Great chance for all of us to do good thing for our peoples in Türkiye and Syria Due to the earthquakes a lot of people lost there life lost there home lost there families Thanks @Hacker0x01 for this i hope @Bugcrowd also will do the same
Bounties that are split with the hackforgood user on H1 will now go to help people in Türkiye and Syria. hackerone.com/hackforgood
May the magic and joy of the holiday season fill your heart and home with love and laughter. Team SecureBinary wishes you and your loved ones a very Merry Christmas and a Happy New Year.

I'm really addicted to ChatGPT. Maybe I will finally complete the last step of becoming a YouTuber - releasing a song.

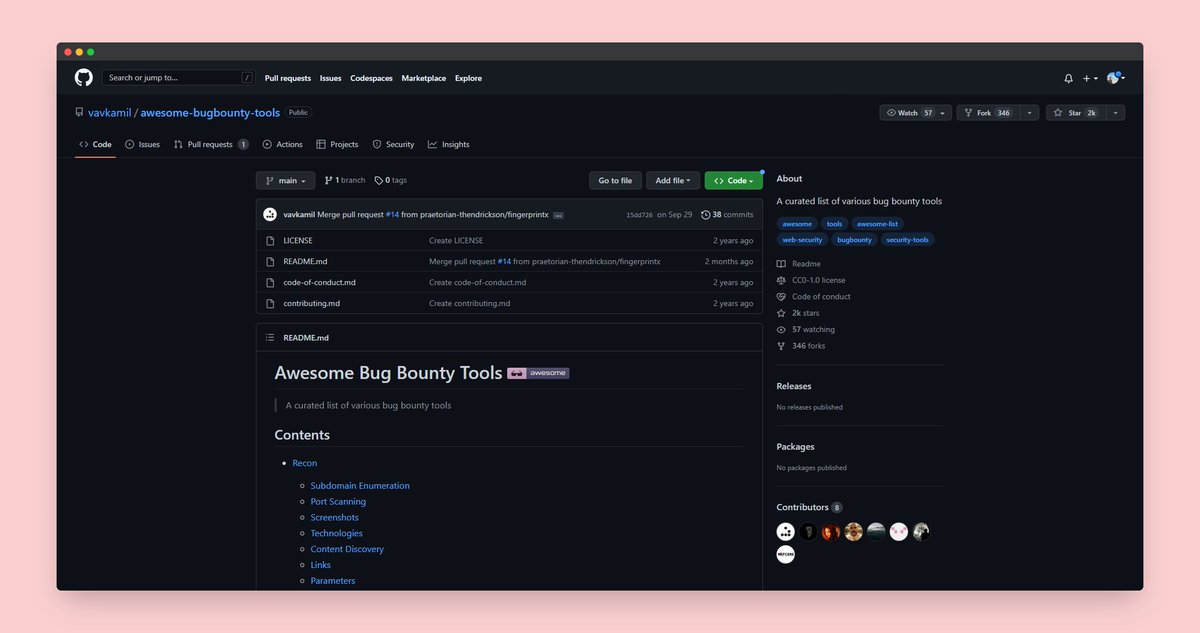
☃️Awesome Bug Bounty Tools☃️ A curated list of various bug bounty tools for: ➡️ Recon ➡️ Exploitation and much more... #bugbounty #pentesting #tools #infosec #cybersecurity
Much like anything else, we #HACKED reporting! 😎 Here's a helpful template and guide to create the report for all your different #pentests: ✔️ Black box ✔️ White box ✔️Web application ✔️ Hardware Take a read of our #blog to learn more👇 bit.ly/3i3Np0y

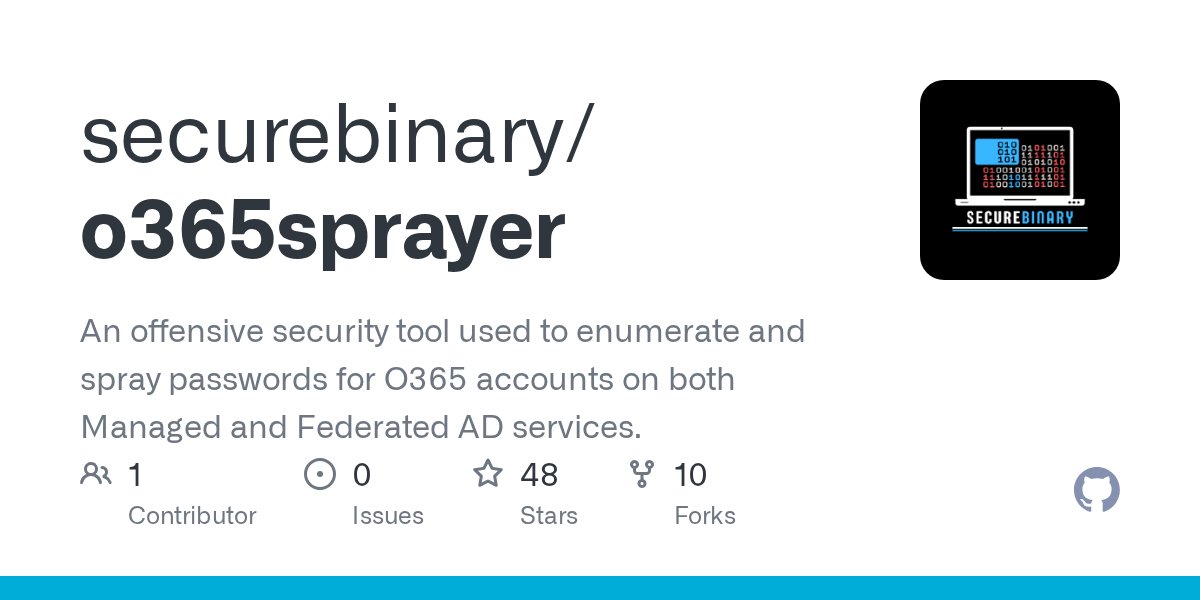
Hello Infosec People ! Check out our new project, our first red team tool written in Go. Introducing you to #o365sprayer An offensive security tool used to enumerate and spray passwords for O365 accounts on both Managed and Federated AD services. github.com/securebinary/o…
Check out this new article about Dom Clobbering by @0xGodson_ 👾 securebinary.in/blog/web/art-o…
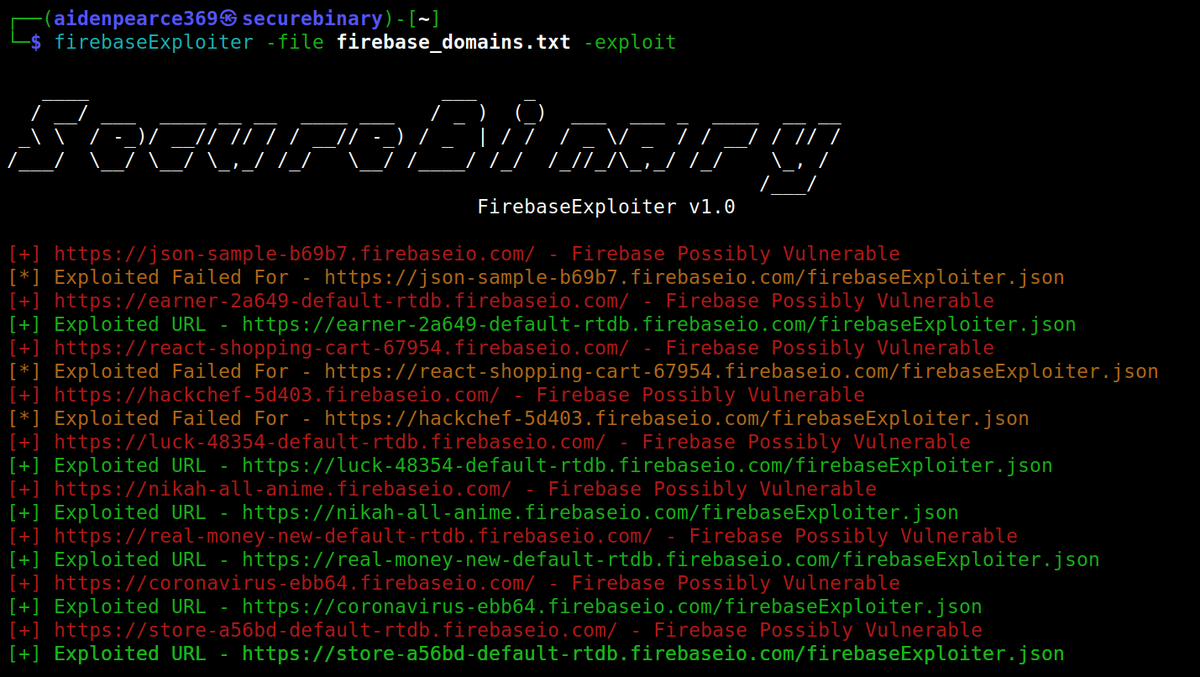
🛠️ firebaseExploiter A vulnerability discovery tool that discovers Firebase databases that are open and can be exploited Primarily built for mass hunting #bugbounty and #pentesting By @thesecurebinary github.com/securebinary/f…
Featuring articles by @xdavidhu, @niksthehacker, @mrgretzky, @rahullraz, @0xnxenon, @Agent472458 Trending threads by @rez0__, @ReconOne_, @Steiner254, @maikroservice Videos by @ippsec, @gregxsunday, @intigriti GitHub repositories & Tools by @pdiscoveryio, @thesecurebinary
Hello community 👋 Check out our new tool: github.com/securebinary/f… FirebaseExploiter is a vulnerability discovery tool that discovers Firebase Database which are open and can be exploitable. Primarily built for mass hunting bug bounties and for penetration testing.
Introduction to Linux Heap Internals
A lot has been said about removing hooks and kernel callbacks to stop an EDR from detecting malicious activity. What if we could terminate the process completely? Well ...we can. Check this out: spikysabra.gitbook.io/kernelcactus/
CVE-2022-35256: HTTP Request Smuggling in NodeJS feed.prelude.org/p/cve-2022-352…
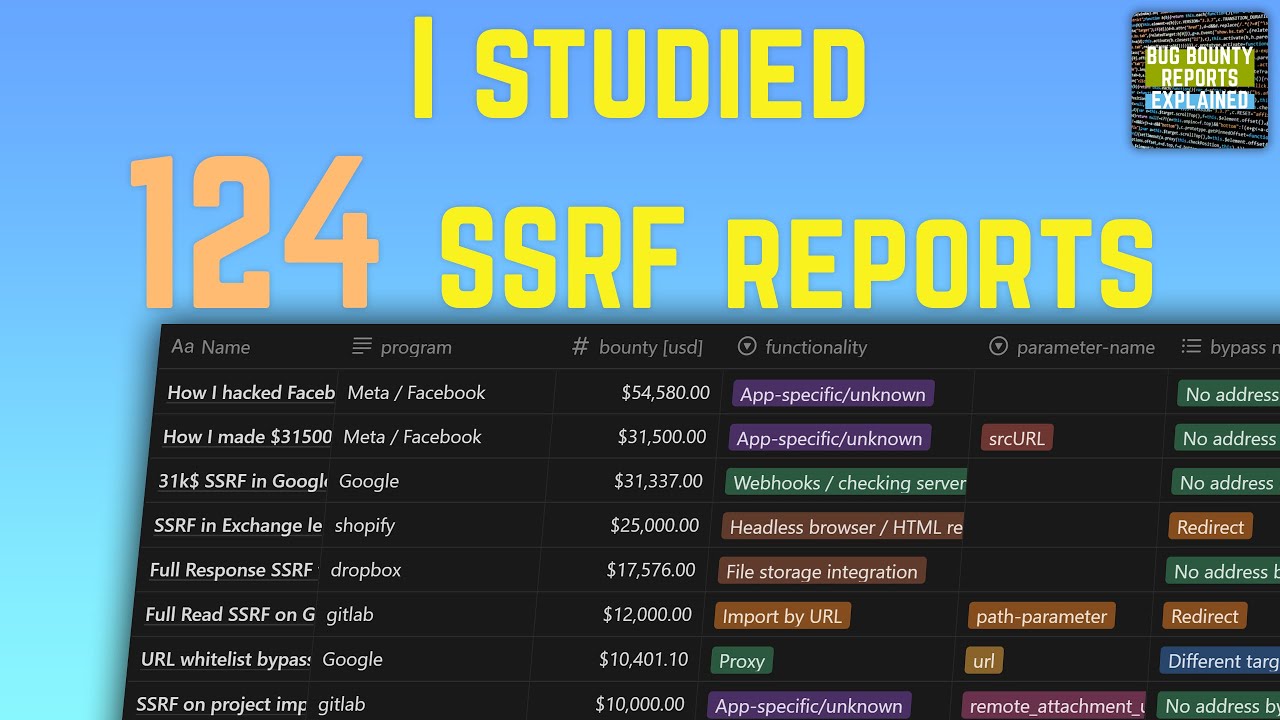
SSRF seems like a simple vulnerability class but in reality, there are many variables. To see how are people really making money with them, I studied 124 bug bounty reports. From this video, you will learn which functionalities are most often vulnerable. youtu.be/0GxsUS1P5xs
youtube.com
YouTube
What functionalities are vulnerable to SSRFs? Case study of 124 bug...
United States الاتجاهات
- 1. D’Angelo 343K posts
- 2. Charlie 651K posts
- 3. Erika Kirk 71.7K posts
- 4. Young Republicans 25.6K posts
- 5. Politico 207K posts
- 6. #AriZZona N/A
- 7. #PortfolioDay 22.2K posts
- 8. Jason Kelce 5,261 posts
- 9. Pentagon 110K posts
- 10. Presidential Medal of Freedom 90.6K posts
- 11. #LightningStrikes N/A
- 12. George Strait 5,049 posts
- 13. Big 12 14.3K posts
- 14. Kai Correa N/A
- 15. NHRA N/A
- 16. Burl Ives N/A
- 17. Milei 322K posts
- 18. Drew Struzan 36.5K posts
- 19. Scream 3 1,063 posts
- 20. Brown Sugar 24.9K posts
Something went wrong.
Something went wrong.
















































































![dayzerosec's profile picture. Account for the day[0] podcast + media.](https://pbs.twimg.com/profile_images/1221600753904537601/8sV0PIy_.png)































