#vulnerabilities نتائج البحث
#AI can detect malicious chip #vulnerabilities with a 97% success rate - but will that be enough? - buff.ly/dHxXrcU #ML #hardwarevulnerabilities #semiconductors #security #supplychain

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

⚠️ CVE-2025-7775 🖥️ Citrix NetScaler ADC/Gateway memory overflow 💬 allows unauthenticated remote code execution on vulnerable NetScaler appliances, enabling full system takeover and lateral movement 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

⚠️ Ivanti Endpoint Manager Vulnerabilities Let Attackers Write Arbitrary Files to Disk Read more: cybersecuritynews.com/ivanti-endpoin… #cybersecuritynews #vulnerabilities #ivanti

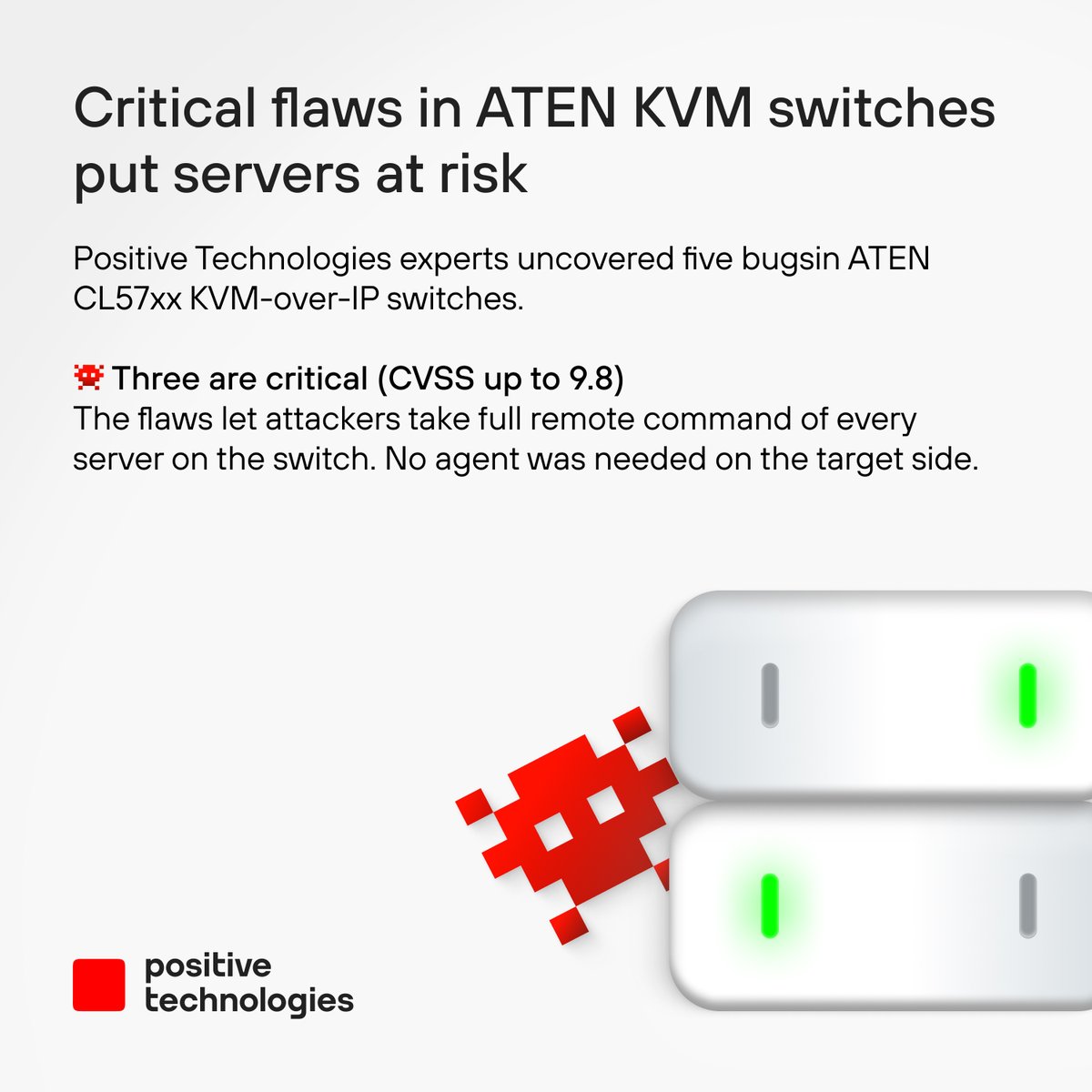
Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies



⚠️ Atenție! Mai multe vulnerabilități critice afectează Google Chrome și alte browsere bazate pe Chromium. 👉 Citește avertizarea completă pe site-ul DNSC: dnsc.ro/citeste/averti… #DNSC #CyberSecurity #Vulnerabilities #UpdateNow #SigurantaOnline

Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



#Cyberattacks on manufacturing aren't just IT issues. They stop production, they threaten supply chains and they exploit wireless and IoT #vulnerabilities. Risk-based security, network segmentation, and strict access controls are now critical.❗mou.sr/3LGw0JU

The #Swagger You Forgot Is the Risk You Inherited Sometimes the biggest #vulnerabilities aren’t hidden behind layers of #obfuscation, they’re sitting in plain sight, waiting for someone curious enough to look. That’s exactly what happened during a recent grey-box web application…

XXE #vulnerabilities happen when a misconfigured XML parser processes an XML input containing external entities. This exposure allows attackers to read local files or conduct SSRF attacks. Disable external entity processing in XML parsers and consider using JSON-based formats…

From 2022 through 2024, APT28 exploited #vulnerabilities to remotely and wirelessly access data from a targeted company network. Our latest post presents vulnerabilities, exploitations, weaknesses, and how they might impact the wireless system - sei.cmu.edu/blog/radio-fre…
#Kubernetes: Newly disclosed #vulnerabilities in the #runC container runtime used in #Docker & Kubernetes (CVE-2025-31133, CVE-2025-52565, CVE-2025-52881) could be exploited to bypass isolation restrictions & get access to the host system (escape): #k8s bleepingcomputer.com/news/security/…
BitsLab’s AI Audit Agent Discovers Multiple Vulnerabilities in Story Protocol’s Smart Contracts @0xbitslab #AI #Vulnerabilities #Web3Security chainwire.org/2025/11/04/bit…
"Let’s draw attention to places where people can act." Tyler Reguly of Fortra weighs in on where CISOs should focus during May's Patch Tuesday. Read his full take via @CSOonline: hubs.la/Q03n7n4N0 #PatchTuesday #infosec #vulnerabilities

✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

Recent updates to the Stakeholder-Specific #Vulnerability Categorization (SSVC) framework help different stakeholders to prioritize #vulnerabilities according to their distinct risk appetites. Our latest post details the updates #CyberSecurityAwareness - sei.cmu.edu/blog/whats-new…

Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


What the Phuzz, we're Back! Ever wonder how #zeroday #vulnerabilities in your favorite websites get uncovered? In this first one, Our guest is diving into a game-changing technique: Coverage-Guided #Fuzzing for #PHP Web Apps! Forget slow scanners; we're talking about finding…
youtube.com
YouTube
S04EP01 | Teaser | What the PHUZZ! - Zero Day Playbook with Coverag...
Unauthenticated DoS Flaw Allows Attackers to Crash Next.js Servers with One HTTP Request gbhackers.com/unauthenticate… #CyberSecurity #Vulnerabilities #CSCIS
An anonymous security researcher has identified at least a dozen juror websites made by government software maker Tyler Technologies that can easily expose jurors' personal data. buff.ly/HfJEACc #Vulnerabilities #PrivacyBreach #DataBreach #Cybersecurity

⚠️ Threats, vulnerabilities, and risks - three words that sound similar but mean very different things. • Threat: What can cause harm • Vulnerability: What makes you weak • Risk: The chance of harm happening #Secura247 #Threats #Vulnerabilities #Risks #CyberEducation
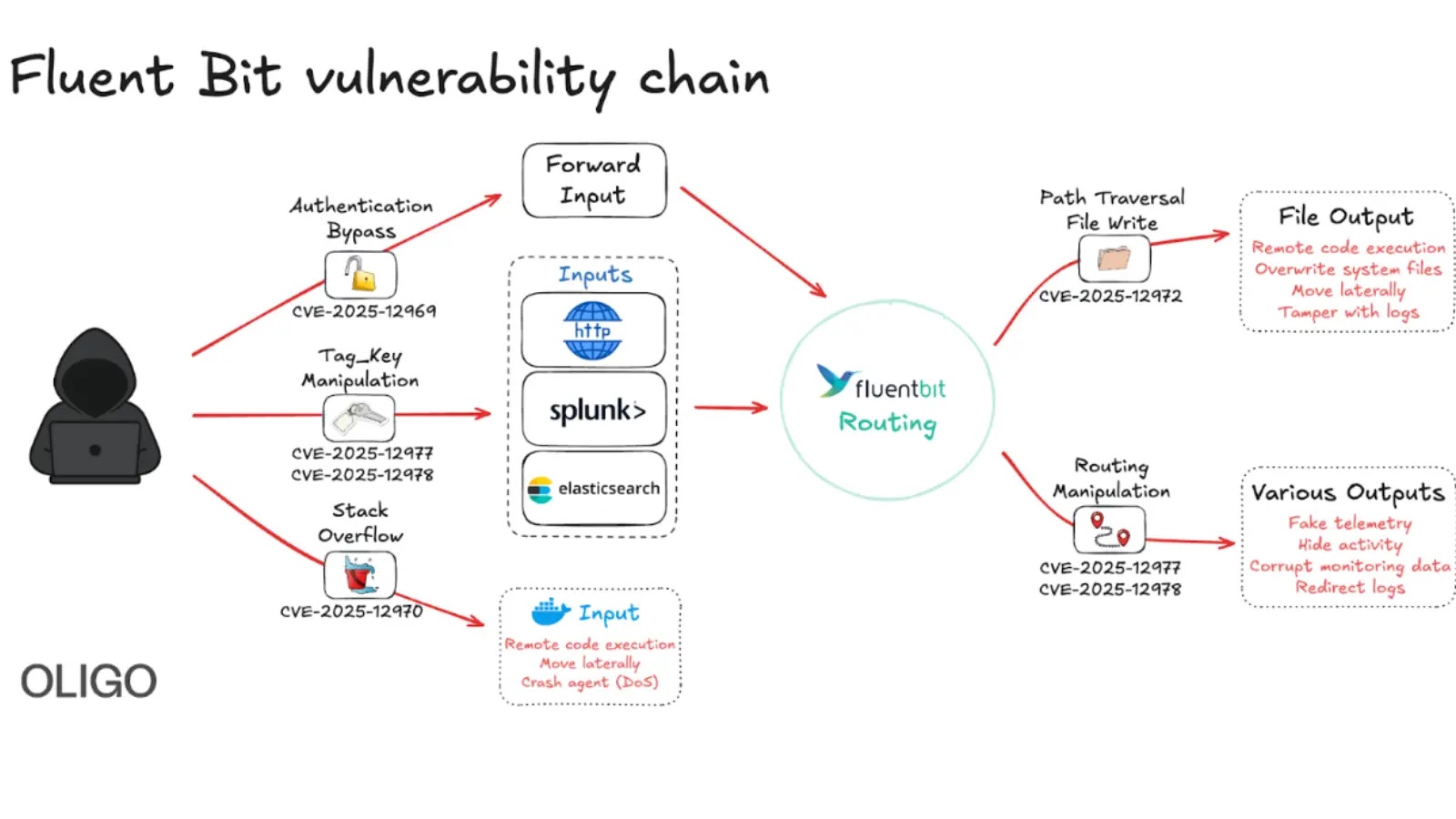
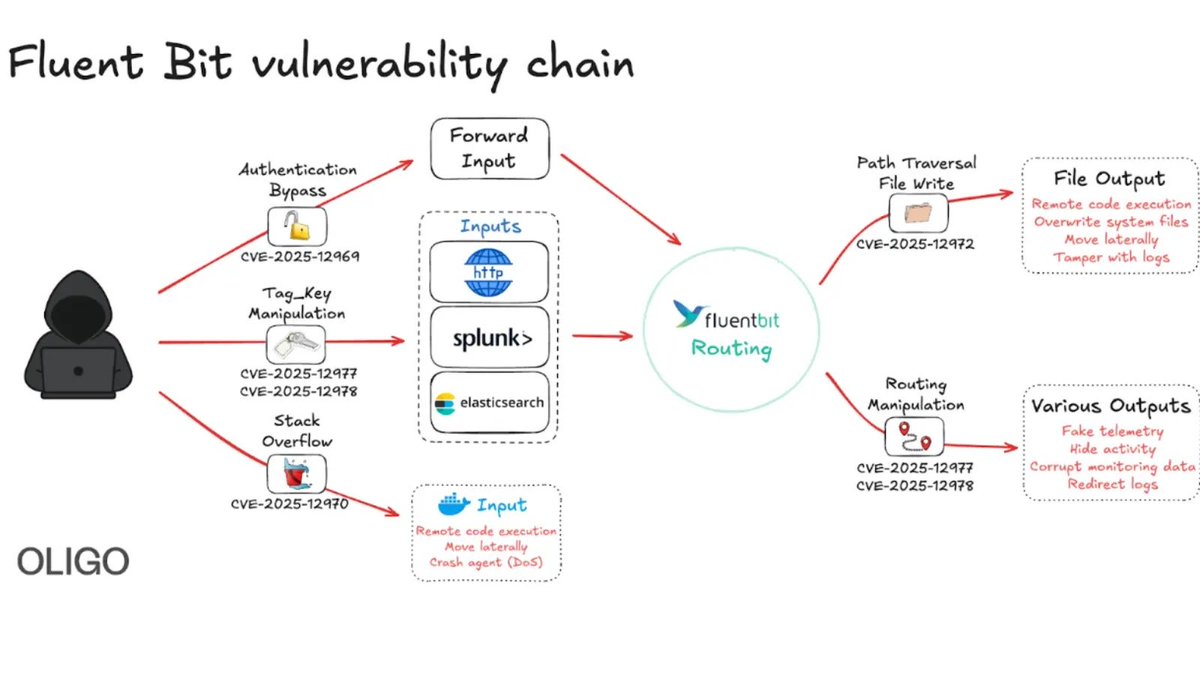
Critical vulnerabilities in Fluent Bit expose cloud environments to remote attacks. Update to version 4.1.0+ immediately to secure your systems. thedailytechfeed.com/critical-vulne… #Vulnerabilities #Remote #Update #Security #Systems #Cloud #Attack #Protection #FluentBit #Technology #Alert…
ASUS firmware updates fix critical authentication bypass in AiCloud routers. Incident response and pen testing recommended. bleepingcomputer.com/news/security/… #CyberSecurity #ASUS #Vulnerabilities
Critical Fluent Bit Vulnerabilities Allow Remote Attacks on Cloud Environments gbhackers.com/fluent-bit-vul… #CyberSecurity #Vulnerabilities #CSCIS
ثغرات خطيرة في Fluent Bit قد تمكّن المهاجمين من السيطرة على خدمات سحابية تستخدمه في مراقبة السجلات. الهجوم يعتمد على تنفيذ أوامر عن بُعد. تحديث عاجل مطلوب لوقف الاستغلال النشط. #FluentBit #CloudSecurity #Vulnerabilities #DevOps #CyberThreats
#WhatsApp closes #security_gap #Vulnerabilities that let researchers collect data on 3.5B accounts ift.tt/Va8M6B3

YOU help keep this movement alive! Thanks for sticking with us while we pursue answers. Full video: youtu.be/3XERg8QilFA #Cybersecurity #Vulnerabilities #Accountability #Trustbutverify #Proofisinthepaper #HandCountedPaperBallots #ItsUpToUs #VerifyTheVote

youtube.com
YouTube
Pennsylvania Lawsuit Filed | Election Truth Alliance
Meltdown and Spectre. Vulnerabilities in modern computers leak passwords and sensitive data meltdownattack.com #meltdown #security #vulnerabilities
Multiple #critical #vulnerabilities have been identified in #VMware products, with evidence of active exploitation by #ransomware groups. Organizations using these products should urgently apply the recommended patches to mitigate potential risks. 1. CISA Adds Four Known…

Pentesting 101 📚 Do you want to gain the fundamental skills to conduct a #penetrationtesting engagement but don't know where to start? This free Module is the answer for all the beginners out there! Explore practical techniques for finding #vulnerabilities and exploiting them…

Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing
⚠️ CVE-2025-3746 🖥️ WordPress OTP-less one tap signin plugin 💬 vulnerable to privilege escalation via account takeover 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

Did you know that all Social Media sites come with psychosocial #vulnerabilities that antimalware can protect you from! Check out: Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/PNmw50X2xoF
🗨️ “As we move into 2025, security teams face a growing wave of AI-powered threats, social engineering attacks, identity exploitation, and supply chain #vulnerabilities”. In their session 'Future‑Proofing Against Cybercrime: The Six Trends Every Organisation Must Know',…

✅ Very happy to report that we have completed STEP 2 of #LUPUSALERT, asking a large international panel to triage & prioritize #lupus #vulnerabilities suggested during step 1, for inclusion in the final screening questionnaire 👍 Thanks to you all for your contributions 👏

#Nvidia #Triton #Vulnerabilities Pose Big Risk to #AI Models - ift.tt/9QulTS4 #genAI #IT #security #infosec #GPUs #AIsecurity #ML

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

#AI can detect malicious chip #vulnerabilities with a 97% success rate - but will that be enough? - buff.ly/dHxXrcU #ML #hardwarevulnerabilities #semiconductors #security #supplychain

✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies




Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


At the launch of the #FutureOfAid2040 report in Delhi, #humanitarians underscored the need to build collectives and understand where #vulnerabilities came from and how they were reshaped. While bridging policy frameworks, it was also essential to ensure that, in the future,…

Popular #AI Systems Still a Work-in-Progress for #Security - ift.tt/MRcrPH1 #vulnerabilities #cybersecurity #infosec #GenaI #LLMs

Something went wrong.
Something went wrong.
United States Trends
- 1. Black Friday 389K posts
- 2. Egg Bowl 4,332 posts
- 3. Mississippi State 2,735 posts
- 4. Kamario Taylor N/A
- 5. Emmett Johnson N/A
- 6. #SkylineSweeps N/A
- 7. NextNRG Inc 1,793 posts
- 8. Trinidad Chambliss N/A
- 9. Wetjen N/A
- 10. Solo Ball N/A
- 11. #Rashmer 24K posts
- 12. Scott Stricklin N/A
- 13. #FanCashDropPromotion 1,766 posts
- 14. #Huskers N/A
- 15. Kewan Lacy N/A
- 16. #jonita 19.8K posts
- 17. Black Ops 7 XP 1,932 posts
- 18. Sumrall 1,093 posts
- 19. Fisch 1,028 posts
- 20. WHO DEY 12.3K posts