
VulnTracker
@vuln_tracker
Track, monitor, and get notified about vulnerabilities before they become threats. Join our telegram group! https://t.me/+Z4tQeCFscVdkNjI8
🚨 CVE-2025-64446 – Fortinet FortiWeb Path Traversal A relative path traversal flaw in FortiWeb 7.0.0–8.0.1 may let attackers execute administrative commands via crafted HTTP/HTTPS requests. More details → vulntracker.io/cves/CVE-2025-… Track only the vulns that affect your products…
Vulntracker.io flips the script on vulnerability tracking. Real-time alerts, zero noise, total control. Stay sharp, stay ahead. Security just got smarter.
Unmask risks before they strike. vulntracker.io dives deep into vulnerabilities, tracking updates in real-time to keep your systems one step ahead. Security isn't reactionary—it's proactive. Elevate your defense game today. #CyberSecurity #VulnTracker
🚨 Alert: CVE-2025-33186 is a critical vulnerability you can't ignore! Stay ahead of threats with vulntracker.io – your ultimate security ally for real-time vulnerability monitoring. Protect your assets & sleep easy. Get today! #CyberSecurity…
🚨 New Vulnerability Alert: CVE-2025-33186 exposes critical security risks! Stay ahead of threats with VulnTracker.io—your ultimate vulnerability management solution. Protect your assets and reduce risk today. Get started now! #CyberSecurity #VulnerabilityManagement…
🚨 Security Alert: CVE-2025-59287 has been identified! This vulnerability could impact your systems if not patched promptly. Ensure you update your software and apply security patches to protect your data and infrastructure. Stay safe and secure! #CyberSecurity #CVE202559287
Discover the latest vulnerabilities instantly with VulnTracker.io! Stay updated on CVEs and security threats to keep your systems safe. #CyberSecurity #Vulnerabilities #VulnTracker vulntracker.io
You can favor this vulnerability and get notified when the vulnerability is updated. Check for more details from vulntracker.io/cves/CVE-2025-….

Unit 42 uncovered LANDFALL, previously unknown Android spyware that exploited a zero-day vulnerability CVE-2025-21042 in Samsung Android’s image processing library. This is the first public analysis of the campaign and the implant. Read more: bit.ly/47rwbS0

You can see the details from vulntracker.io/cves/CVE-2025-… for free now!

🚨 Cisco warns hackers are targeting unpatched Secure Firewall ASA & FTD devices with a new attack variant exploiting two flaws — CVE-2025-20333 and CVE-2025-20362. The attacks can crash devices (DoS) or let attackers run code as root. Details here ↓ thehackernews.com/2025/11/cisco-…
Security shouldn’t slow down developers. In our latest post, I wrote about automating vulnerability tracking so you only see alerts that affect your dependencies. Check it out → vulntracker.io/blog/developer…
Imagine getting alerts only for vulnerabilities that affect the products you use. Meet VulnTracker.io — your smart CVE tracker, free for now. 🔒
You can check the details from vulntracker.io/cves/CVE-2025-… for free!

[ZDI-25-960|CVE-2025-62590] Oracle VirtualBox VMSVGA Stack-based Buffer Overflow Local Privilege Escalation Vulnerability (CVSS 8.2; Credit: VMBreakers(GANGMIN KIM, SANGBIN KIM, Un3xploitable)) zerodayinitiative.com/advisories/ZDI…
You can check the details from vulntracker.io/cves/CVE-2025-… for free!

🚨Alert🚨:CVE-2025-12044&CVE-2025-11621 : Two HashiCorp Patches Vault Flaws——Unauthenticated JSON DoS and AWS Auth Bypass 📊117.9K Services are found on the hunter.how yearly. 🔗Hunter Link:hunter.how/list?searchVal… 👇Query HUNTER : product.name="HashiCorp…

Vulnerabilities don’t wait — and neither should you. VulnTracker.io keeps you updated on daily CVEs affecting your products. 🚀 It’s free for now. Try it today.
Yes you can see the updates for CVE-2025-59287 from our newly published product vulntracker.io. Check the link vulntracker.io/cves/CVE-2025-… and get the details you need!
CORRECTED: We've observed exploitation in the wild of Windows Server Update Services RCE CVE-2025-59287. MSFT rec: immediately install the out-of-band update. If unable to patch: Block high-risk ports and disable WSUS Server Role. bit.ly/4hLlMEp
Yes you can see the details from vulntracker.io/cves/CVE-2025-… for free!

Unauthenticated SQL injection leading to RCE in FreePBX Endpoint (CVE-2025-57819) labs.watchtowr.com/you-already-ha… Credits @watchtowrcyber #infosec


You can easily see the details from vulntracker.io/cves/CVE-2025-… for free!

CVE-2025-39965: UAF in Linux Kernel XFRM hackyboiz.github.io/2025/10/26/l0c… A July fix for duplicate SPI allocation introduced a UAF vulnerability in the IPsec XFRM subsystem:
You can easily see the details from vulntracker.io/cves/CVE-2023-… for free!

VMware Workstation guest-to-host escape (CVE-2023-20870/CVE-2023-34044 and CVE-2023-20869) nccgroup.com/media/b2chcbti… Credits Alexander Zaviyalov (@NCCGroupInfosec) #infosec
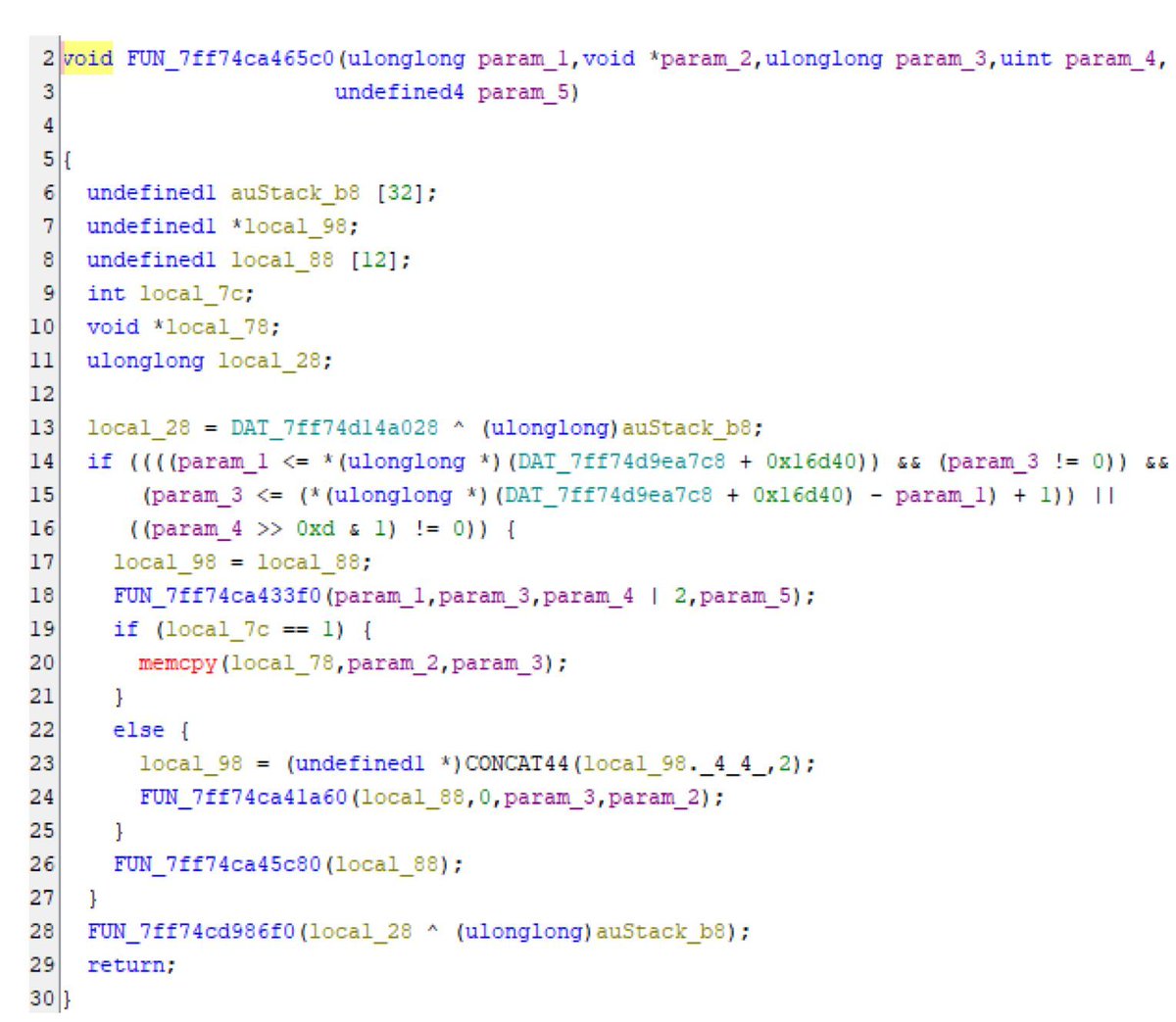
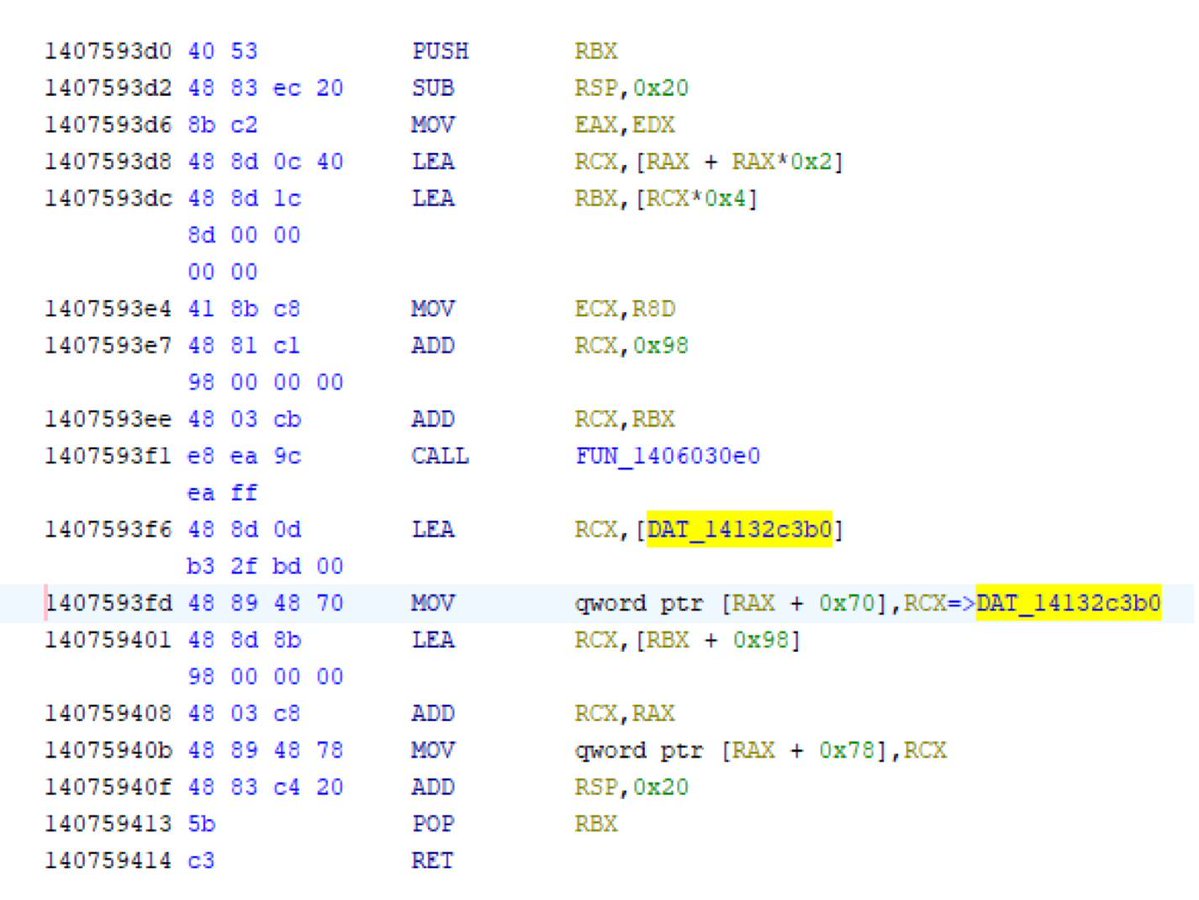
You can easily see the details from vulntracker.io/cves/CVE-2025-… for free!

While the exploit craddles from hawktrace for CVE-2025-59287 did not work in our testbed, github.com/jiansiting/CVE… actually did. Be aware, include SCCM when the Software Update Point role is in use, as this requires WSUS.
You can see the details from vulntracker.io/cves/CVE-2025-… for free!

hey hi hello we've been seeing summa dat WSUS sussy baka CVE-2025-59287 remote code execution exploitation windows servers with WSUS ports 8530 & 8531 exposed ( -- why?) getting point-and-shoot popped from a POC already public huntress.com/blog/exploitat… prolly limited ITW…
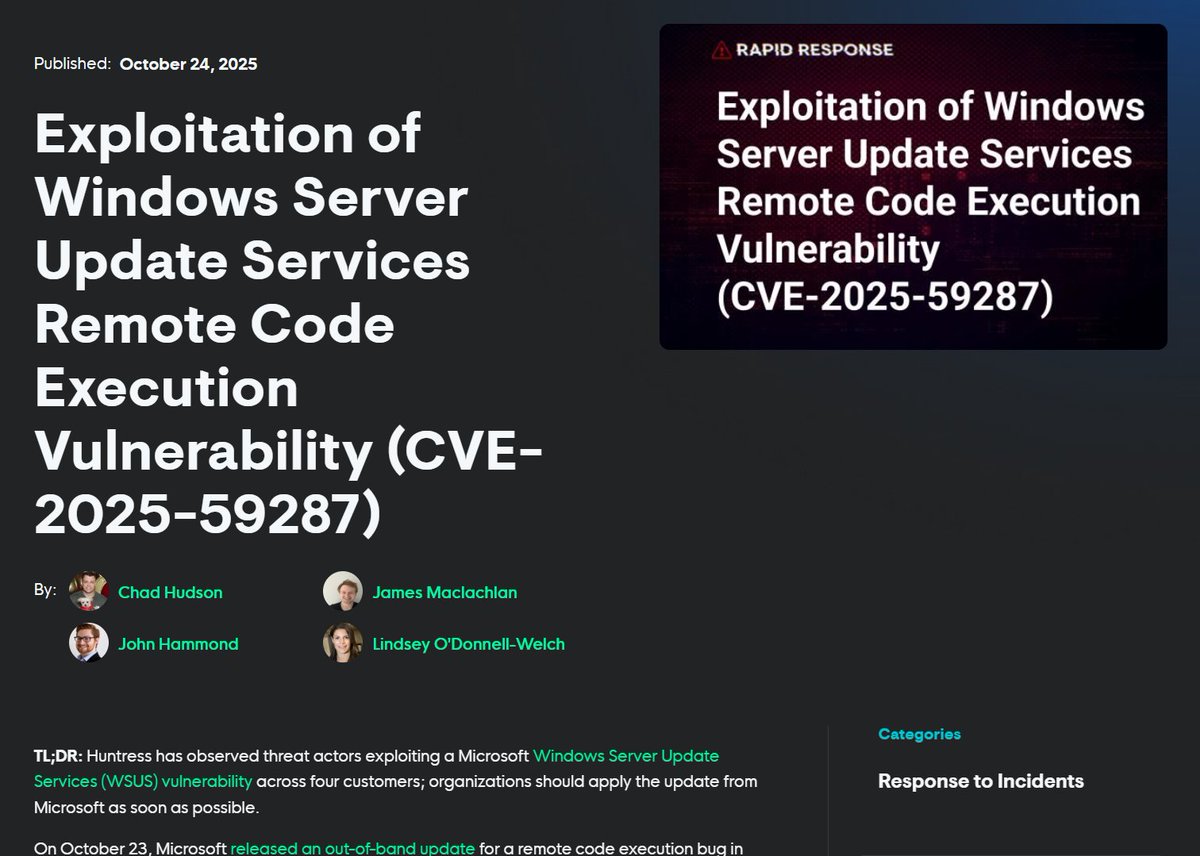
United States Trends
- 1. Massie 84.7K posts
- 2. Good Saturday 33K posts
- 3. GAME DAY 29.2K posts
- 4. Willie Green 3,868 posts
- 5. #Caturday 4,291 posts
- 6. #SaturdayVibes 4,825 posts
- 7. #MeAndTheeSeriesEP1 1.13M posts
- 8. #Varanasi 80.7K posts
- 9. Virginia Tech 2,115 posts
- 10. Brooklynn 2,684 posts
- 11. Senior Day 2,536 posts
- 12. James Borrego 1,299 posts
- 13. Draymond 28.9K posts
- 14. Marjorie 103K posts
- 15. James Franklin 1,828 posts
- 16. #GlobeTrotter 437K posts
- 17. PONDPHUWIN AT MAT PREMIERE 733K posts
- 18. Lindsey Graham 19.6K posts
- 19. Liz Cheney 6,056 posts
- 20. Bubba 69.8K posts
Something went wrong.
Something went wrong.























































